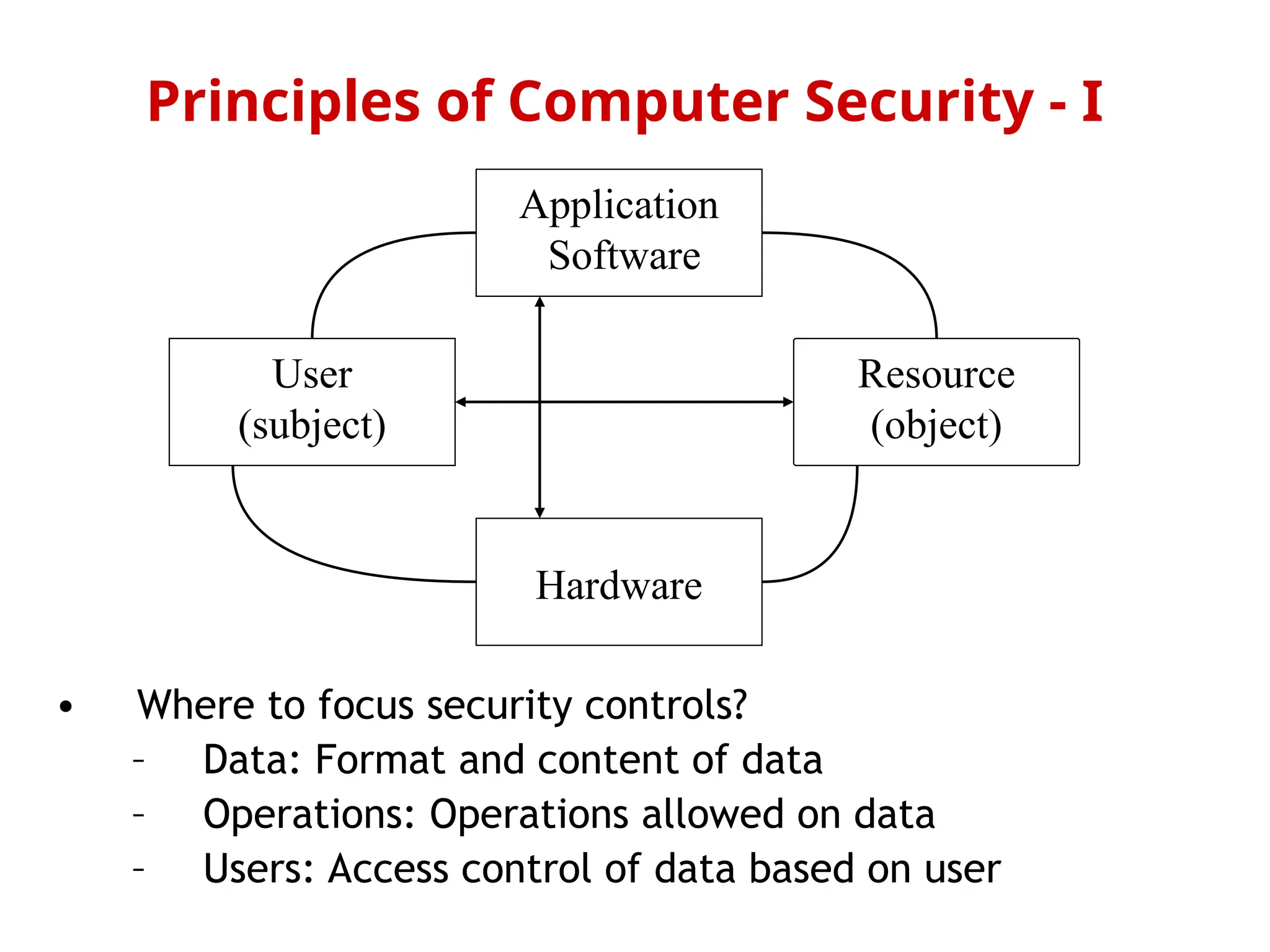
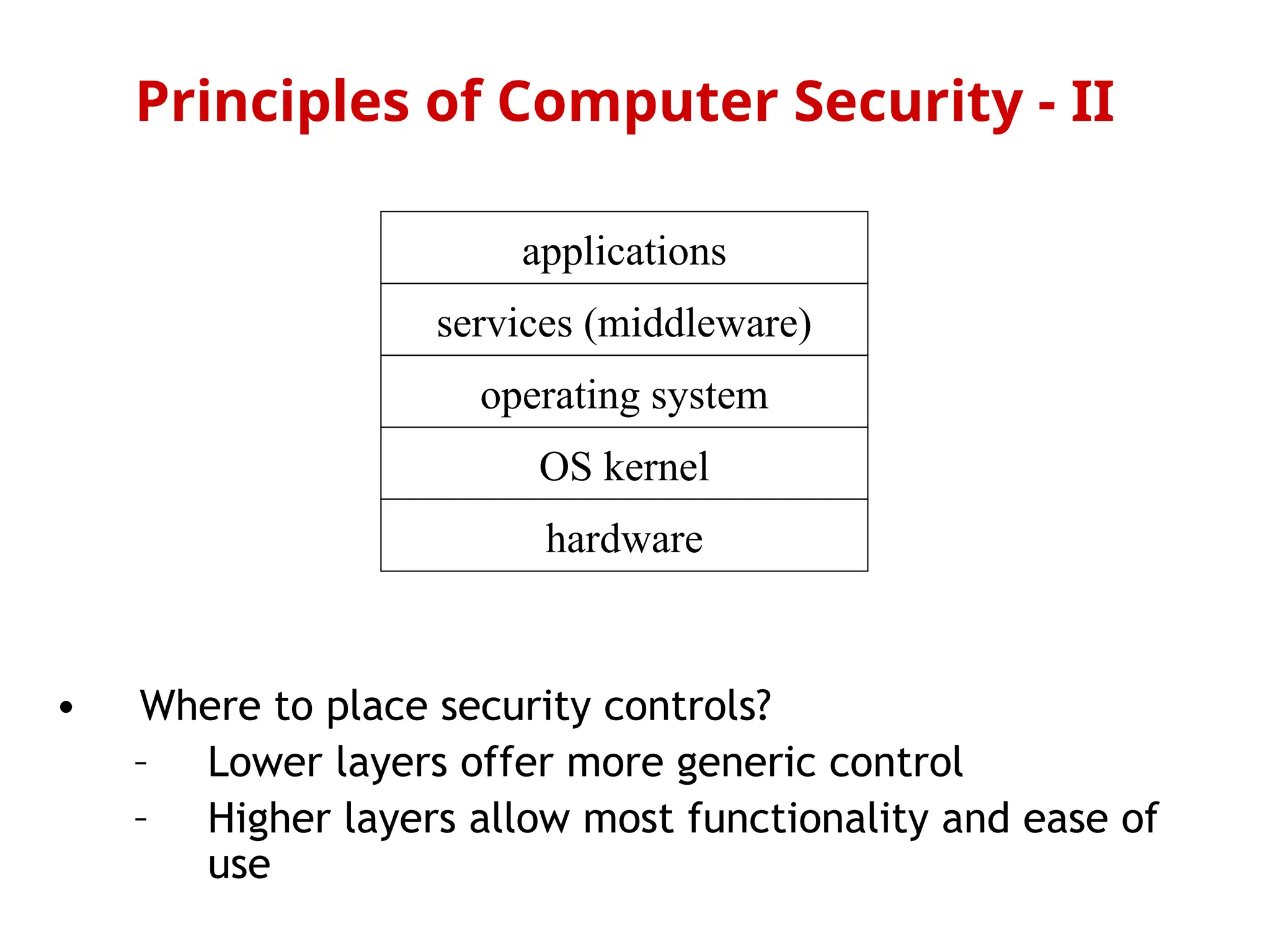
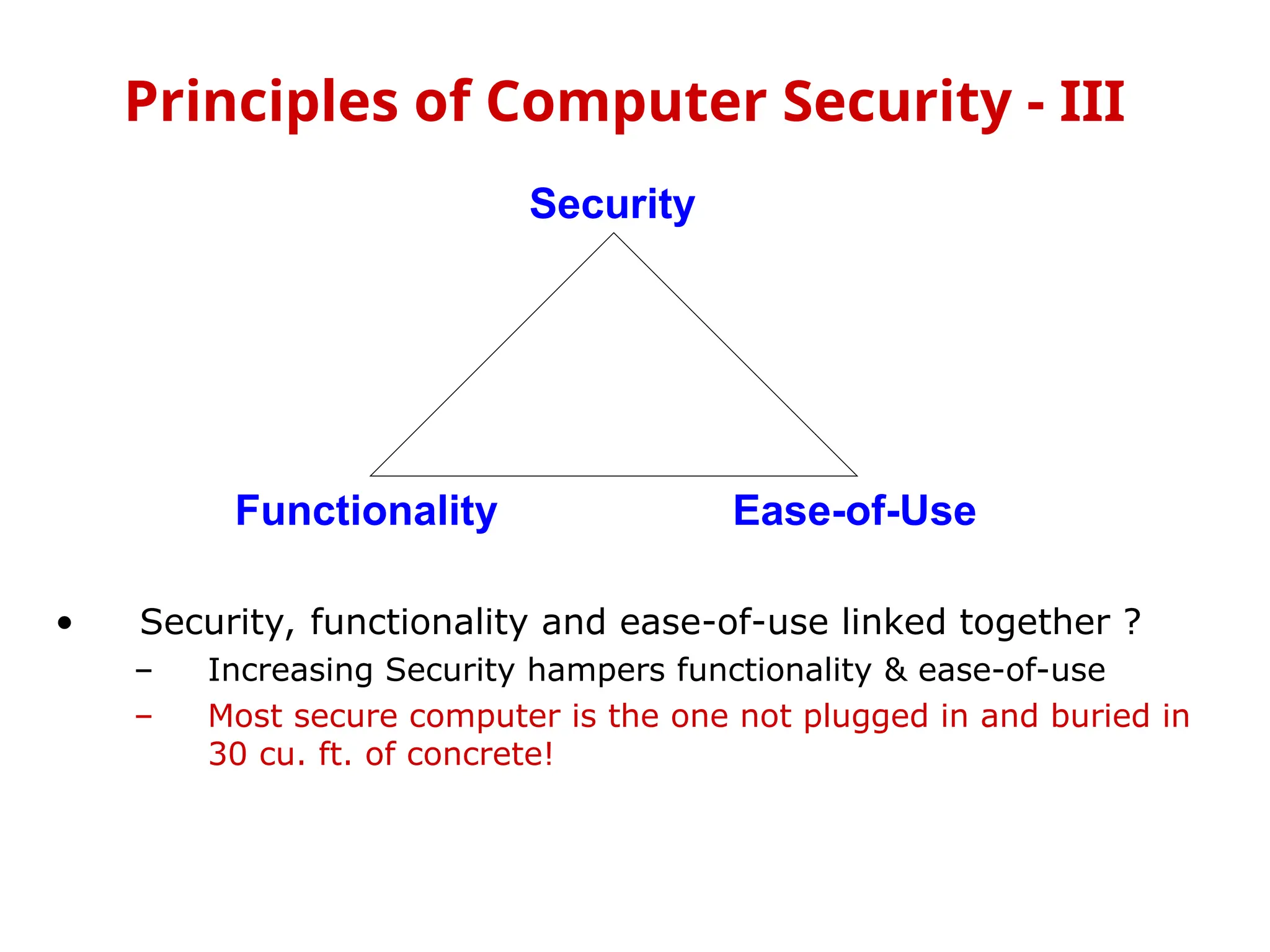
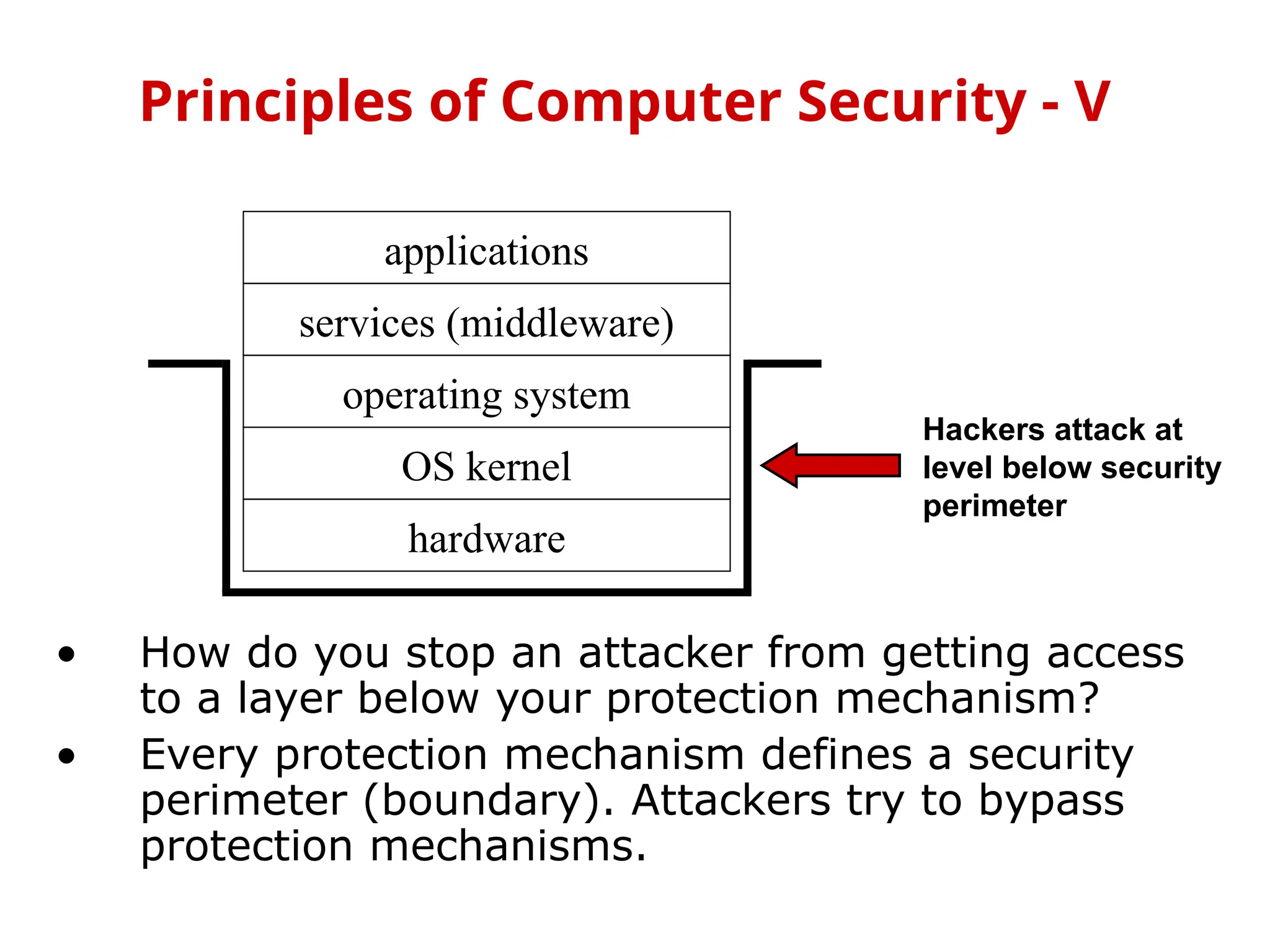
The document outlines the principles of computer security, focusing on the key aspects of confidentiality, integrity, availability, authenticity, and accountability. It discusses goals such as preventing unauthorized information disclosure, ensuring data integrity, and maintaining system availability, emphasizing the need for proper security policies and measures. Additionally, it addresses challenges like user access control, the balance between security and usability, and specific considerations for sensitive information such as medical records.