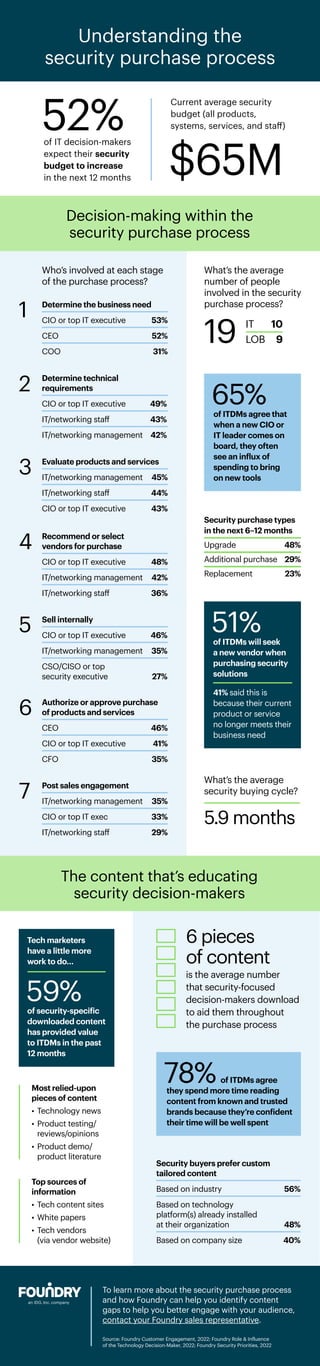
This document discusses how Foundry can help identify content gaps to better engage audiences on the security purchase process. It notes that 59% of downloaded security-specific content has provided value to IT decision-makers, and 52% expect their security budgets to increase in the next year. The document outlines the typical stages in the security purchase process and who is involved at each stage.