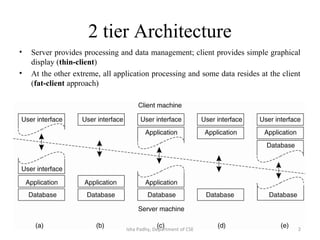
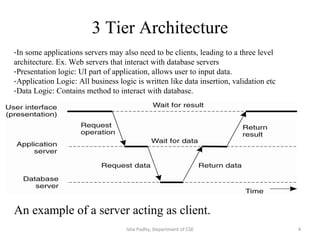
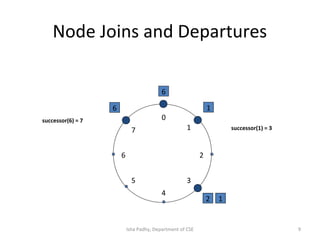
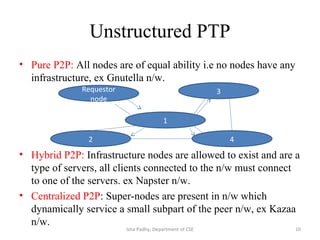
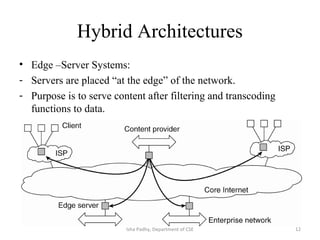
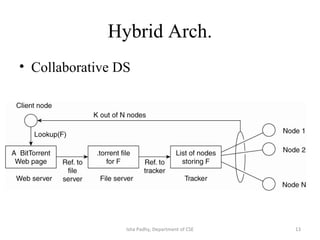
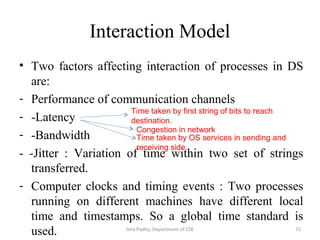
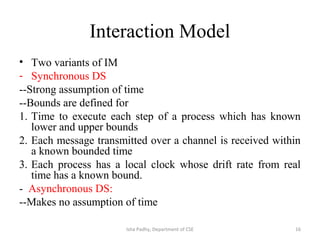
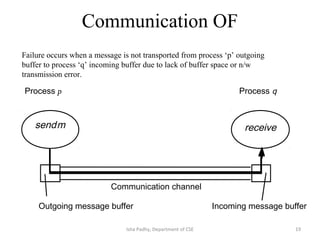
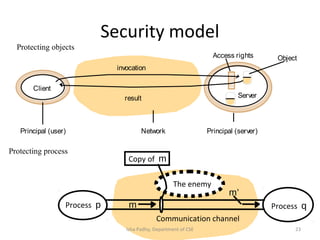
The document discusses different architectural models for distributed systems including tiered, two-tier, three-tier, decentralized, structured (Chord), and hybrid architectures. It covers concepts like interaction models, failure models, and security models that are important for designing distributed systems. The interaction model accounts for latency, bandwidth, and clock synchronization issues. The failure model defines process and communication channel omission, arbitrary, and timing failures. The security model aims to protect objects, processes, and communication channels against unauthorized access.