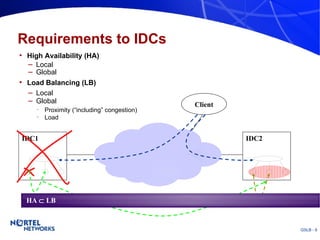
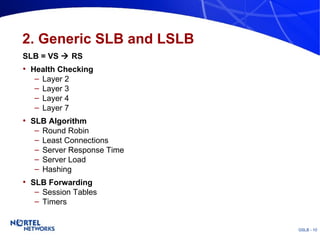
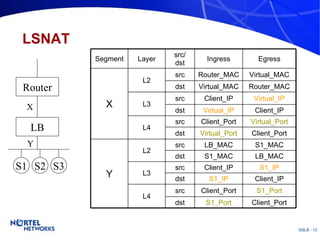
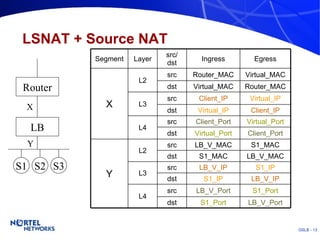
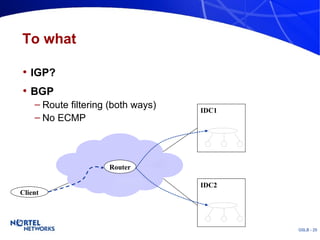
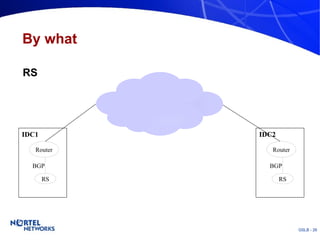
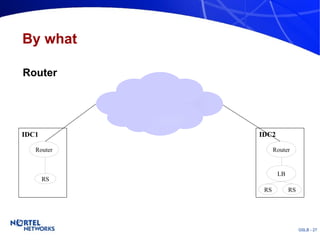
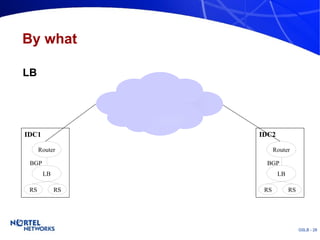
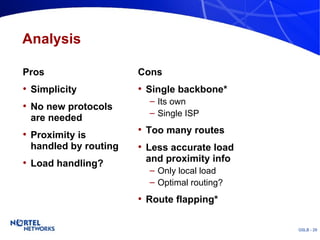
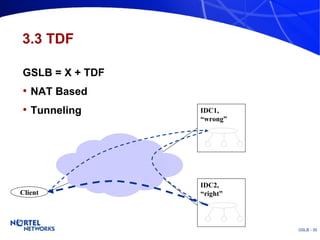
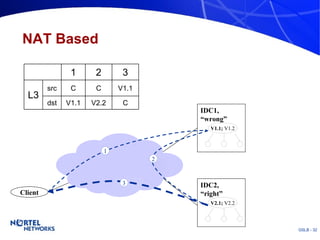
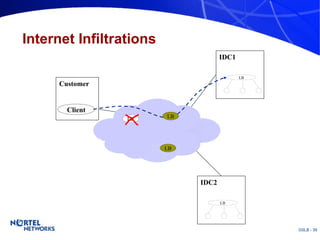
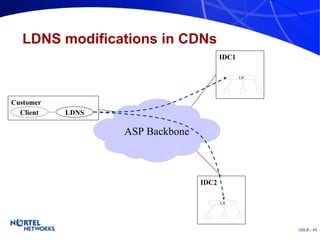
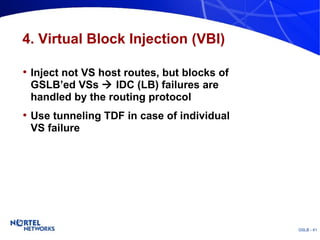
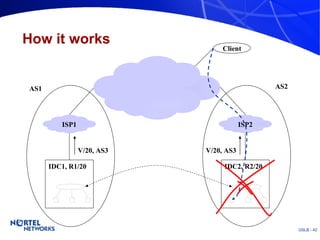
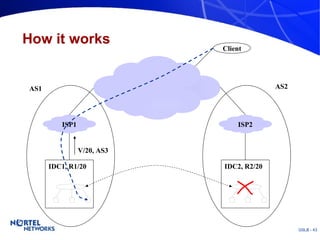
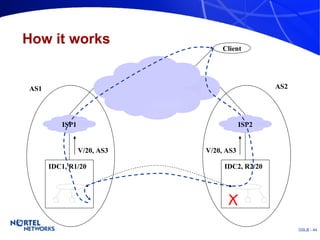
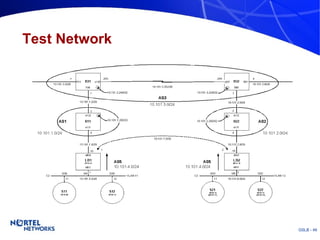
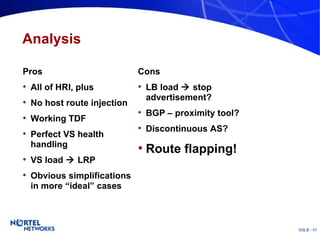
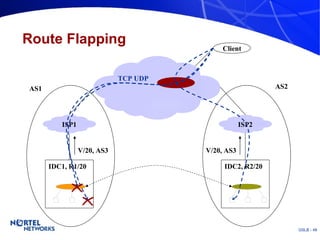
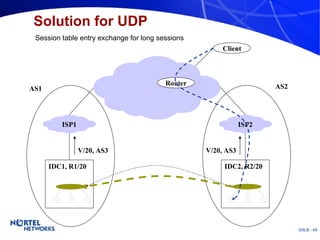
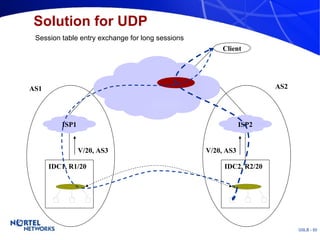
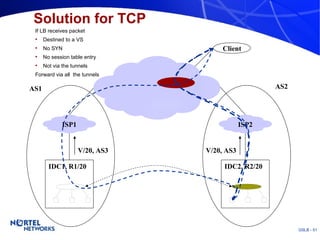
The document discusses various techniques for global server load balancing (GSLB) including DNS-based methods, host route injection (HRI), and a new proposed technique called virtual block injection (VBI). It outlines the requirements for internet data centers (IDCs), describes existing GSLB methods and their pros and cons, and analyzes the potential benefits and limitations of the VBI approach. The document concludes that no single method is ideal and the best solution depends on the specific network scenario.
![Global Server Load Balancing Dima Krioukov [dima@nortelnetworks.com] Alex Kit [akit@winstar.com] October 24, 2000](https://image.slidesharecdn.com/title-subtitle3254/75/Title-Subtitle-1-2048.jpg)