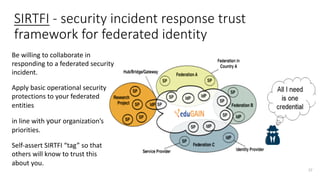
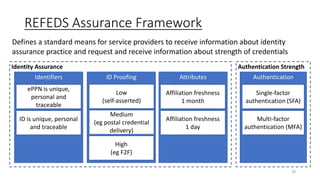
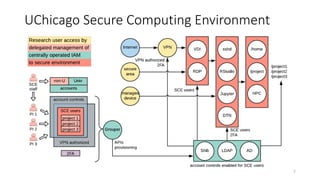
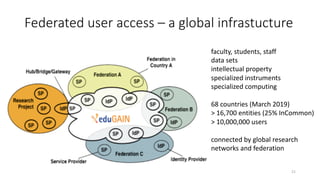
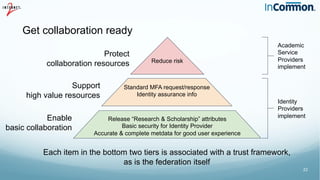
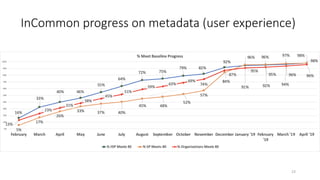
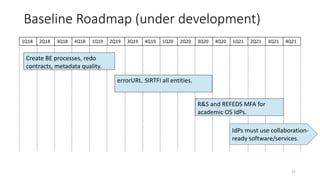
The document discusses the importance of trust frameworks and security programs in reducing risk to scientific cyberinfrastructure, enabling research while addressing security obligations, especially for sensitive data. It highlights collaboration between research computing, IT, and legal partners to implement effective security measures, as well as the complexity of managing federated user access across multiple organizations. Additionally, it emphasizes the necessity of aligning cybersecurity practices with federal standards to support secure research environments.
















![Research & Scholarship attribute release
• Name, email, affiliation, persistent identifier
• Common need for “research and scholarship” services
• Those service providers are “tagged” by their national federation
operators as “R&S”
• Identity Providers automatically release the R&S attributes to R&S tagged
services
• Such Identity Providers are also tagged as “R&S” so that services can elect
to require R&S attributes in order to provide service
• The R&S program contributes to good privacy practice under the
European General Data Protection Regulation (GDPR)
[ 26 ]](https://image.slidesharecdn.com/06bartonenablingsciencetrustsecurity-190515220136/85/Enabling-Science-with-Trust-and-Security-Guest-Keynote-26-320.jpg)