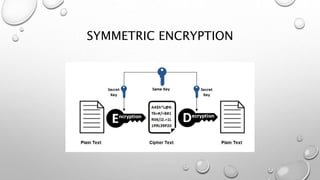
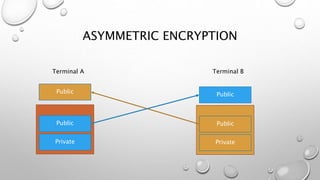
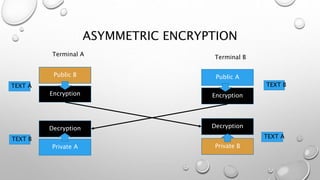
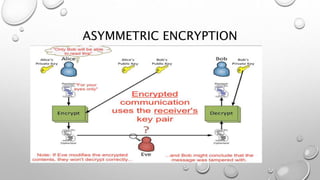
The document discusses different methods of encryption, comparing symmetric and asymmetric encryption. Symmetric encryption uses a single key for both encryption and decryption, while asymmetric encryption utilizes a pair of keys (public and private) for secure communication. It also distinguishes between encoding, encryption, and hashing, highlighting their purposes and reversibility.