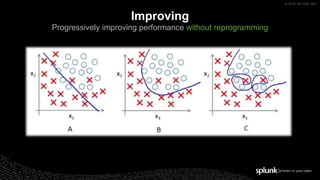
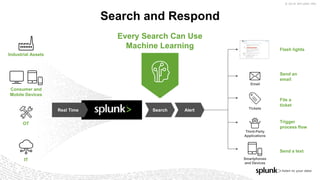
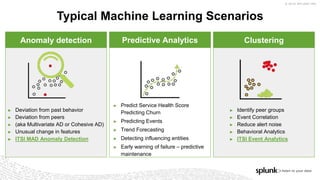
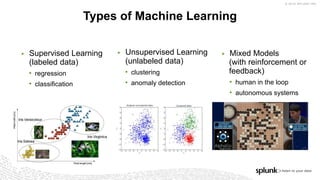
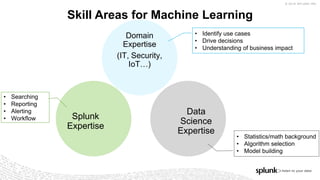
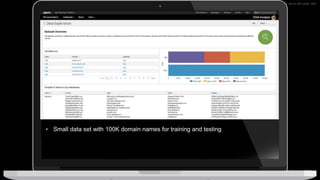
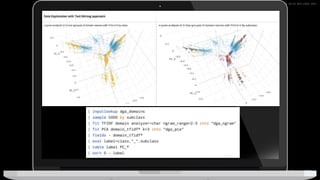
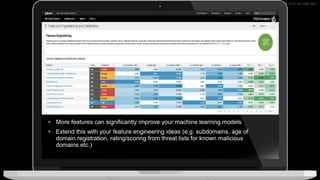
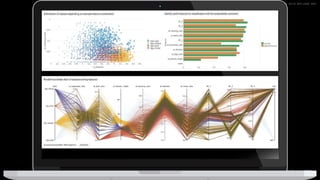
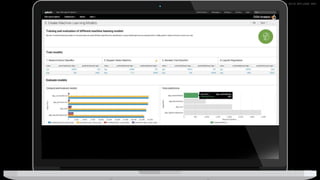
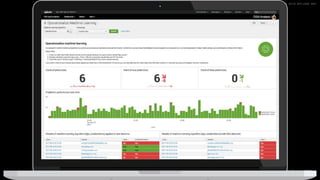
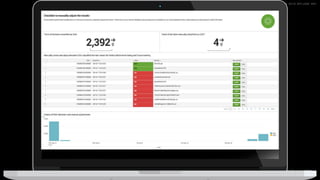
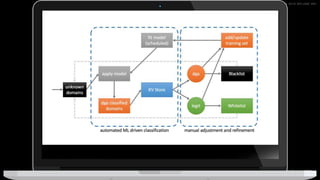
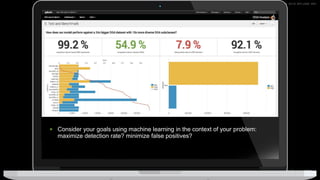
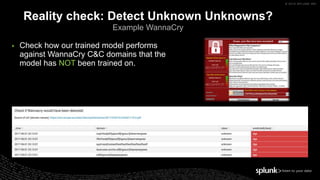
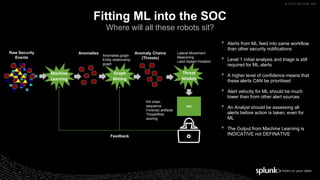
The document discusses machine learning in security and provides examples of its applications. It begins with defining machine learning and explaining how it can augment security investigations by enabling bulk data analysis, anomaly detection, and focusing analyst time. The document then discusses common machine learning techniques and use cases in security domains like fraud detection and insider threat. It also provides a worked example of using machine learning to detect domain generation algorithms (DGAs). Finally, it discusses best practices for integrating machine learning into existing security operations center workflows and processes.