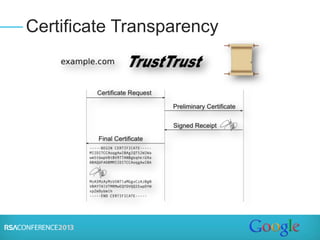
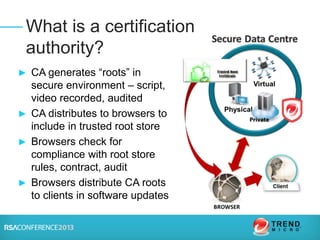
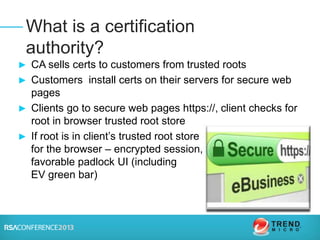
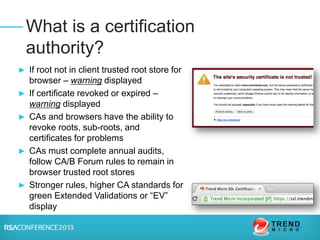
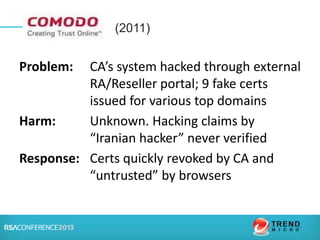
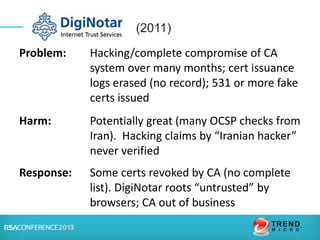
The document discusses certification authorities (CAs) and alternatives to the current CA model. It provides background on what a CA is and how the current system works. It then discusses recent security issues with CAs and the responses to those issues. Finally, it explores some potential alternatives and enhancements to CAs, including DANE, Certificate Transparency, CAA, and public key pinning. The presentation aims to provide context around CAs while also outlining new approaches that could further improve security and trust.





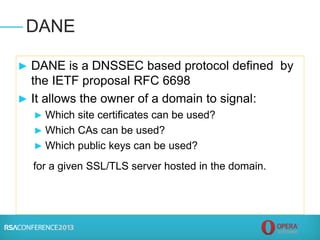
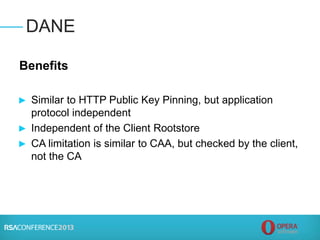
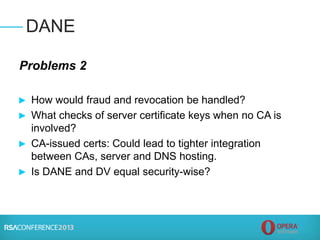
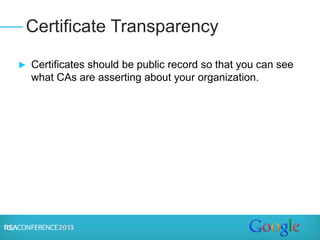
![► Putting it in perspective:
► Certs issued worldwide: 2,000,000 per year
► Bad certs issued: maybe 1,000 over 11 years (~91
bad certs per year) – mostly DigiNotar incident
► Accuracy ratio for certs issued each year: 99.995%
(Error rate 0.005%) – are Passport Office and state
Departments of Motor Vehicles more accurate? [No]
► Significant harm from bad certs? Only likely in
DigiNotar case (actual harm unknown)
► CAs are continuously improving security, processes
Summary and Conclusion](https://image.slidesharecdn.com/tech-t18-150420135133-conversion-gate01/85/Tech-t18-15-320.jpg)