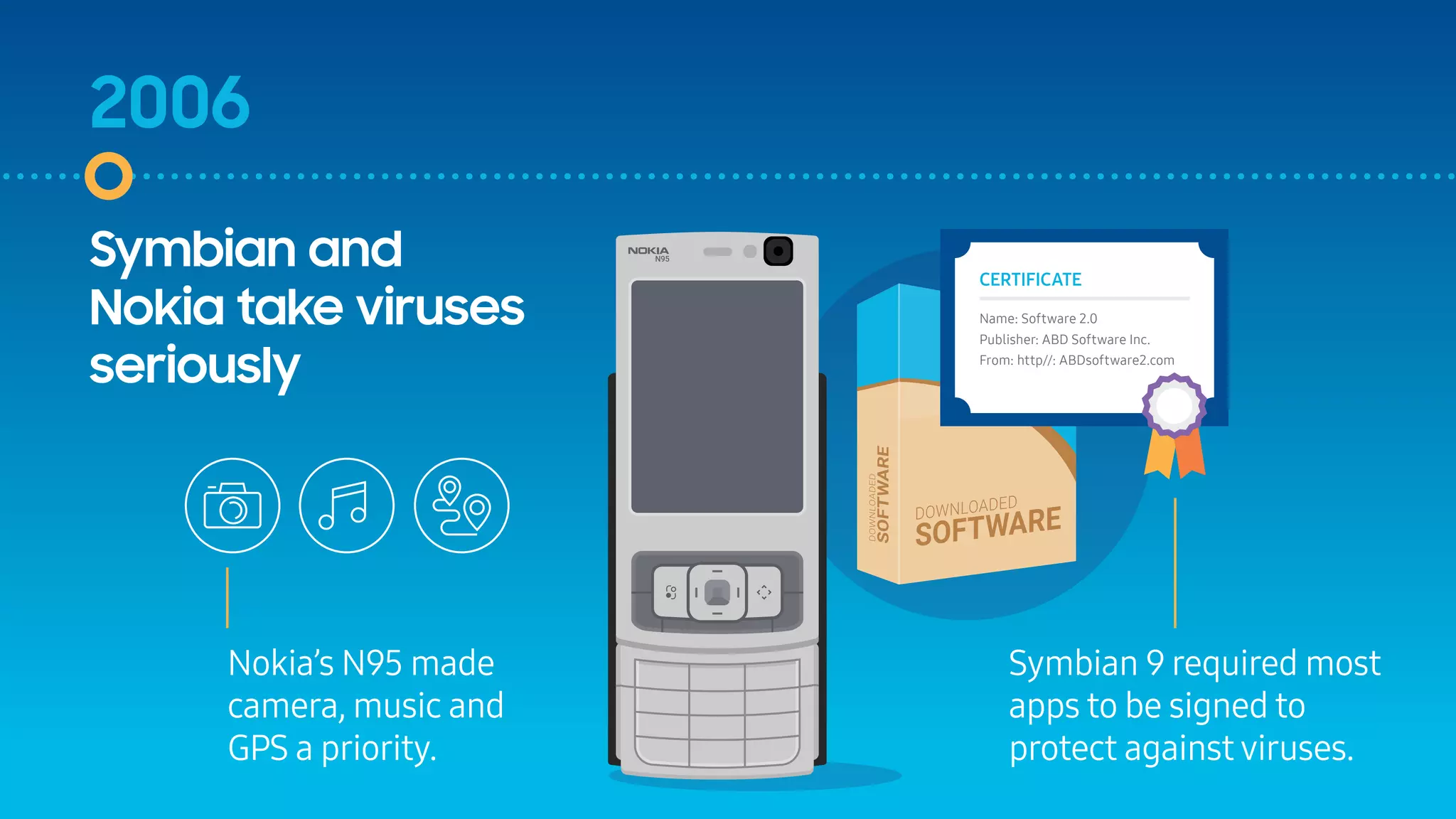
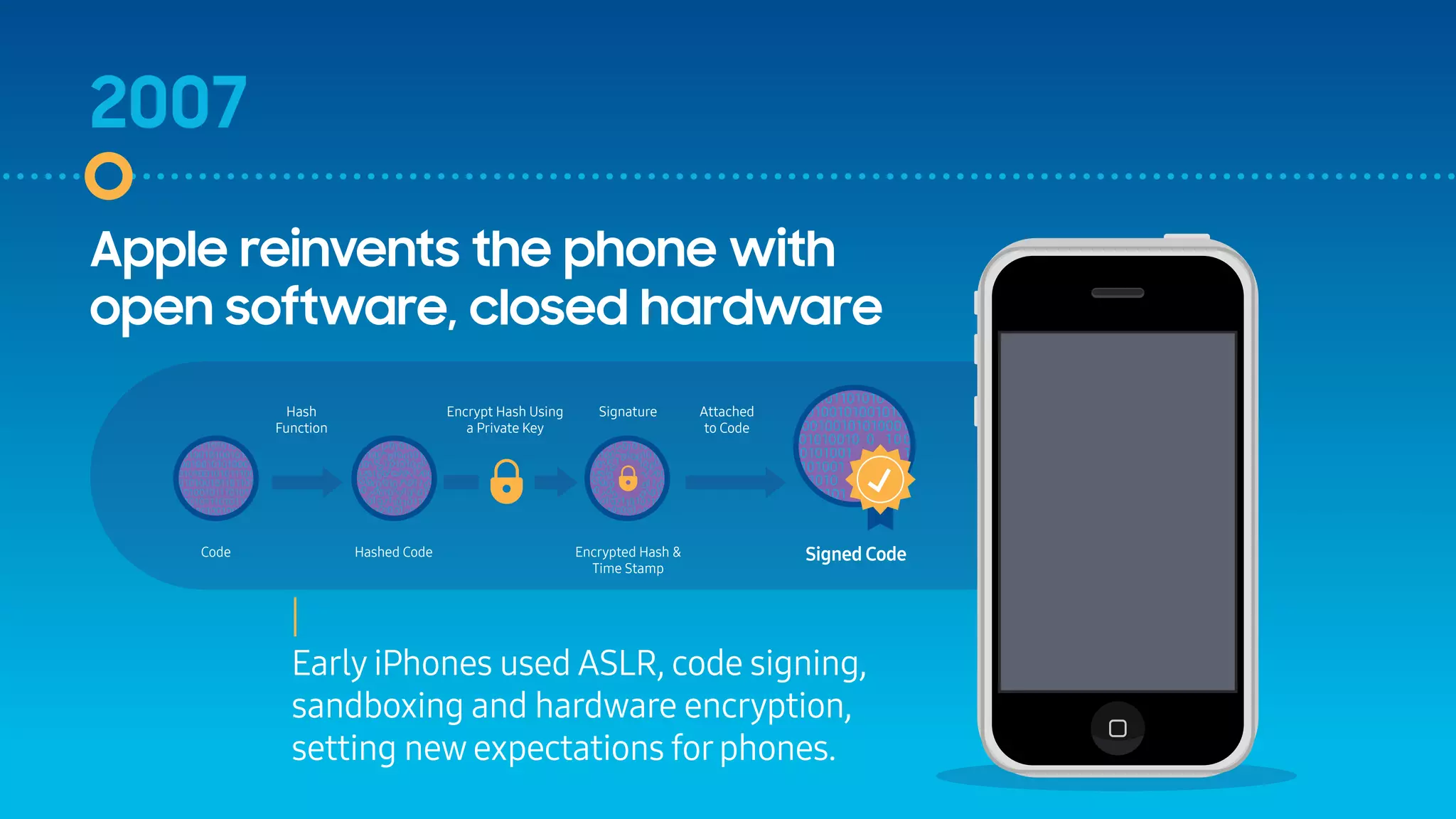
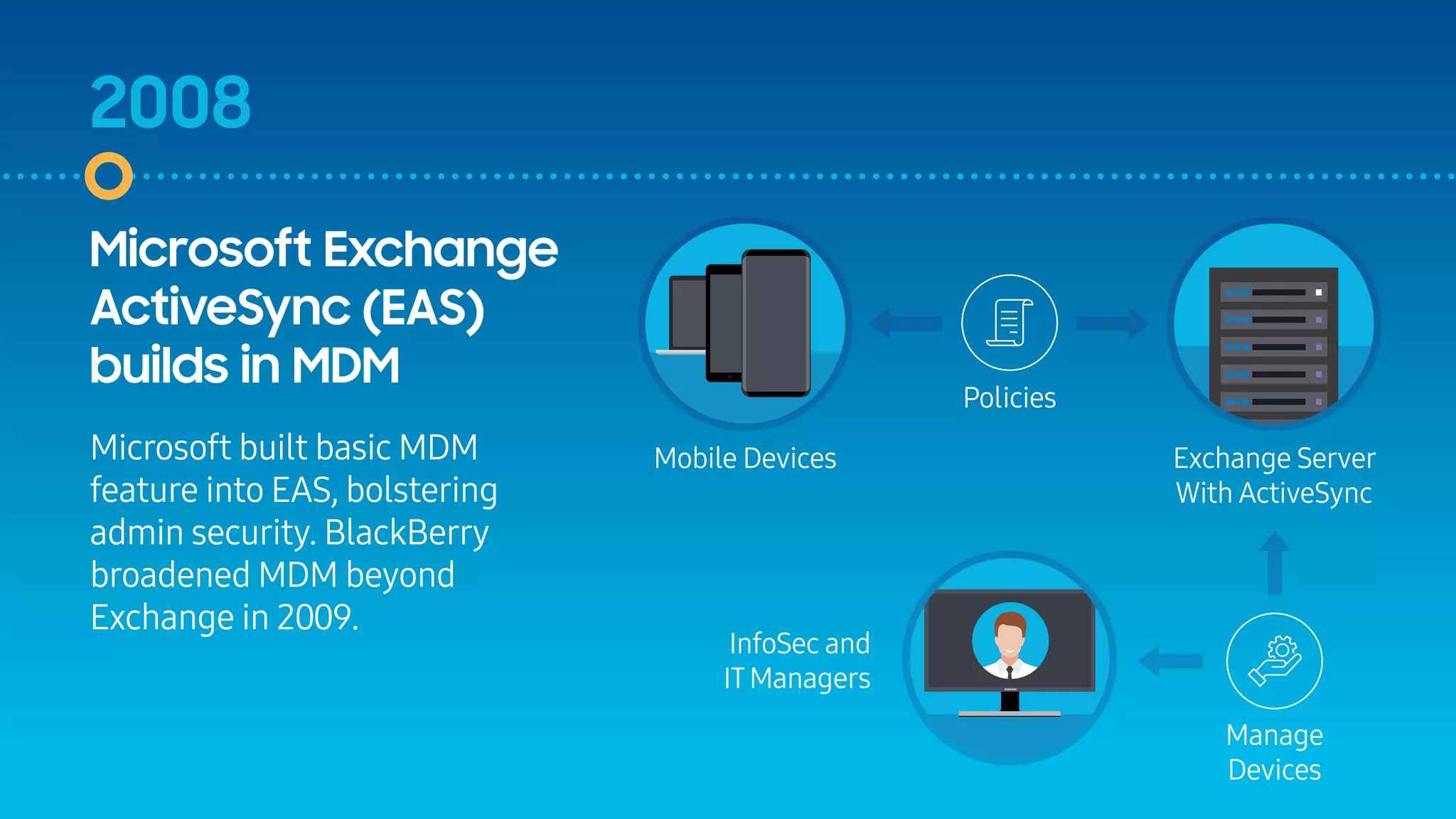
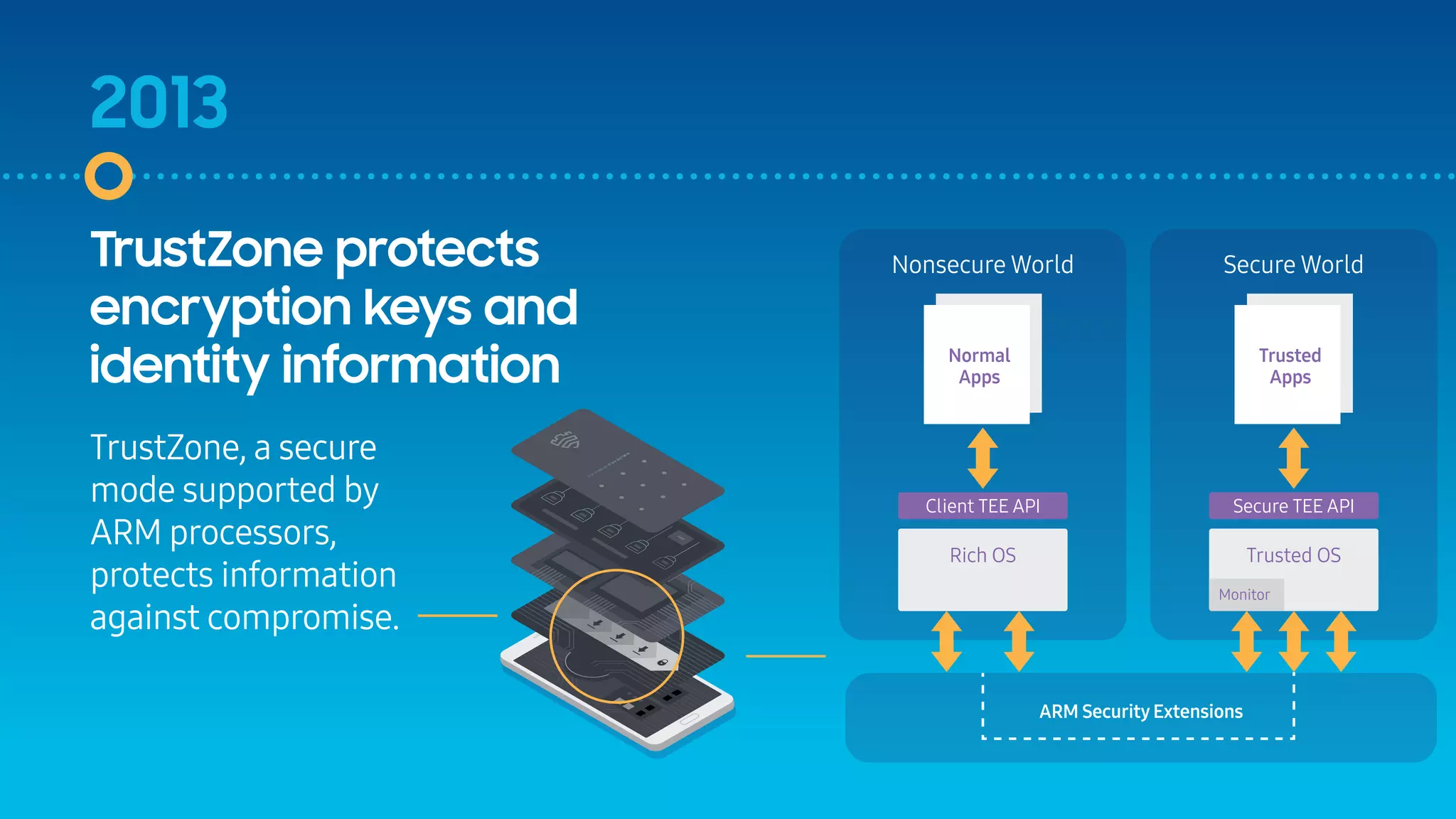
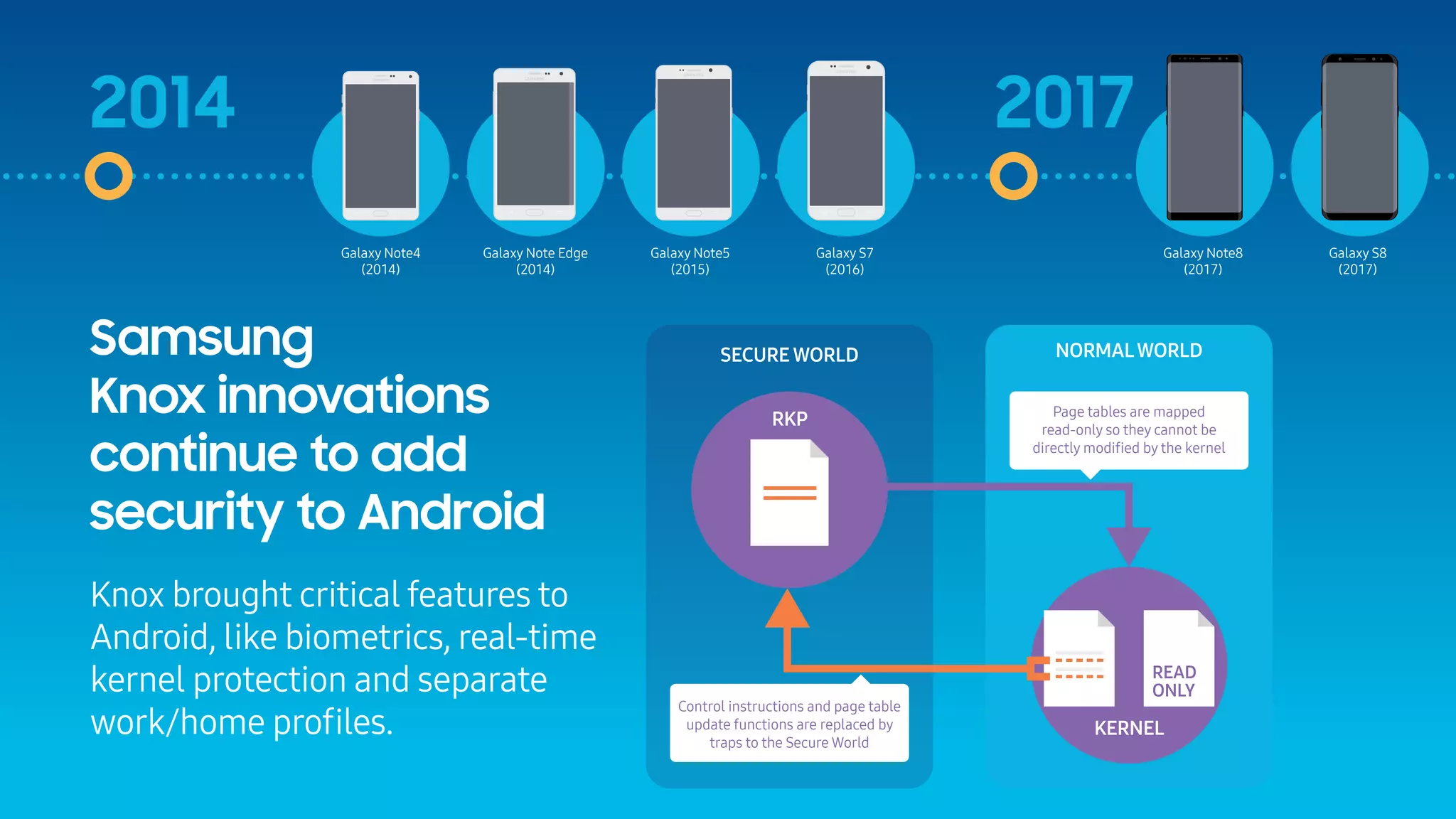
The document outlines the evolution of mobile security over fifteen years, highlighting significant developments from the emergence of the first smartphones to the advancements in security features like Samsung Knox. It discusses the introduction of various security measures, including code signing, MDM, and secure modes like TrustZone in response to increasing threats. The document emphasizes Samsung Knox's role in fortifying Android security for enterprise environments.