This document presents a comprehensive overview of fog computing, its applications, advantages, and challenges in relation to sustainability. It defines fog computing as an extension of cloud computing that enhances performance and reduces latency while addressing the increasing energy consumption and environmental impact of data centers. The survey discusses several research efforts aimed at optimizing fog computing and highlights its significance in creating sustainable computing solutions for various sectors including smart cities and healthcare.


![Introduction to Fog Computing
• In recent years fog computing has emerged as a load balancer for data centers.
• Enormous amount of internet traffic is generated every day and growing.
• Global IP traffic in 2016 was 96 exabyte per month and will nearly triple by 2021,
Consumer IP traffic will reach 232.7 exabyte per month and business IP traffic
will be 45.5 exabyte per month by 2021 [1] .
• Due to this tremendous amount of data transaction, data centers require more
powerful computing devices to perform certain tasks efficiently.](https://image.slidesharecdn.com/sustainabilityandfogcomputing-applicationsadvantagesandchallenges-190920060507/85/Sustainability-and-fog-computing-applications-advantages-and-challenges-3-320.jpg)
![Introduction to Fog Computing
Continued…
• Powerful computing devices consume electricity
and emit CO2 in the atmosphere which is very
harmful for the environment [2].
• Another term related to cloud computing has
emerged recently, called Internet of Things (IoT).
• In simple words IoT means “connect the
unconnected” [3] through the Internet.
• According to International Data Corporation (IDC)
statistics [4] by 2020:](https://image.slidesharecdn.com/sustainabilityandfogcomputing-applicationsadvantagesandchallenges-190920060507/85/Sustainability-and-fog-computing-applications-advantages-and-challenges-4-320.jpg)
![Introduction to Fog Computing
Continued…
• Data center burden has been further increasing because cloud computing is
the only cost-efficient choice left that can handle such massive amount of
data to be stored and processed.
• Such issues compelled researchers to think about an alternative of the cloud
or something which can at least extend the cloud services so that data center’s
load could be lighter.
• That’s why fog computing came into limelight in 2012 [5] and became
further prevalent in 2015 [6].](https://image.slidesharecdn.com/sustainabilityandfogcomputing-applicationsadvantagesandchallenges-190920060507/85/Sustainability-and-fog-computing-applications-advantages-and-challenges-5-320.jpg)

![Problem Statement
• In 2017, approximately 8 million data centers all over the globe were handling the
entire data load. They required 416.2 terawatt-hours of electricity [7].
• In real world such amount of energy emits as much CO2 as more than 33 million
houses emit in one year [8].
• That is 2 percent of total global use, and it’s most likely to reach a never before 5
percent of global electricity consumption by 2020 [7]
• To reduce the heavy burden of data centers fog computing emerges as an extended
solution of cloud.](https://image.slidesharecdn.com/sustainabilityandfogcomputing-applicationsadvantagesandchallenges-190920060507/85/Sustainability-and-fog-computing-applications-advantages-and-challenges-7-320.jpg)




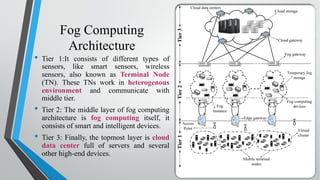
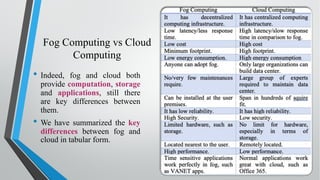

![References
[1] “Cisco Visual Networking Index: Forecast and Methodology, 2016–2021,” p. 17, 2017.
[2] A. Jain, M. Mishra, S. K. Peddoju, and N. Jain, “Energy efficient computing- Green cloud computing,” 2013 International
Conference on Energy Efficient Technologies for Sustainability, ICEETS 2013, pp. 978–982, 2013.
[3] D. Hanes, IoT fundamentals : networking technologies, protocols, and use cases for the Internet of Things, 1st ed. Cisco
Press, 2017.
[4] M. Mukherjee, L. Shu, and D. Wang, “Survey of Fog Computing: Fundamental, Network Applications, and Research
Challenges,” IEEE Communications Surveys & Tutorials, no. c, p. 30, 2018.
[5] F. Bonomi, R. Milito, J. Zhu, and S. Addepalli, “Fog Computing and Its Role in the Internet of Things,” Proceedings of the
first edition of the MCC workshop on Mobile cloud computing, pp. 13–16, 2012.
[6] M. Janakiram, “Is Fog Computing The Next Big Thing In Internet of Things?,” Forbes Magazine, 2016. [Online]. Available:
https://www.forbes.com/sites/janakirammsv/2016/04/18/is-fog-computing-the-next-big-thing-in-internet-of-
things/#563dd9b5608d. [Accessed: 08-Oct-2018].
[7] Jim Witham, “Achieving Data Center Energy Efficiency,” 2018. [Online]. Available:
https://www.datacenterknowledge.com/industry-perspectives/achieving-data-center-energy-efficiency. [Accessed: 15-Oct-2018].
[8] C. US EPA, OAR,OAP, “Greenhouse Gas Equivalencies Calculator,” United States Environmental Protection Agency, 2018.
[Online]. Available: https://www.epa.gov/energy/greenhouse-gas-equivalencies-calculator. [Accessed: 16-Oct-2018].](https://image.slidesharecdn.com/sustainabilityandfogcomputing-applicationsadvantagesandchallenges-190920060507/85/Sustainability-and-fog-computing-applications-advantages-and-challenges-15-320.jpg)
