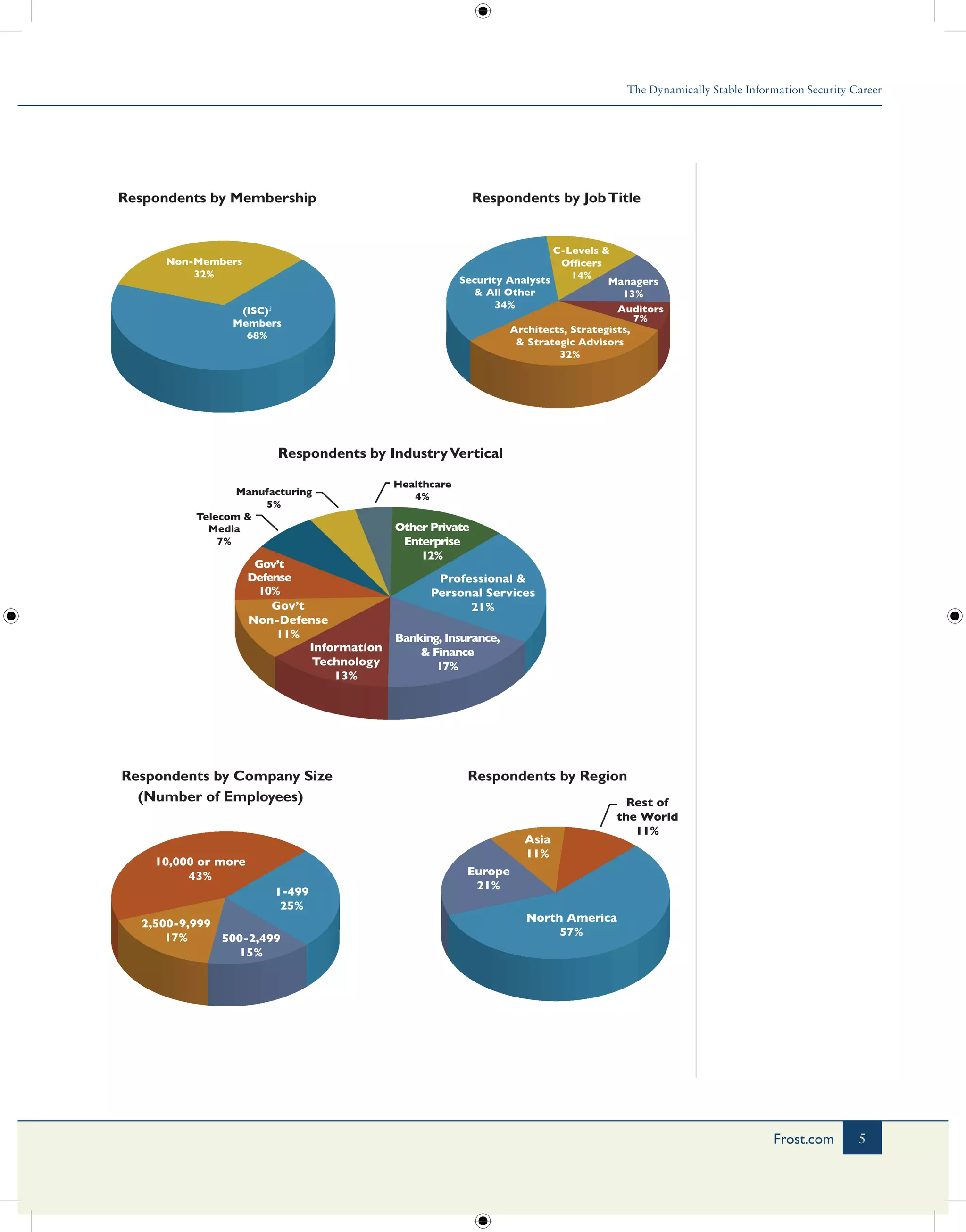
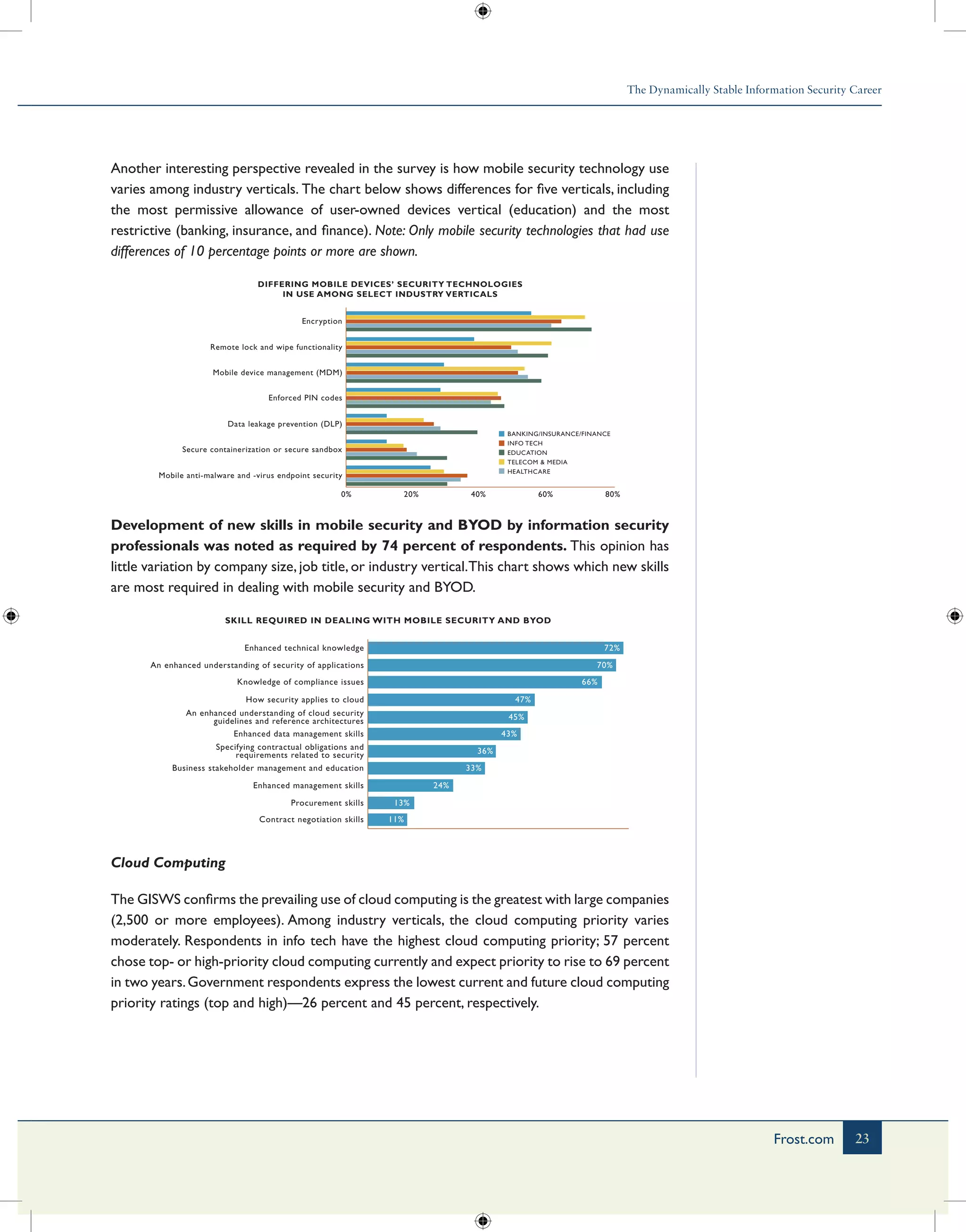
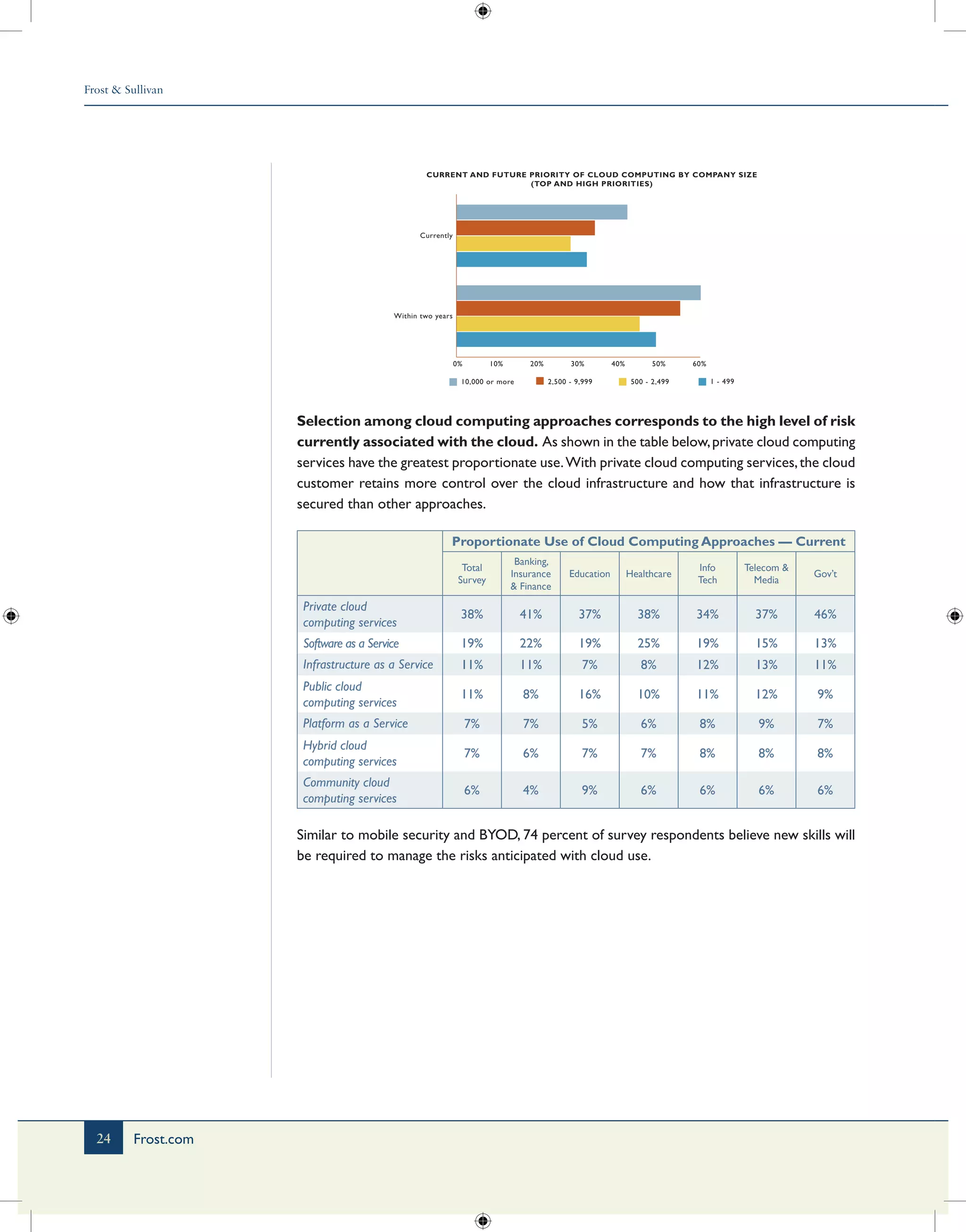
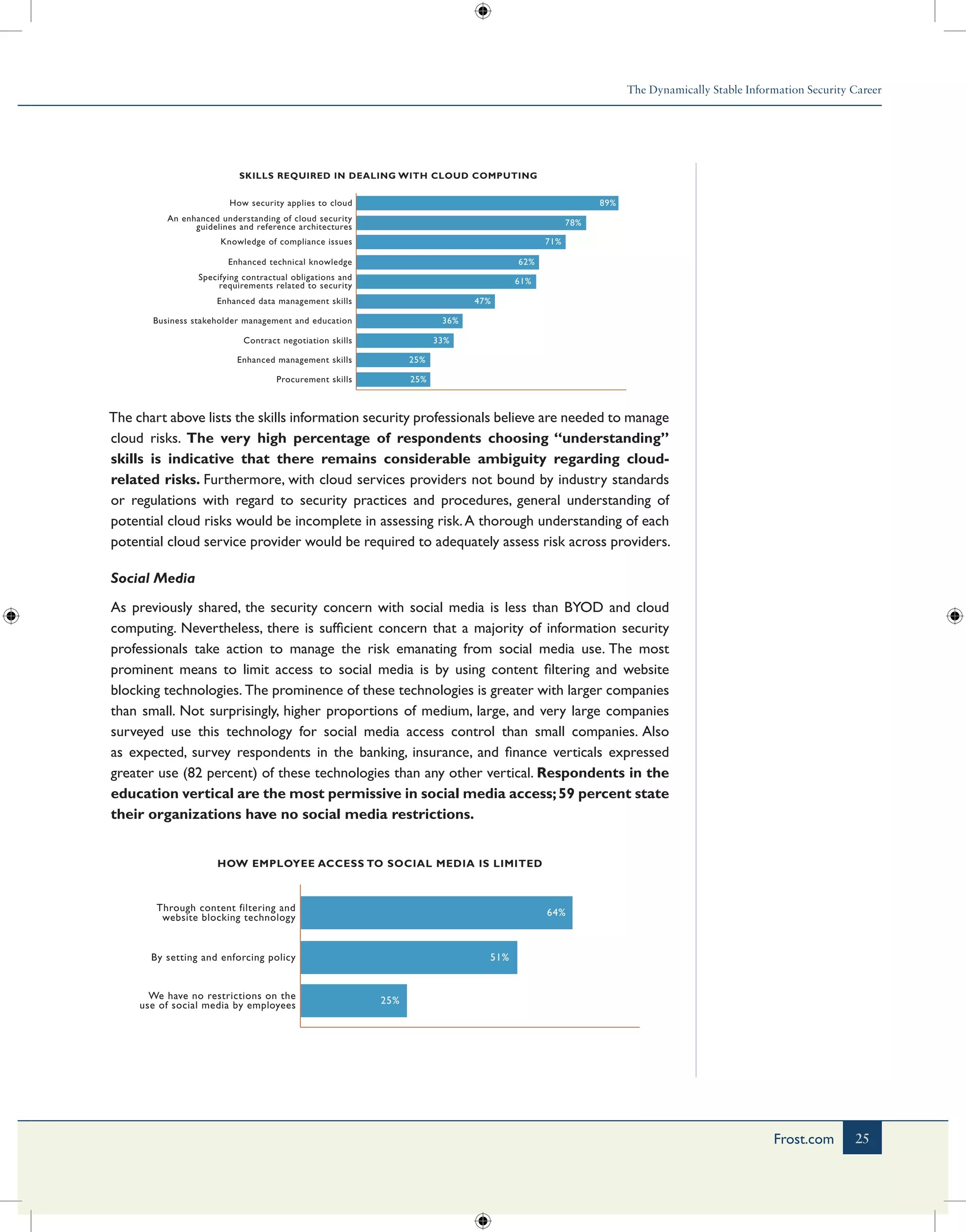
The document summarizes key findings from a survey of over 12,000 information security professionals conducted in 2012. Some of the main findings include:
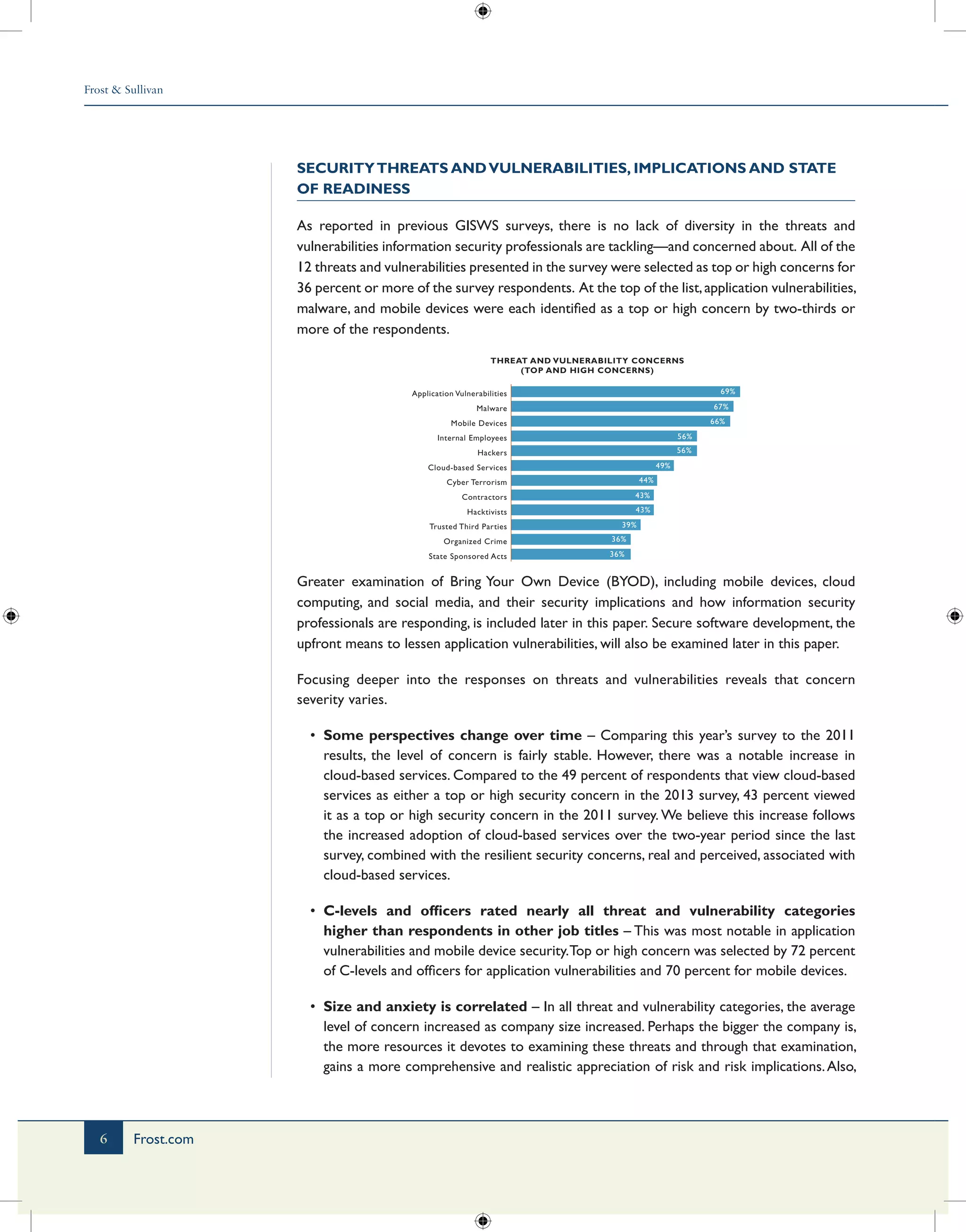
1) Application vulnerabilities, malware, and mobile devices were the top security concerns. Concern over cloud-based services also increased significantly since the previous survey in 2011.
2) Information security is seen as a stable career path, but workforce shortages persist. Knowledge and certification are important for career success and advancement.
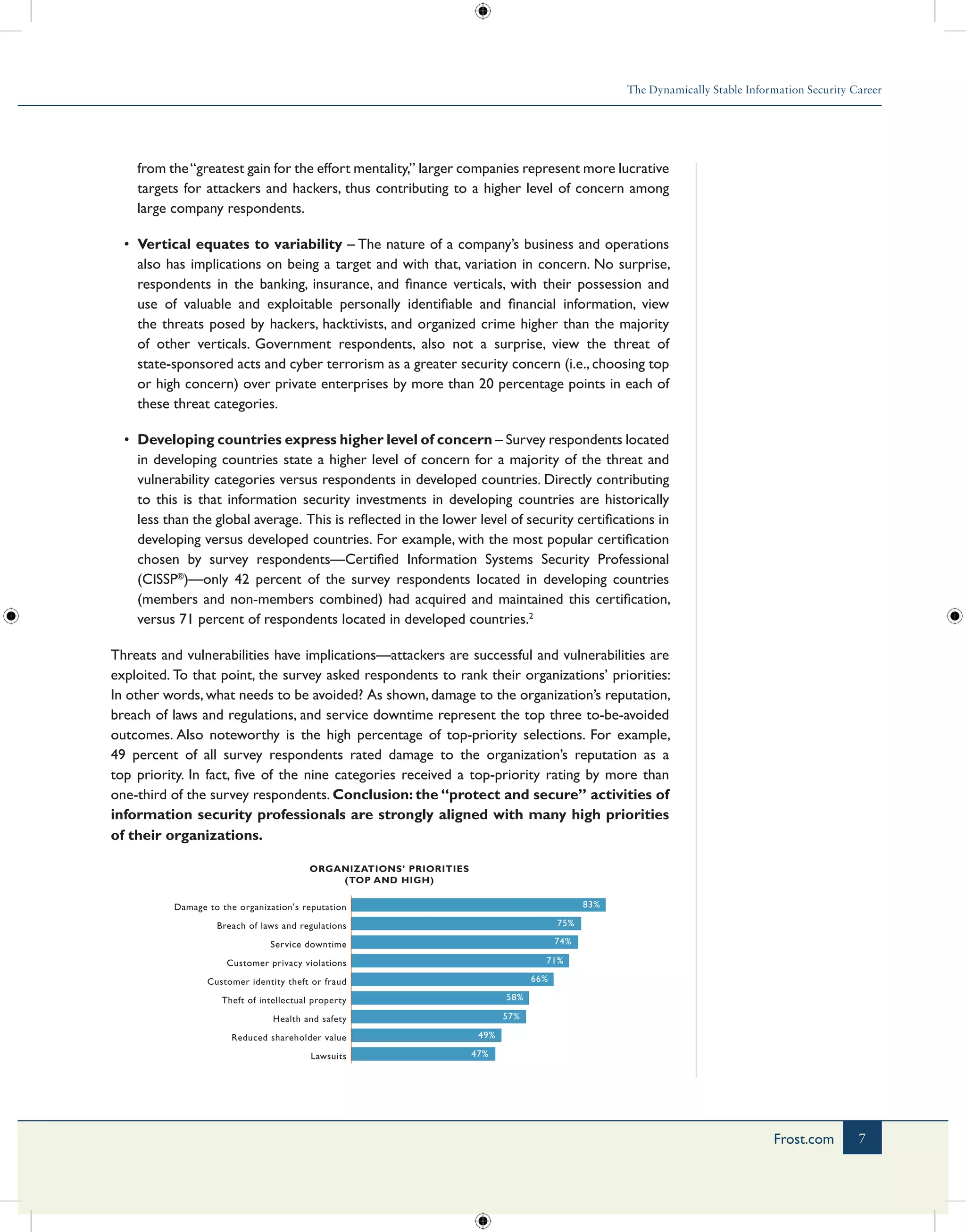
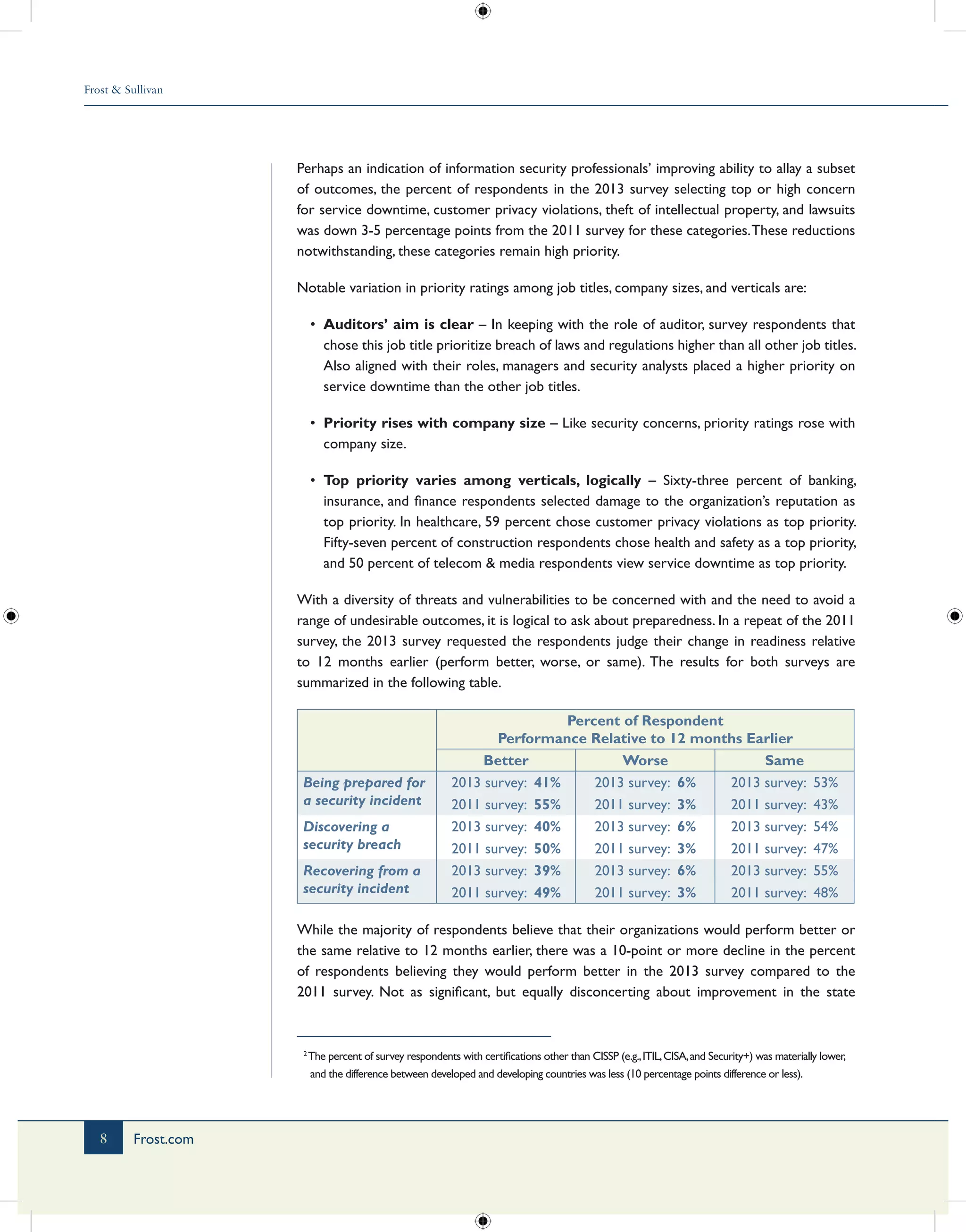
3) While attack remediation is believed to be rapid, preparedness for security incidents showed signs of strain, with twice as many respondents saying preparedness had worsened compared to 2011.