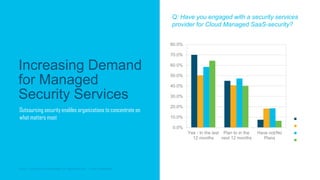
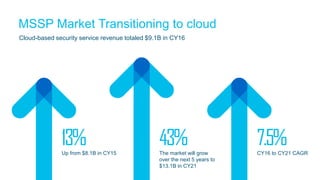
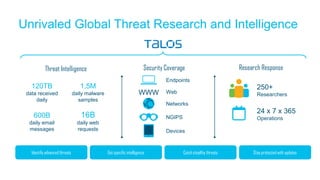
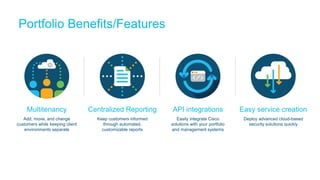
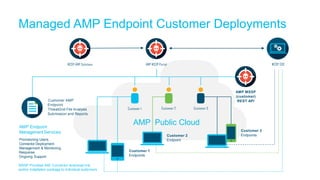
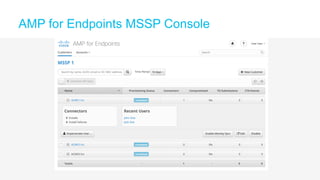
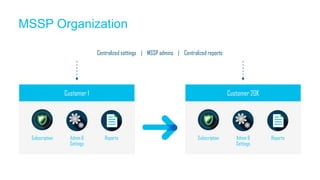
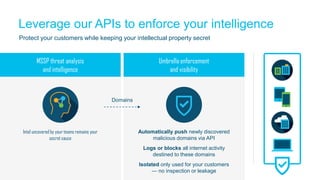
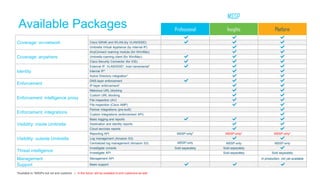
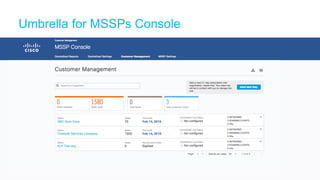
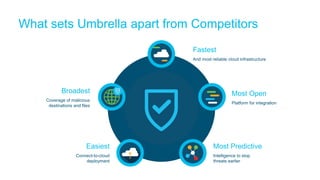
The document discusses the importance of cloud-based security solutions for Managed Security Service Providers (MSSPs), highlighting the growing demand for outsourcing endpoint security due to resource limitations and advanced threats. Cisco offers a comprehensive endpoint security portfolio that enables visibility, control, and protection against malware while simplifying service delivery through a multi-tenant cloud model. The market for cloud-managed security services is projected to grow significantly, emphasizing the need for effective cybersecurity strategies and solutions.