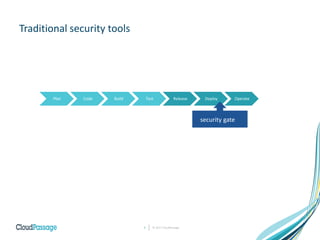
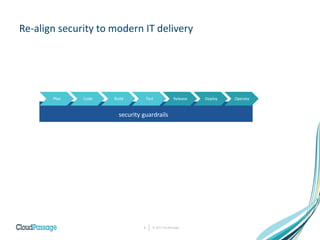
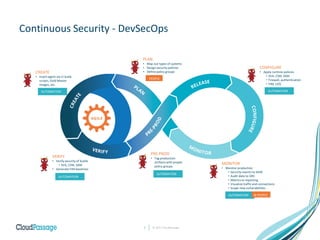
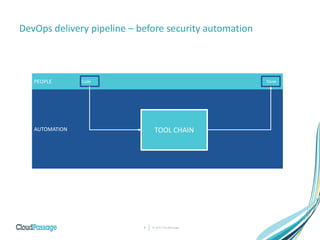
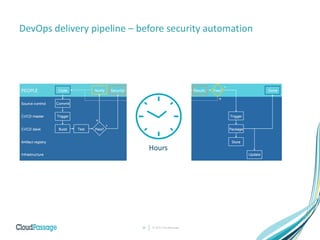
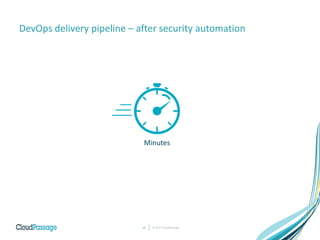
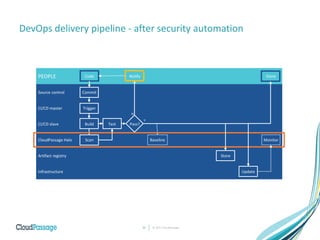
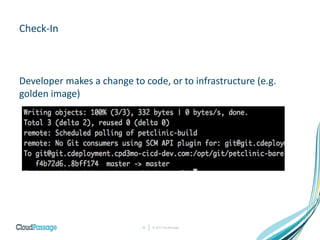
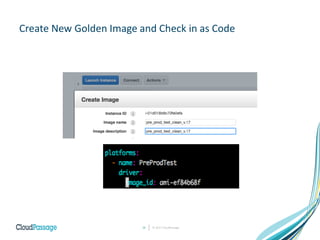
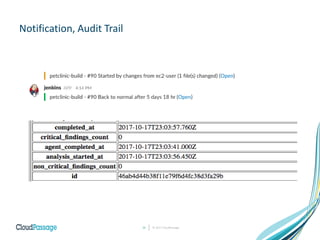
The document discusses the integration of security into DevOps practices to accelerate continuous delivery and address security challenges. It presents a case study of Acme Incorporated, detailing their transition from traditional security processes that delayed deployment to a more agile approach where security is embedded within CI/CD pipelines. Key strategies include collaboration among development, operations, and security teams, automated workload security, and the creation of 'golden' images with predefined security policies.