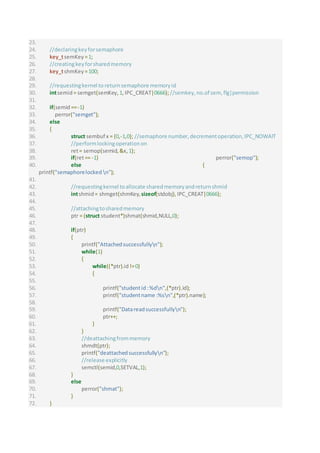
The document describes code that uses semaphores to synchronize shared memory access between writing and reading processes. The writing process writes data to a shared memory structure and the reading process reads the data, waiting for new data to be written. Semaphores are used to lock access to the shared memory so that only one process can write or read at a time, similar to solving the producer-consumer problem. The code includes two programs, one for writing and one for reading, that demonstrate using semaphores and shared memory.
![NarayanLal Menariya August30,2018
Synchronization of shared memory using Semaphore
Using semaphores synchronization can beprovided between two or moreprocess. Here
i am going to writea codewhich will clear that how a semaphorecan be used with
shared memory to providesynchronization between writing processand reading
process.
The following codewrites structurein shared memory and read it back. Oncethe writing
process will writefirst messageinto shared memory receiver process will read it
immediately and will wait for second messageto arriveinto shared memory. Receiver
process will be in sleep statetill thenew data will arrivein shared memory. Just like
producer-consumer problem.
This code is written by meonly and not copied from anywhere.
Code : writeIn_sharedMemory_UsingSemaphore.c
1. /*
2. Narayan Lal Menariya:August30,2018
3. * */
4. #include<sys/sem.h>
5. #include<stdio.h>
6. #include<sys/shm.h>
7. #include<sys/ipc.h>
8. #include<string.h>
9. #include "file.h"
10.
11. int counter;
12.
13.
14. struct student
15. {
16. intid;
17. char name[20];
18. }stdobj;
19.
20. int main()
21. {
22. intret;
23. char choice;
24. char msg[20];
25. struct student*ptr;
26.
27. //declaringkeyforsemaphore
28. key_tsemKey =1;
29. //creatingkeyforsharedmemory
30. key_tshmKey =100;](https://image.slidesharecdn.com/messagequeuesharedmemory-180830174120/75/Synchronization-of-shared-memory-using-semaphores-1-2048.jpg)
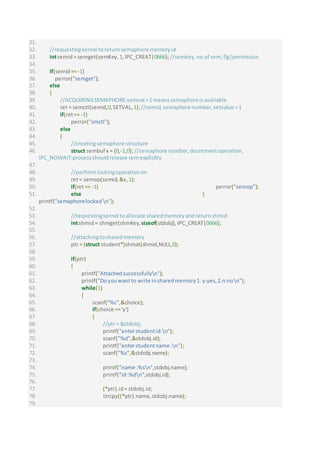
![80.
81. printf("nDatawrittensuccessfullyn");
82. ptr++;
83. printf("writechoice y/n:");
84. }
85. if(choice =='n')
86. {
87.
88. break;
89. }
90.
91. }
92.
93. //deattachingfrommemory
94. shmdt(ptr);
95. printf("deattachedsuccessfullyn");
96. //releasingsemaphore
97. semctl(semid,0,SETVAL,1);
98.
99. }
100. else
101. perror("shmat");
102. }
103. }
104. }
105. return 0;
106. }
Code :Read_UsingSemaphore.c
1. /*
2. Narayan Lal Menariya:August30,2018
3. * */
4. #include<sys/sem.h>
5. #include<stdio.h>
6. #include<sys/shm.h>
7. #include<sys/ipc.h>
8. #include<string.h>
9.
10.
11. struct student
12. {
13. intid;
14. char name[20];
15. }stdobj;
16.
17. int main()
18. {
19. intret;
20. char choice;
21. char msg[20];
22. struct student*ptr;](https://image.slidesharecdn.com/messagequeuesharedmemory-180830174120/85/Synchronization-of-shared-memory-using-semaphores-3-320.jpg)