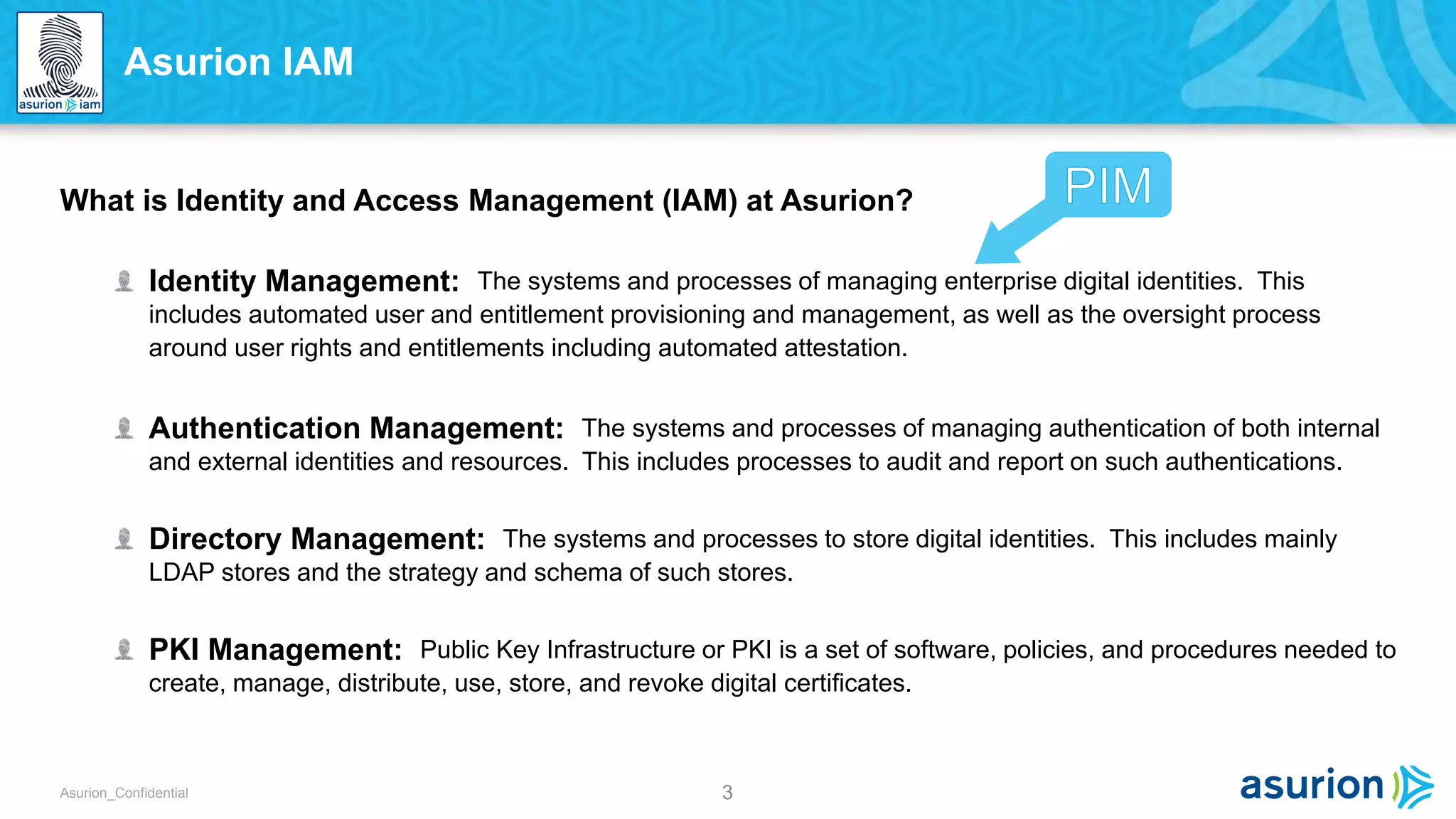
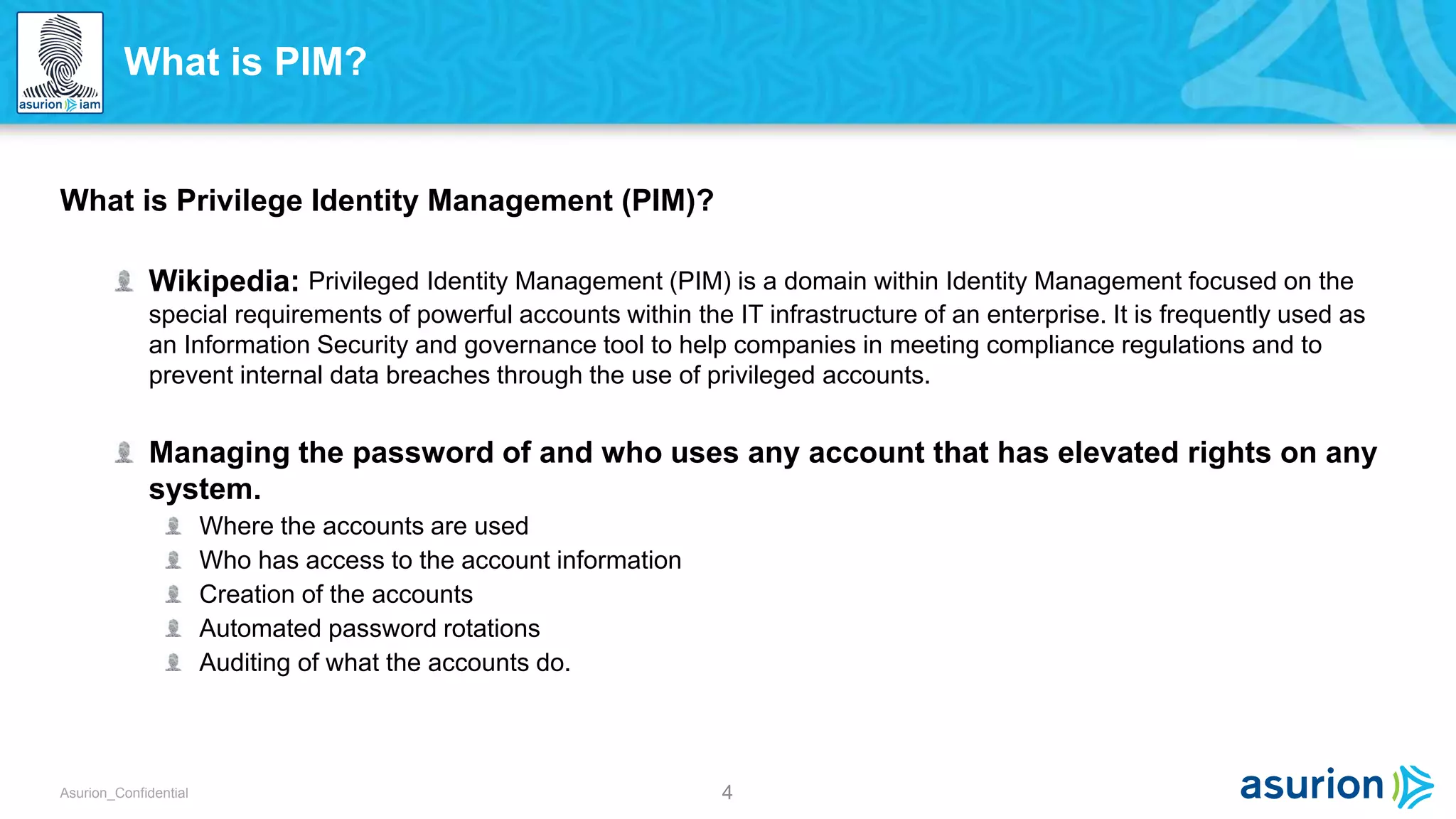
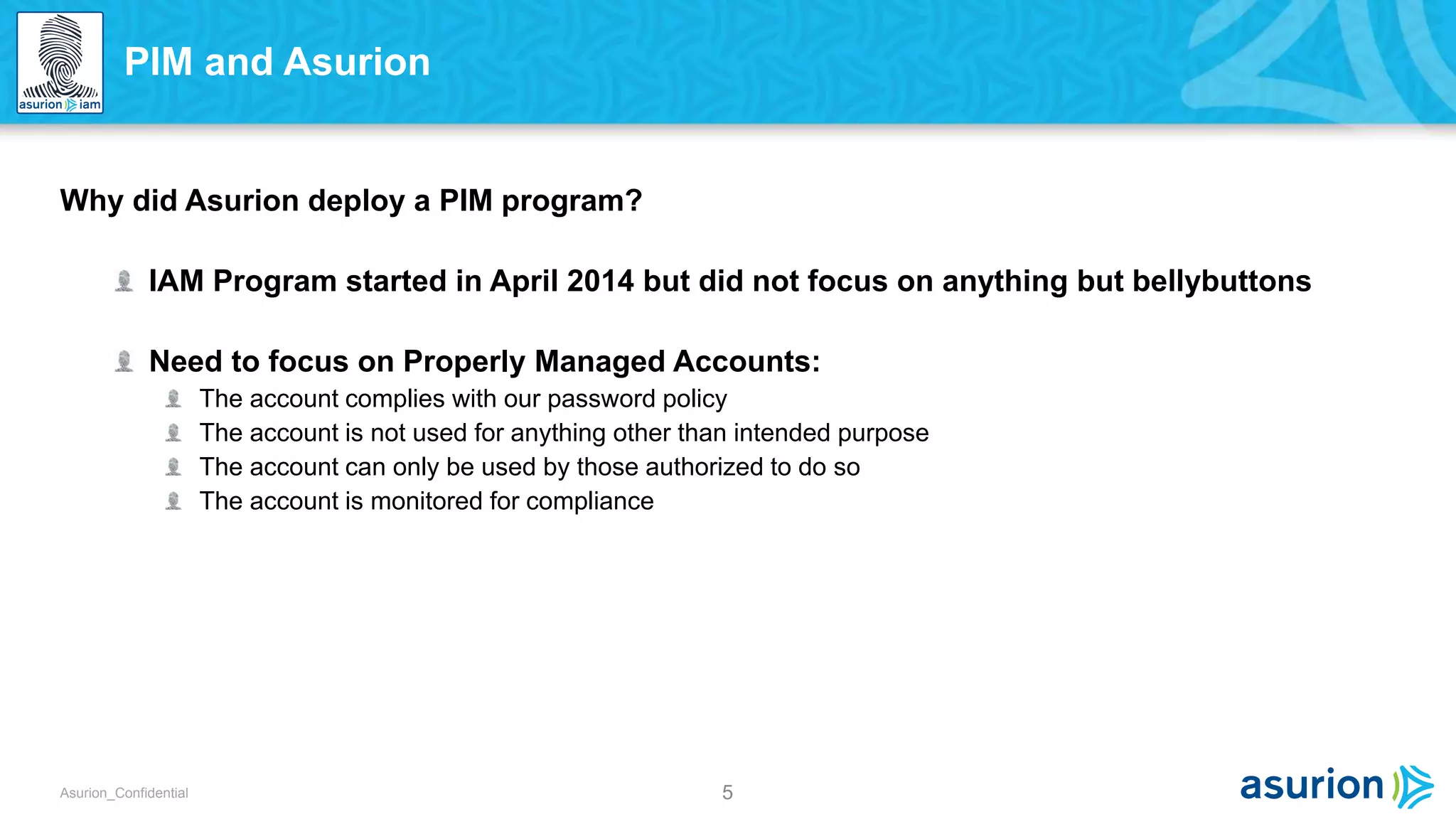
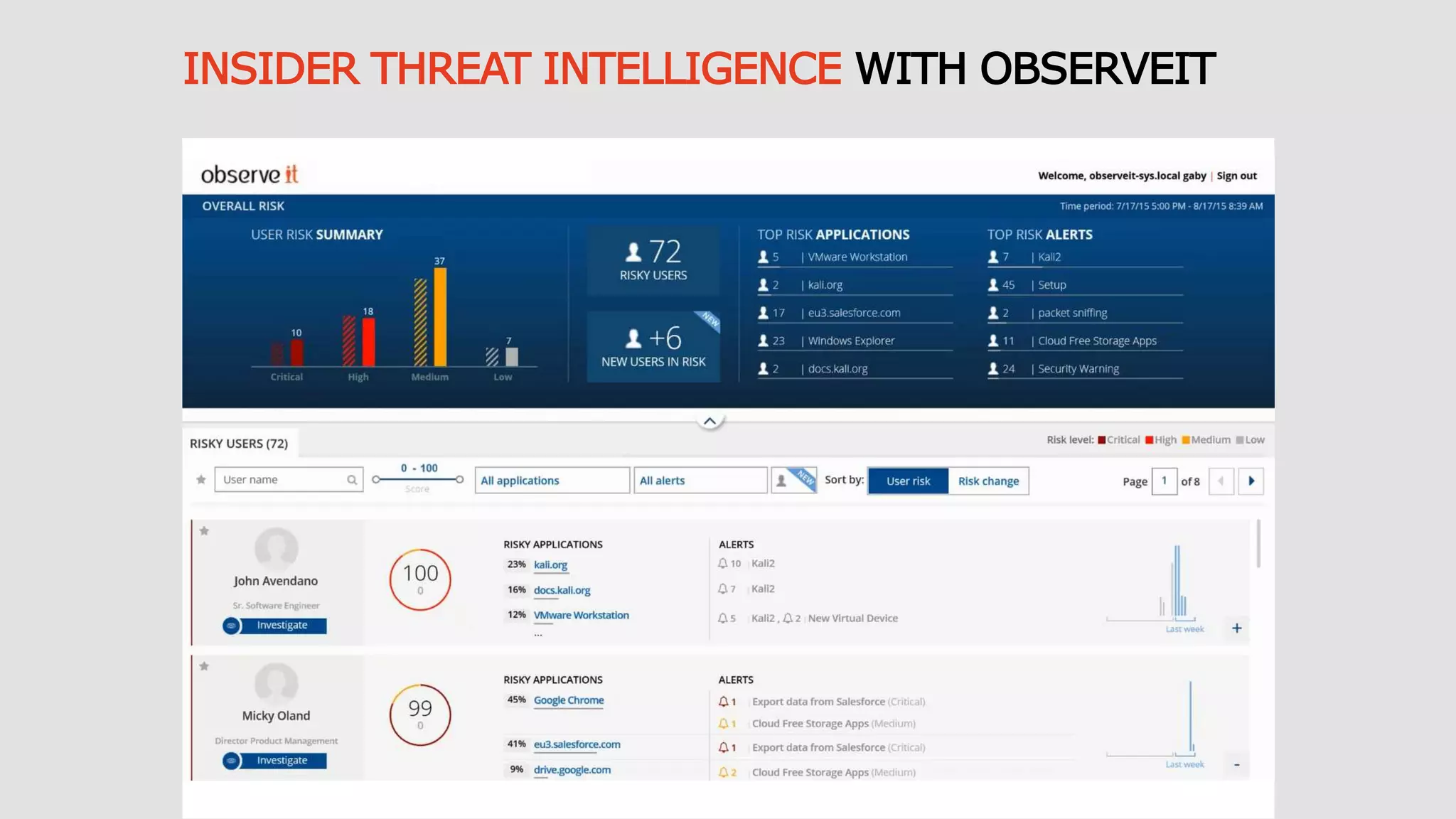
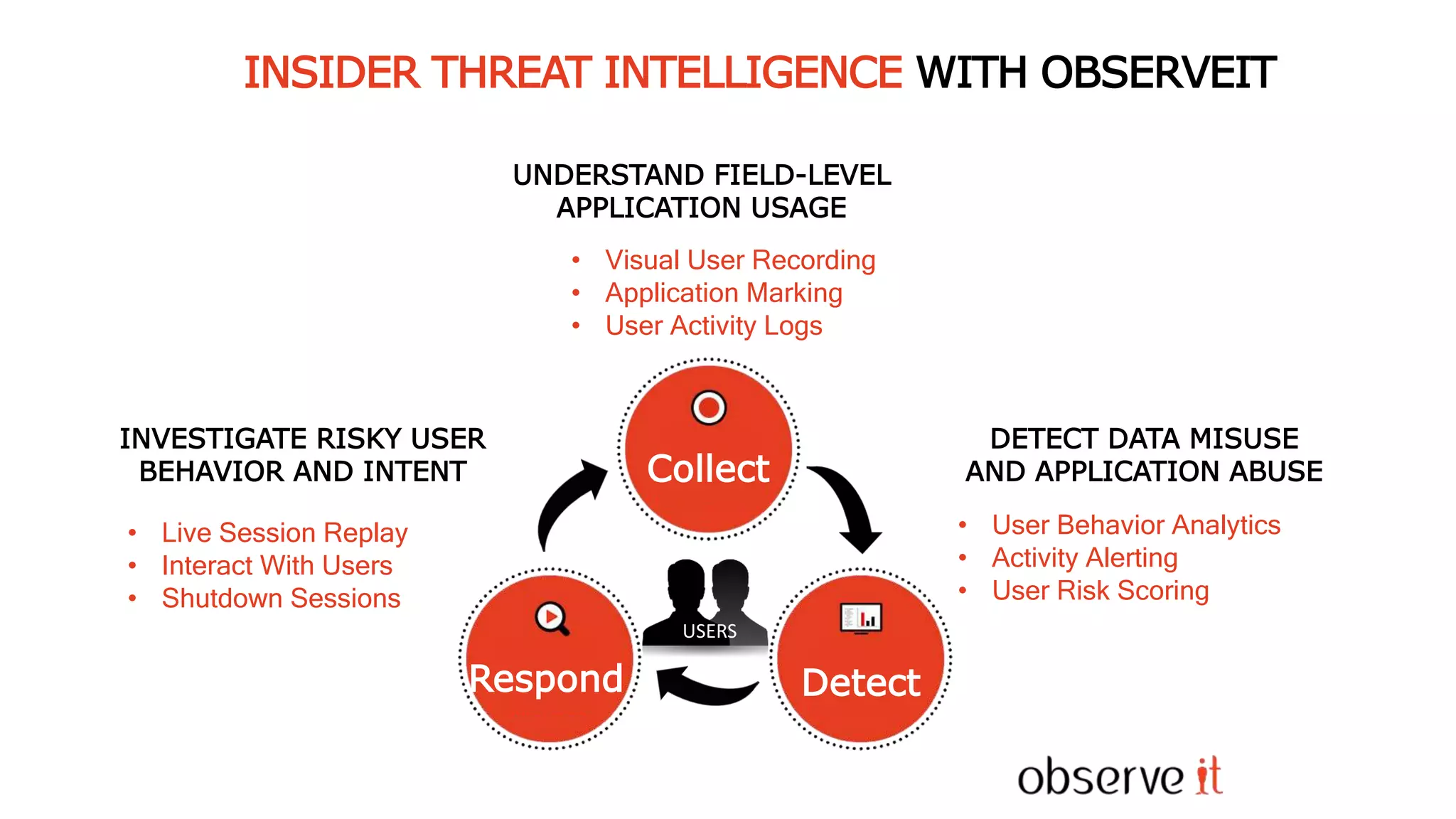
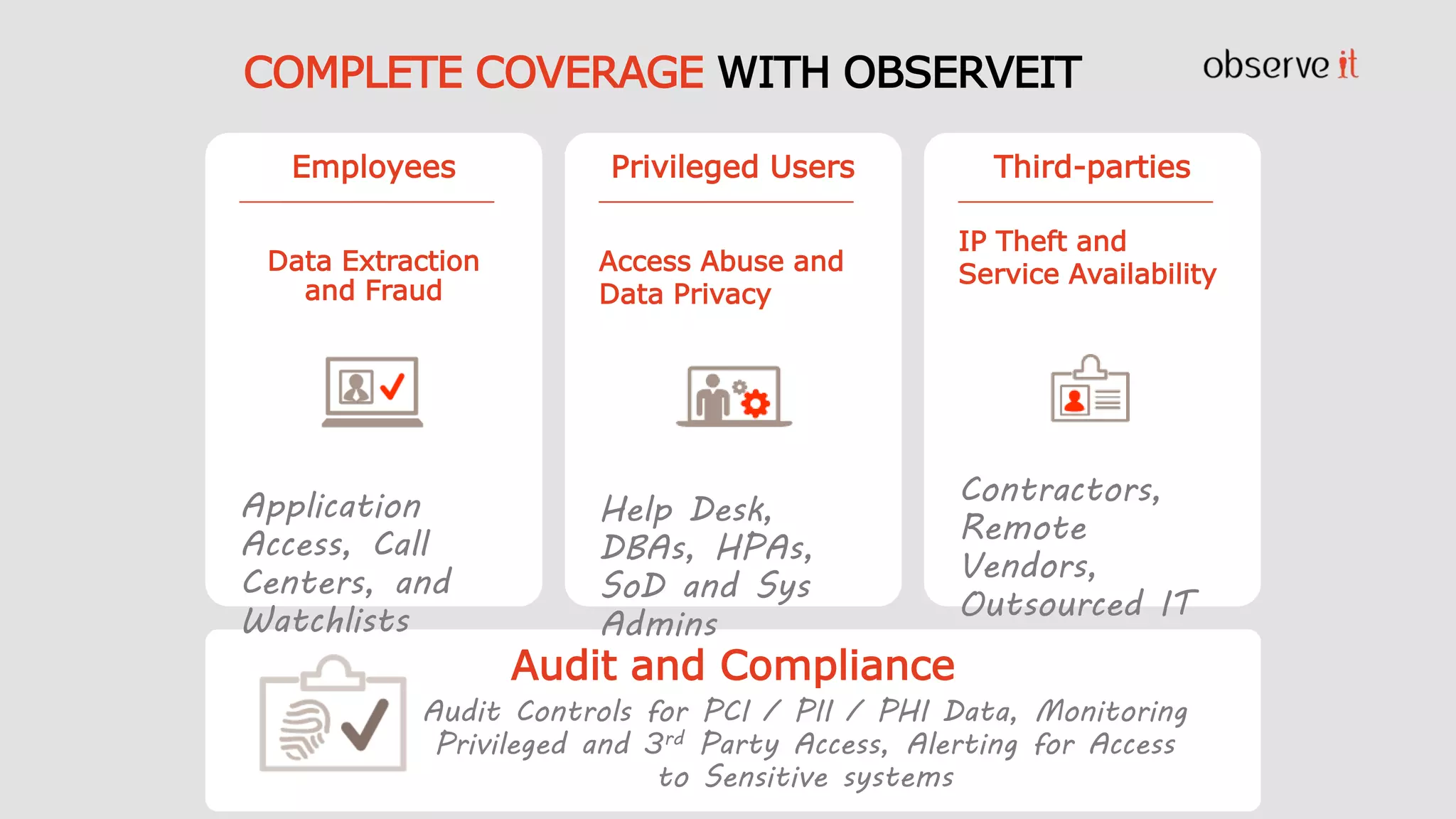
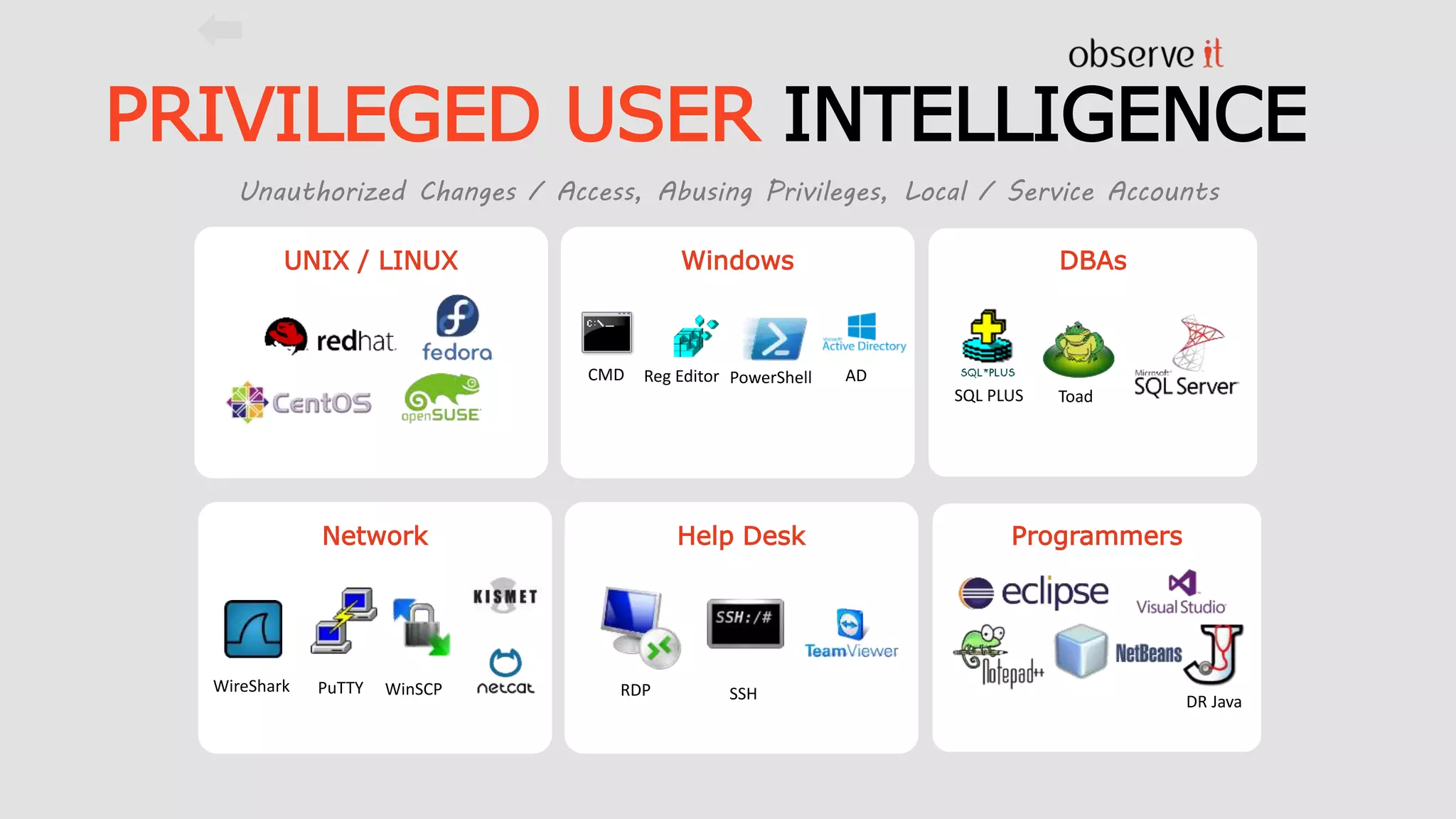
This document discusses Privilege Identity Management (PIM) at Asurion. It provides an overview of why Asurion deployed a PIM program to better manage privileged accounts and identities. Previously, privileged account information was tracked through methods like sticky notes, spreadsheets, and wikis, and accounts were not properly monitored or access controlled. The presentation outlines Asurion's past issues, current PIM practices like using a secure password vault and auditing, and future goals to further improve privileged identity governance.