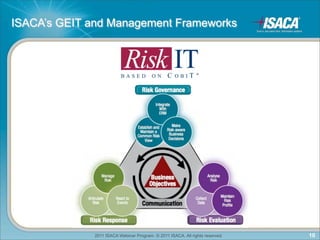
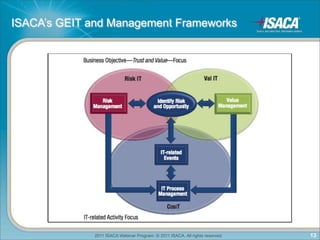
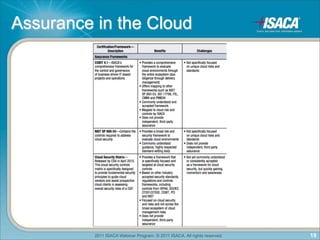
The document discusses cloud computing. It defines cloud computing as a pay-as-you-go model for using applications, development platforms, and IT infrastructure. It outlines some of the key domains in cloud computing including architecture, governance, compliance, security, and operations. It also discusses some of the key drivers and challenges of cloud computing. Finally, it discusses frameworks that can be used for assurance in the cloud such as COBIT, SOC reports, ISO27001, and others.