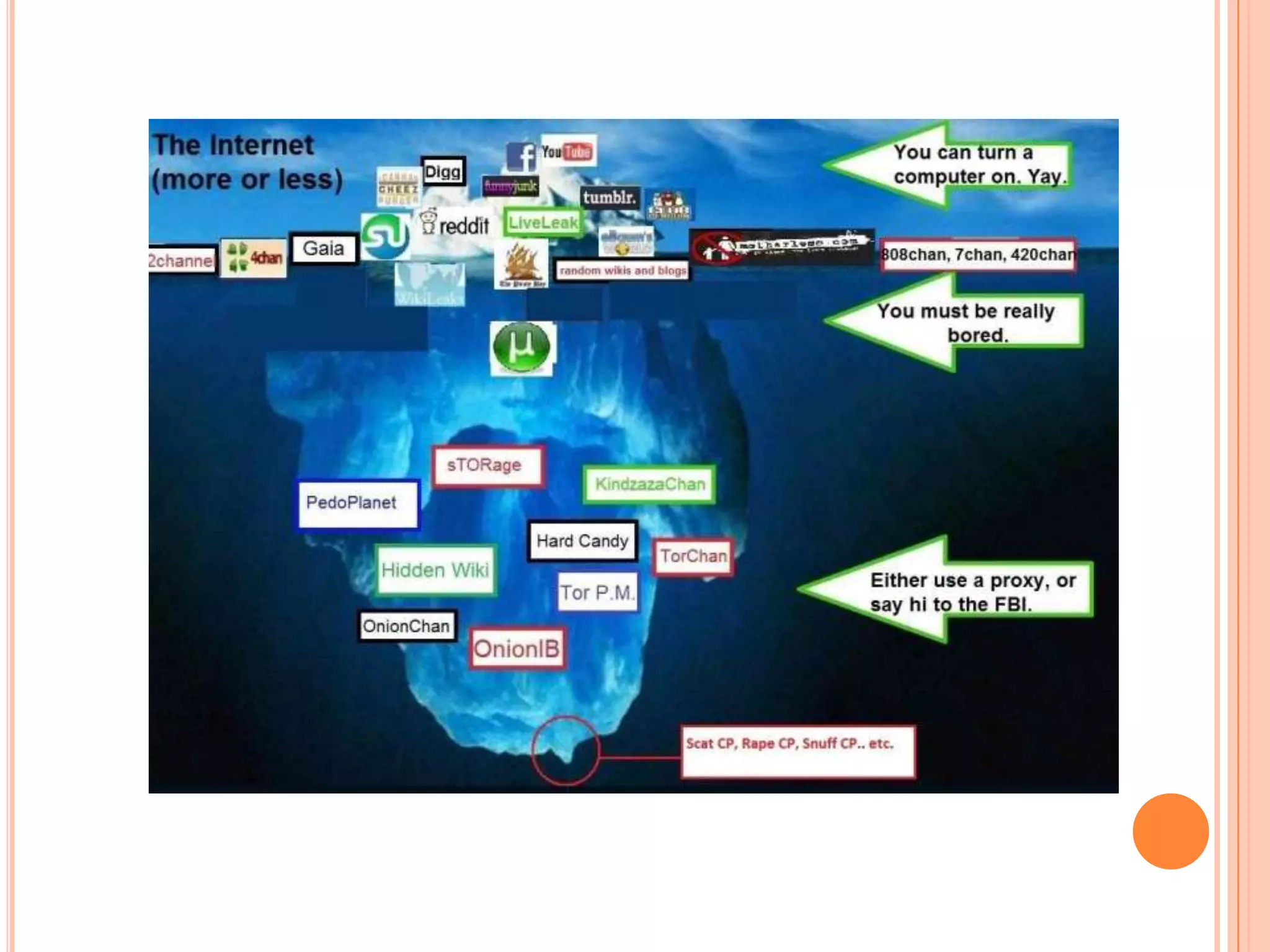
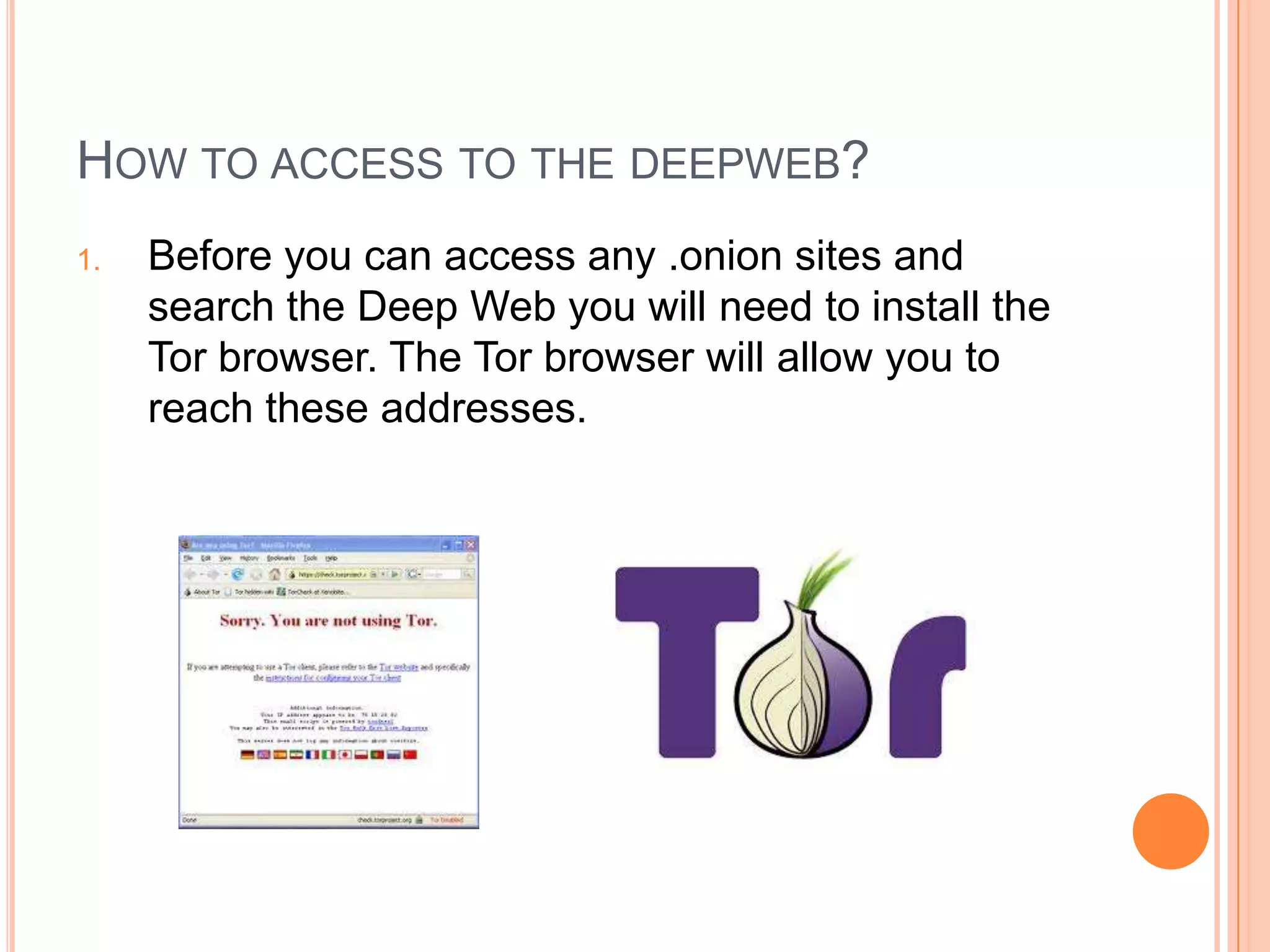
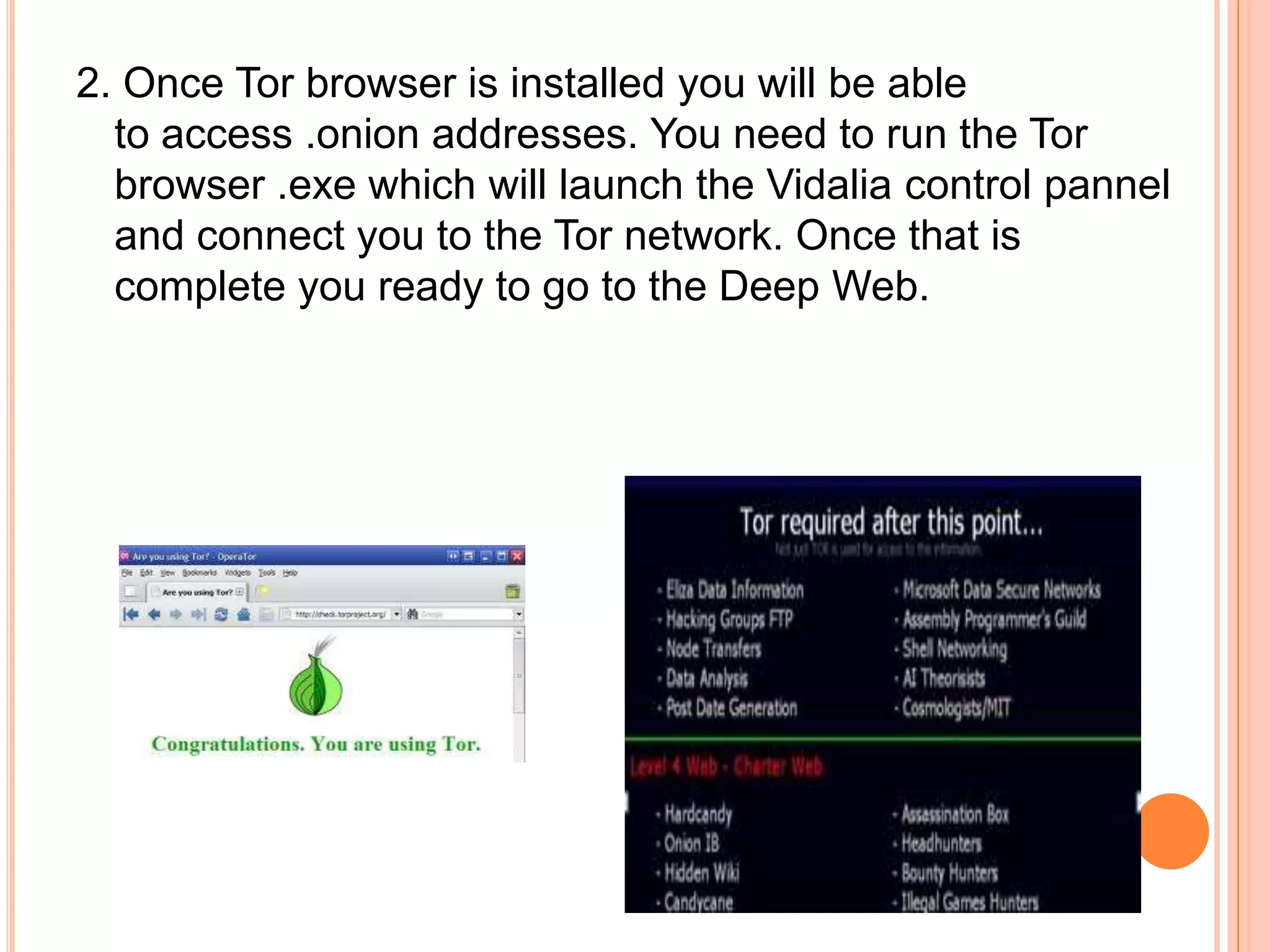
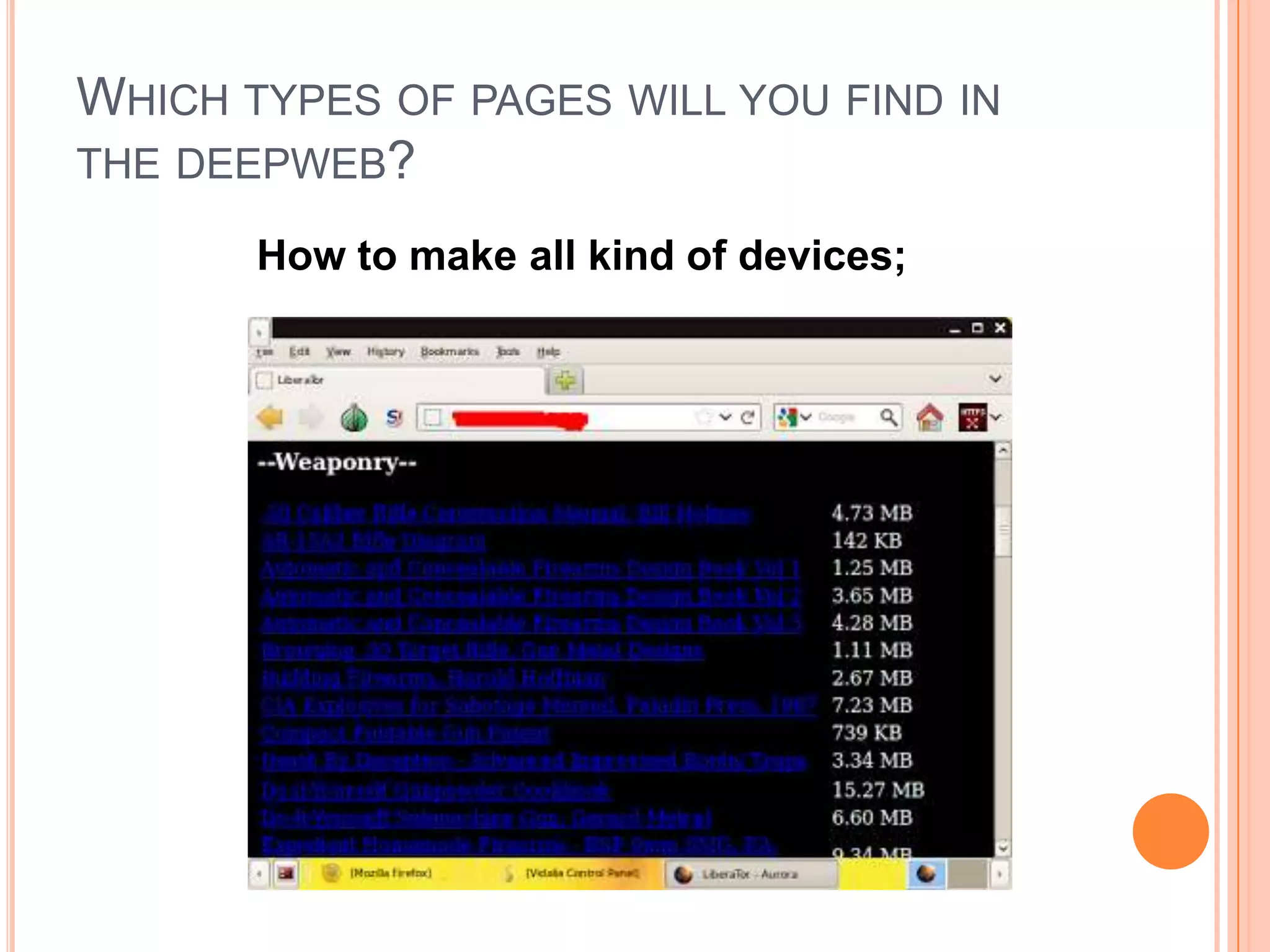
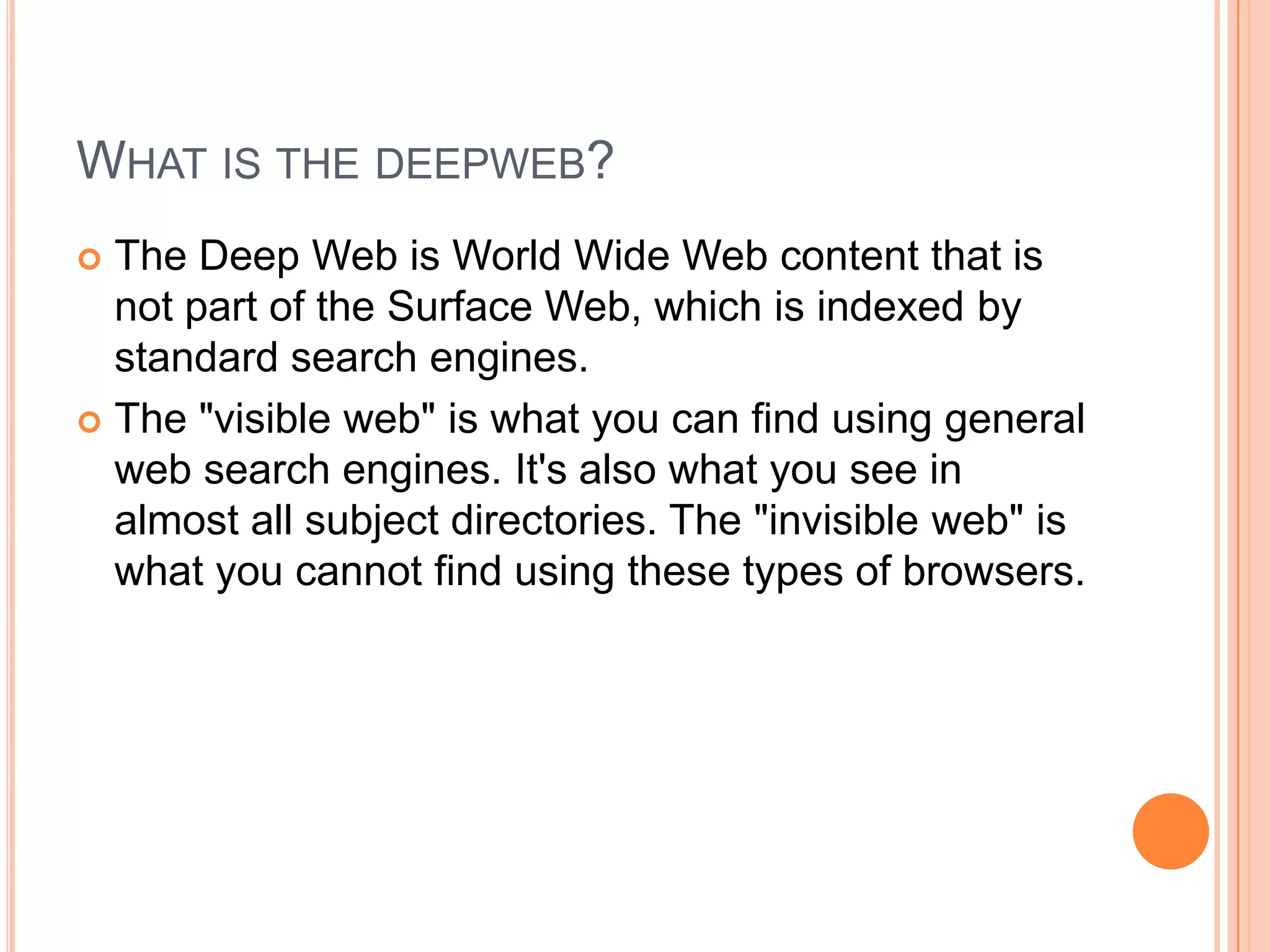
The deep web, also known as the invisible web, contains content that is not indexed by traditional search engines. It consists of an estimated 7,500 terabytes of information, including over 300,000 websites. To access the deep web, one must install the Tor browser to reach .onion addresses and access content like instructions on making devices, discussion forums, marketplaces, and information on Bitcoin, which allows anonymous possession and transfer of value.

![SIZE
Estimates based on extrapolations from a study
done at University of California, Berkeley in
2001,[3] speculate that the deep Web consists of
about 7,500 terabytes. More accurate estimates are
available for the number of resources in the deep
Web: research led by Microsoft and IBM detected
around 300,000 deep web sites in the entire Web in
2004,[4] and, according to Shestakov, around
14,000 deep web sites existed in the Russian part
of the Web in 2006.](https://image.slidesharecdn.com/thedeepweb-130919150849-phpapp01/75/The-deepweb-4-2048.jpg)