State of the Network Infographic 2018
The document discusses the evolving role of network professionals and key trends in networking. It finds that most network professionals feel their role is becoming more strategic and business oriented, and that collaboration between network teams and other IT teams is successful. Emerging technologies that are transforming networking include edge computing, hyperconverged infrastructure, converged infrastructure, software-defined networking, and SD-WAN. Security is also a major focus and challenge for network teams. The top security concerns are maintaining network security while ensuring connectivity, protecting against data breaches, and ensuring availability. Over half of network professionals have plans to implement various emerging technologies in the next year.
Recommended
Recommended
More Related Content
What's hot
What's hot (20)
Similar to State of the Network Infographic 2018
Similar to State of the Network Infographic 2018 (20)
More from IDG
More from IDG (20)
Recently uploaded
Recently uploaded (17)
State of the Network Infographic 2018
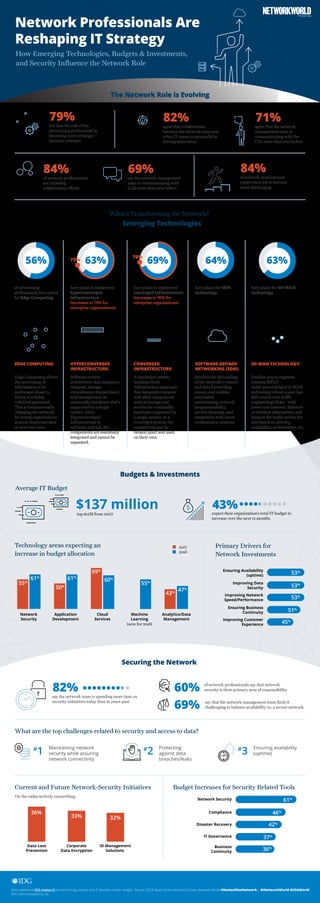
- 1. 10% The Network Role is Evolving feel that the role of the networking professional is becoming more strategic/ business oriented 79% agree that collaboration between the network team and other IT teams is successful in driving innovation 82% agree that the network management team is communicating with the CIO more than ever before 71% of network professionals are initiating collaboration efforts 84% say the network management team is communicating with LOB more than ever before 69% of network professionals expect their job to become more challenging 84% Emerging Technologies What’s Transforming the Network? EDGE COMPUTING: Edge Computing allows the processing of information to be performed closer to where it is being collected/generated. This is fundamentally changing the network by letting organizations analyze important data in near real-time. HYPERCONVERGED INFRASTRUCTURE: Software-centric architecture that integrates compute, storage, virtualization (hypervisor), and management on commodity hardware that’s supported by a single vendor. Since Hyperconverged Infrastructure is software-defined, the components are essentially integrated and cannot be separated. CONVERGED INFRASTRUCTURE: A hardware-centric, building block infrastructure approach that integrates compute and other components such as storage and servers on commodity hardware supported by a single vendor. In a converged system, the components can be broken apart and used on their own. SOFTWARE-DEFINED NETWORKING (SDN): Involves the decoupling of the network's control and data forwarding planes, and enables automated provisioning, network programmability, service chaining, and integration with cloud orchestration systems. SD-WAN TECHNOLOGY: Enables you to augment existing MPLS— multi-protocol label (a WAN technology where a user has full control over traffic engineering) links—with lower cost Internet, Ethernet or wireless alternatives, and balance the traffic across the mix based on priority, availability, performance, etc. Budgets & Investments Average IT Budget $137 million(up $12M from 2017) expect their organization’s total IT budget to increase over the next 12 months 43% View additional IDG research on technology trends and IT decision-maker insight. Source: 2018 State of the Network Survey, Network World #StateoftheNetwork | @NetworkWorld @IDGWorld IDG Communications, Inc. Technology areas expecting an increase in budget allocation Ensuring Availability (uptime) Improving Data Security Improving Network Speed/Performance 53% 53% 53% Network Security Application Development Cloud Services Machine Learning (new for 2018) Analytics/Data Management 2017 2018 55% 61% 50% 61% 69% 60% 55% 43% 47% Primary Drivers for Network Investments Ensuring Business Continuity Improving Customer Experience 51% 45% Securing the Network say the network team is spending more time on security initiatives today than in years past 82% of network professionals say that network security is their primary area of responsibility60% say that the network management team finds it challenging to balance availability vs. a secure network69% What are the top challenges related to security and access to data? Maintaining network security while assuring network connectivity # 1 Protecting against data breaches/leaks # 2 Ensuring availability (uptime) # 3 Current and Future Network-Security Initiatives On the radar/actively researching Data Loss Prevention Corporate Data Encryption ID Management Solutions 36% 33% 32% Budget Increases for Security Related Tools Network Security Compliance Disaster Recovery 61% 46% 42% IT Governance Business Continuity 37% 36% Network Professionals Are Reshaping IT Strategy How Emerging Technologies, Budgets & Investments, and Security Influence the Network Role of networking professionals have plans for Edge Computing 56% have plans to implement hyperconverged infrastructure (increases to 73% for enterprise organizations) 63% have plans to implement converged infrastructure (increases to 76% for enterprise organizations) have plans for SD-WAN technology 63% have plans for SDN technology 64%69% 76% 73%