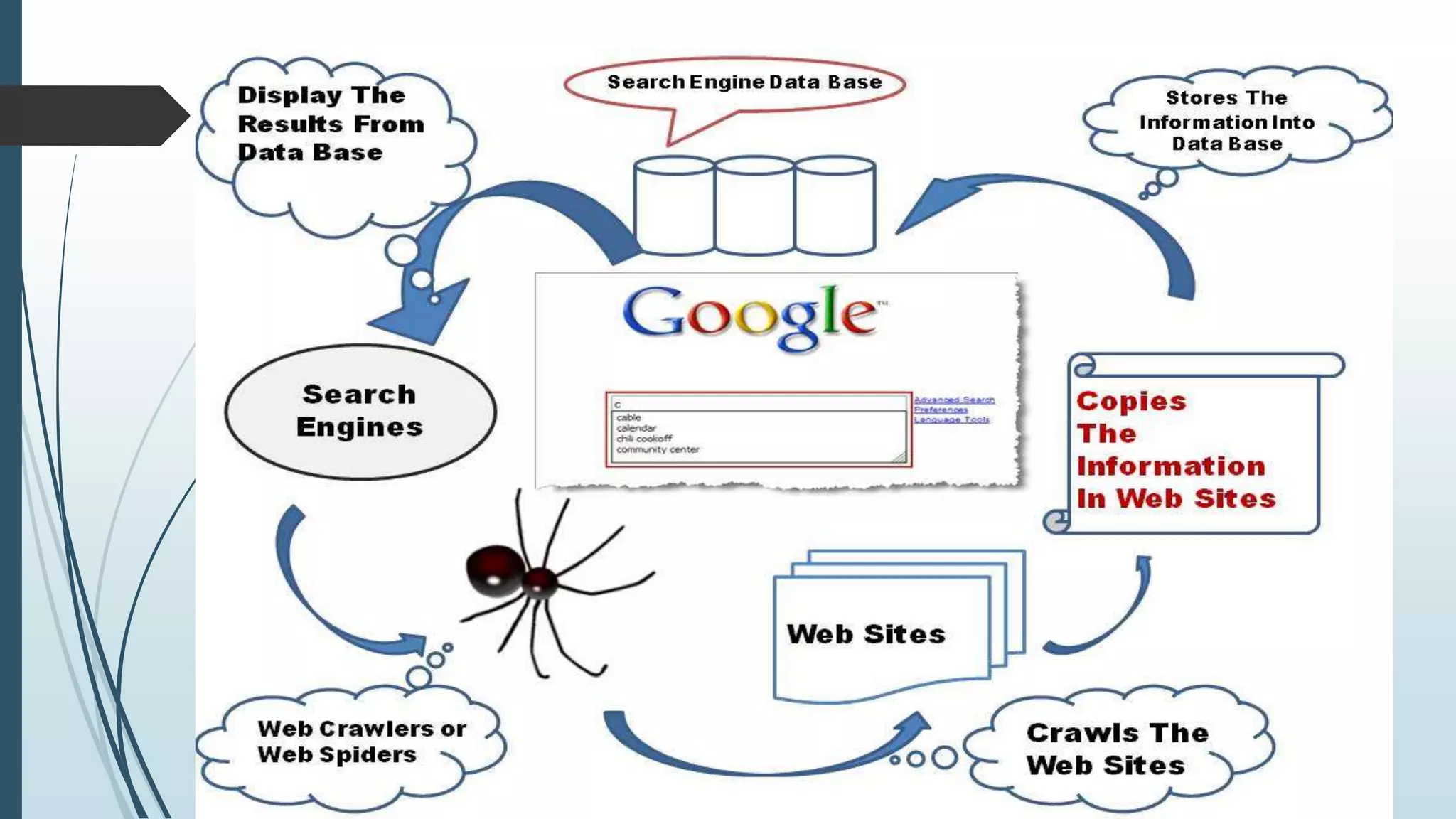
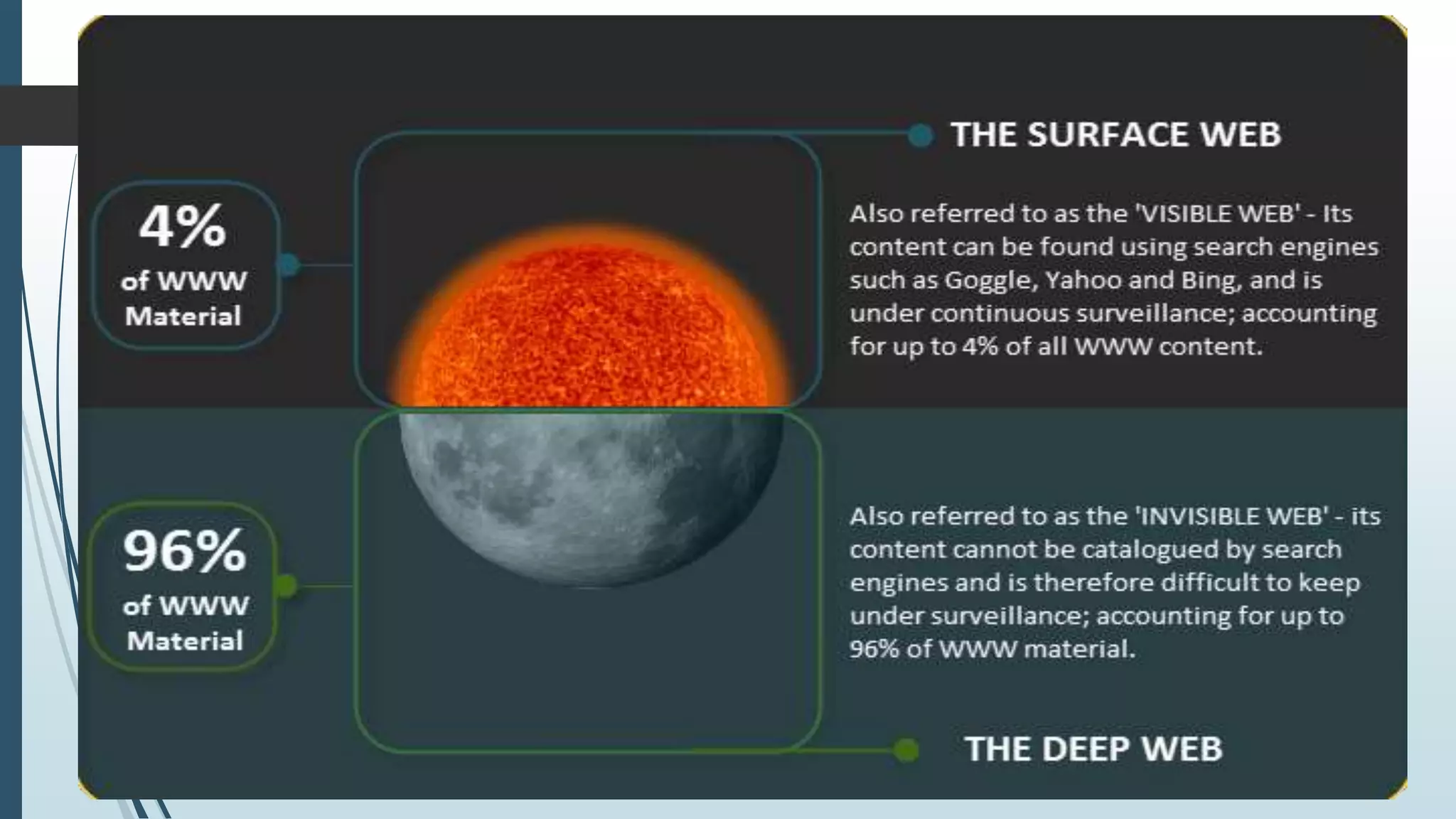
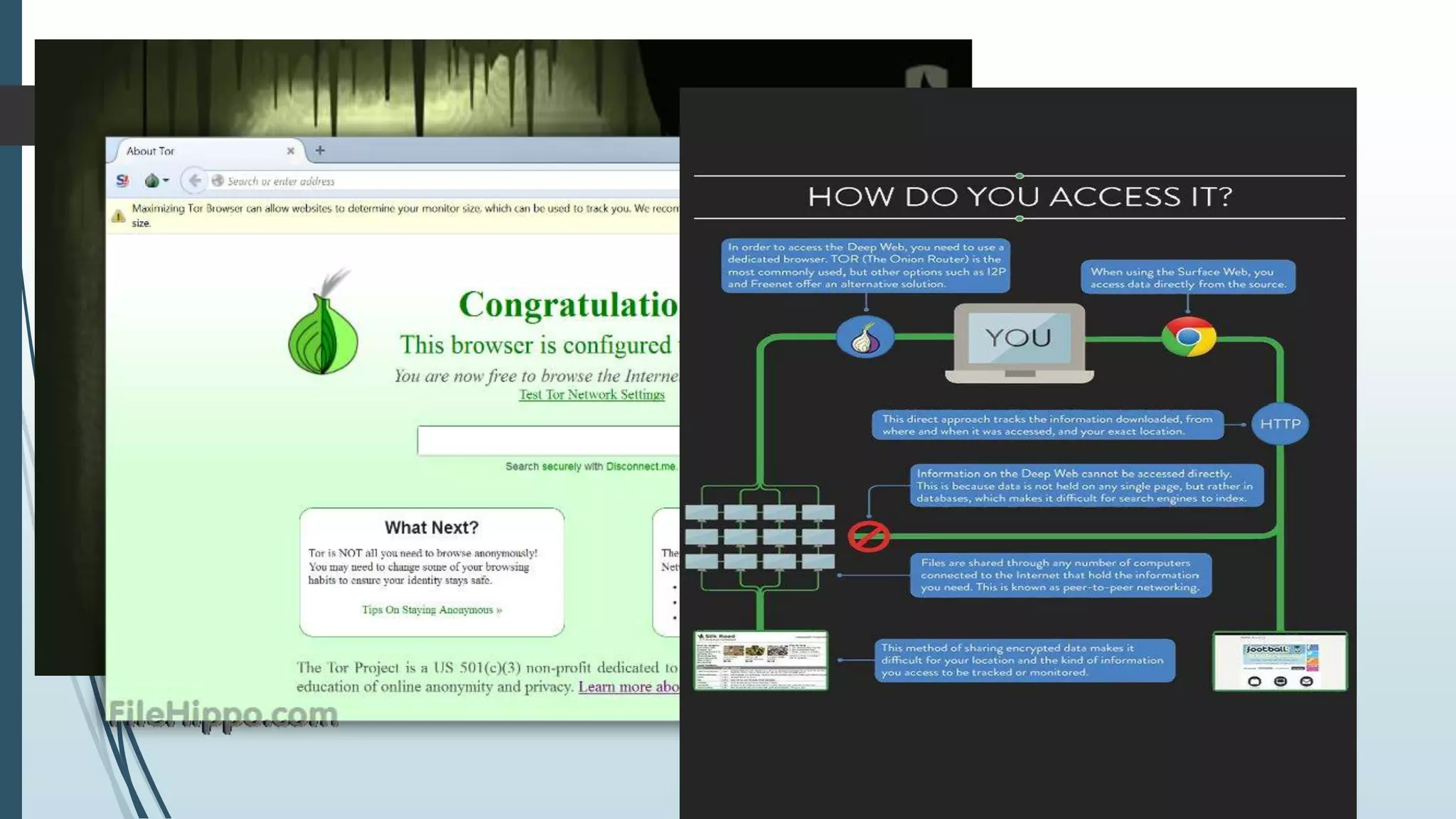
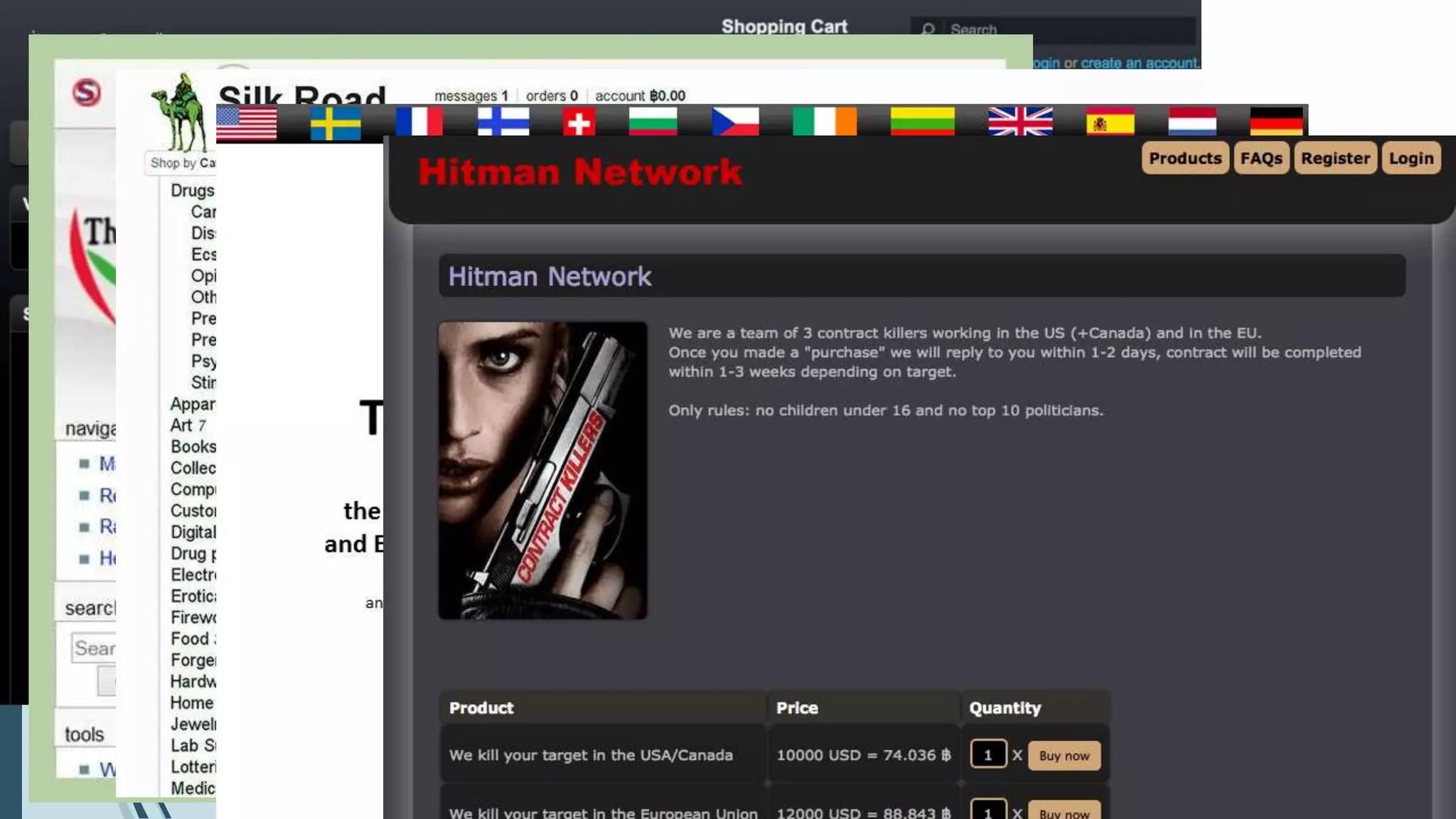
This seminar presentation provides an overview of deep web data extraction. It defines the deep web as content that is not indexed by typical search engines. The presentation covers the history of the deep web, how search engines work, differences between the deep web and surface web, how to access the deep web using tools like Tor, advantages and disadvantages of the deep web, and future applications. The presentation concludes that the deep web provides anonymous access to valuable information not easily accessible otherwise and will continue growing as more users seek online privacy and security.