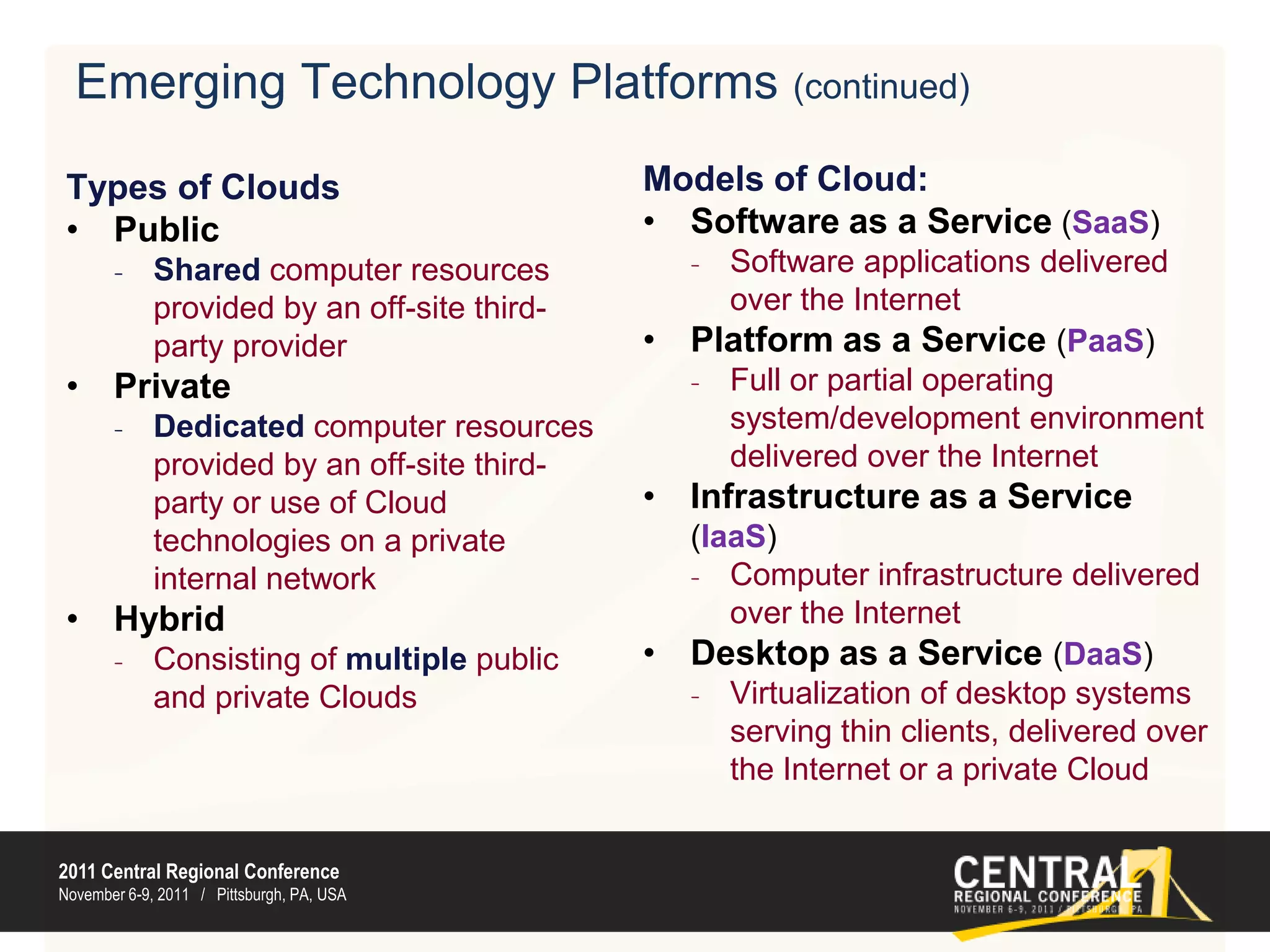
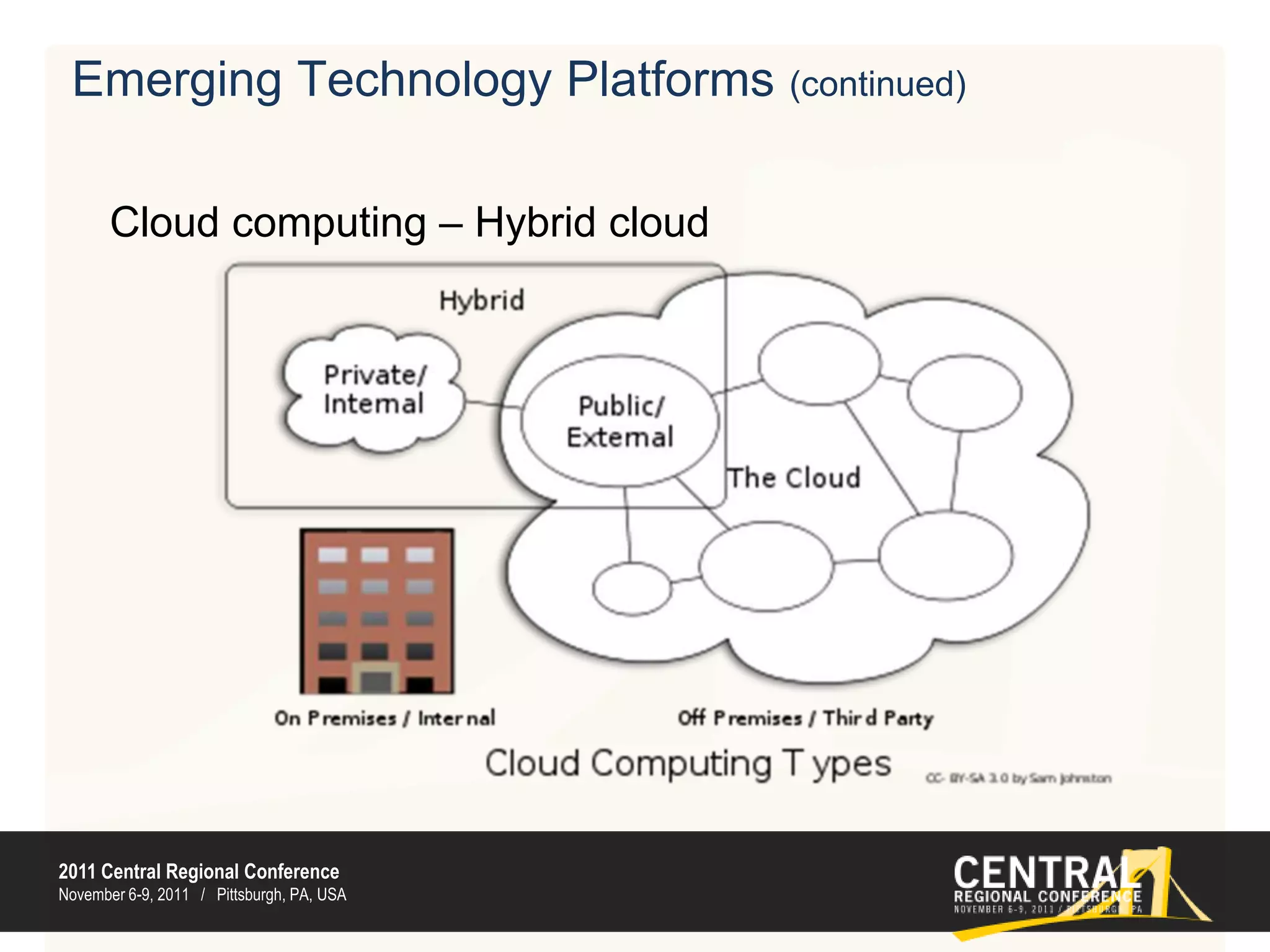
This document discusses emerging technology challenges and solutions for internal audit and compliance. It covers the current technology landscape of on-premise hardware and software and contrasts it with emerging technologies like cloud computing, mobile computing, and data analytics. These emerging technologies can potentially increase complexity for internal audit through issues around availability, security, privacy, and auditability. However, the document provides solutions for addressing these challenges such as encrypting data, implementing security architectures, and conducting security audits. It concludes by discussing future trends around distributed computing, cybersecurity, analytics tools, and new data standards.