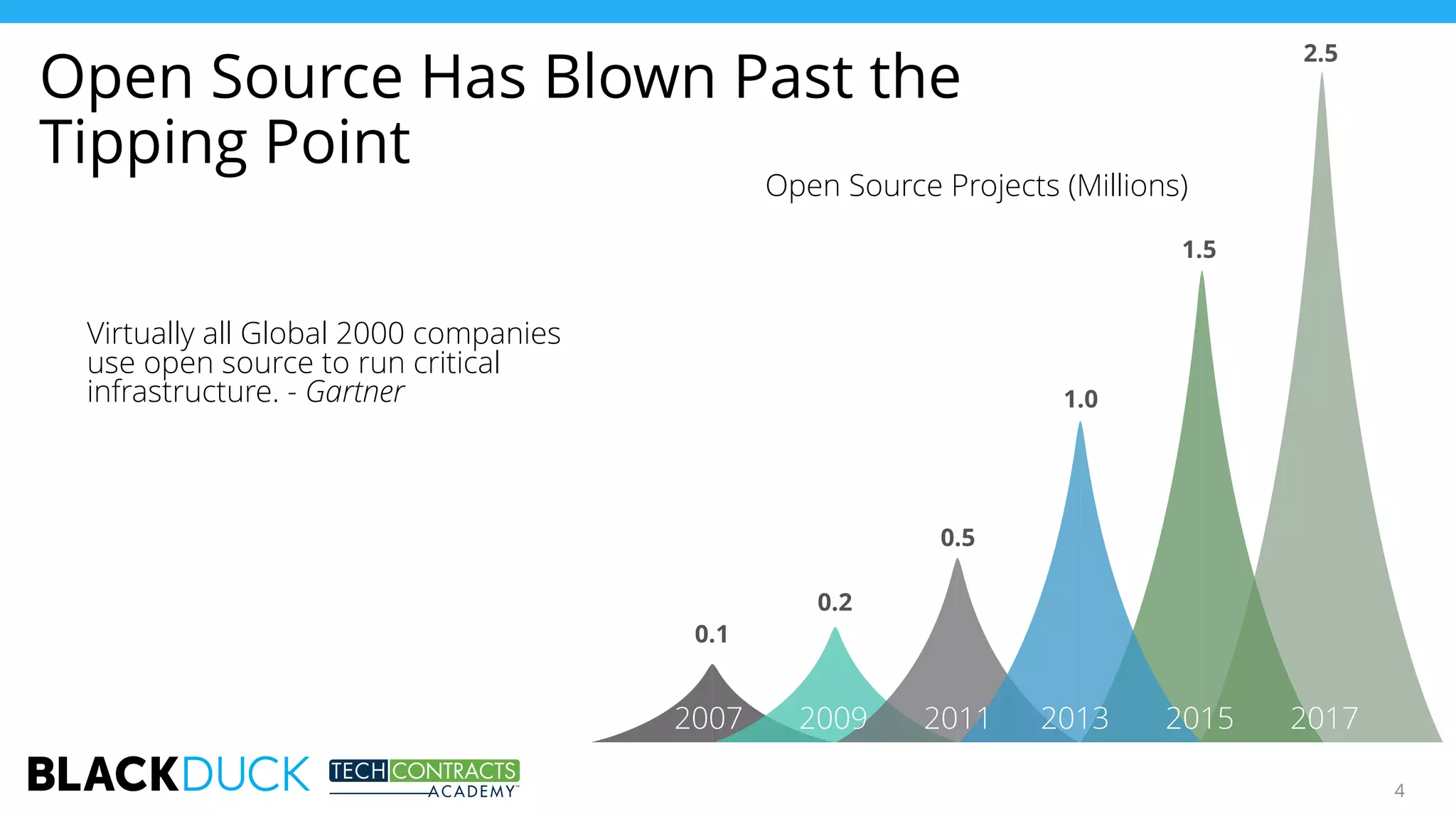
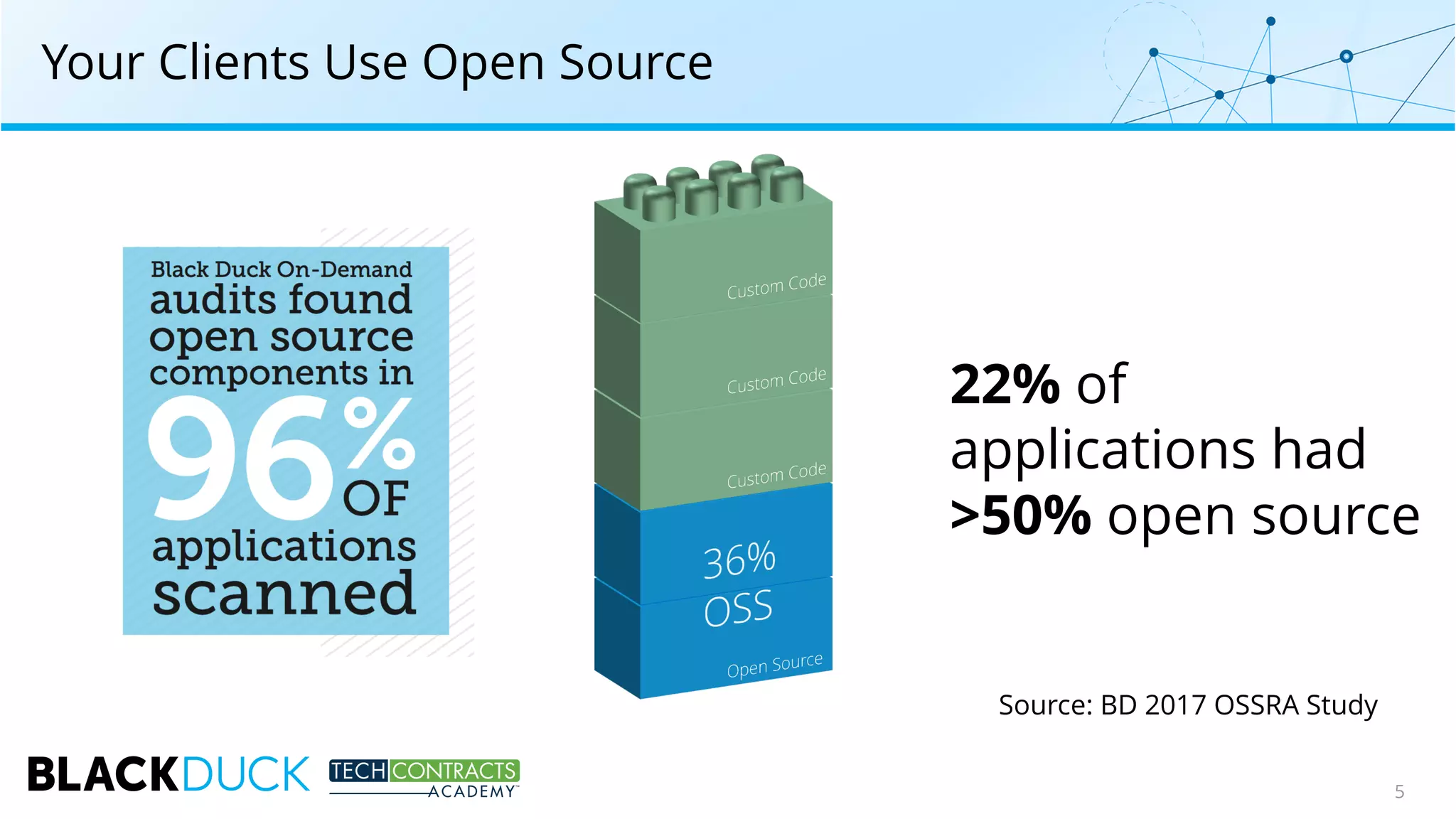
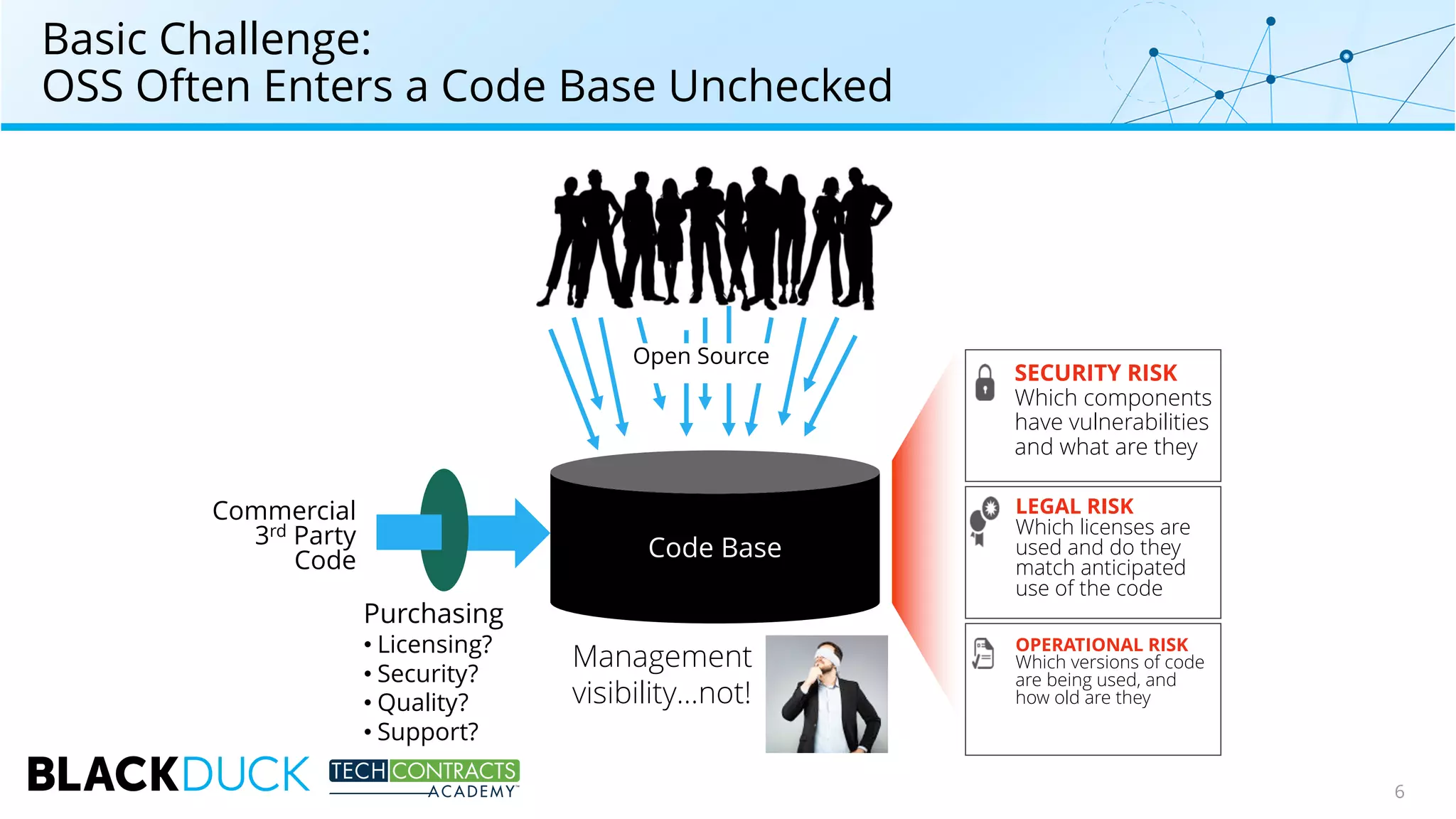
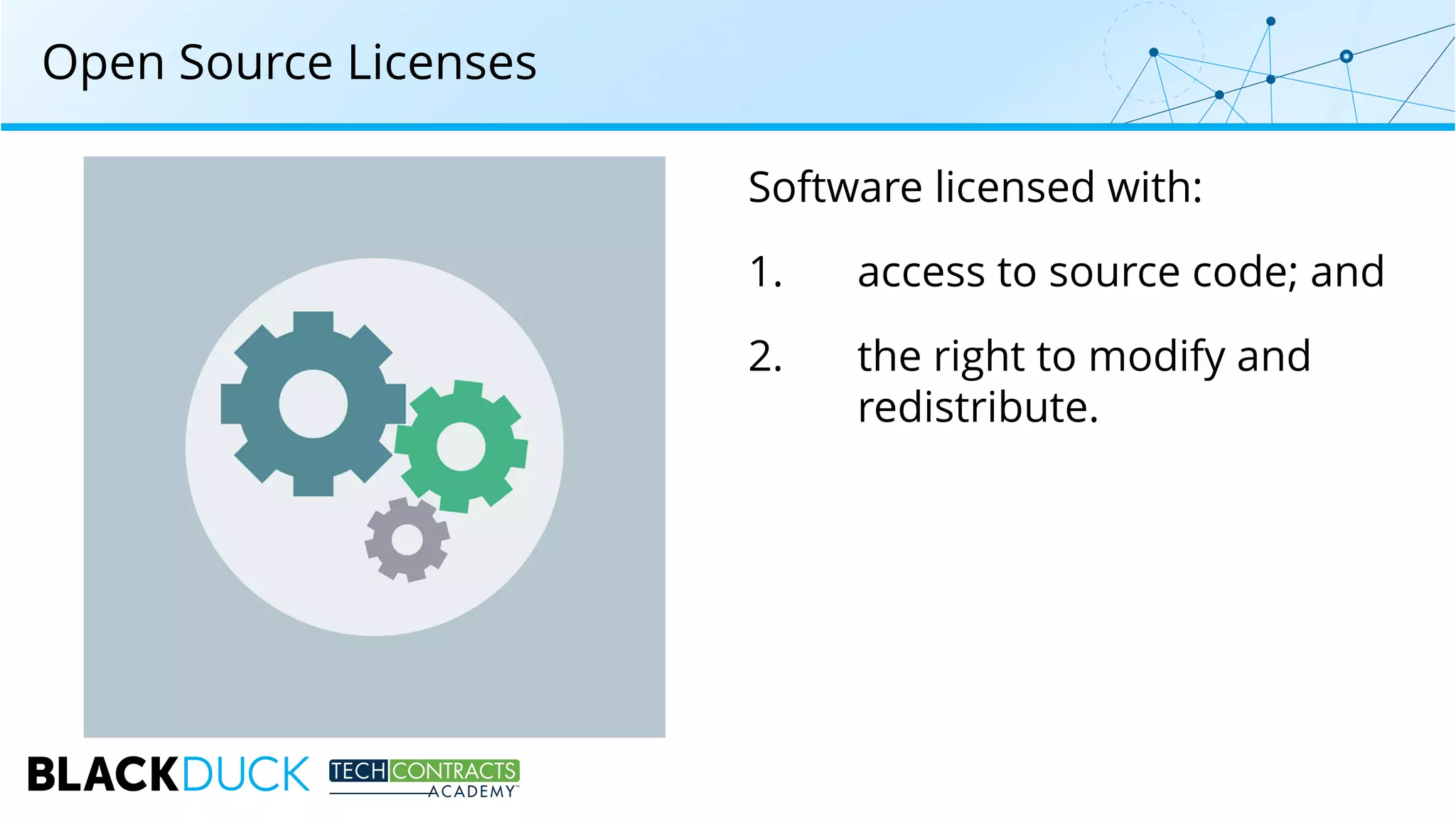
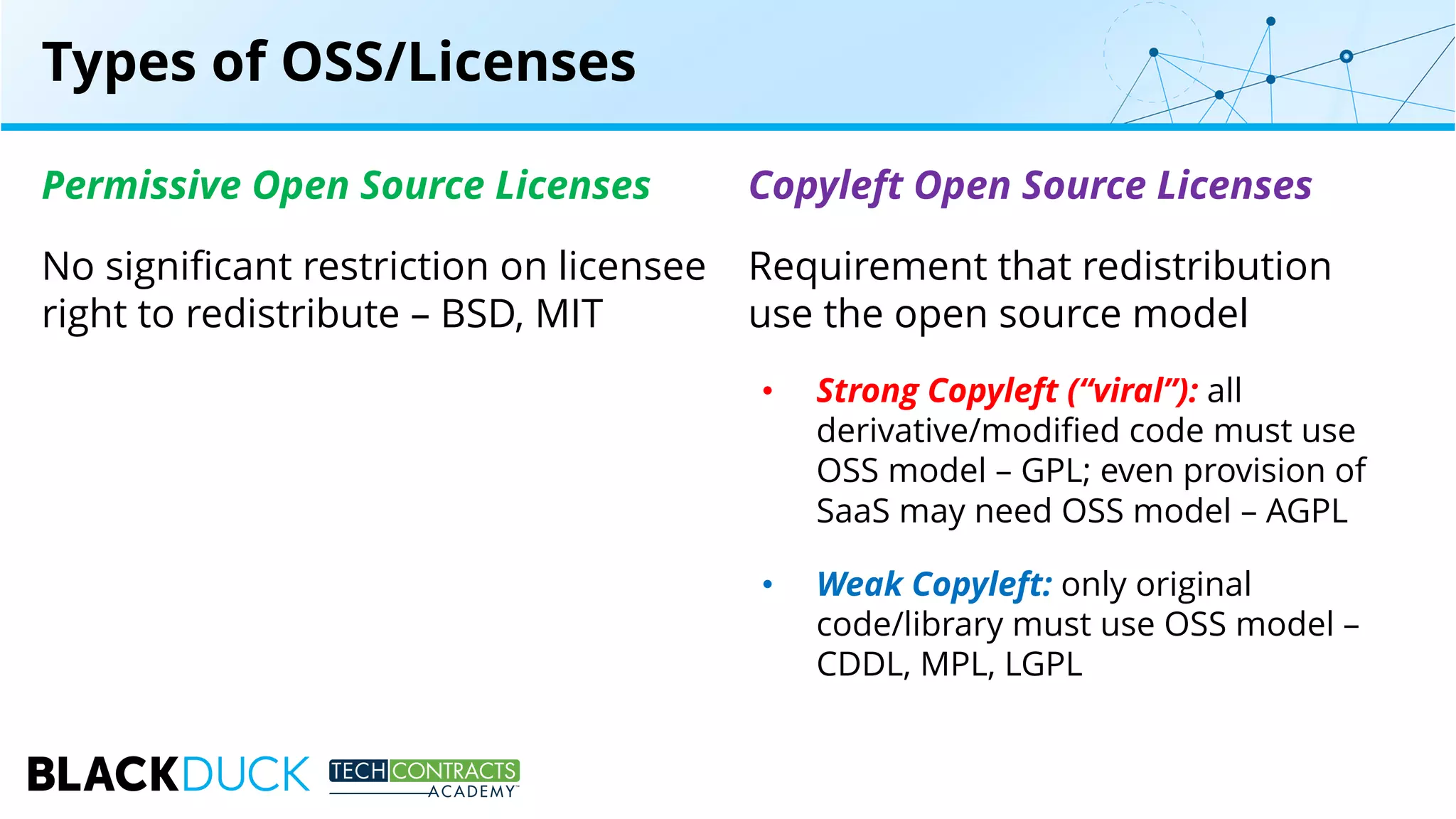
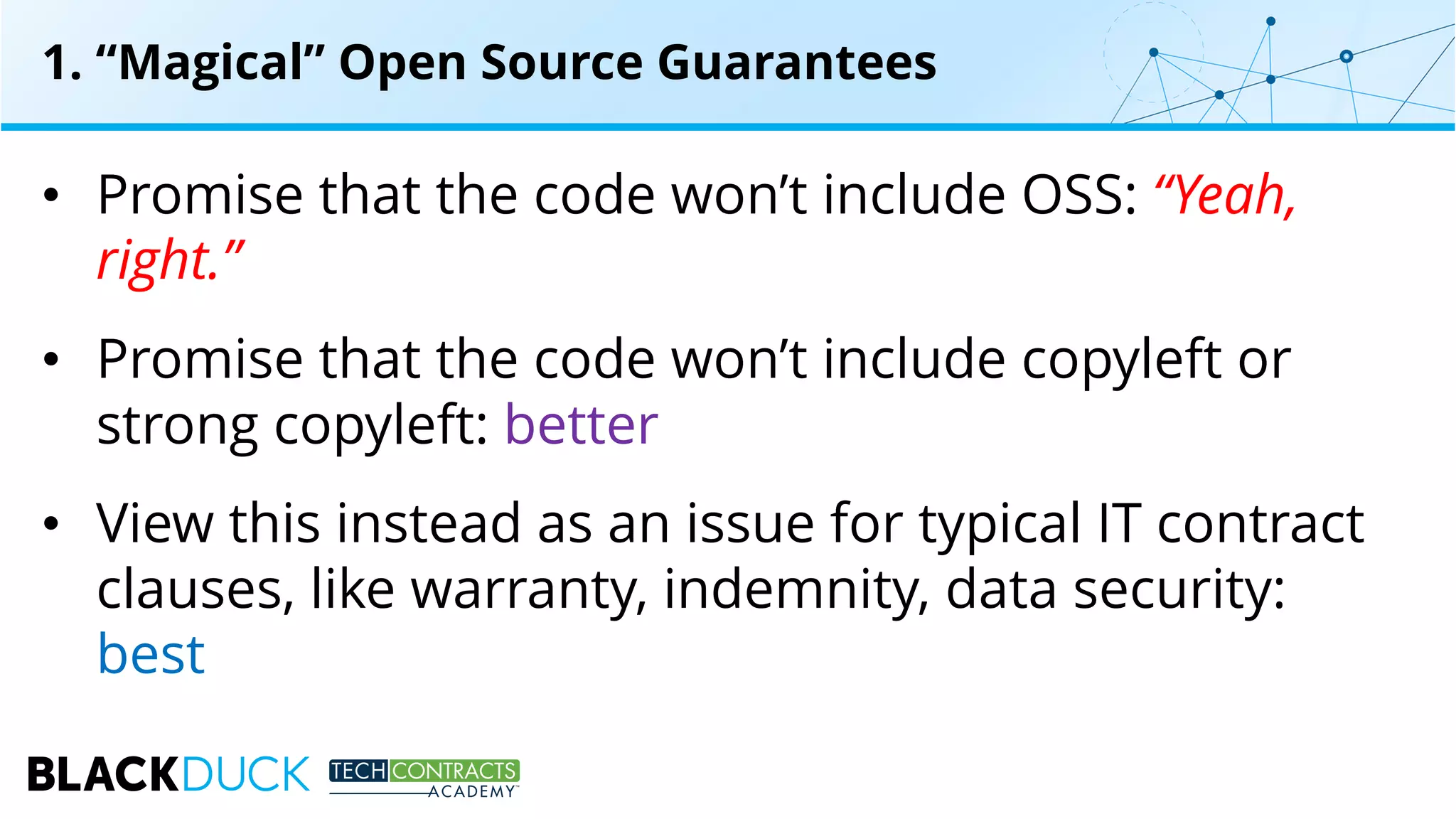
The document discusses the use of open source software in technology contracts, highlighting the risks and challenges related to licensing, security, and quality management. It emphasizes the importance of understanding open source licenses, particularly copyleft, and how they impact key contract clauses such as indemnity and liability. The speakers provide insights into effective governance practices for maximizing the benefits of open source while managing associated risks.