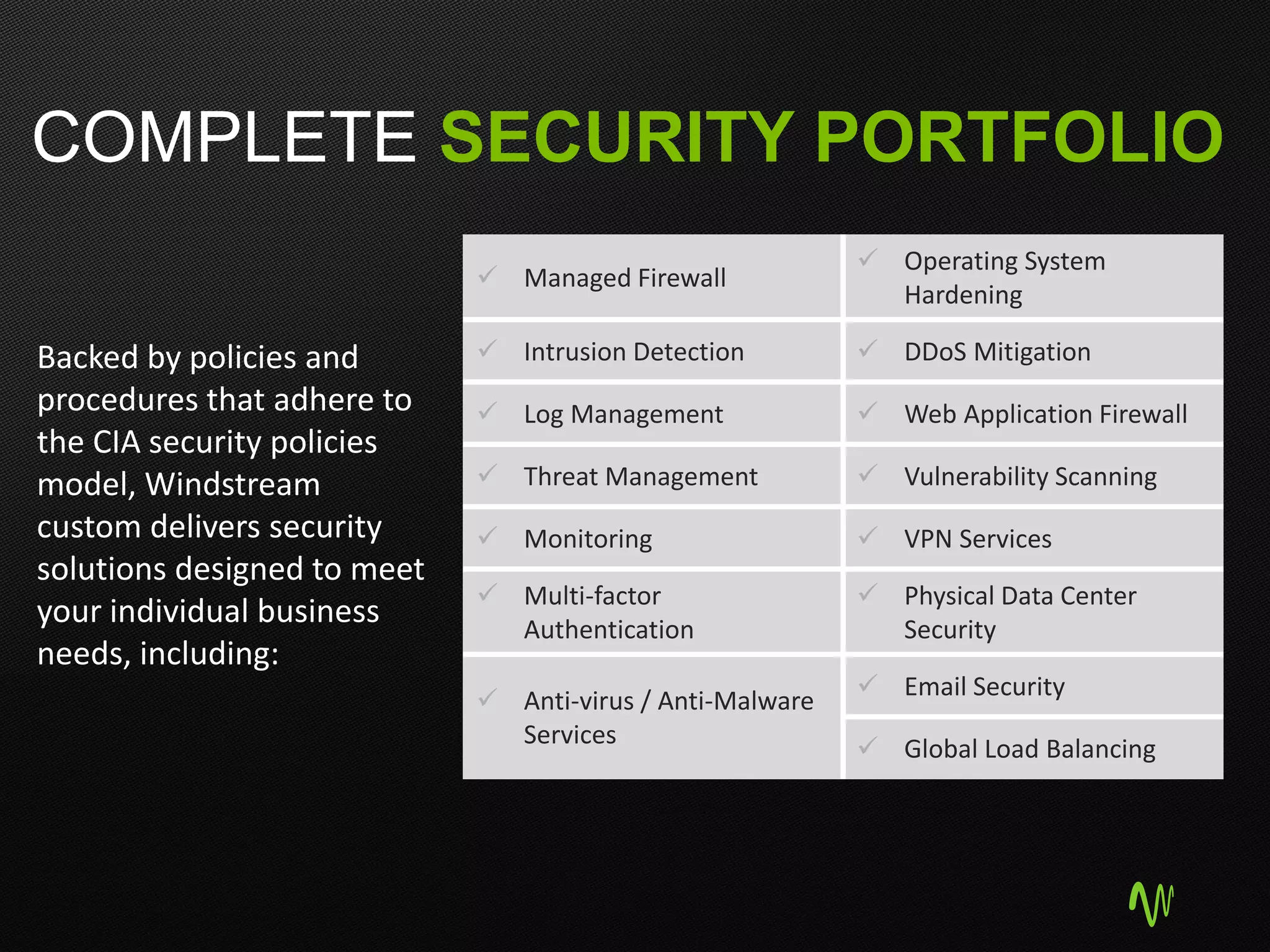
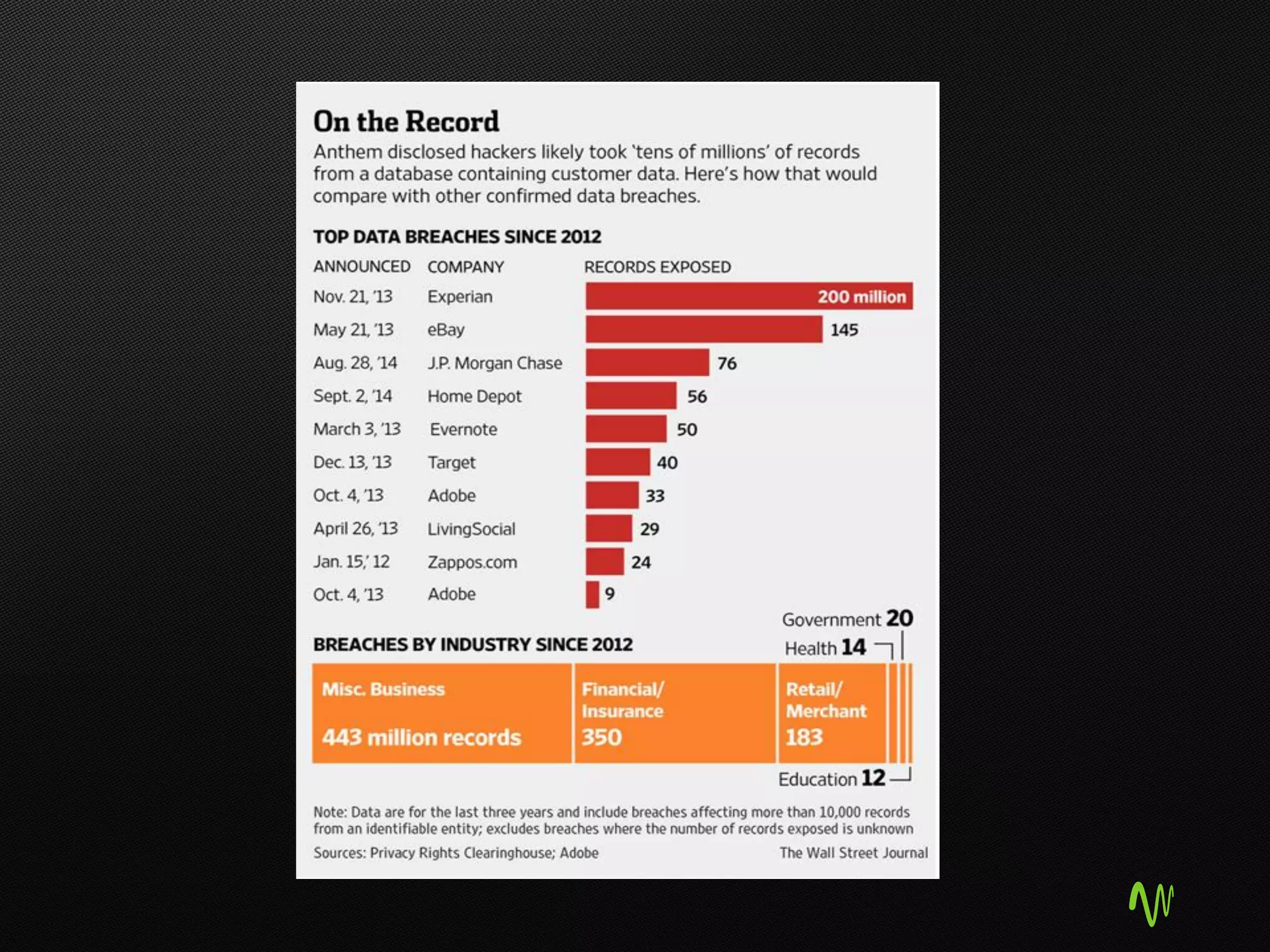
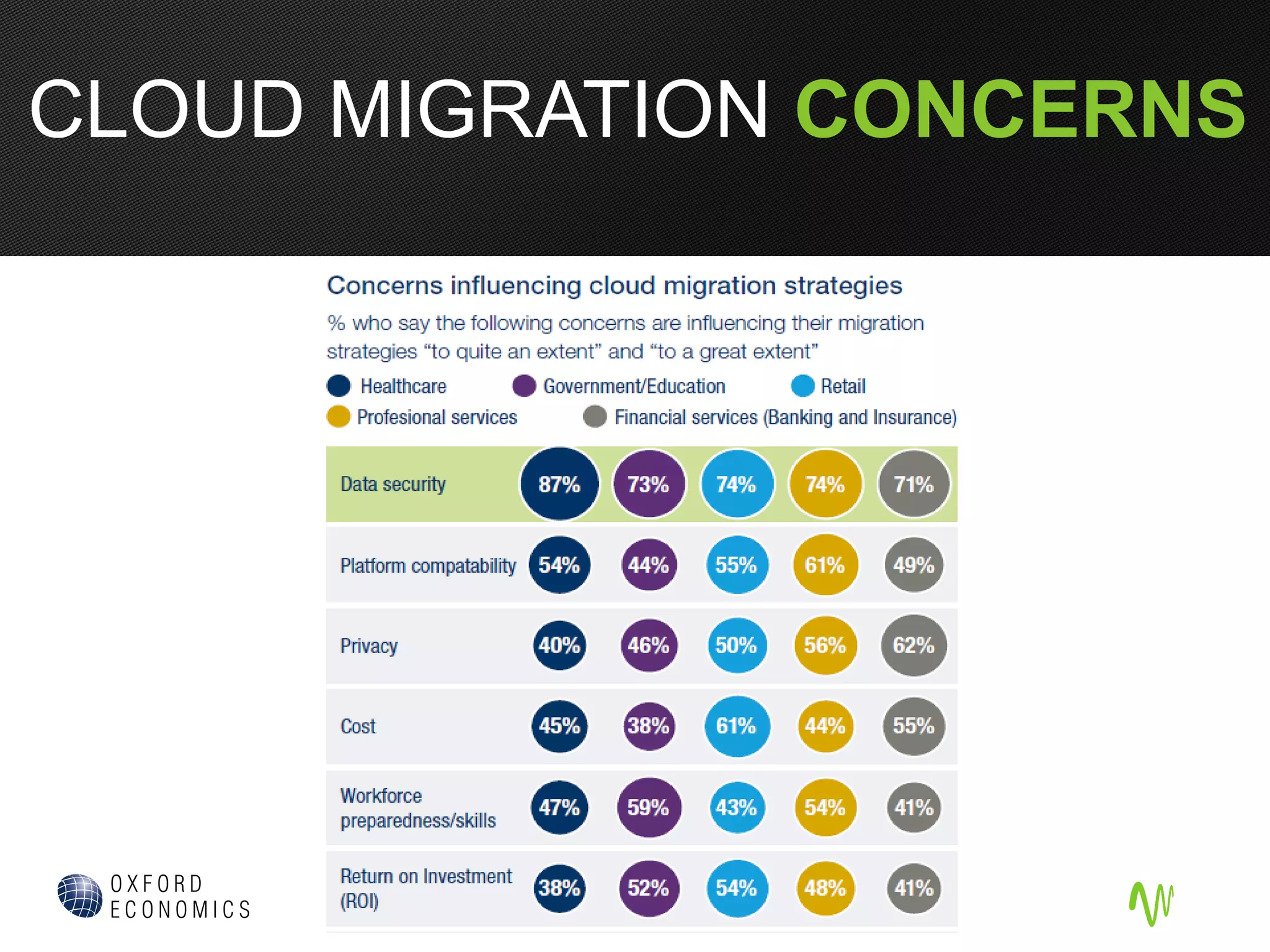
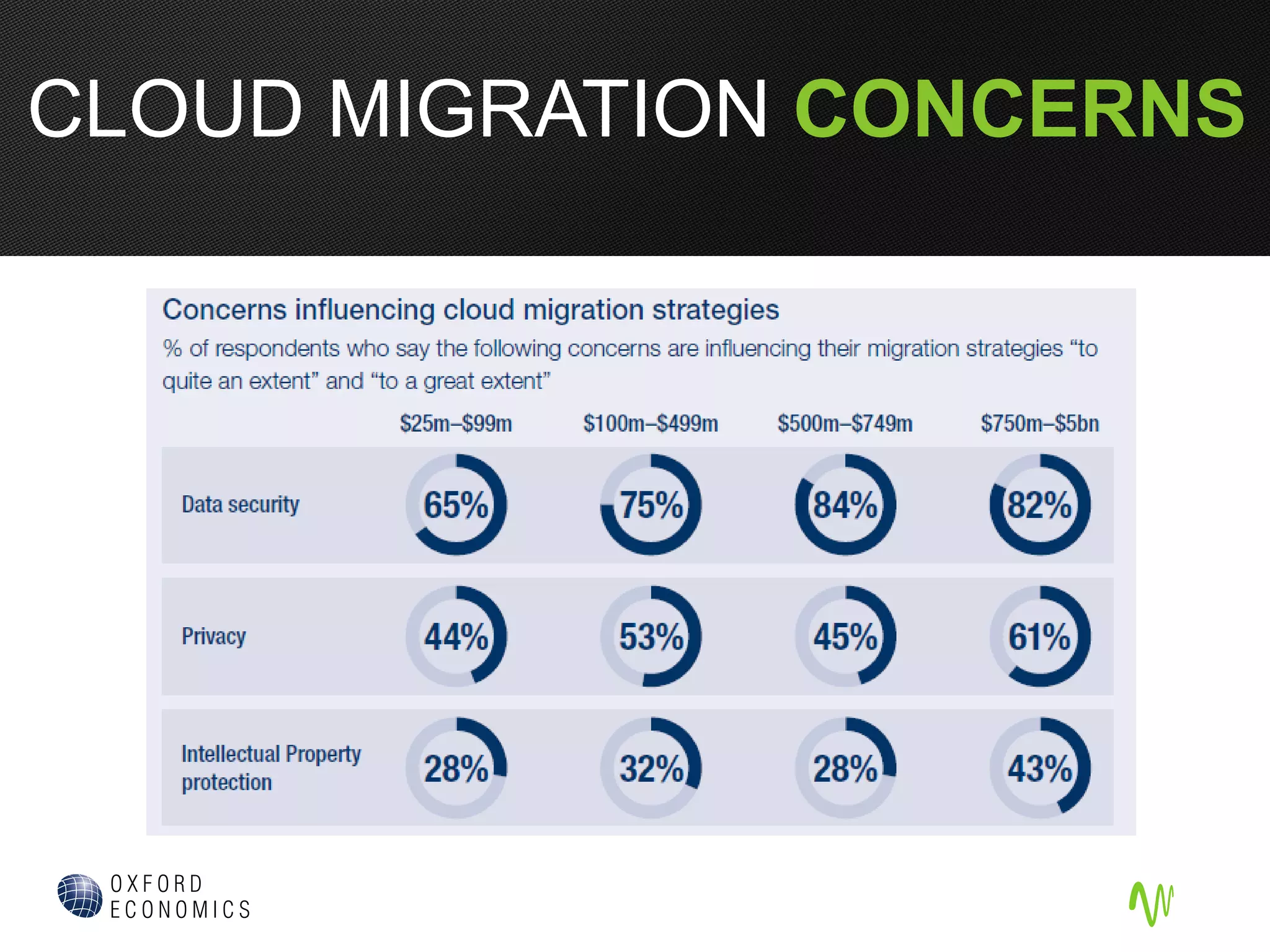
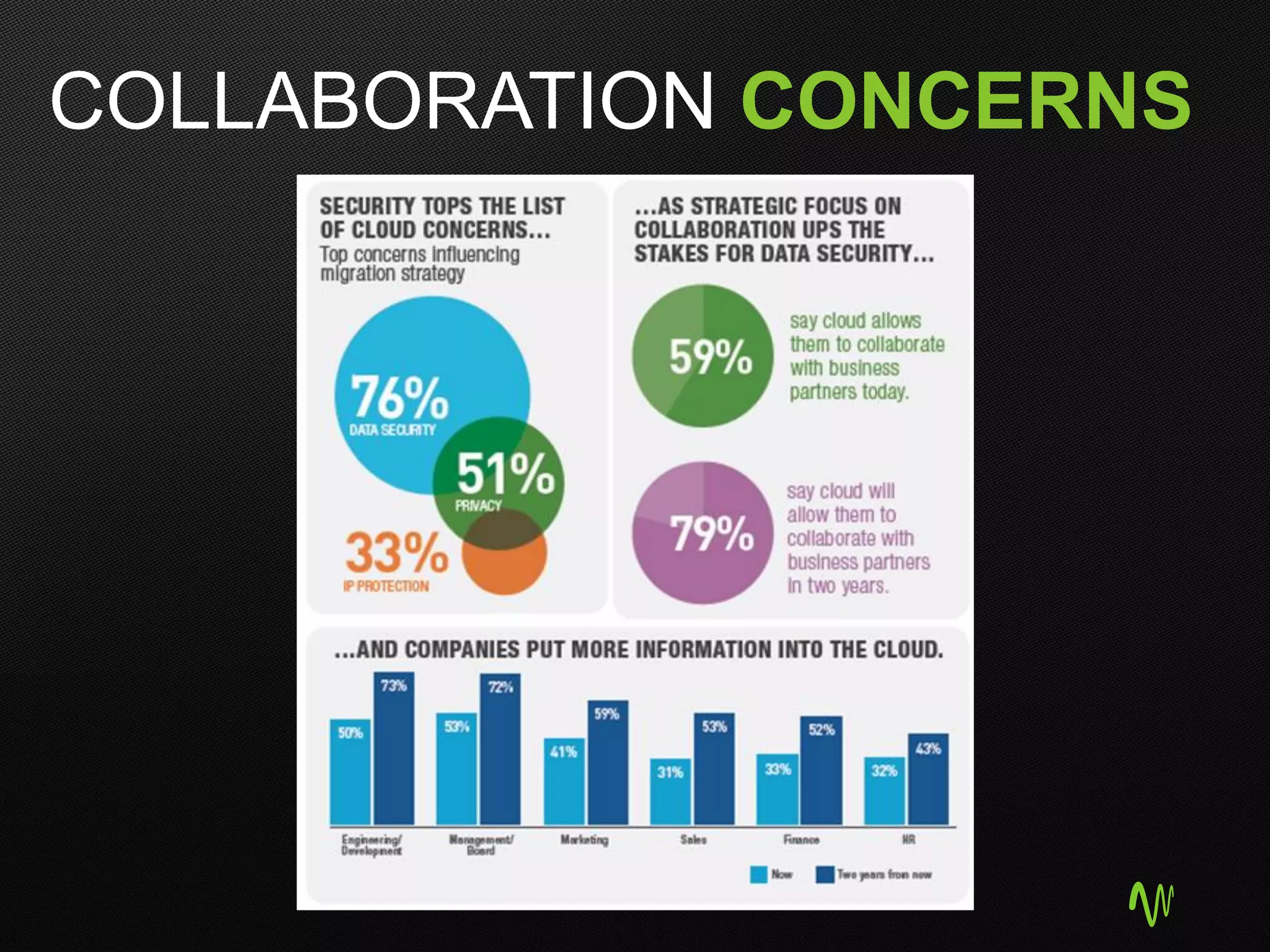
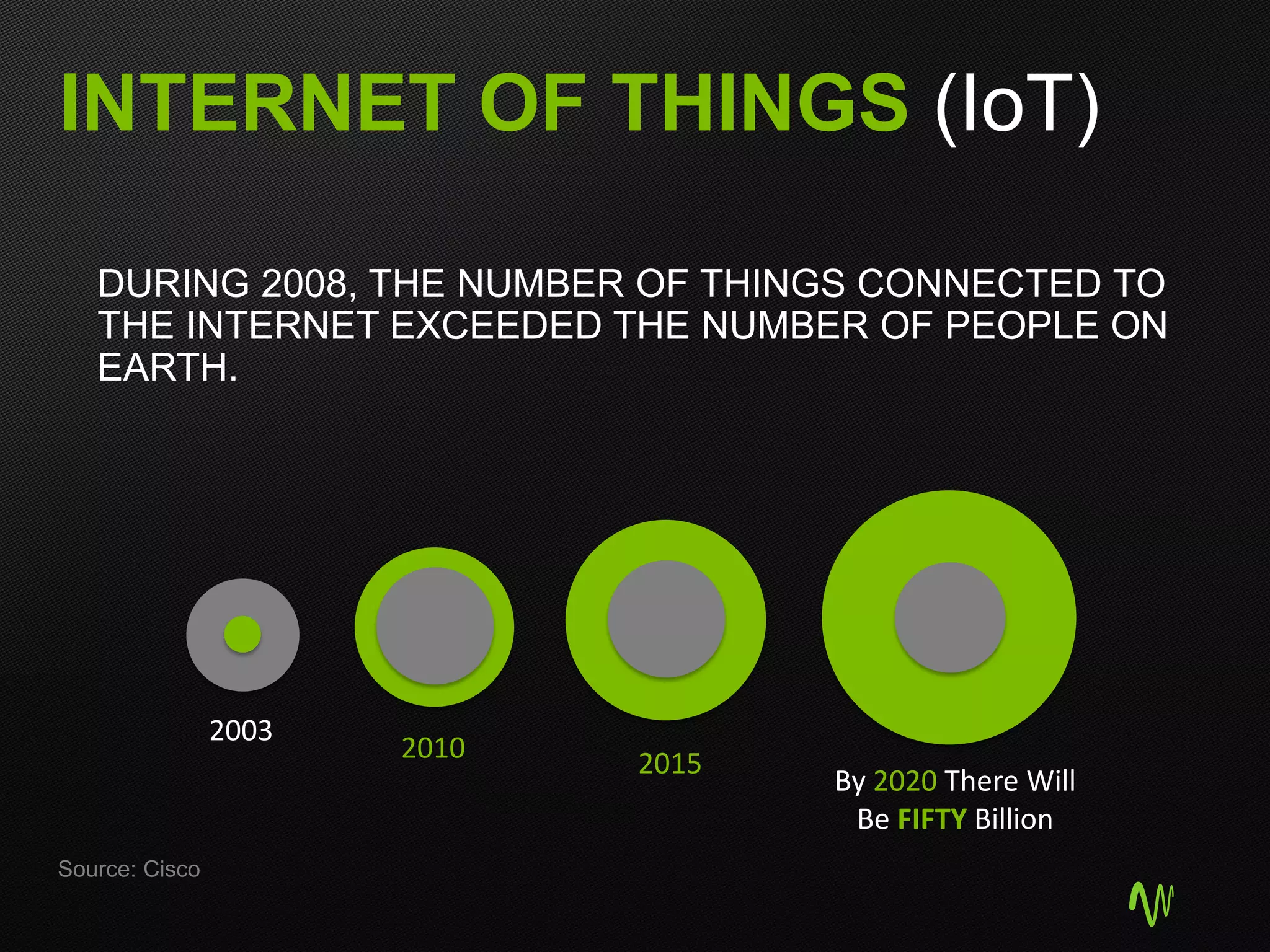
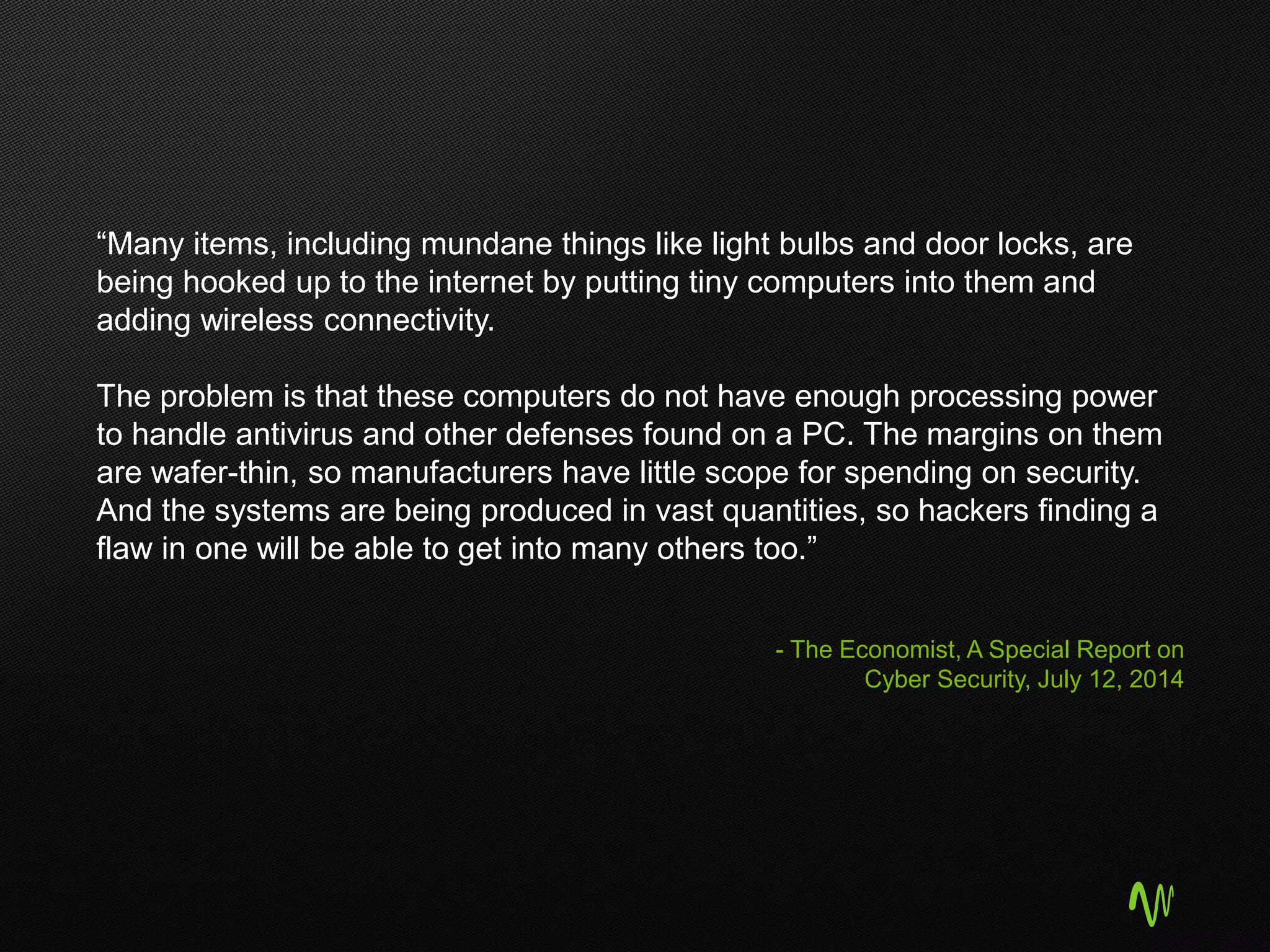
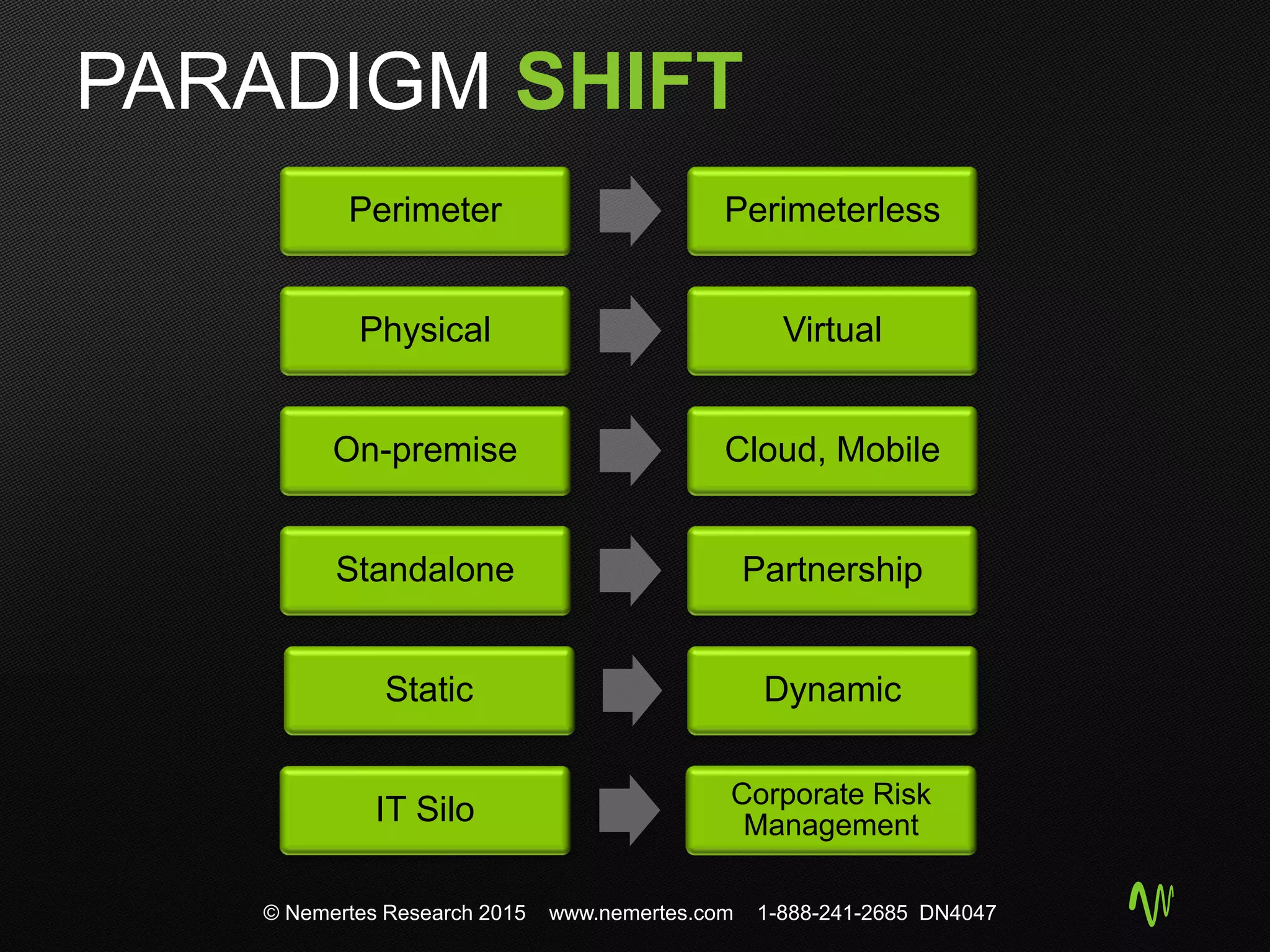
The document outlines the significance of cloud computing in business growth and highlights its associated security concerns, emphasizing the need for a robust security approach when selecting a cloud provider. It discusses various cyber threats and urges companies to involve executives in cloud security decisions as well as to adopt comprehensive IT frameworks. Key takeaways include prioritizing security, maintaining compliance, and ensuring continuous monitoring to mitigate risks.