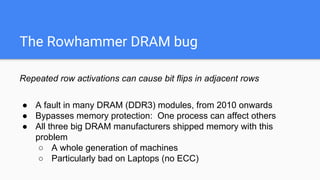
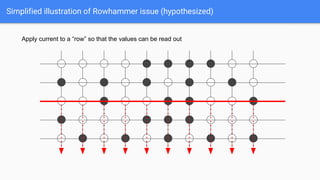
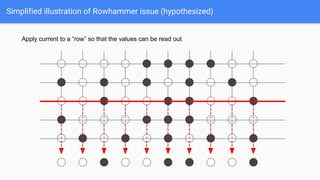
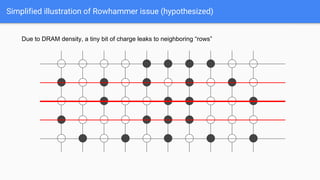
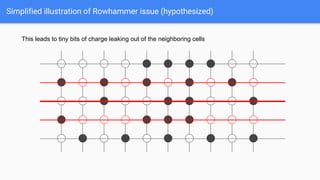
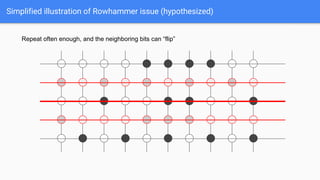
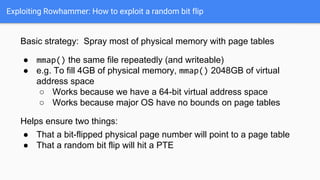
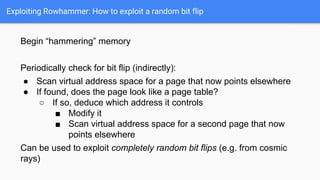
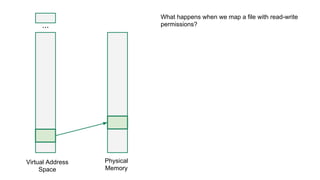
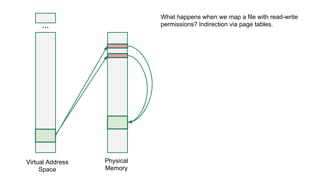
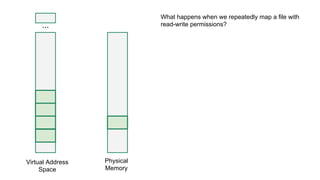
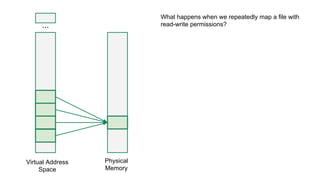
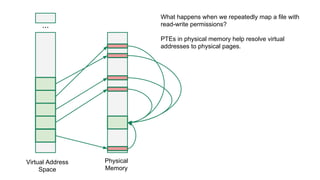
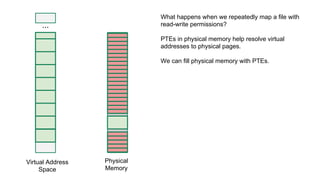
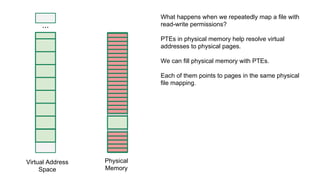
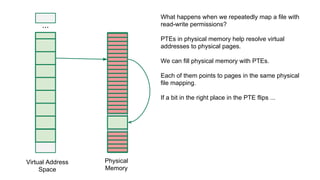
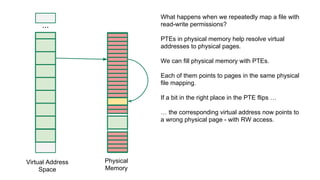
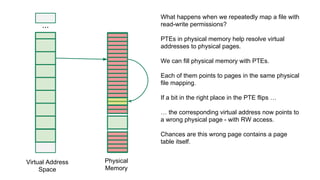
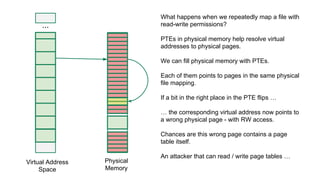
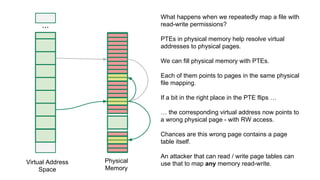
The document discusses the Rowhammer DRAM bug, which involves repeated row activations causing bit flips in adjacent rows, leading to memory exploitation and privilege escalation across major operating systems. It highlights the implications of Rowhammer for future security research, emphasizing the need for a theoretical understanding of exploitation, collaboration across disciplines, and a focus on building inspectable systems. The author suggests that even minor faults in hardware can lead to significant security vulnerabilities, urging researchers to investigate these issues further.