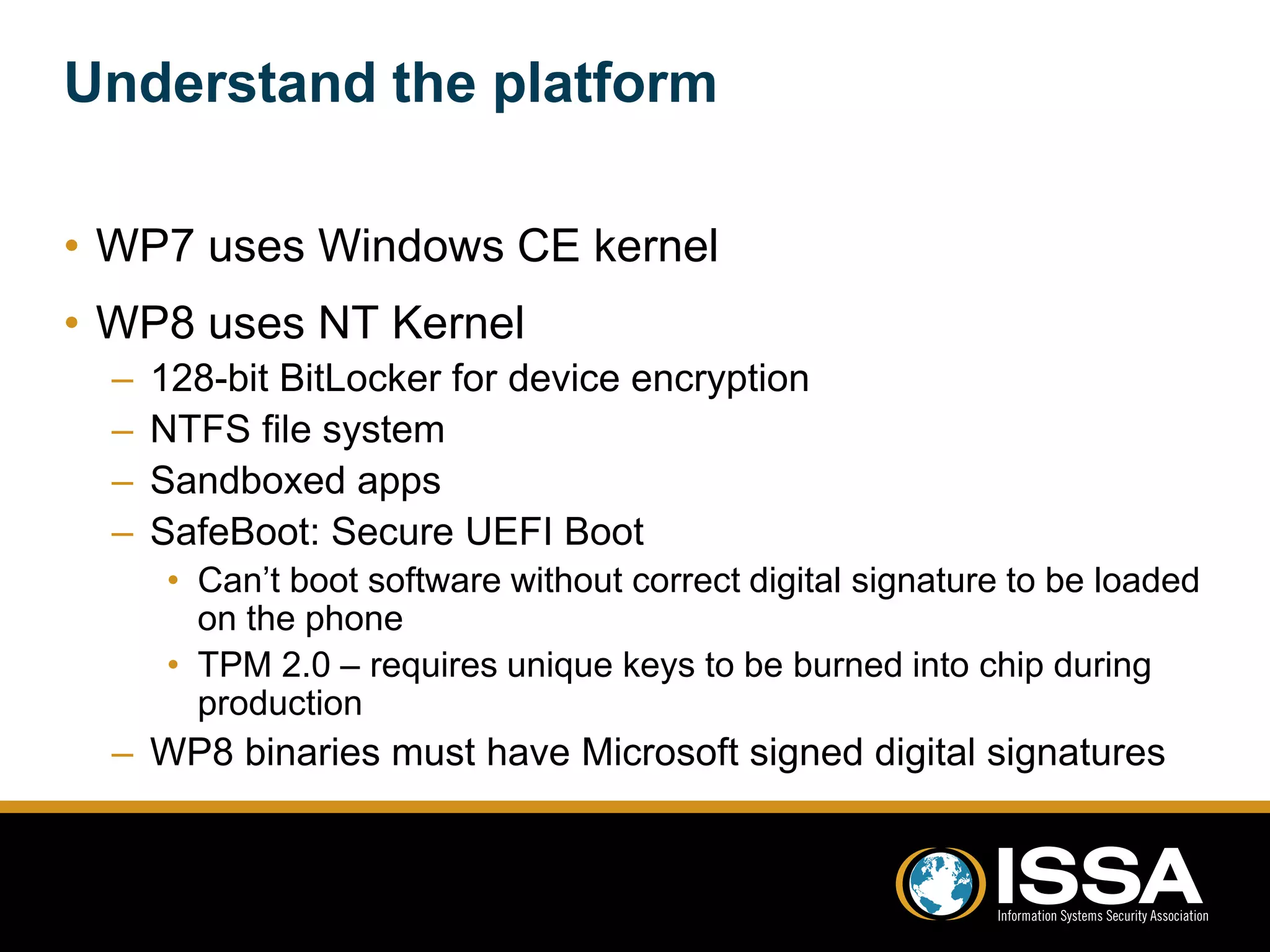
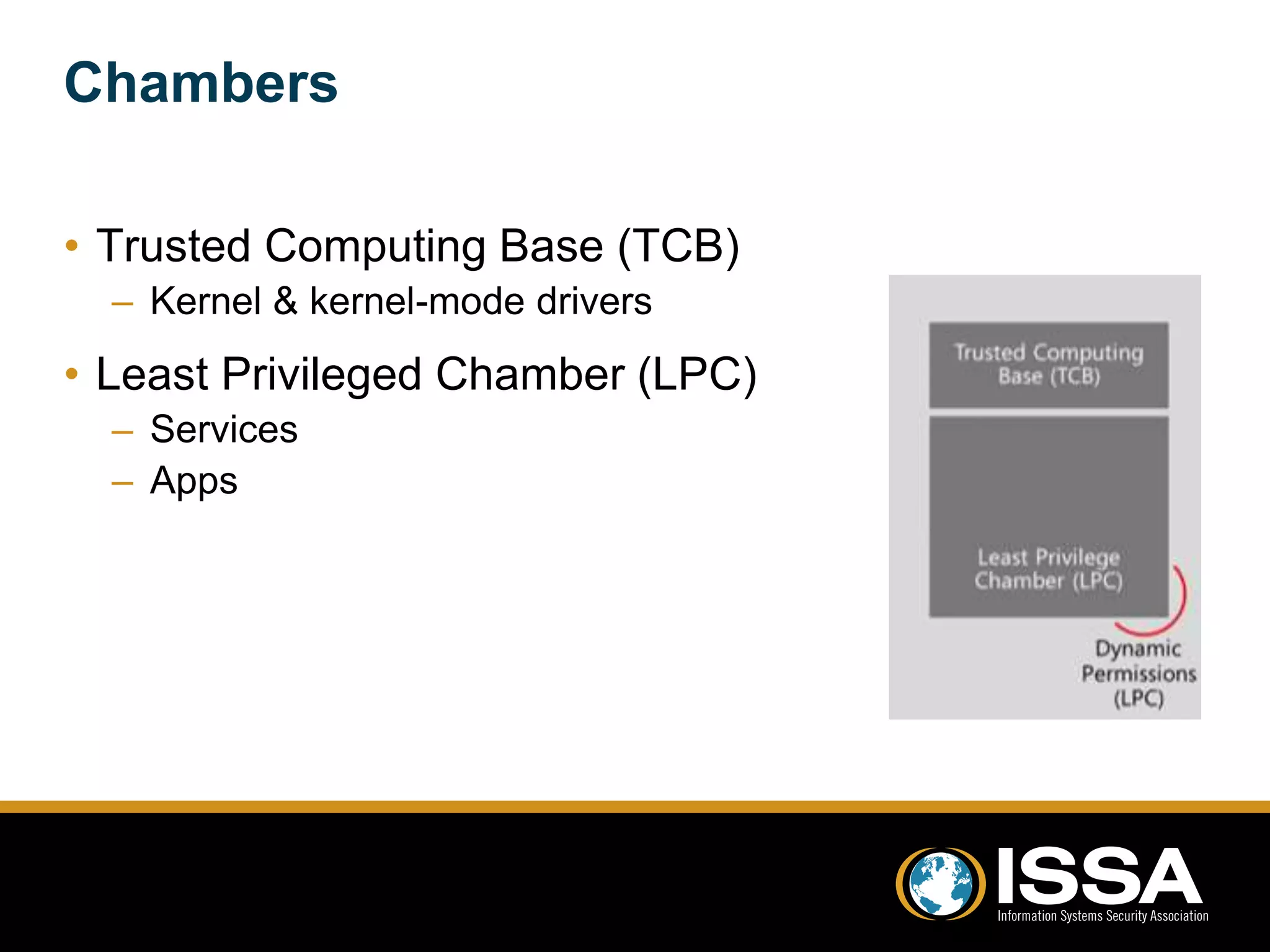
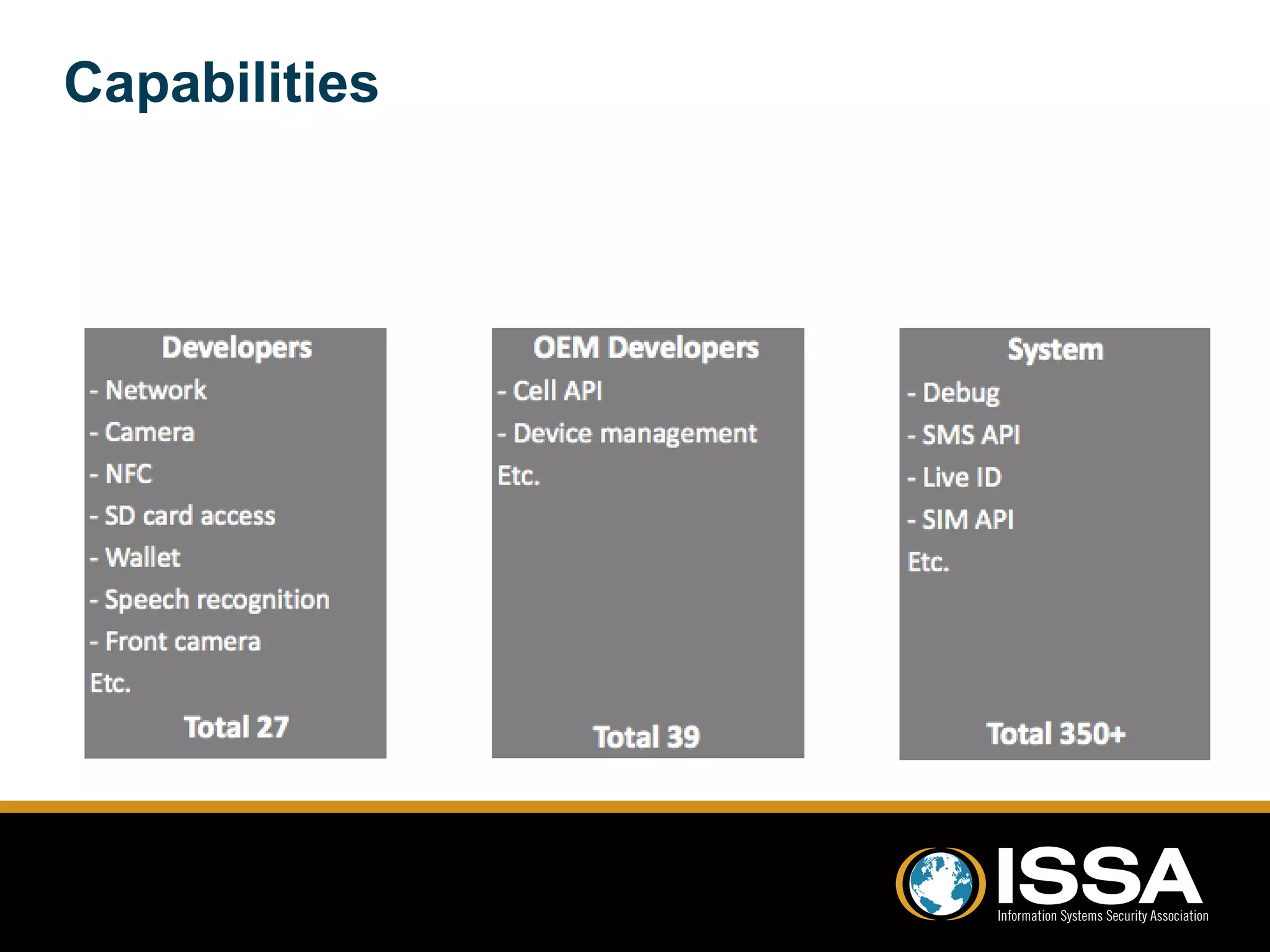
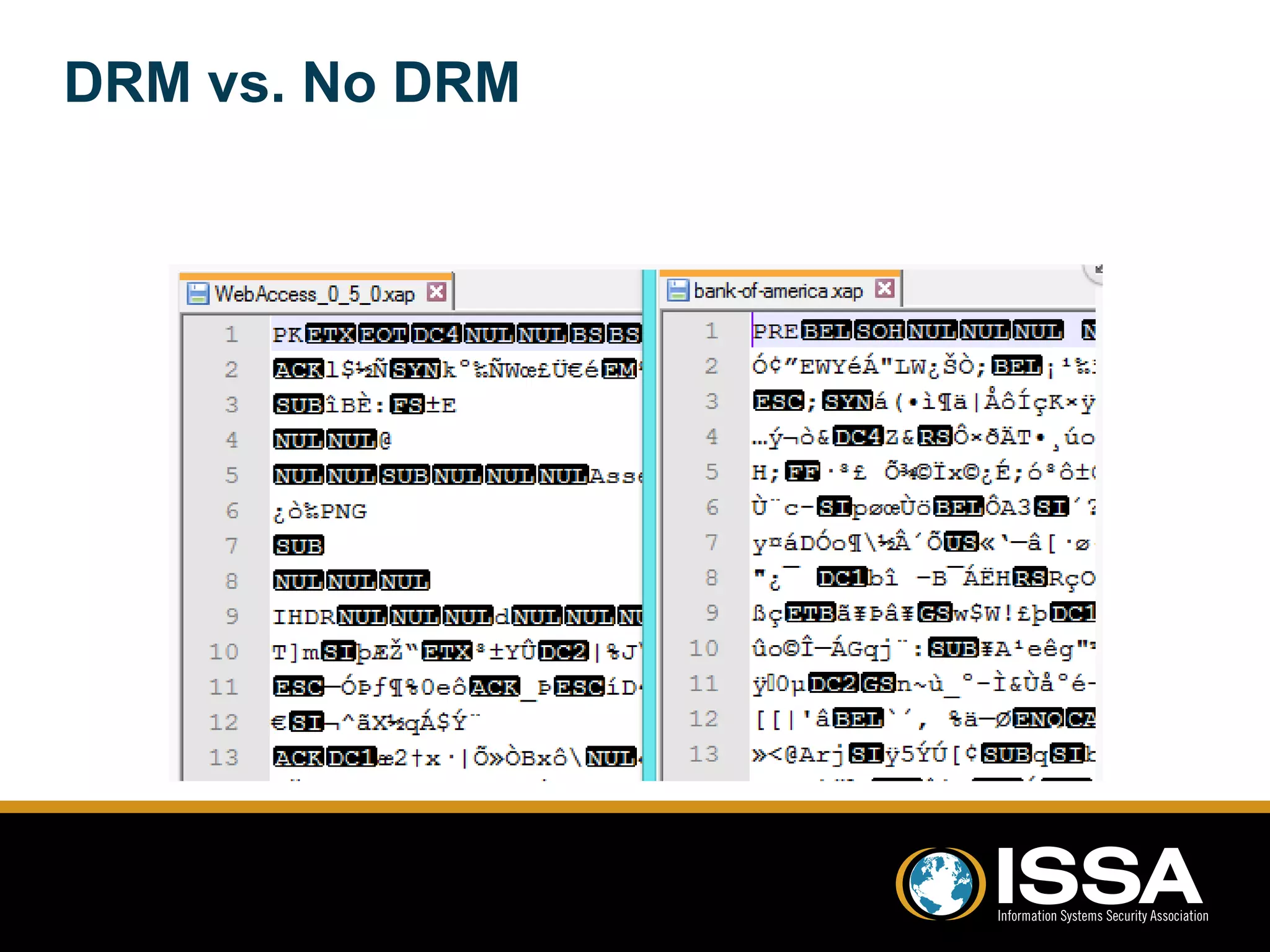
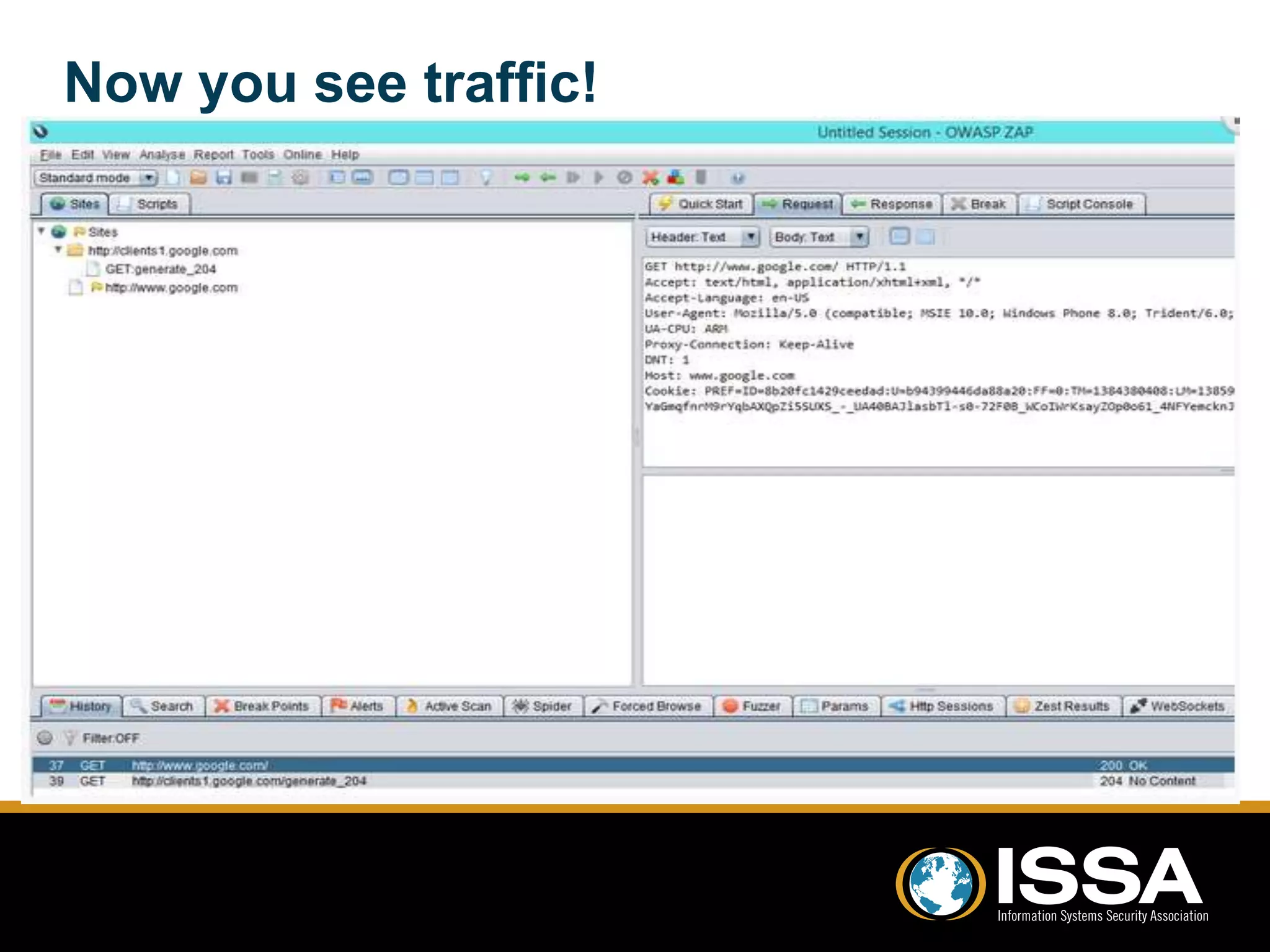
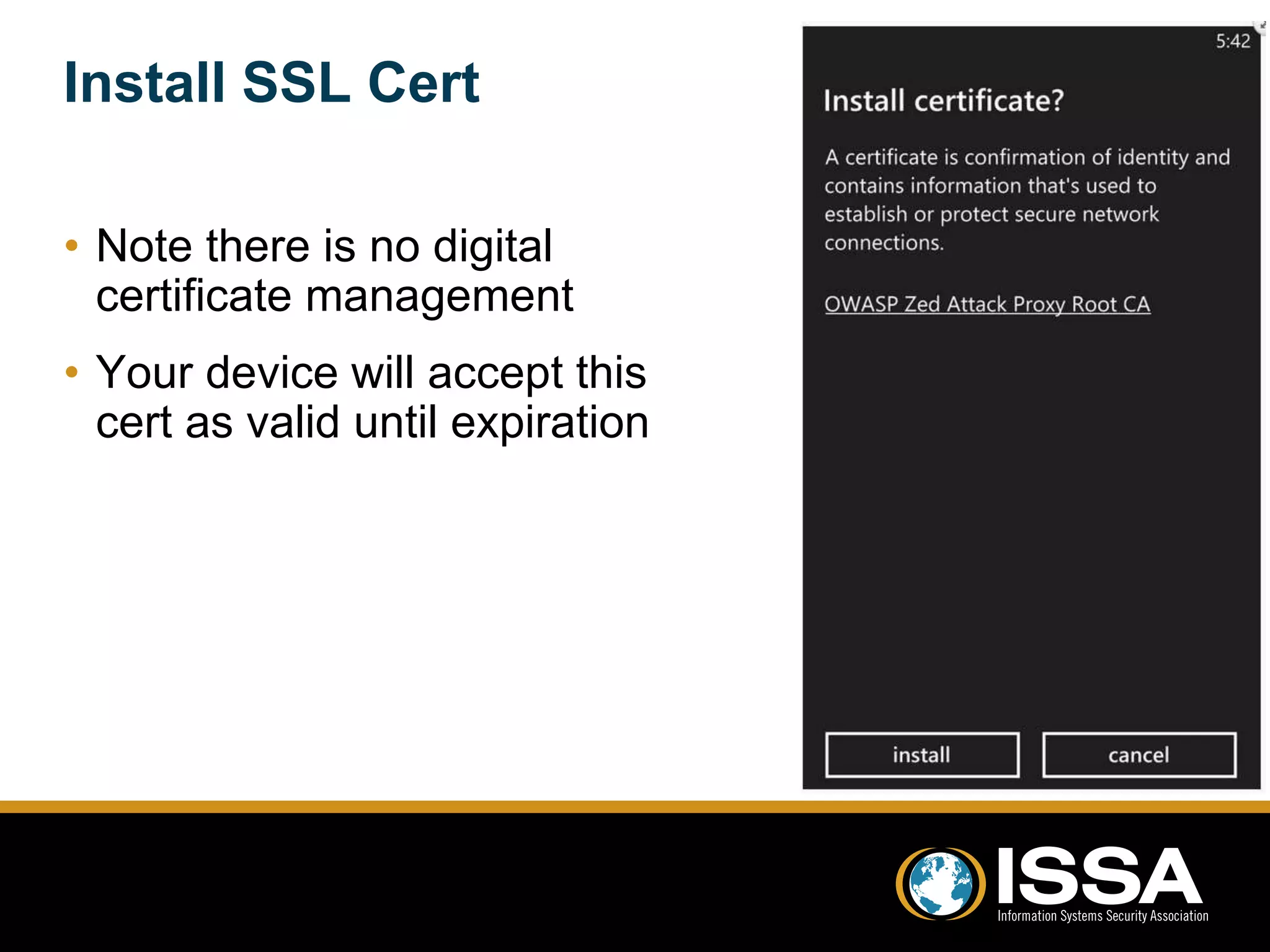
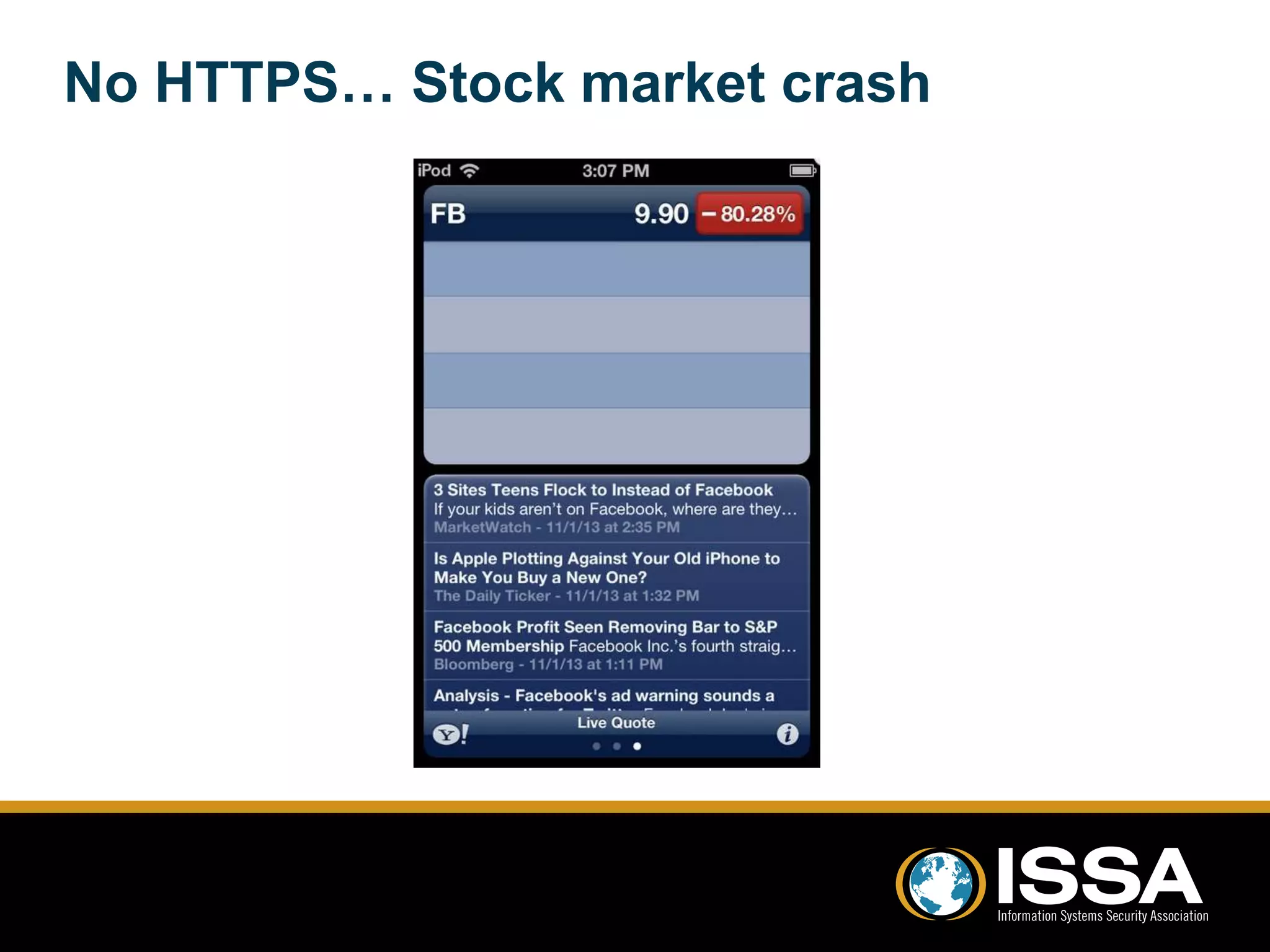
This document discusses security testing of Windows Phone 8 applications. It provides an overview of the Windows Phone 8 platform and architecture, including the use of the NT kernel and sandboxing of applications. Methods for testing applications are covered, including dynamic analysis using a proxy to view network traffic and static analysis by decompiling application files. Vulnerabilities that may be tested for are also outlined, such as lack of encryption or validation of certificates. The document concludes that while application testing depends on access to application files, server and client side testing is similar to other mobile platforms.