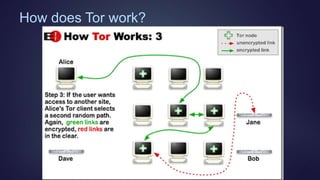
The document provides an overview of the darknet and the invisible web, including how search engines operate and the distinction between the visible and invisible web. It explores tools like Tor and I2P for anonymous communication, as well as Shodan's capabilities for discovering connected devices. Additionally, it discusses the legality of accessing hidden content, potential vulnerabilities of accessing the deep web, and offers resources for navigating this hidden part of the internet.