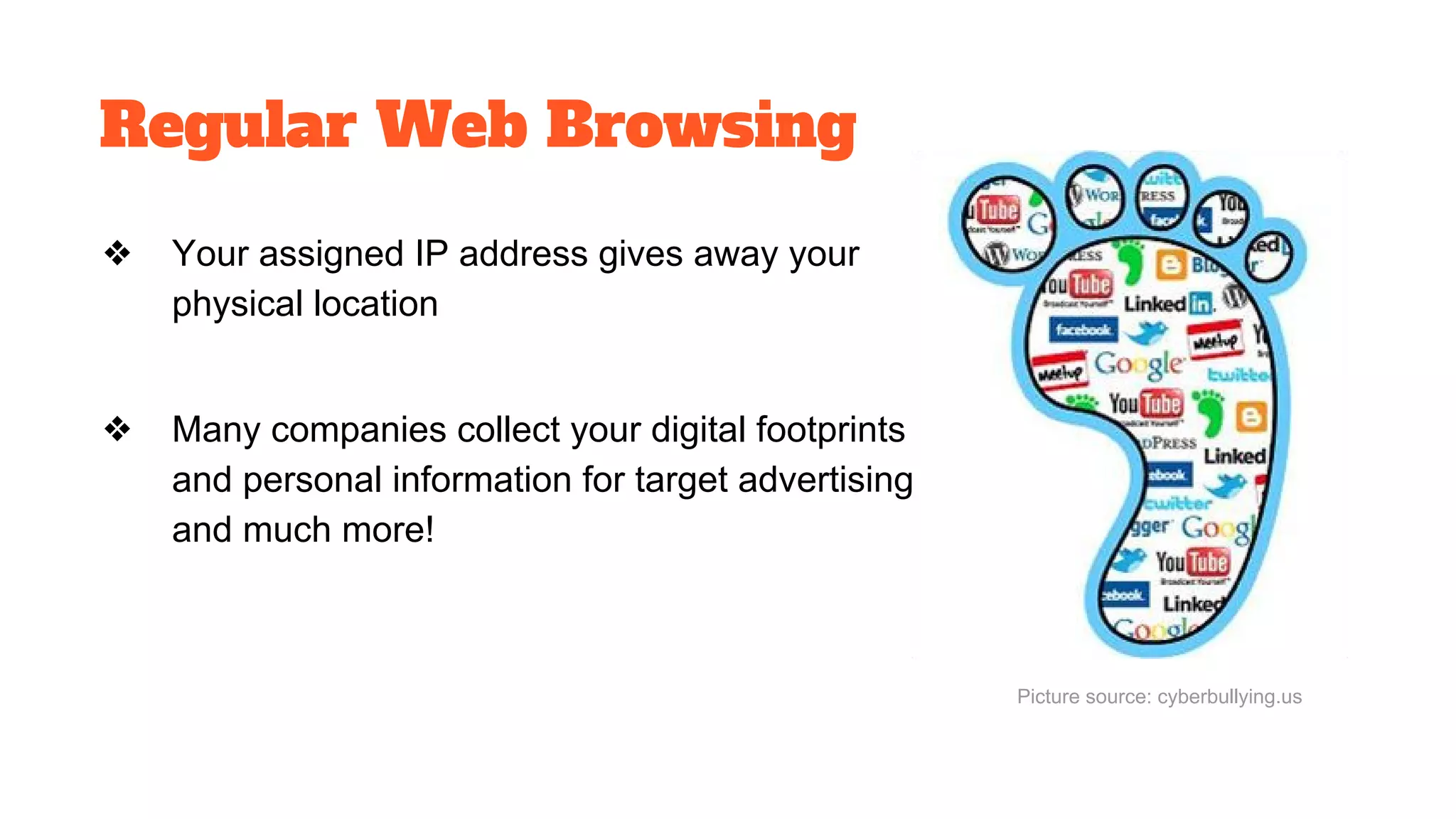
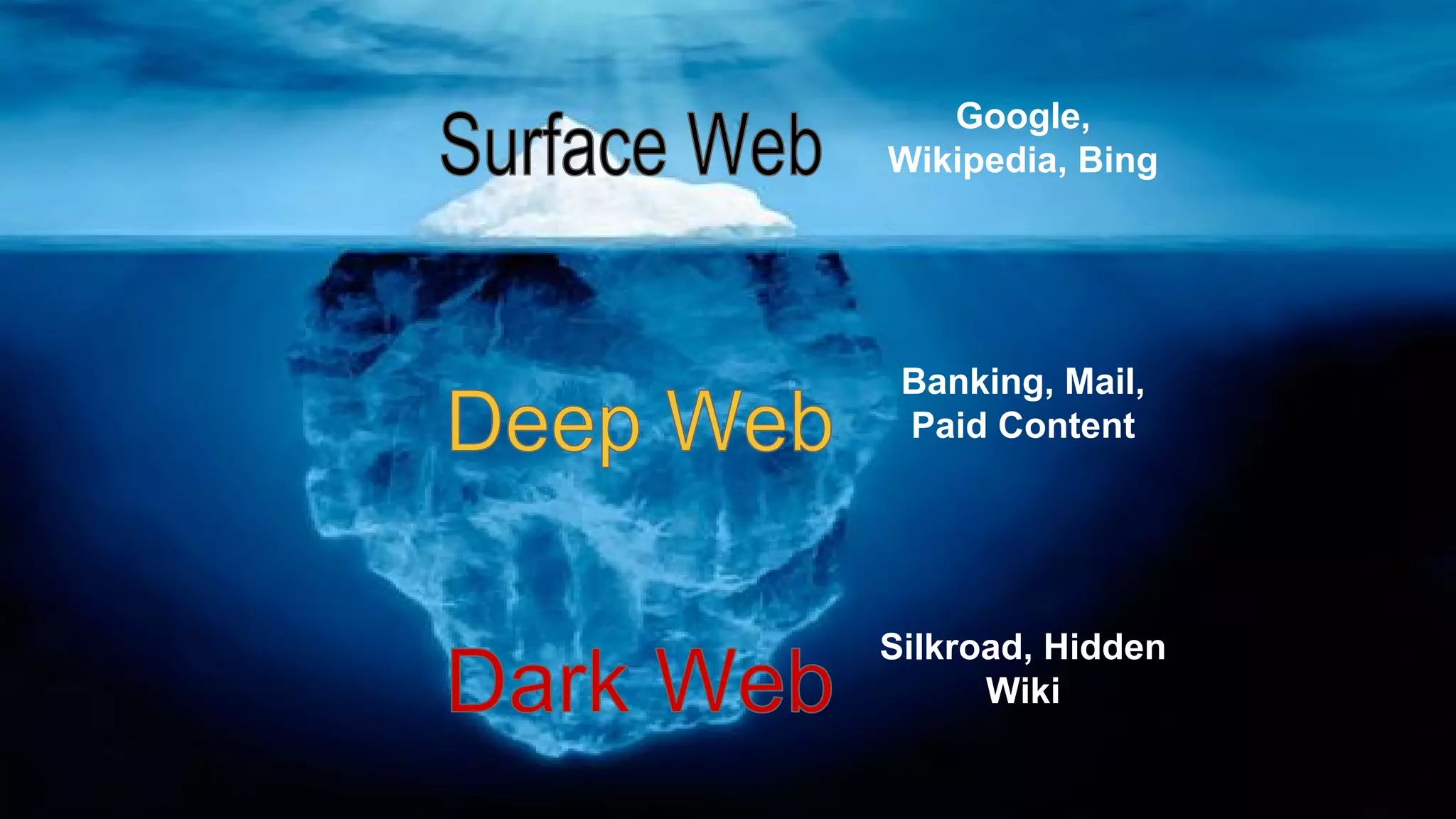
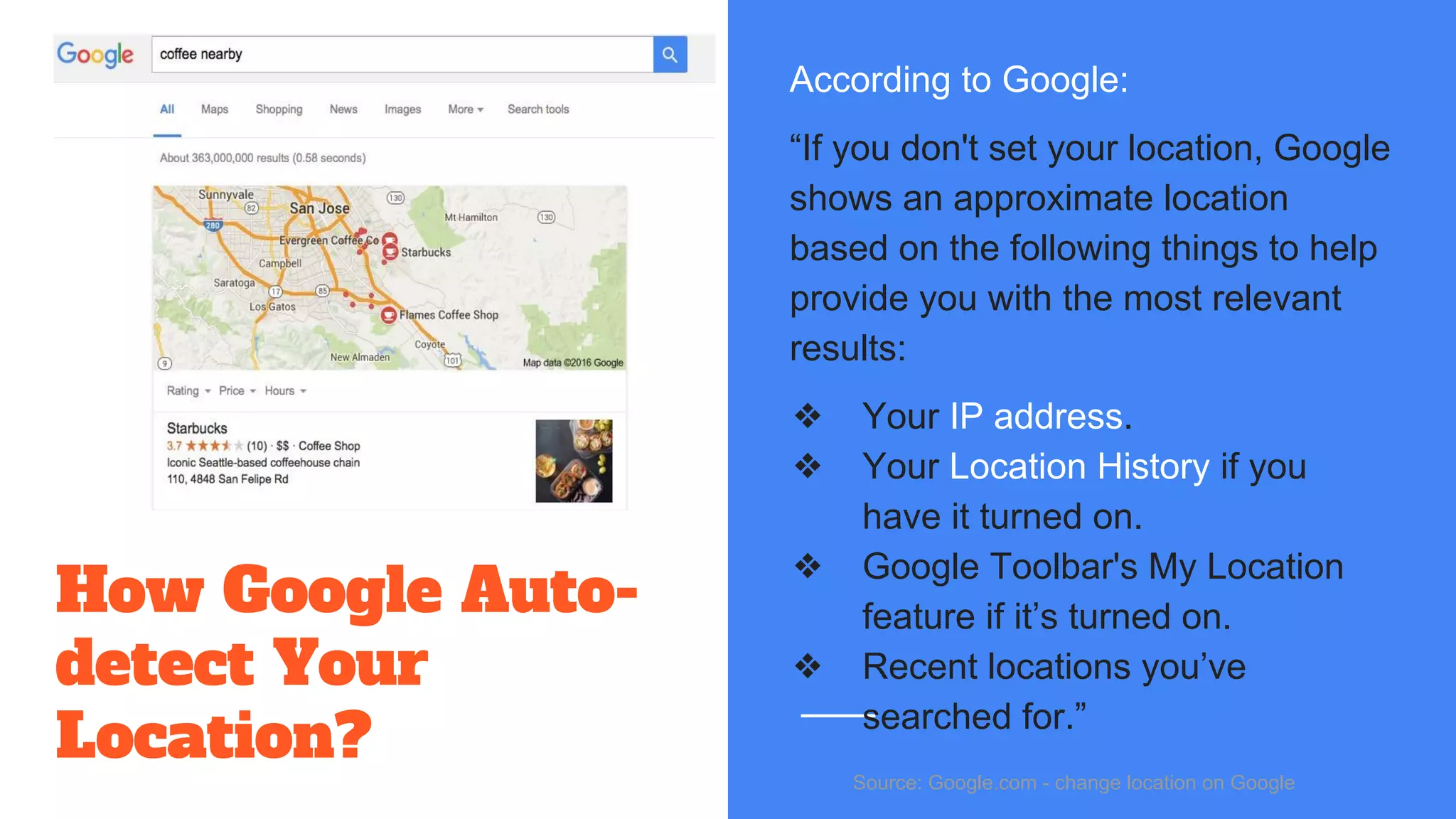
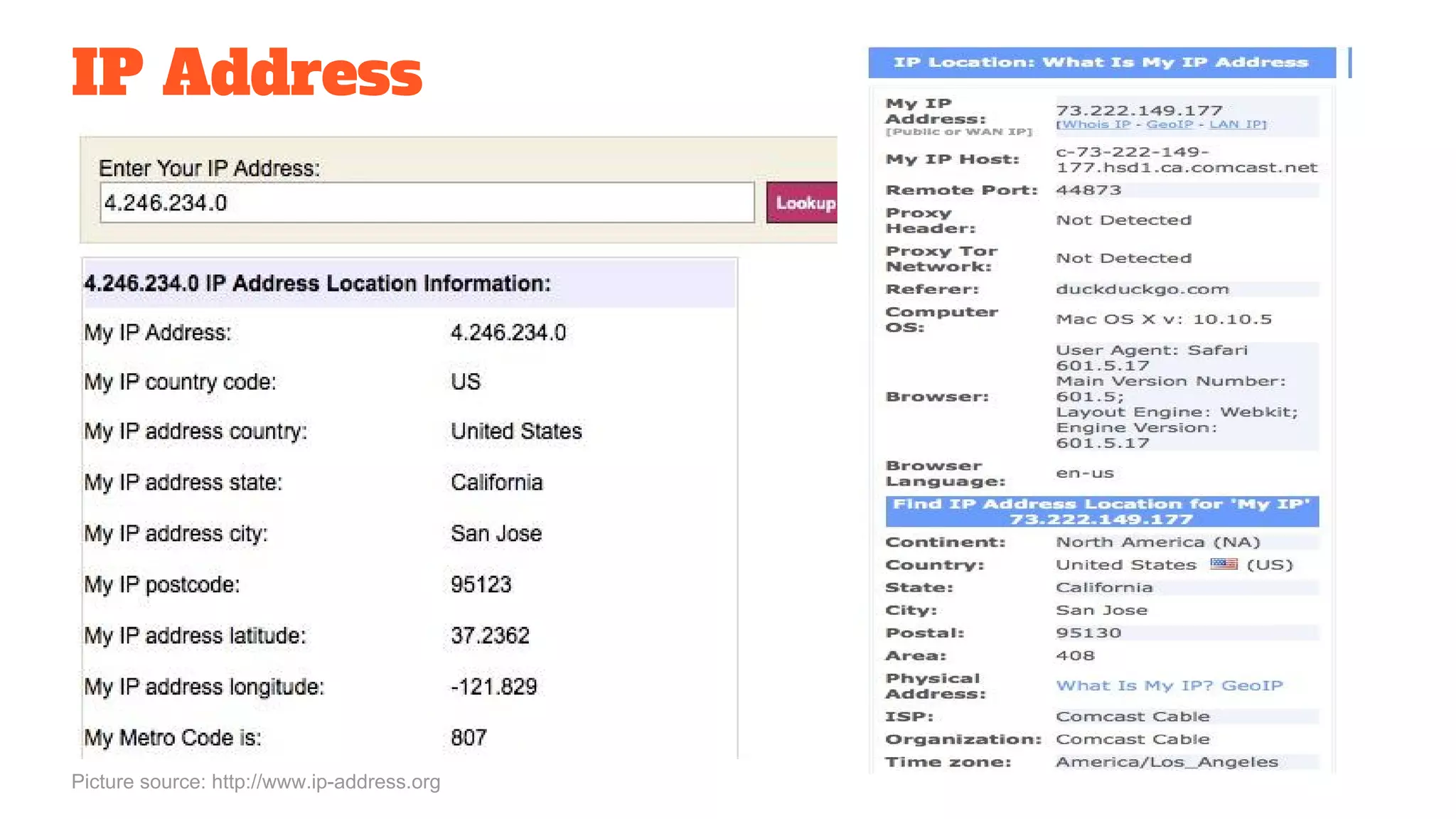
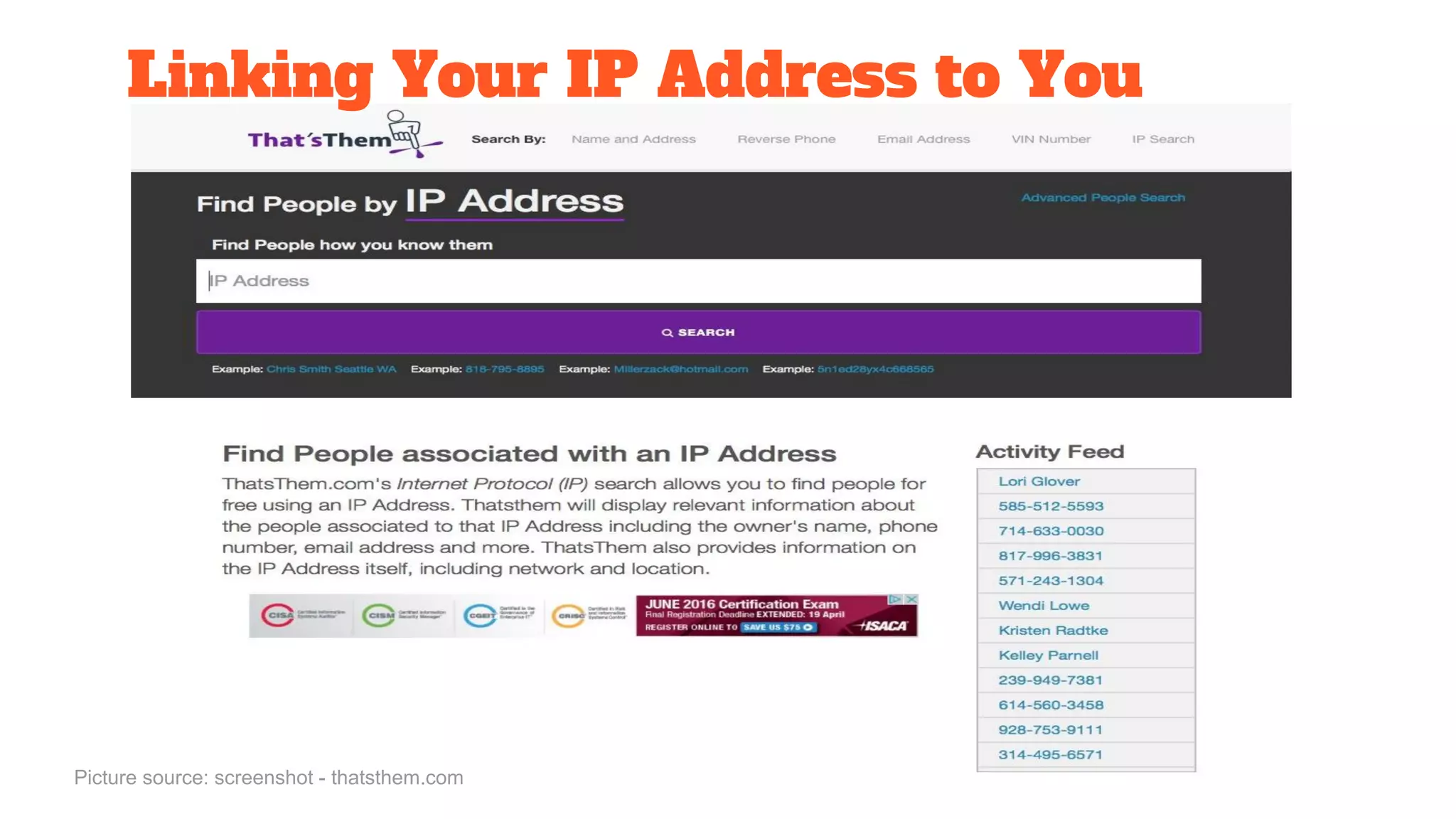
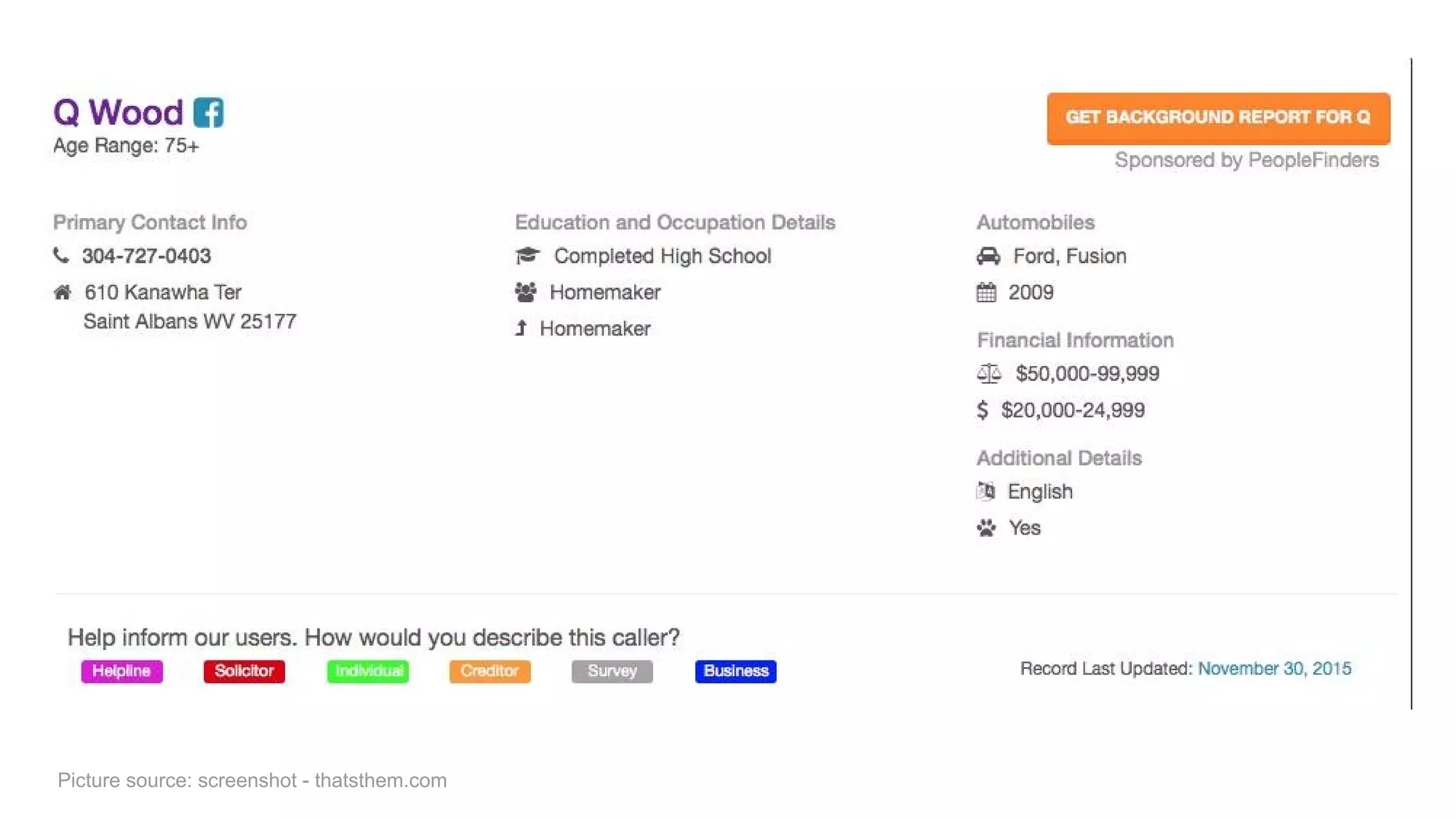
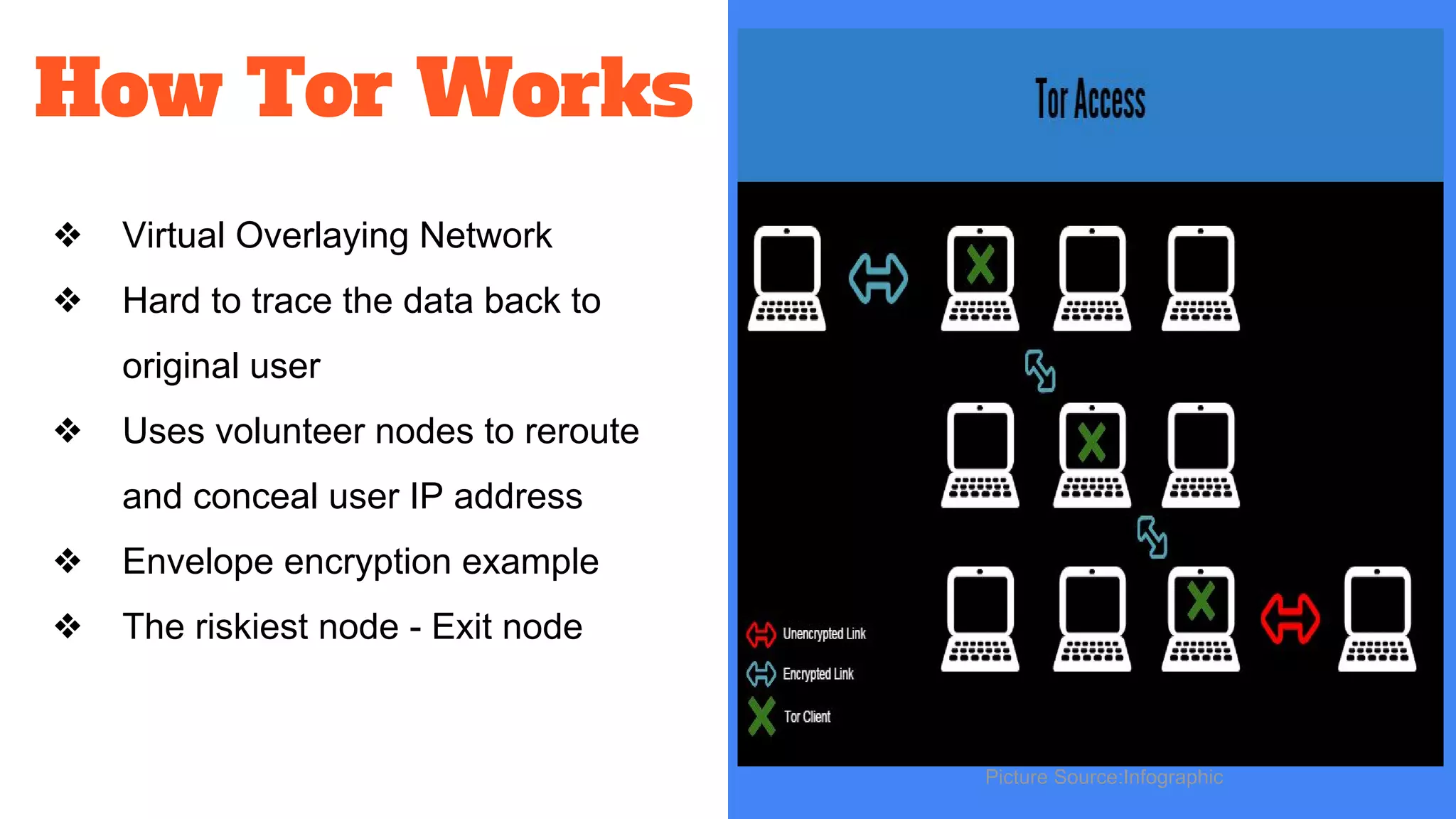
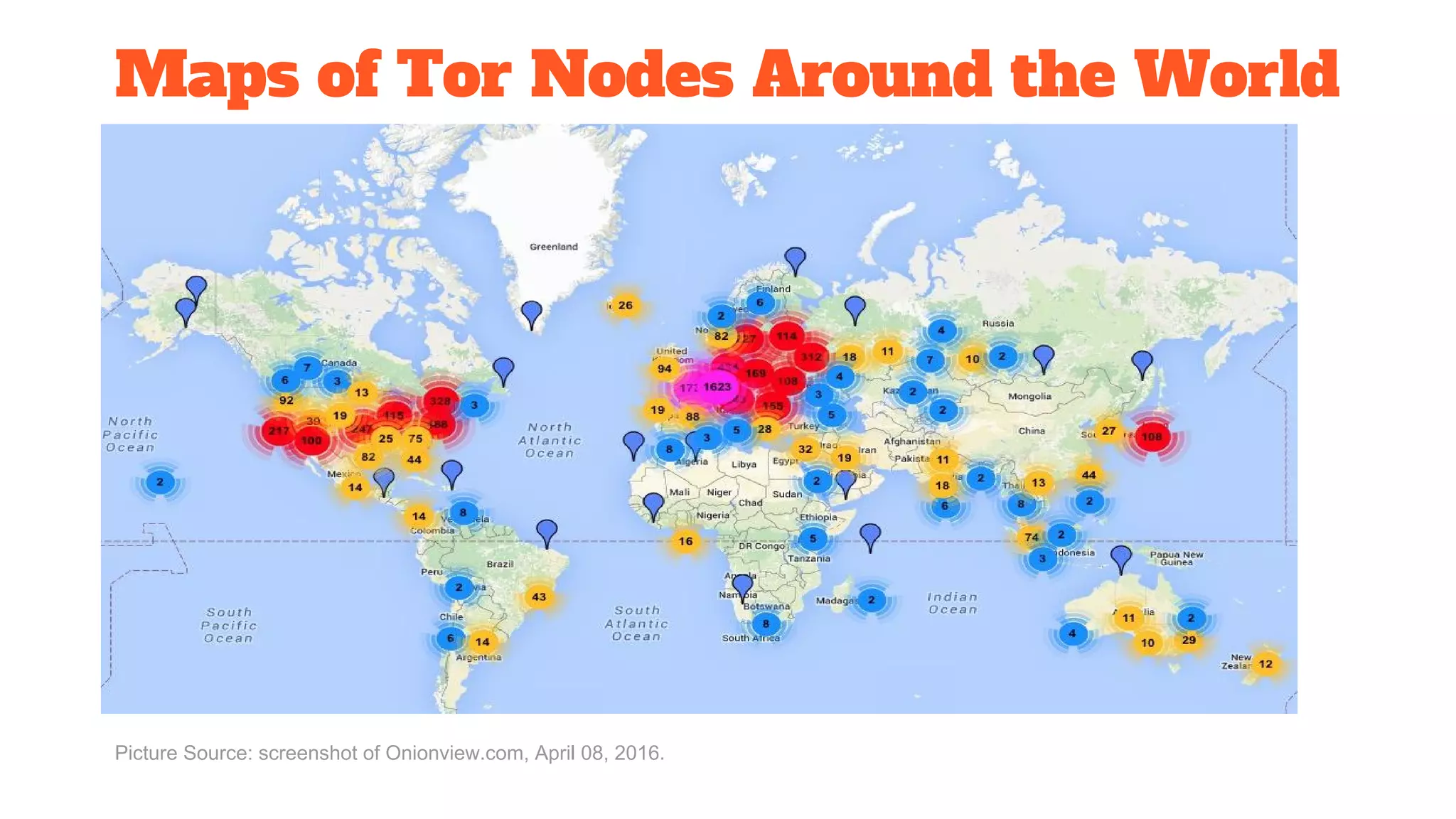
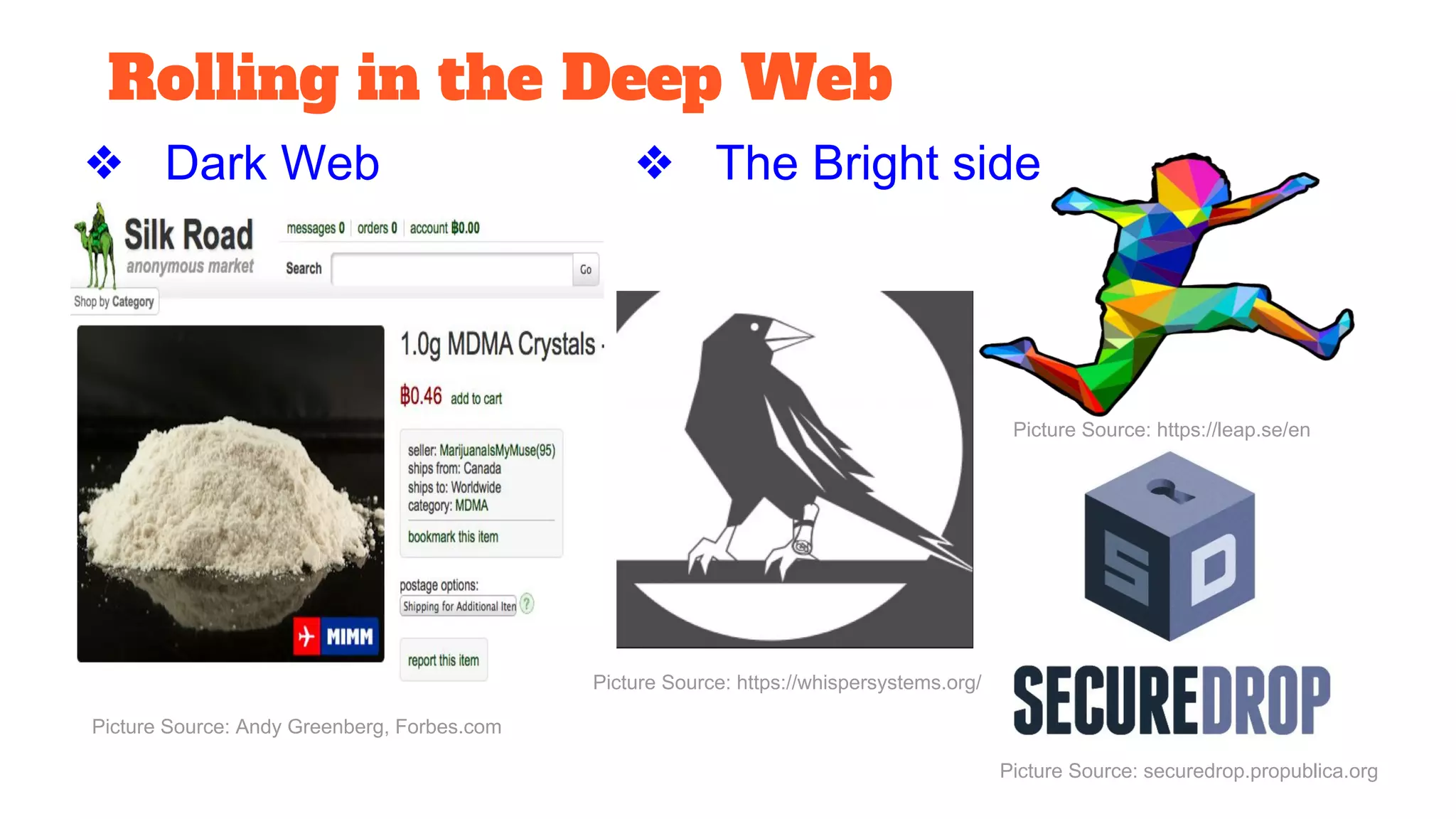
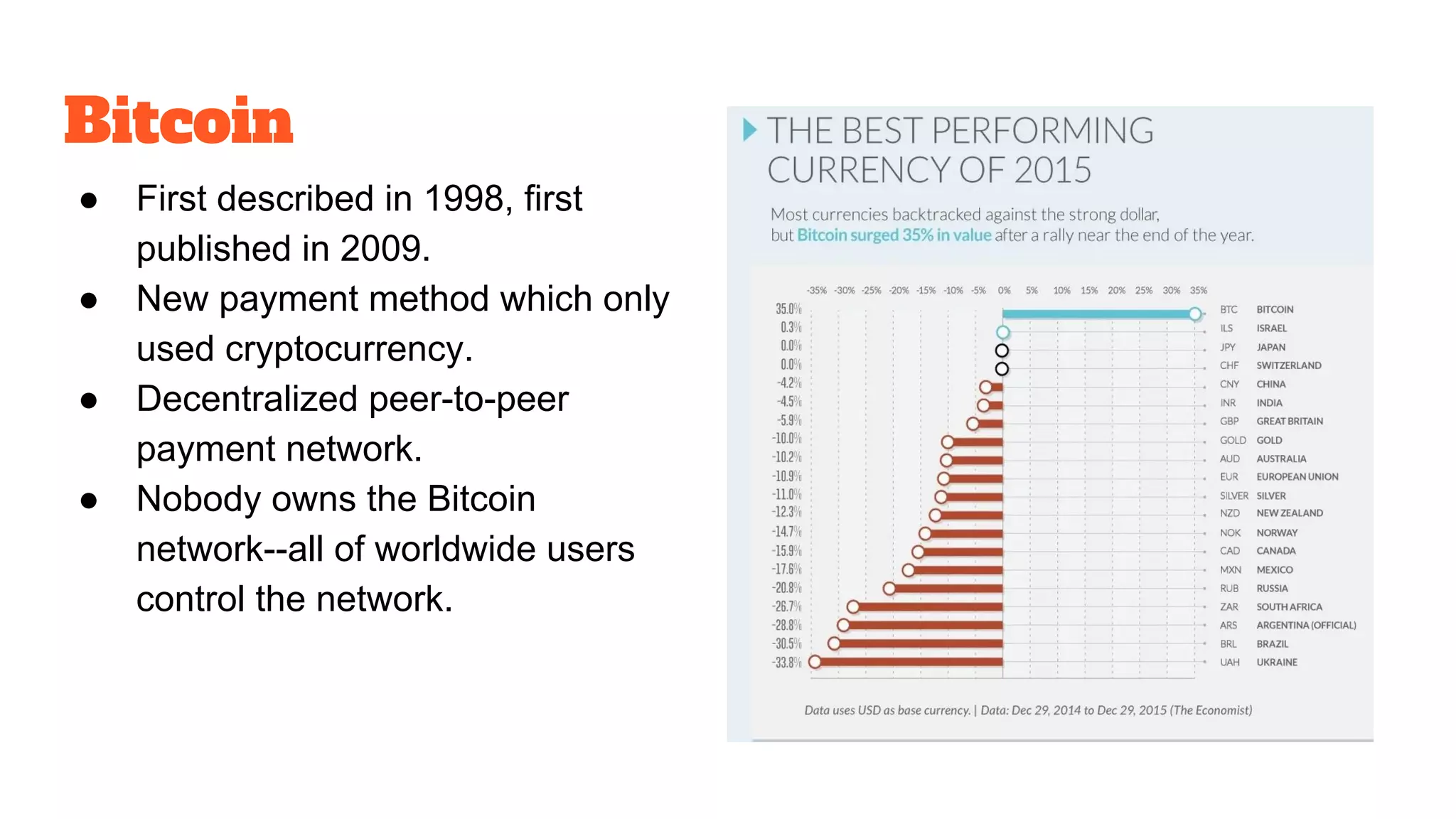
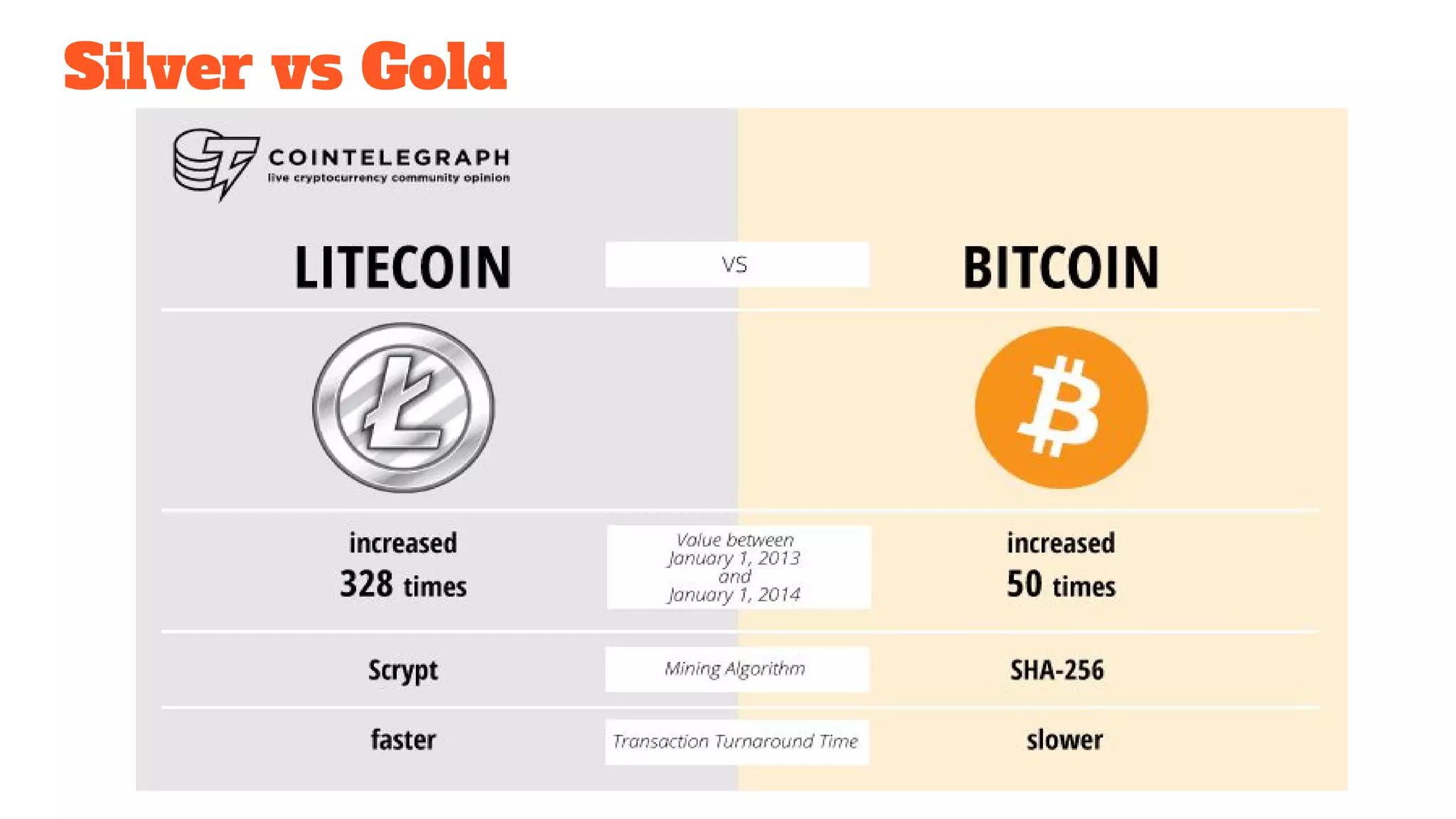
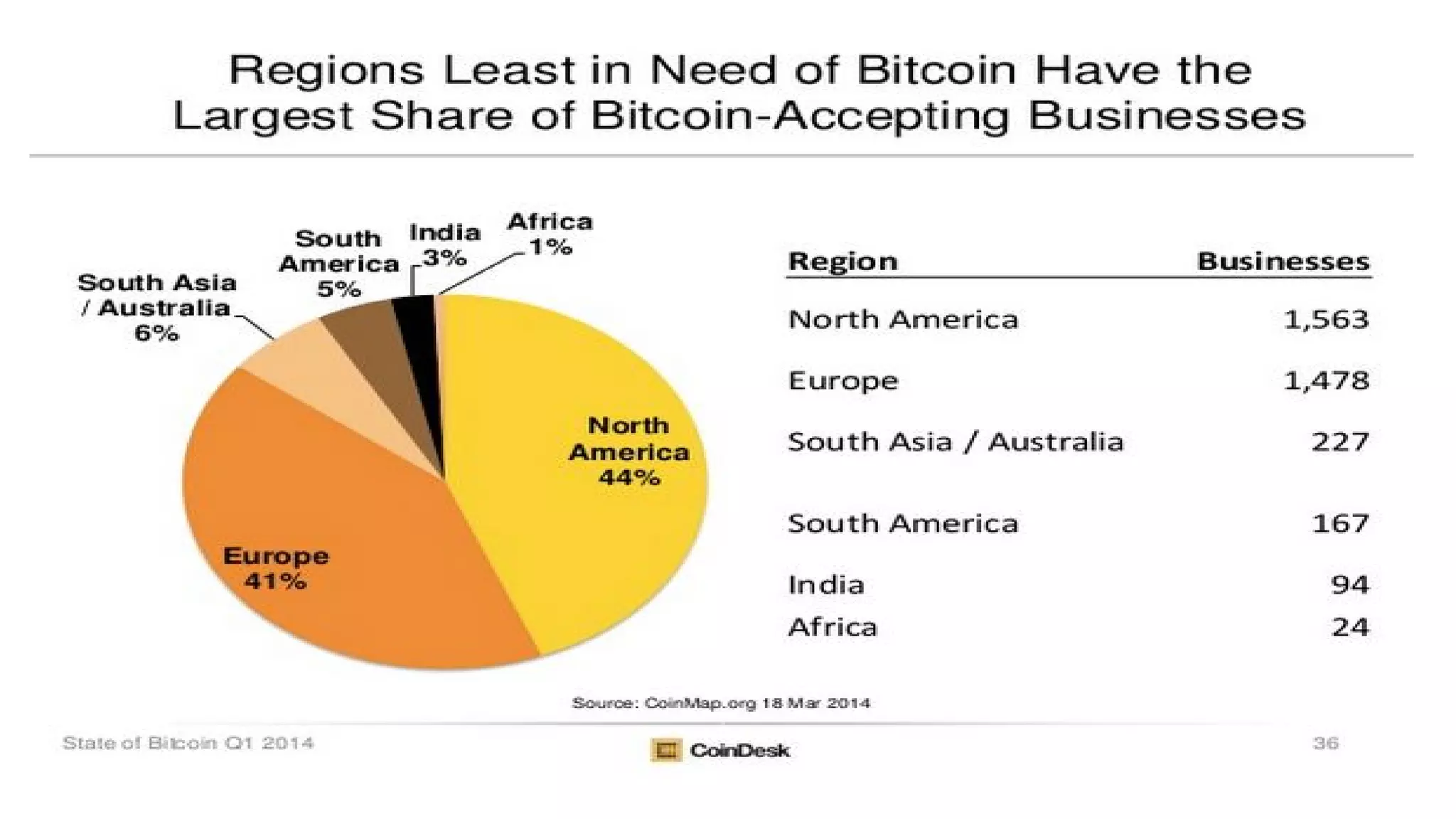
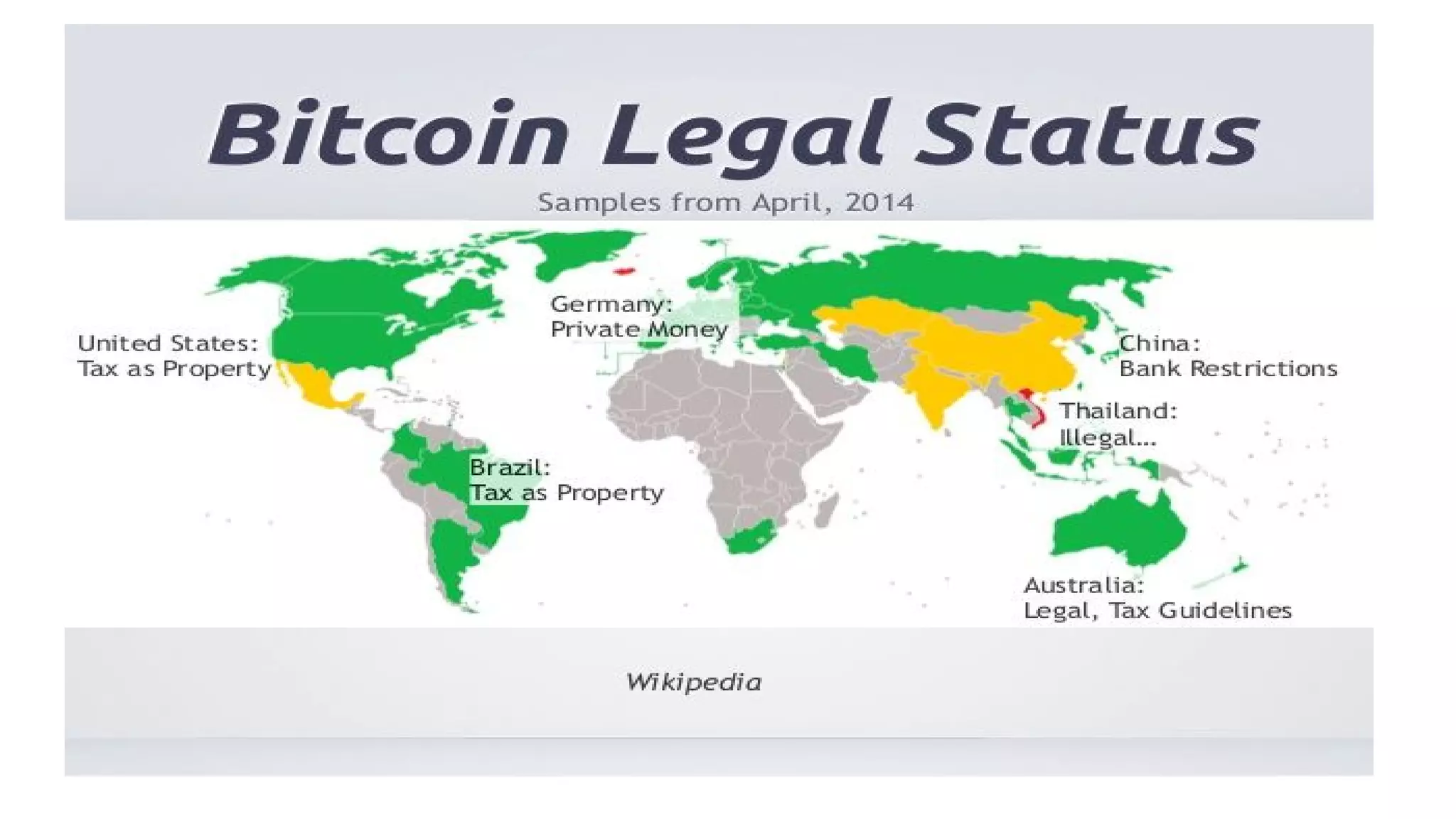
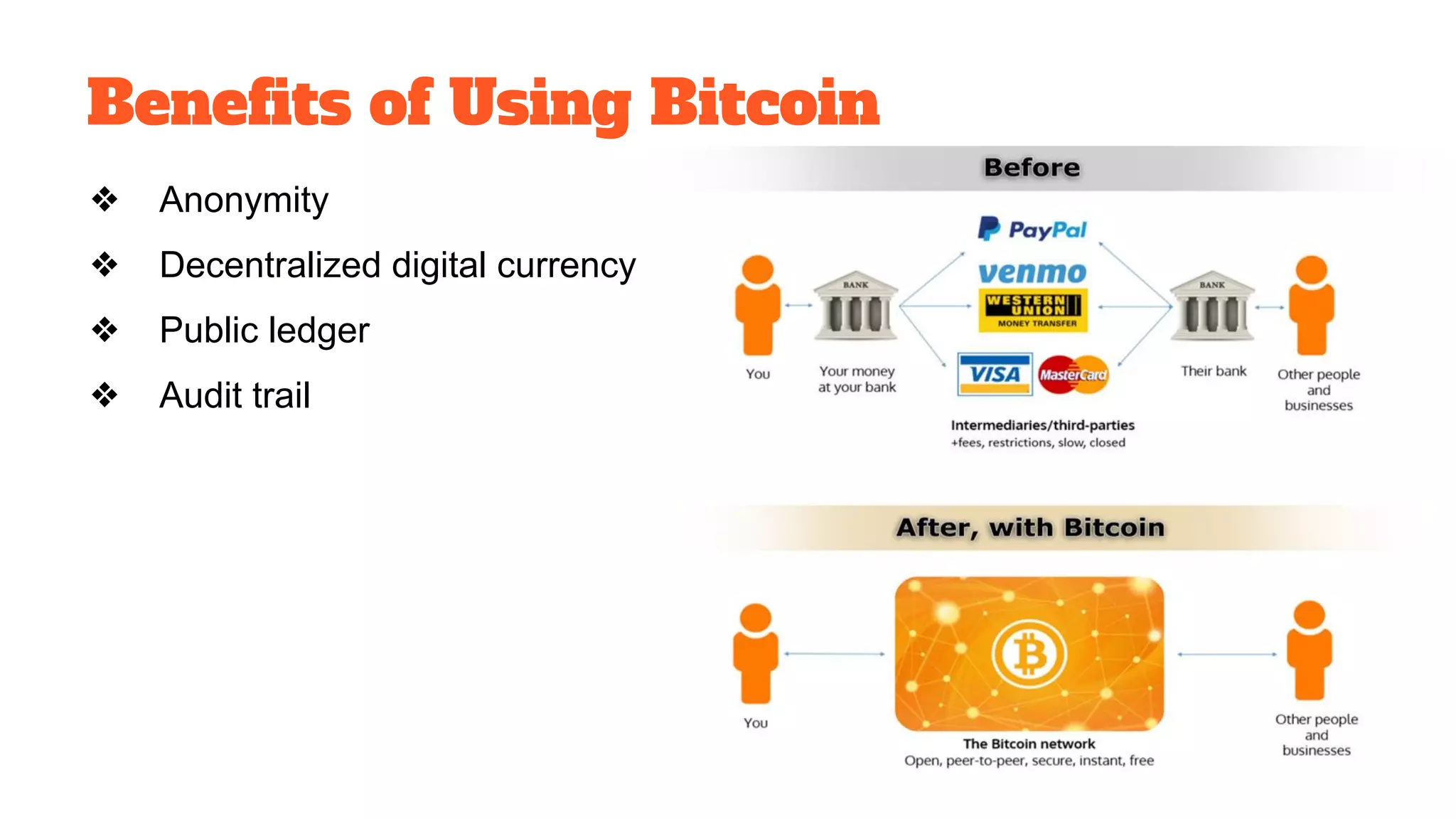
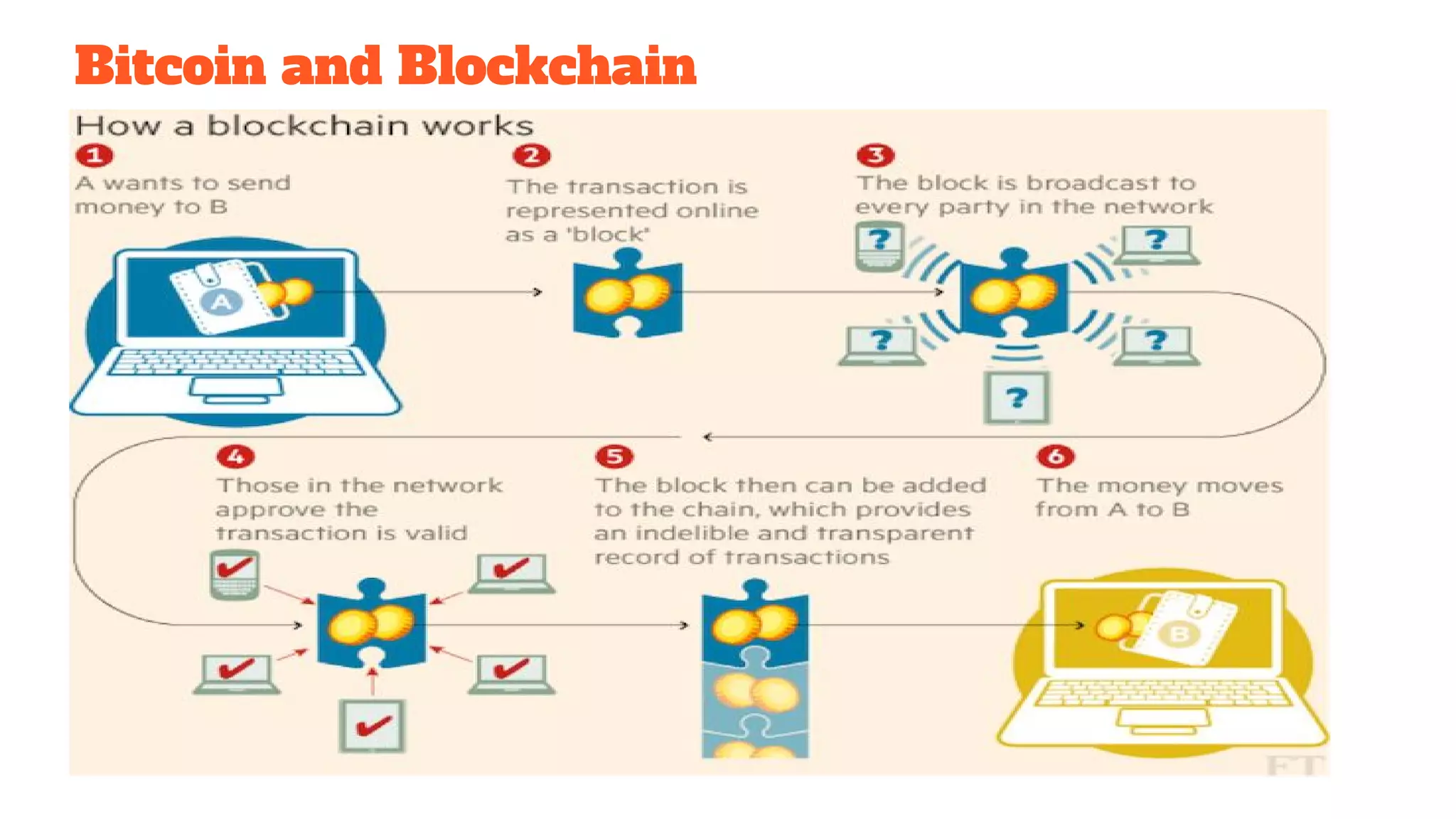
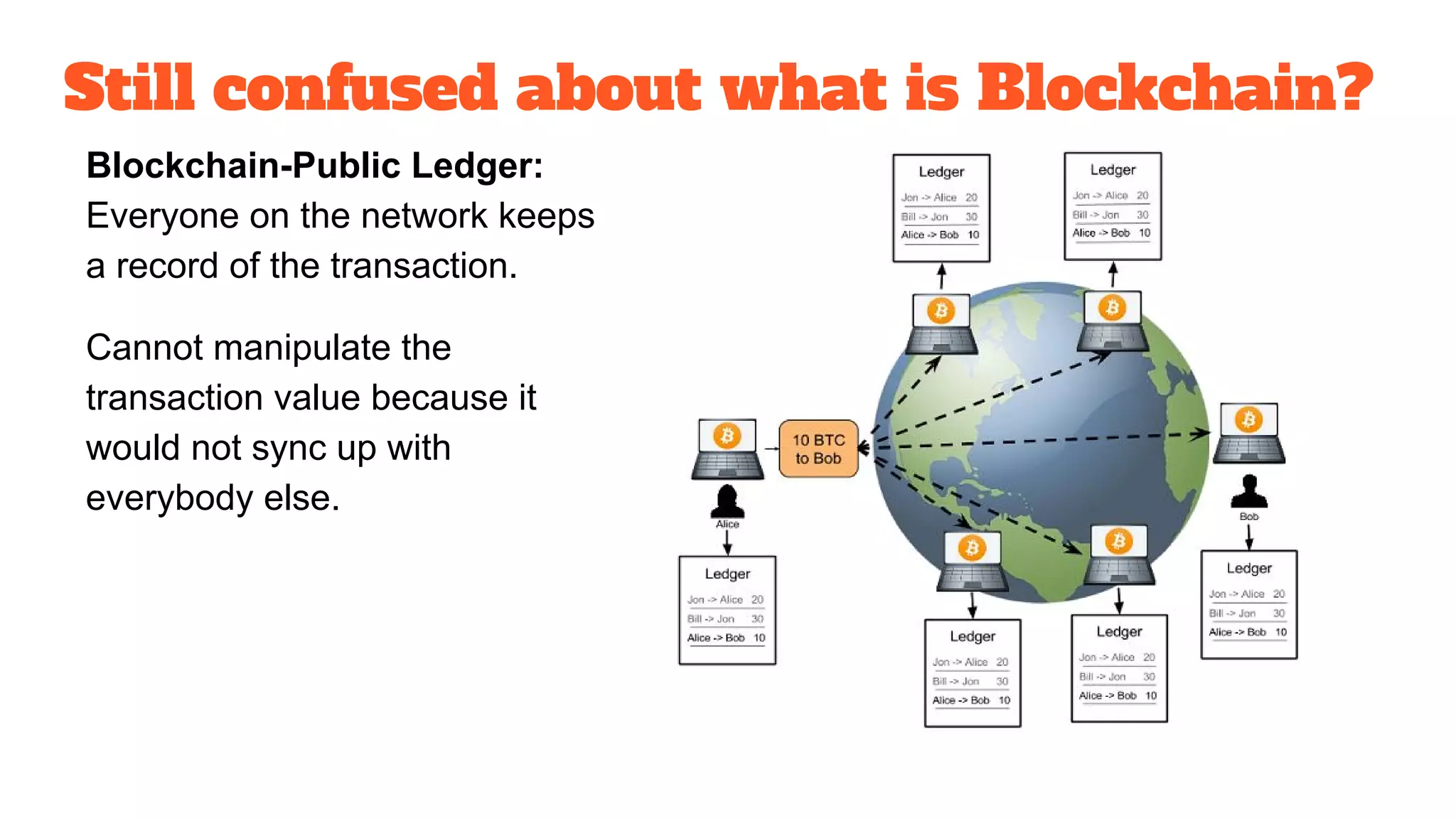
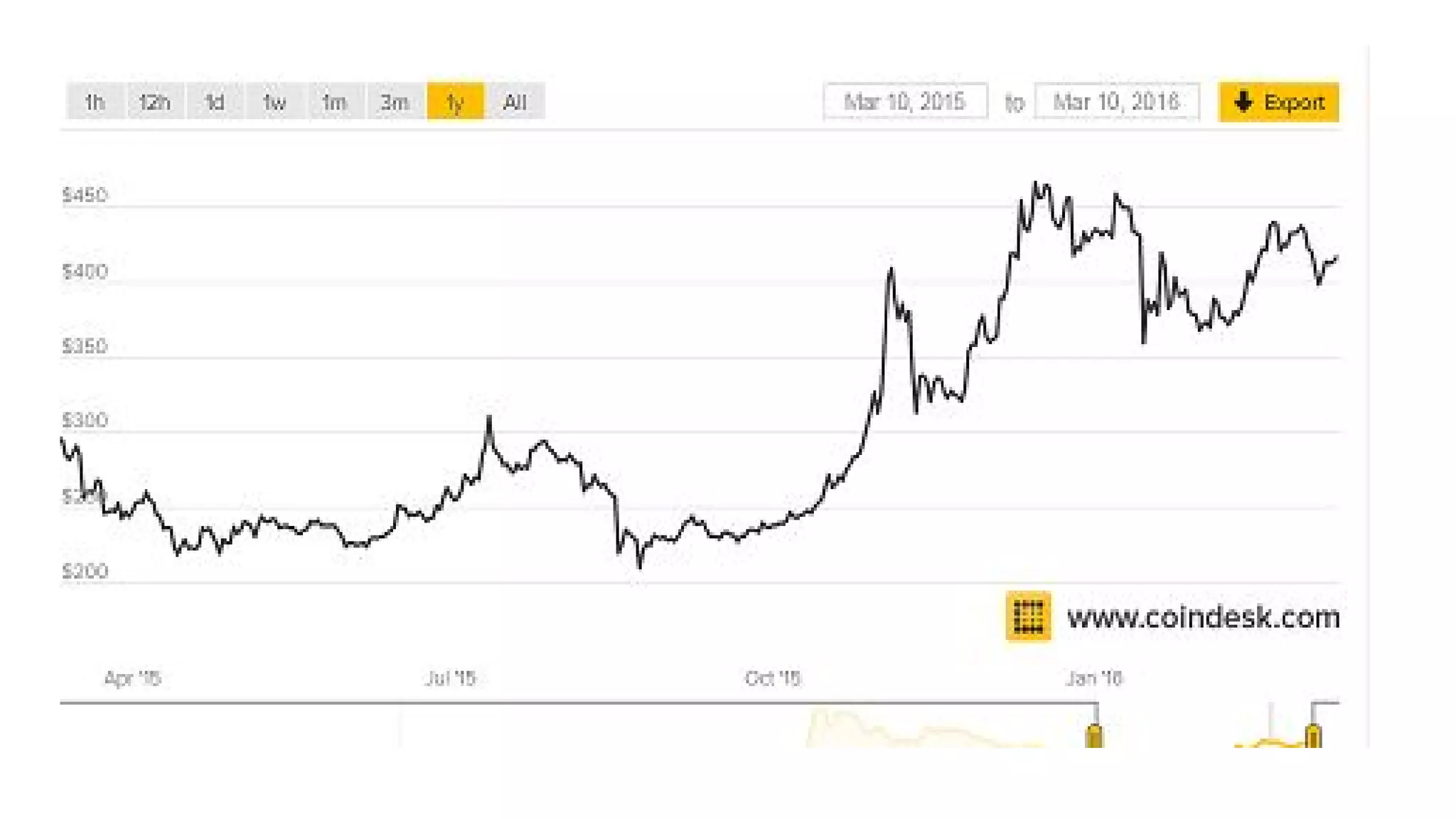
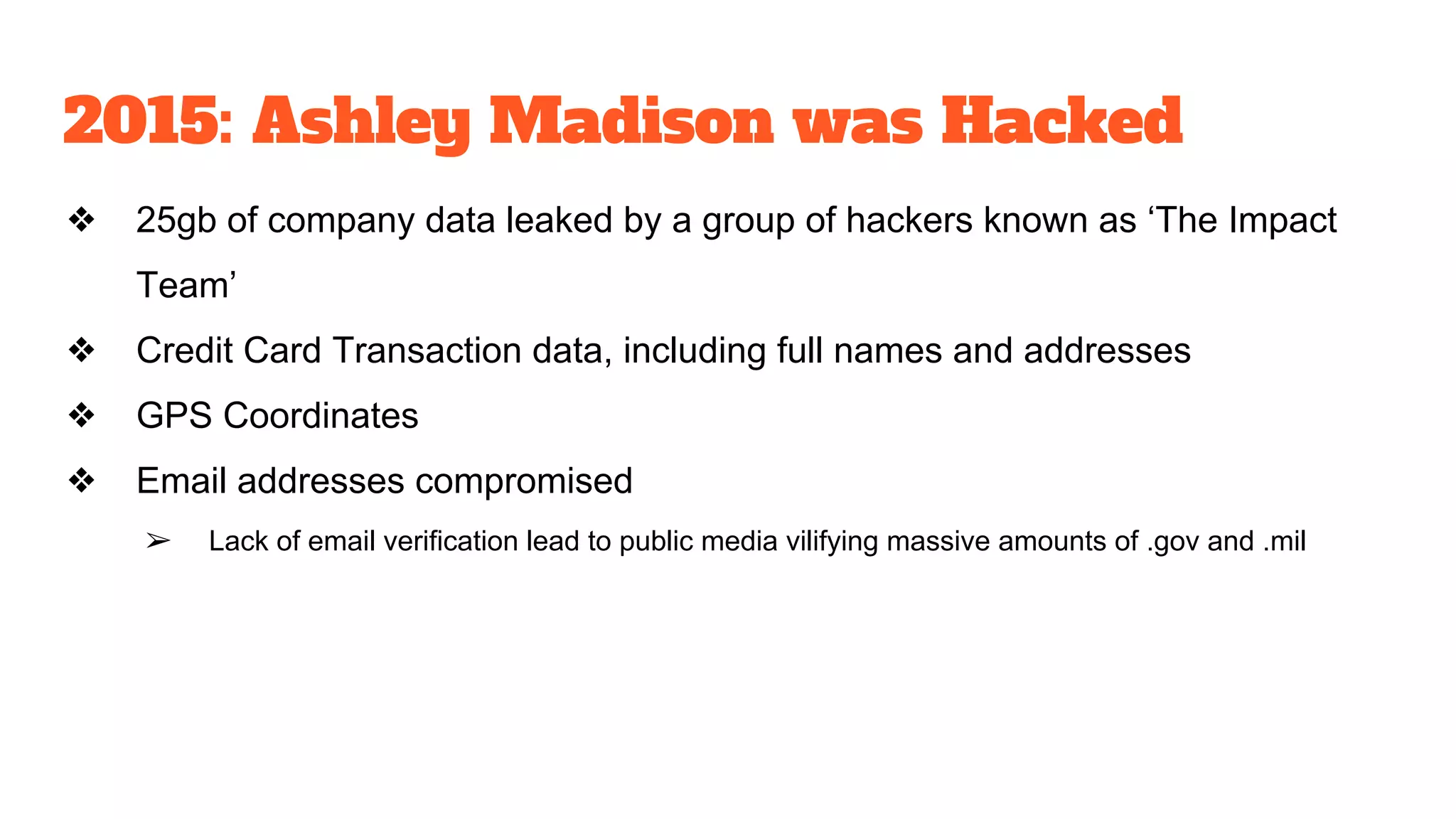
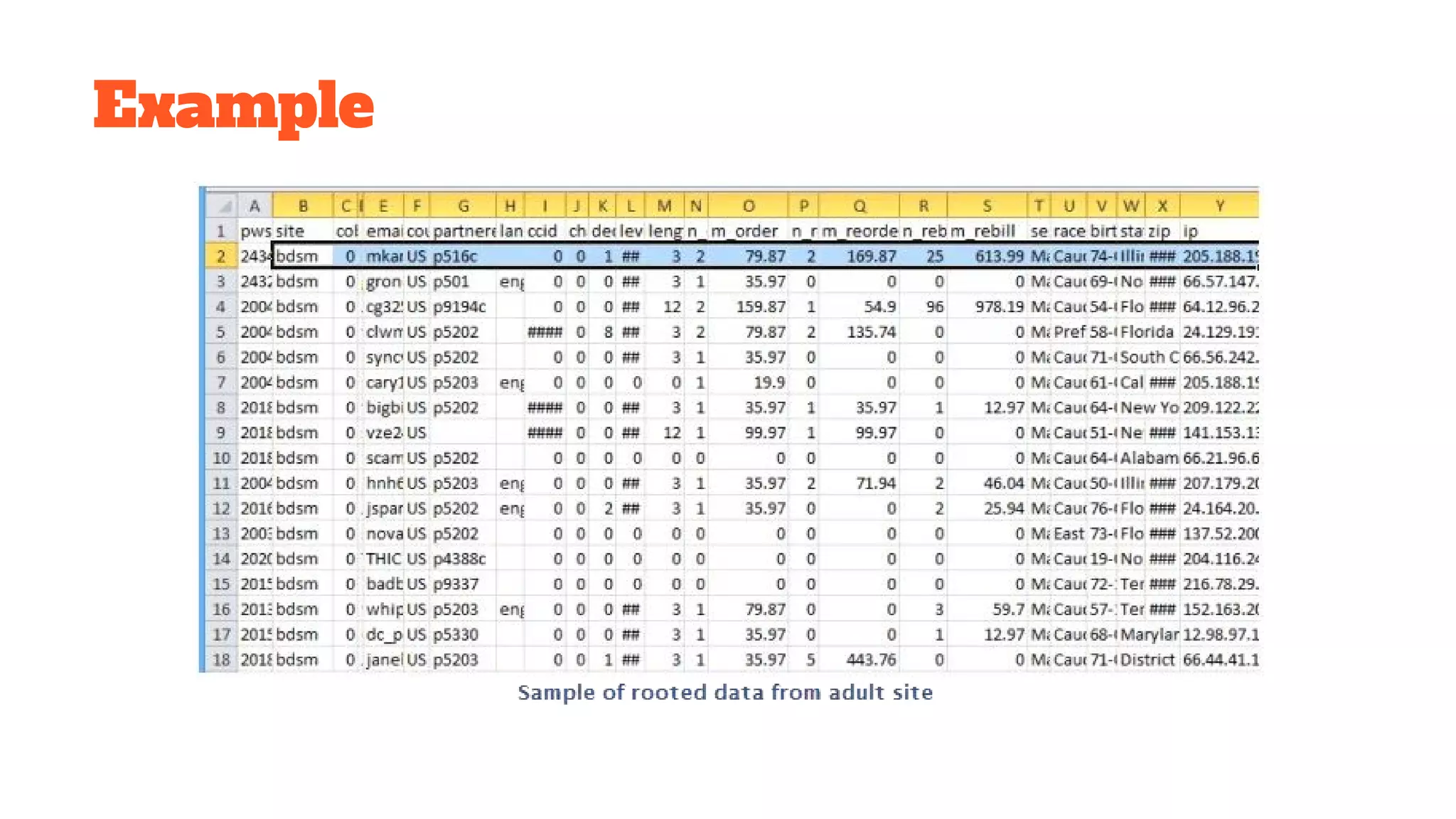
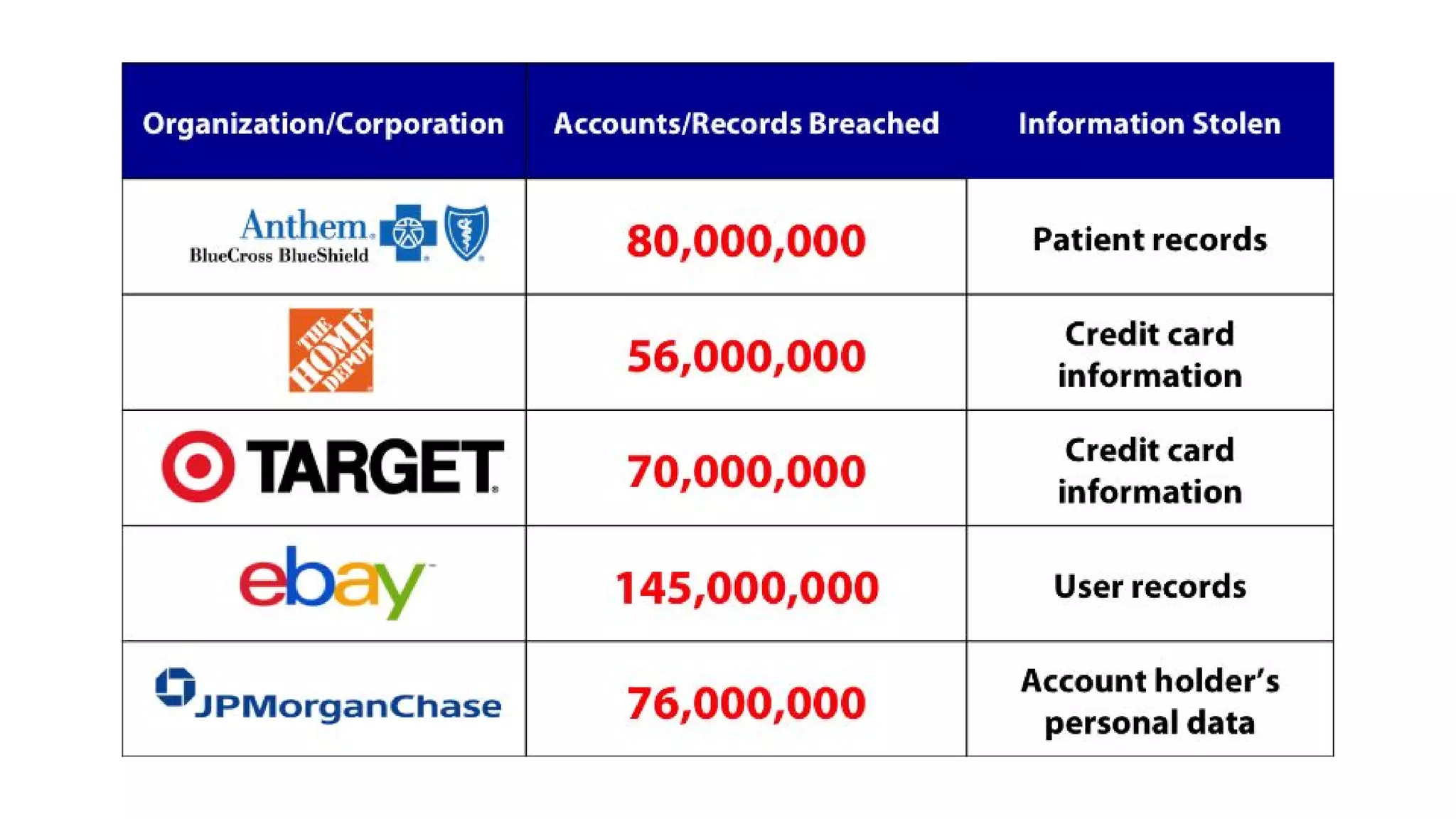
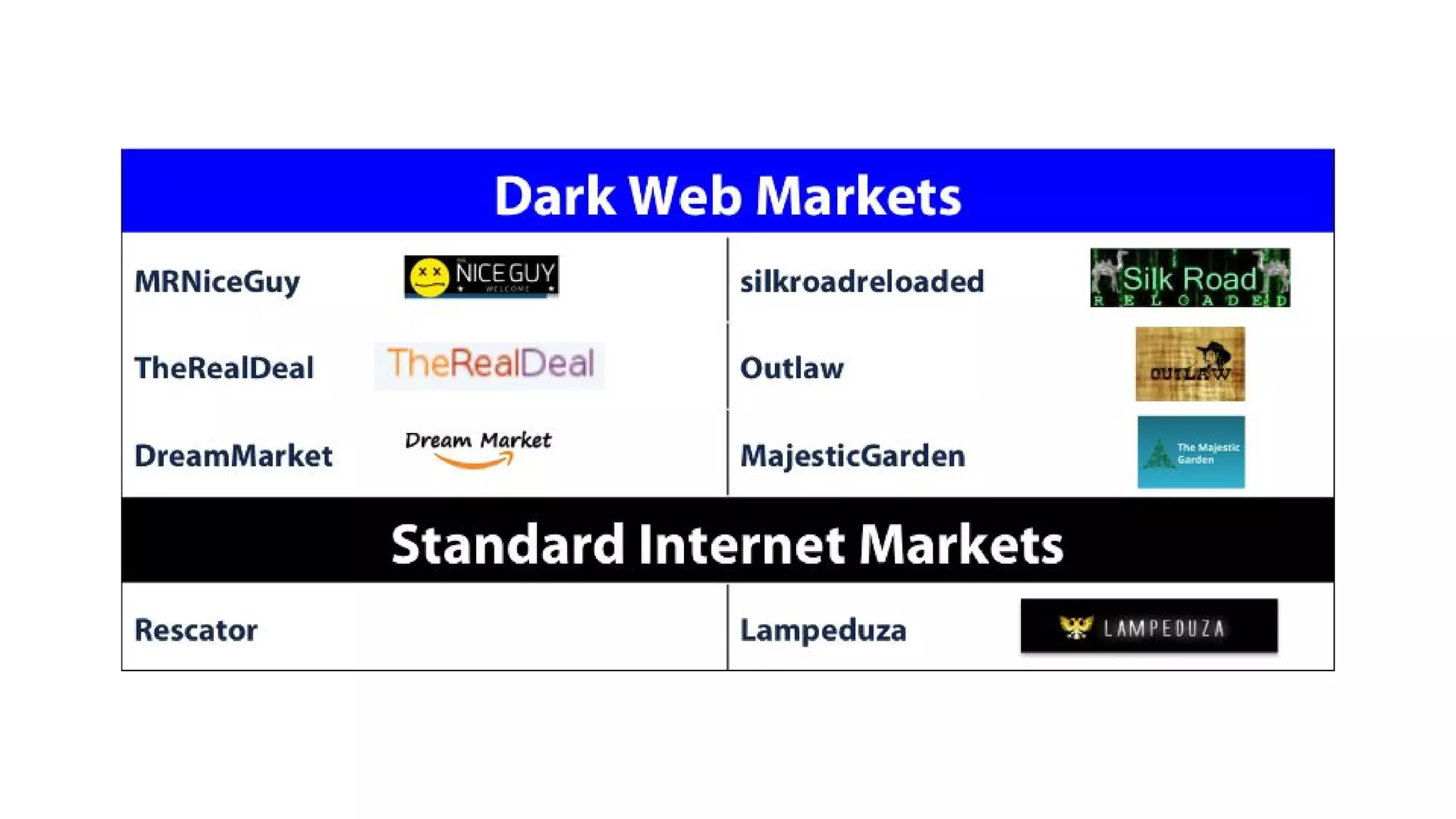
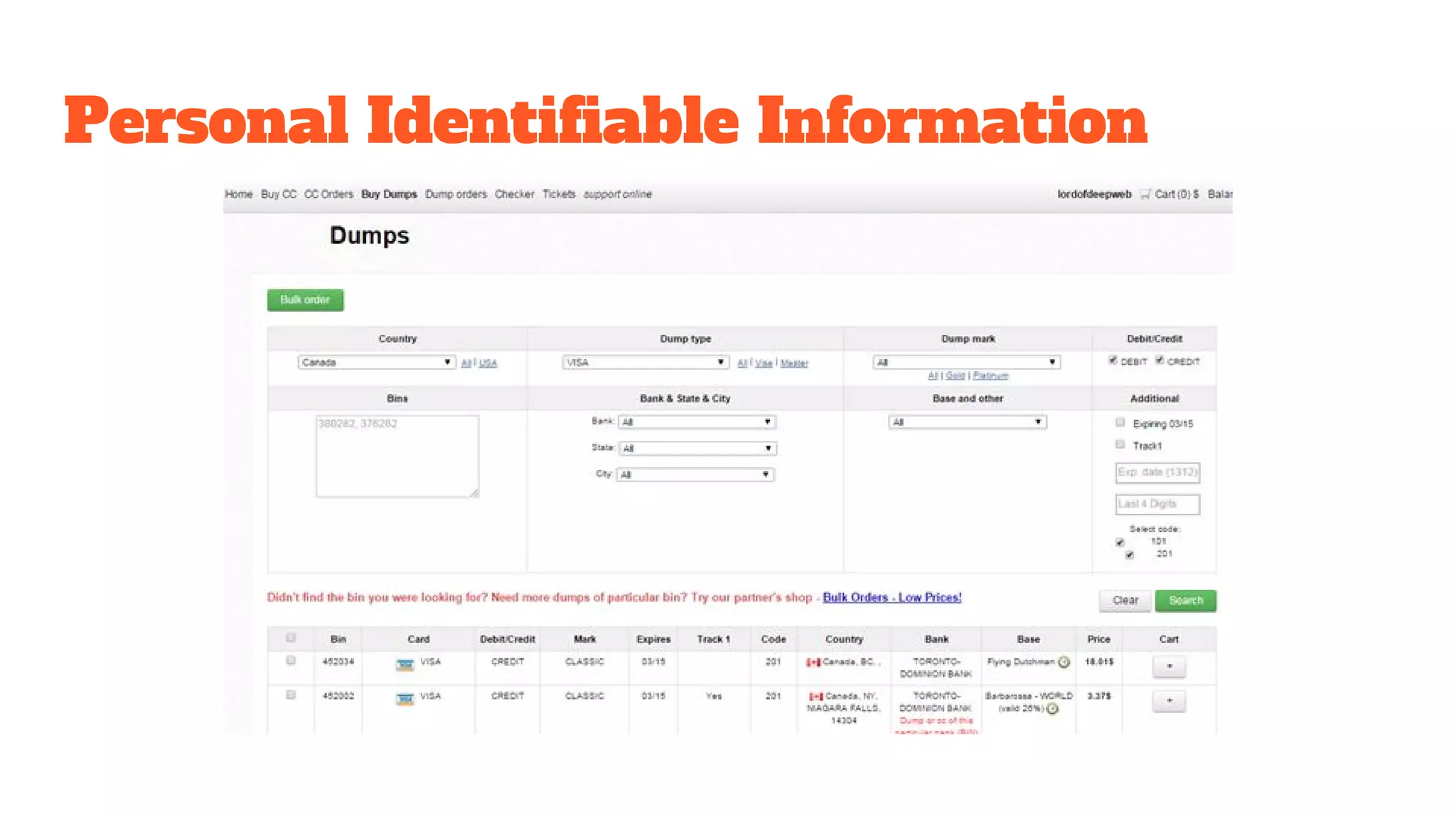
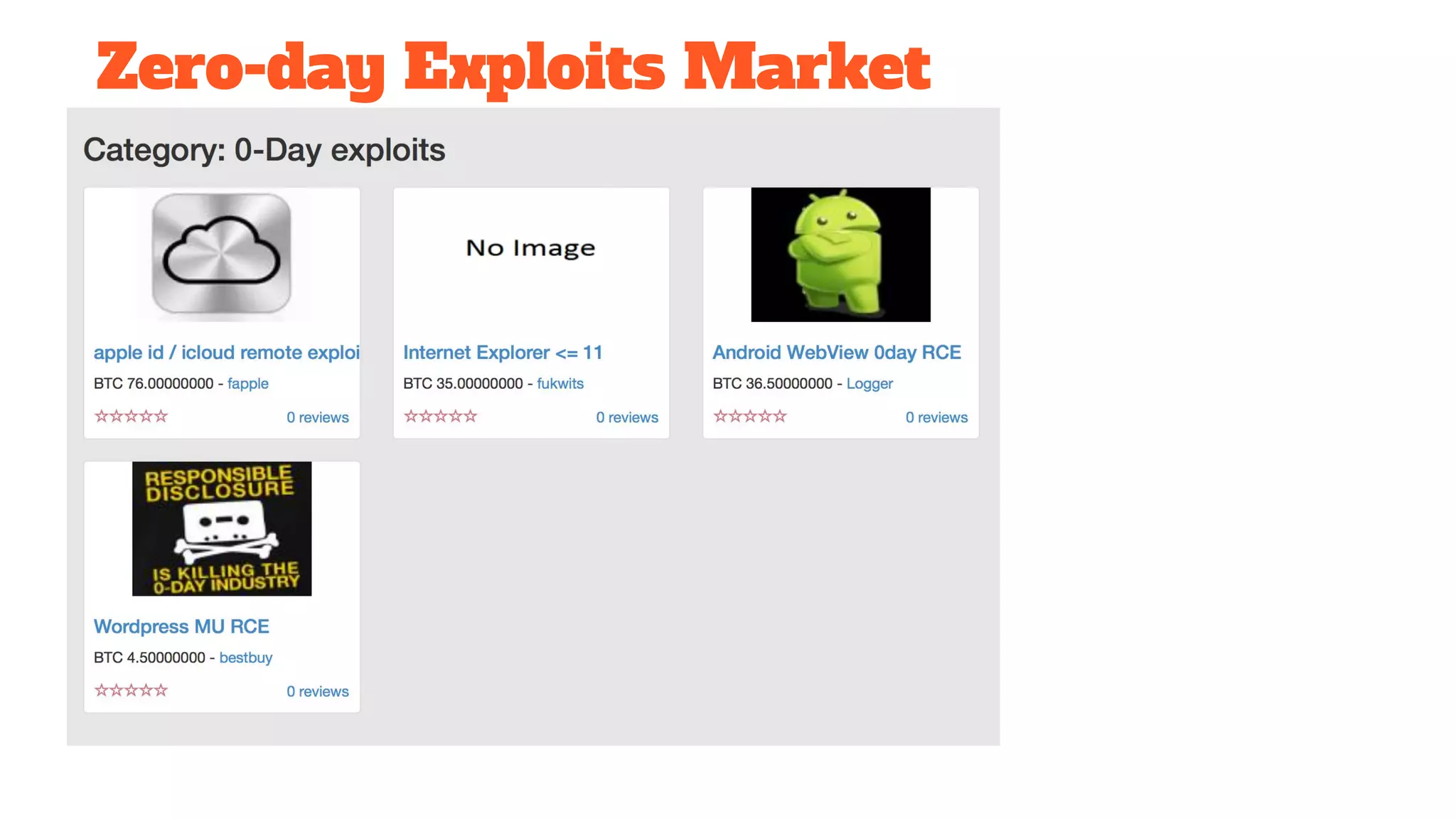
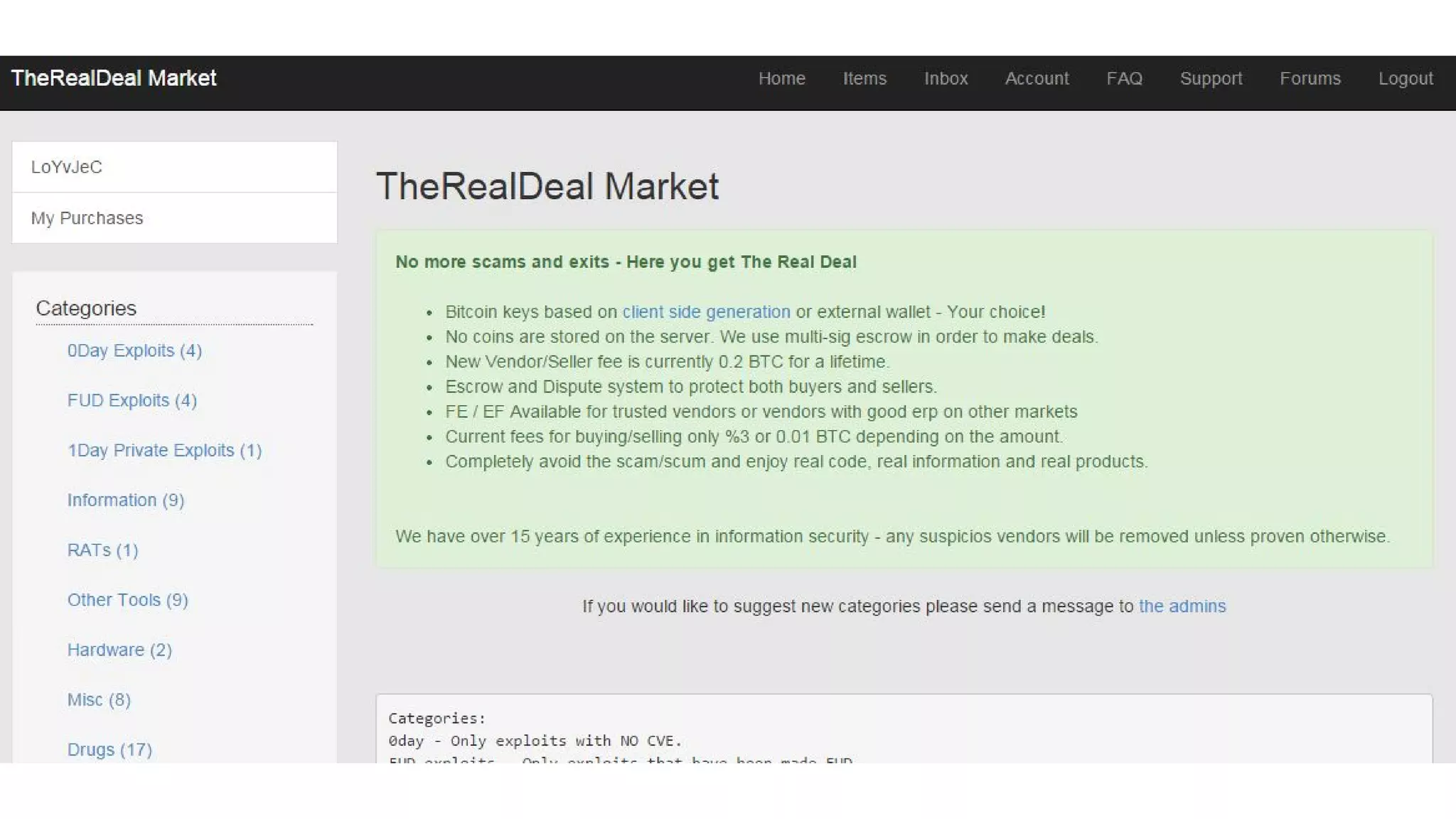
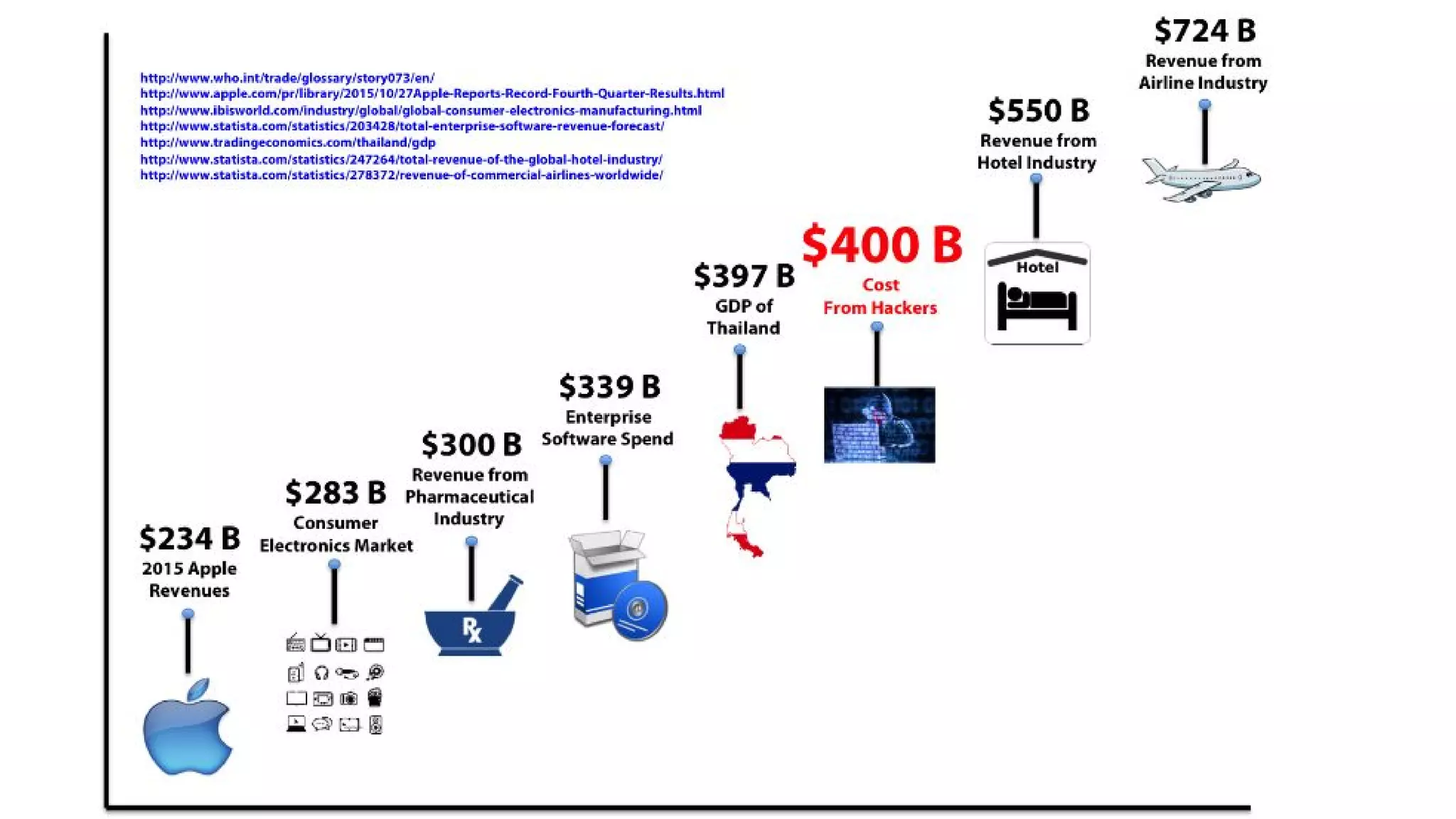
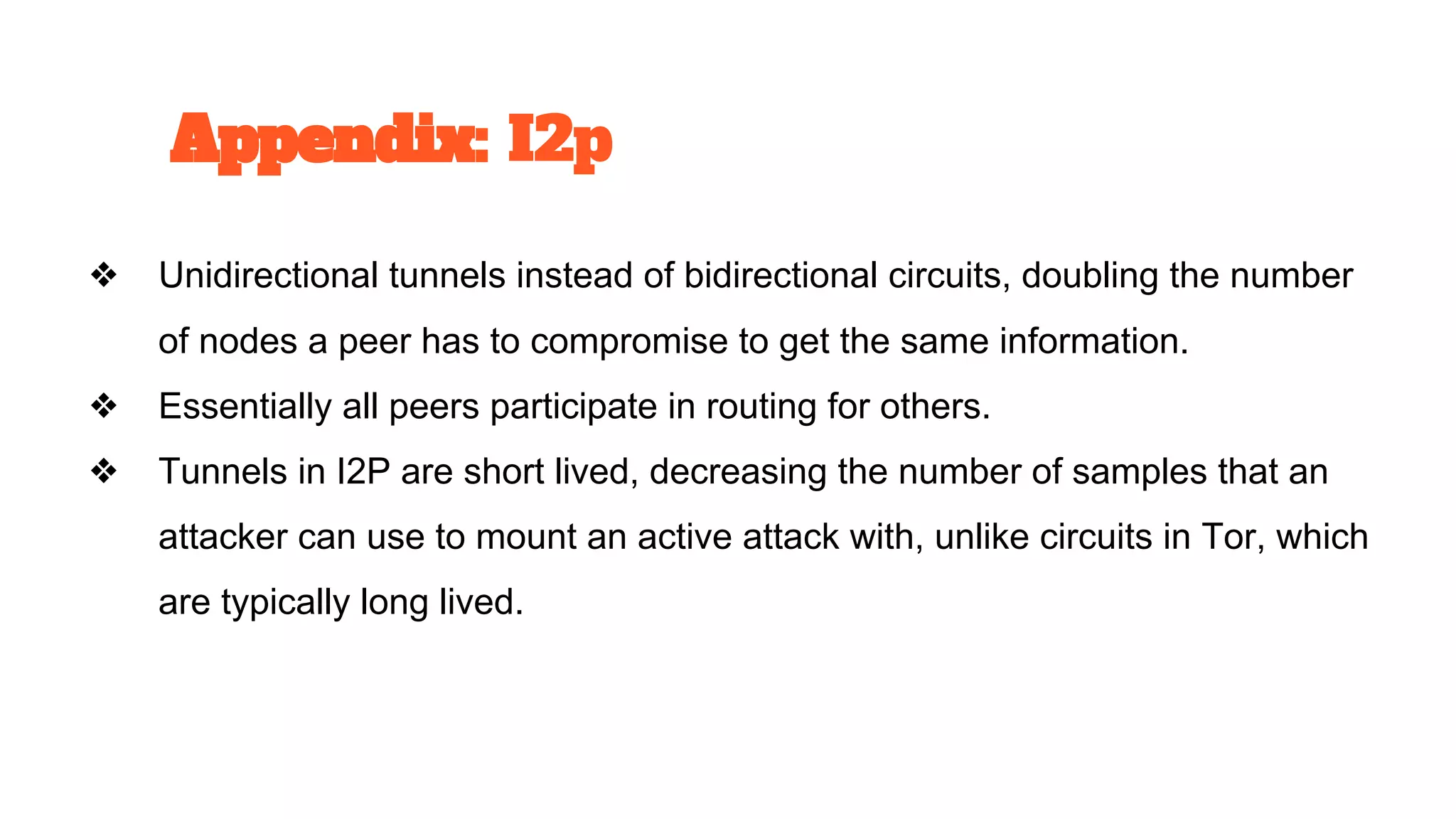
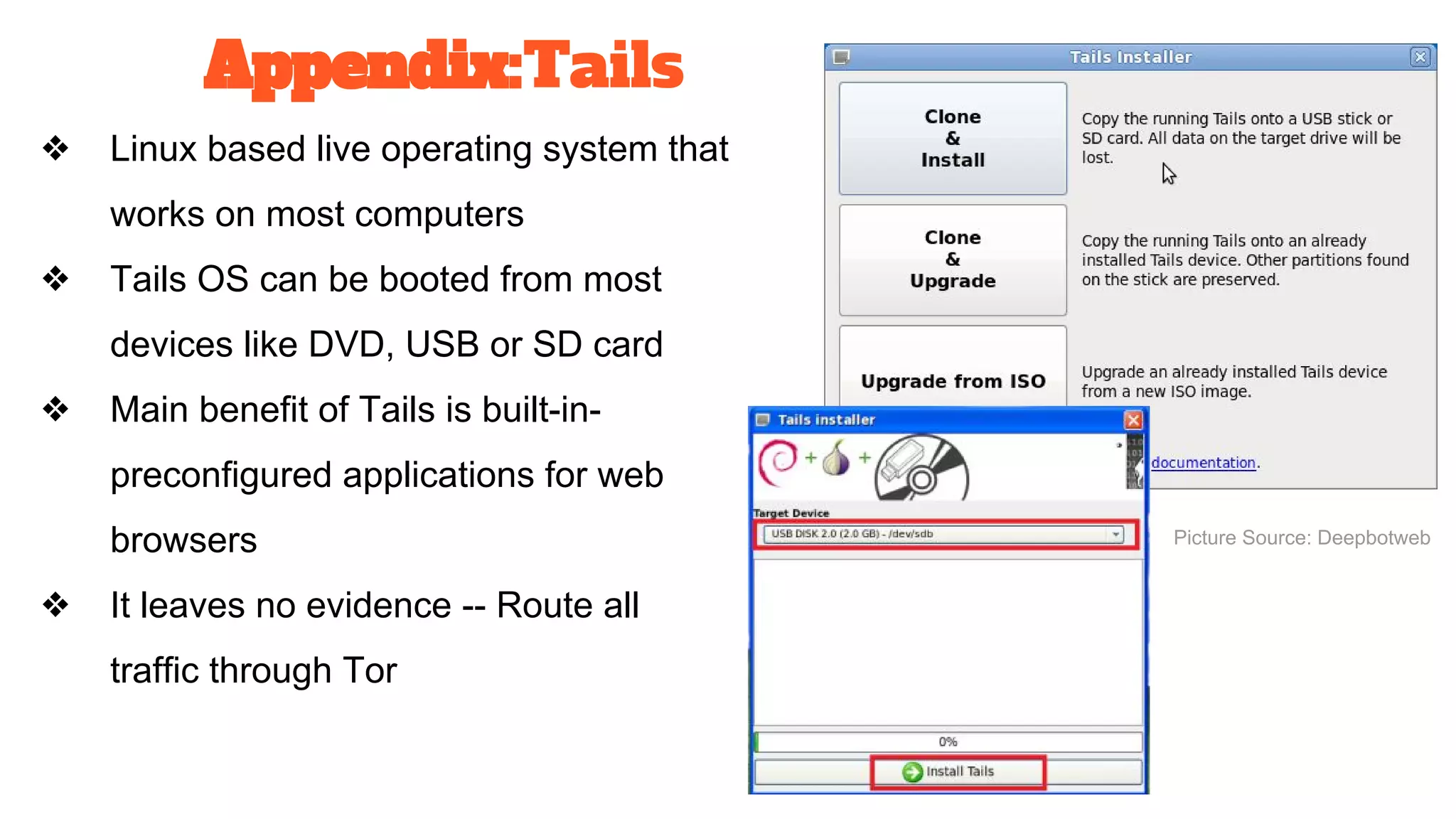
The document discusses the structure and components of the web, highlighting the differences between the surface web, deep web, and dark web, alongside their uses and risks. It covers the benefits of technologies like Tor and Bitcoin, noting their implications for privacy, censorship, and transactions. The document also addresses the associated risks of utilizing the deep web, including criminal information access and data breaches.