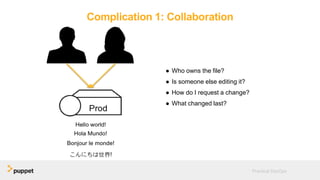
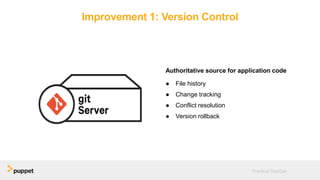
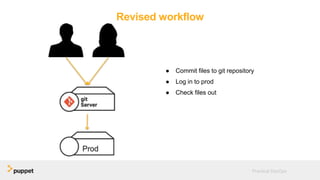
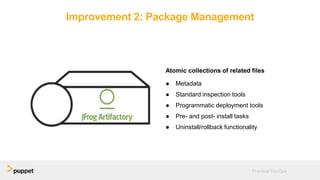
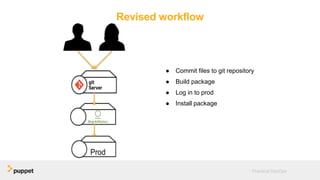
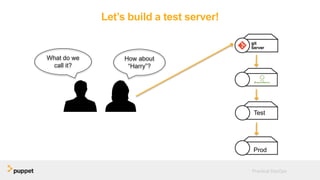
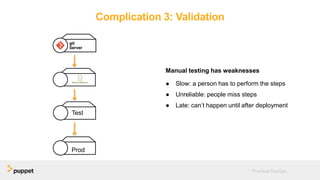
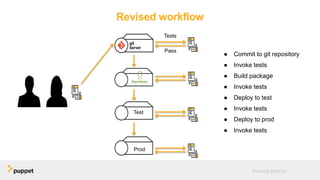
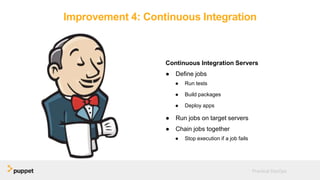
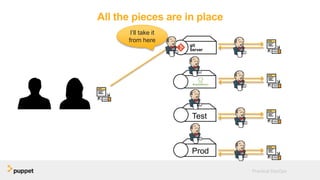
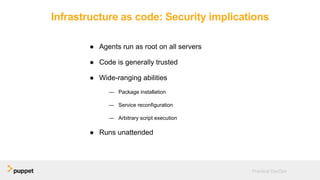
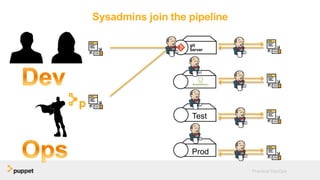
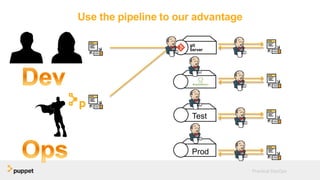
DevOps aims to break down silos between development and operations teams through collaboration, automation, and continuous delivery. While this provides benefits, it can also introduce security risks if security is not properly included. The presentation discusses five key aspects of a DevOps transformation and their security implications. It argues that DevOps and security are not mutually exclusive if security is incorporated through collaboration, automated testing of security requirements, and accelerating remediation of vulnerabilities.