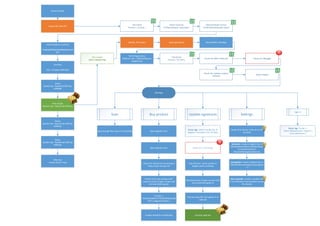
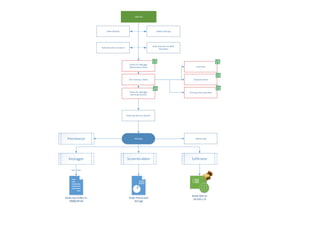
The document describes the behavior of a ransomware sample. It unpacks files, checks system requirements like CPU cores and Windows version, decrypts decoy files using XOR, identifies a .NET binary, writes registry keys for persistence, checks for security software and debuggers, downloads and executes updates, and includes keylogging and screenshot capturing functionality before deleting logs and persisting on the system.