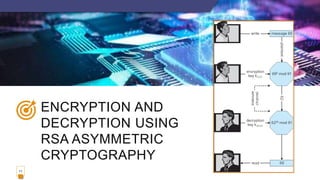
1. Cryptography is the broadest security tool available that allows for secure communication over insecure mediums. It provides confidentiality through encryption.
2. Encryption algorithms use a set of keys to encrypt messages into ciphertexts and decrypt ciphertexts back into messages. The encryption and decryption functions must be efficiently computable.
3. Symmetric encryption uses the same key to encrypt and decrypt, while asymmetric encryption uses a public key to encrypt and a private key to decrypt, allowing for secure communication without having to share private keys.