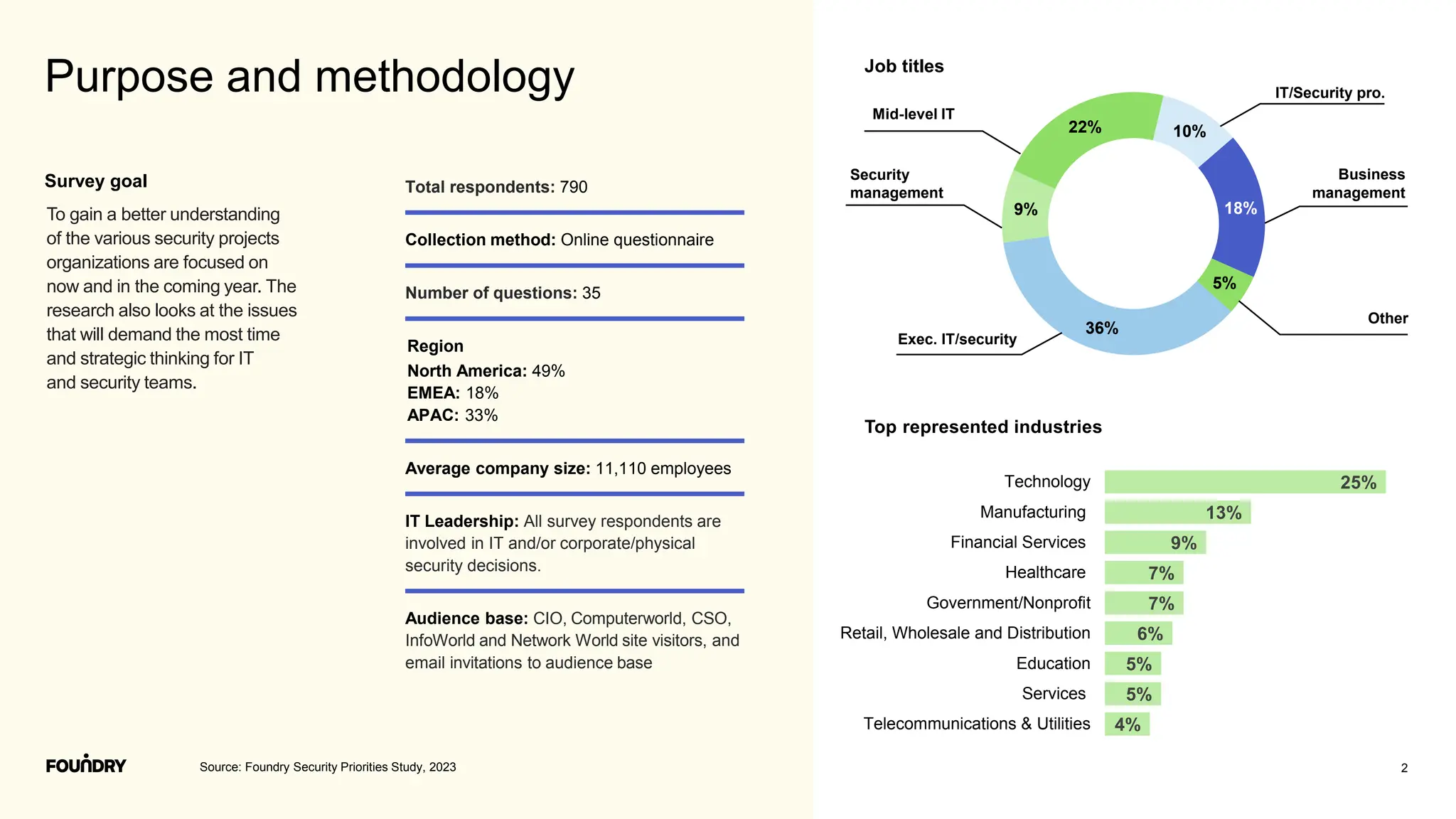
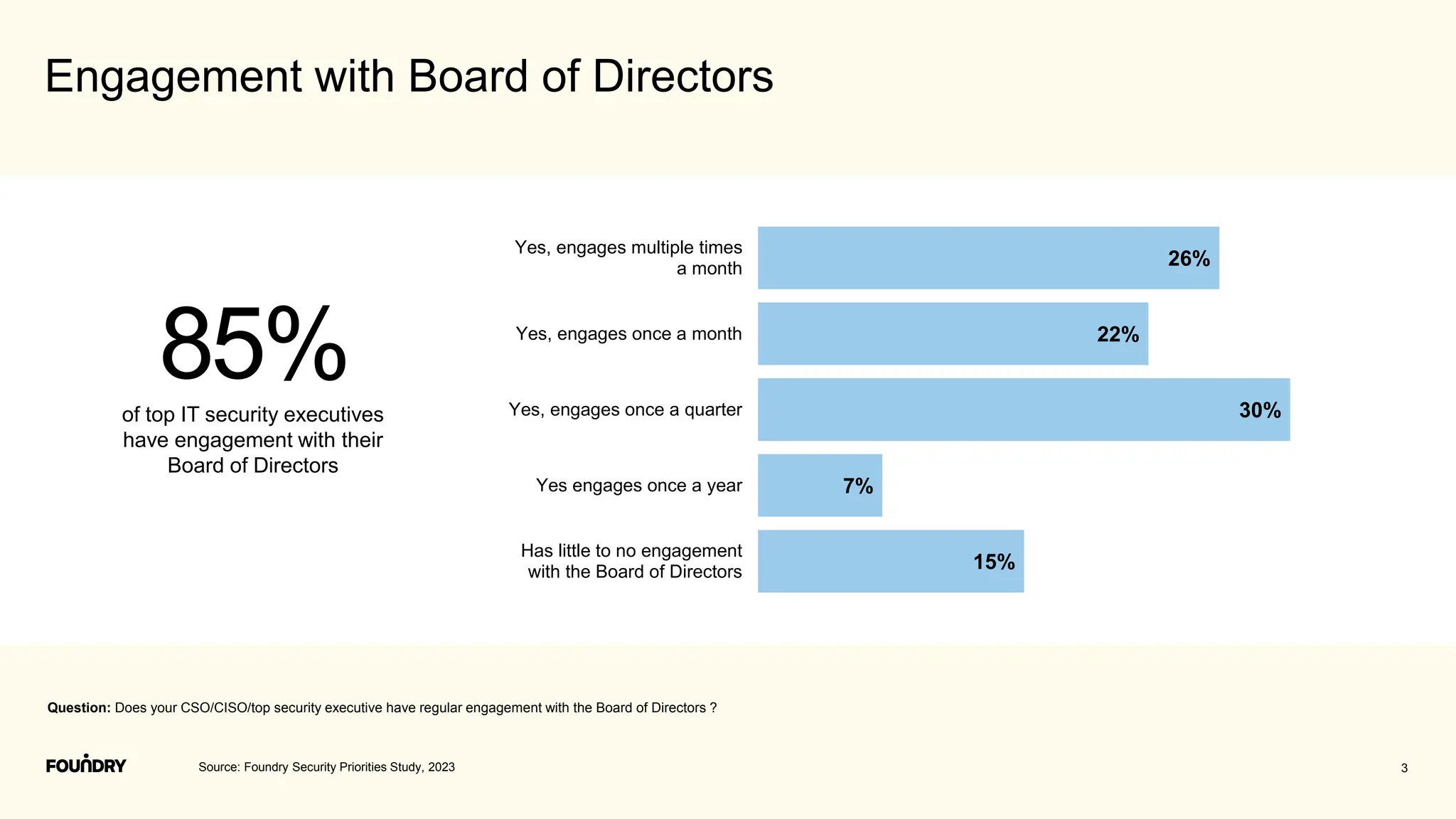
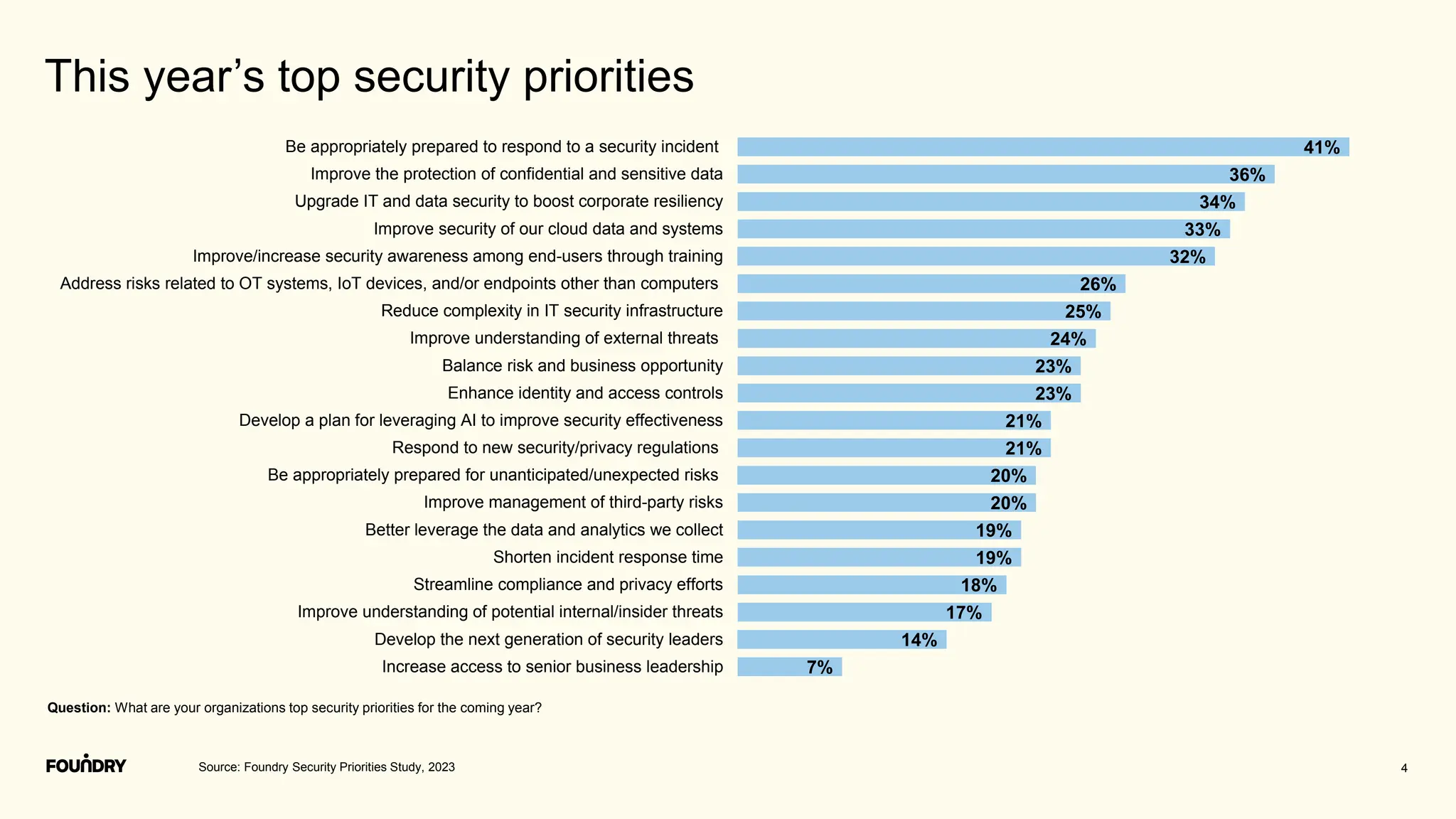
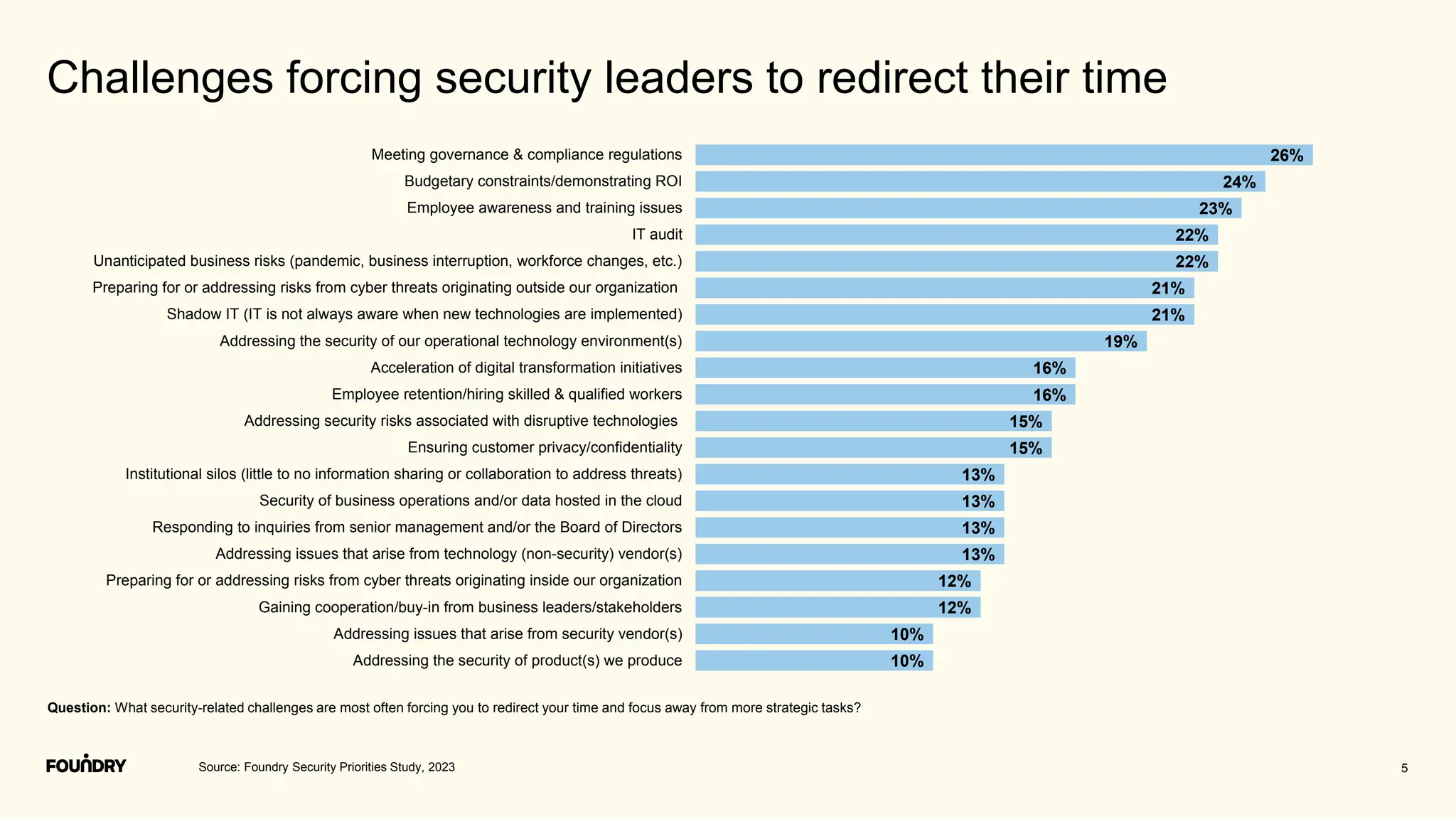
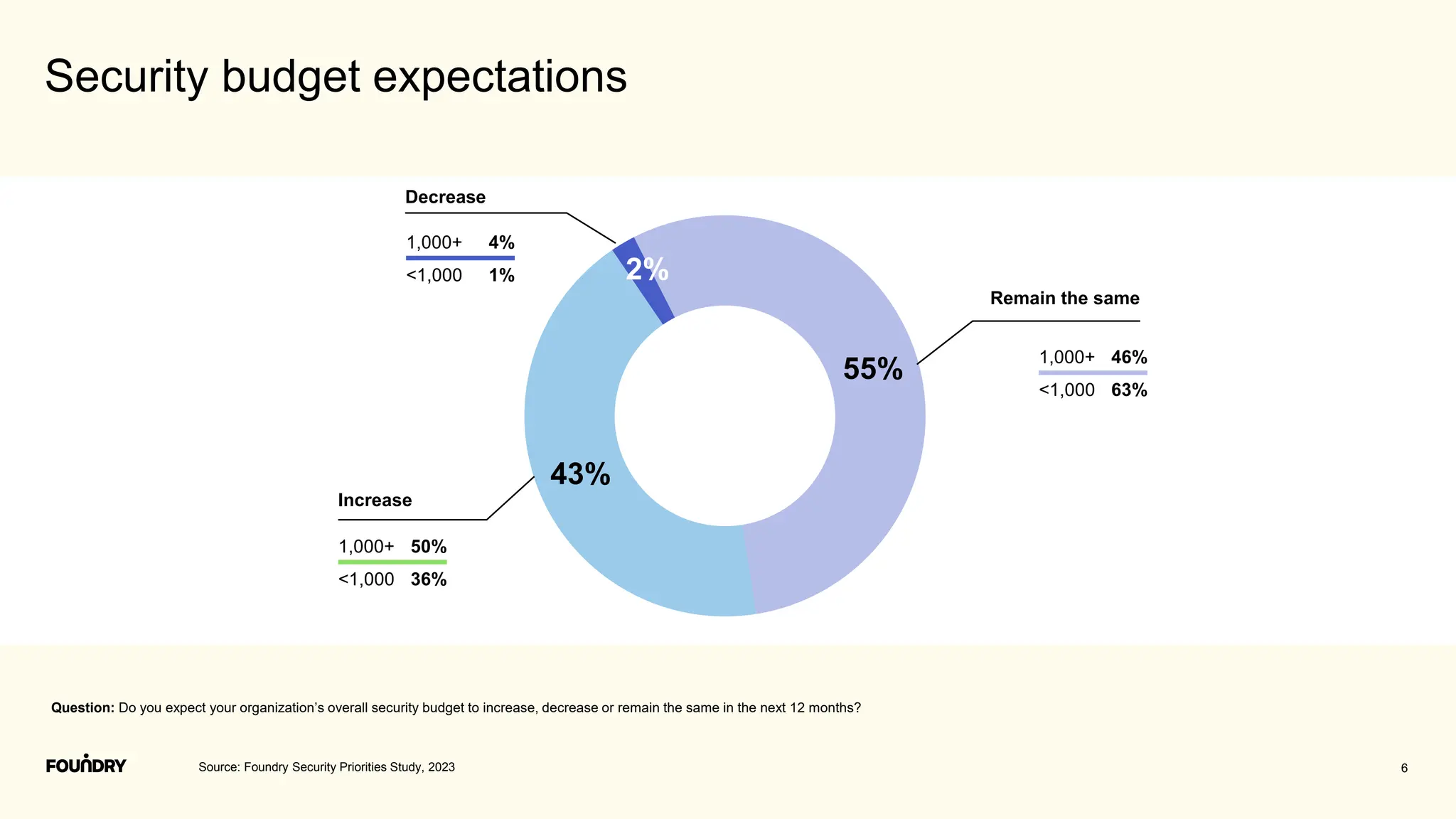
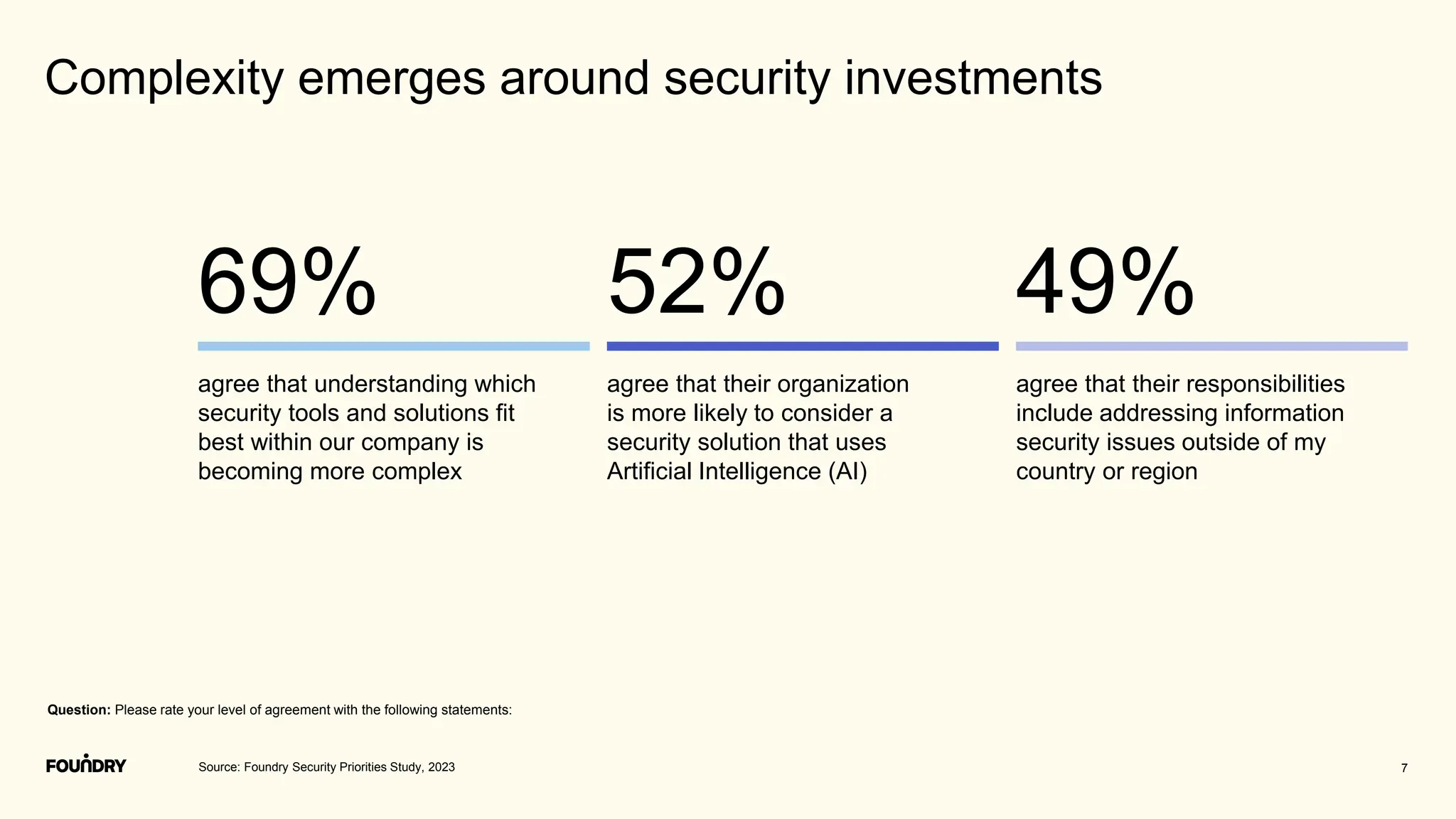
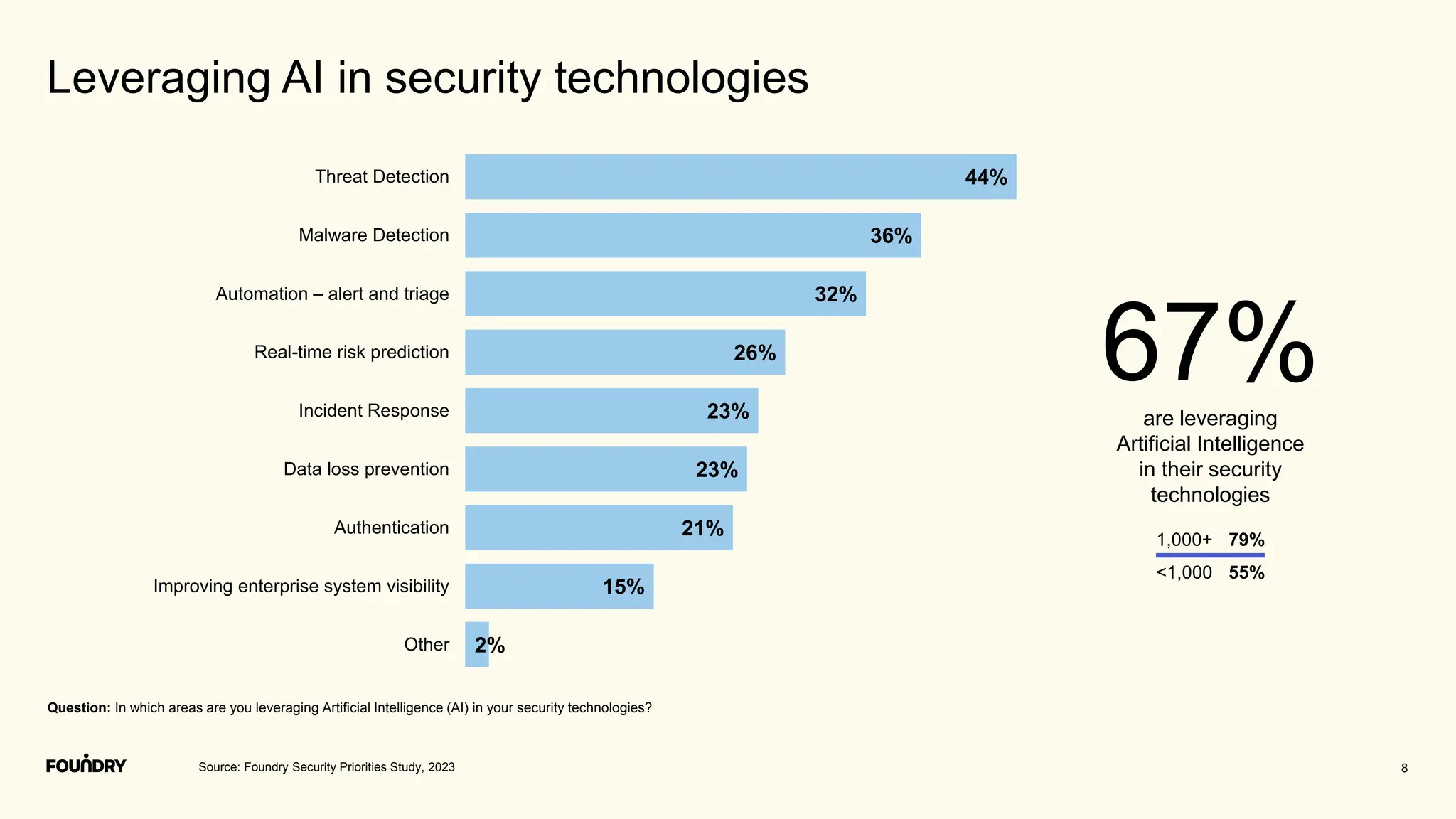
This document summarizes the results of a security priorities study conducted in 2023. It provides details on the methodology, including that 790 respondents from a variety of industries and company sizes completed an online questionnaire with 35 questions. It then outlines the top security priorities for organizations in the coming year, including improving protection of confidential data and preparing for security incidents. Challenges distracting security time are also examined, with budget expectations and compliance cited as areas pulling focus.