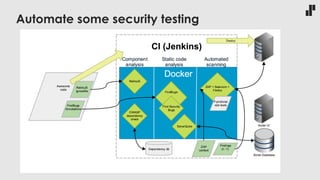
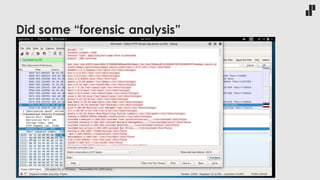
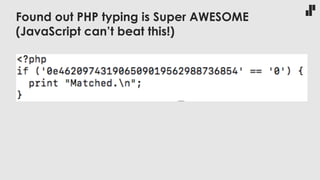
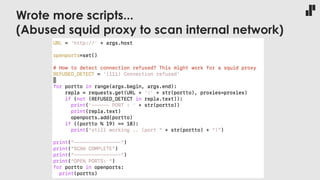
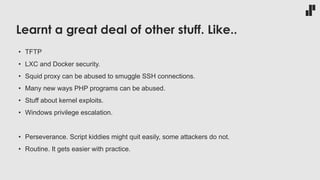
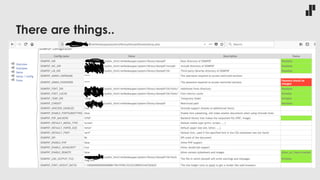
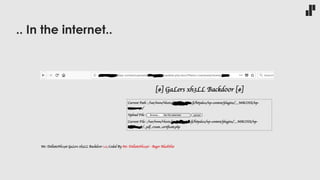
The document discusses the evolving landscape of developer responsibilities in relation to security, emphasizing the trend of integrating security into development practices (DevSecOps). It highlights the need for developers to be educated about various security threats and operational security measures and encourages hands-on hacking experiences to enhance their skills. The speaker also advocates for gamification of learning security, suggesting platforms like Hack The Box for practical and engaging training.