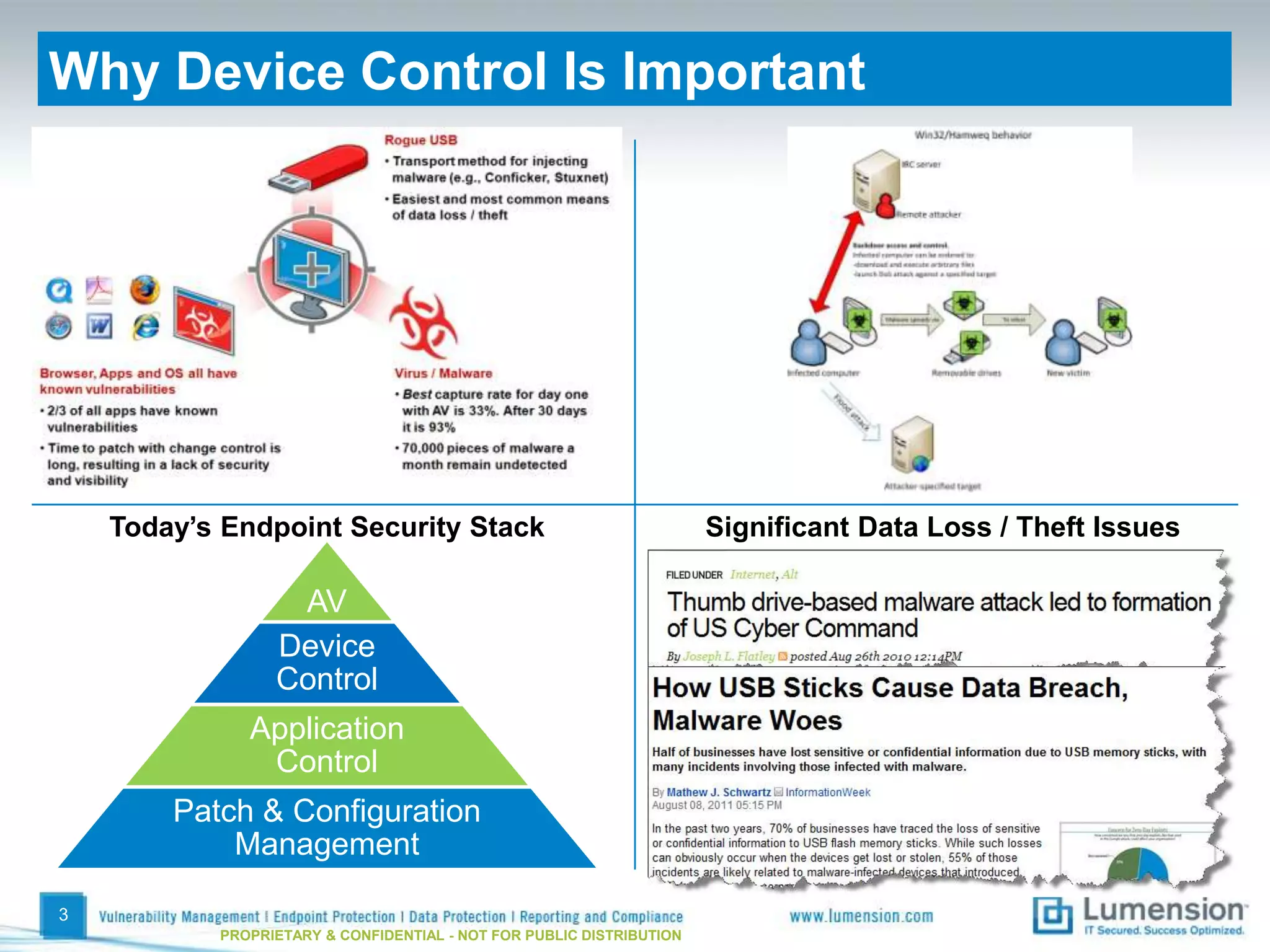
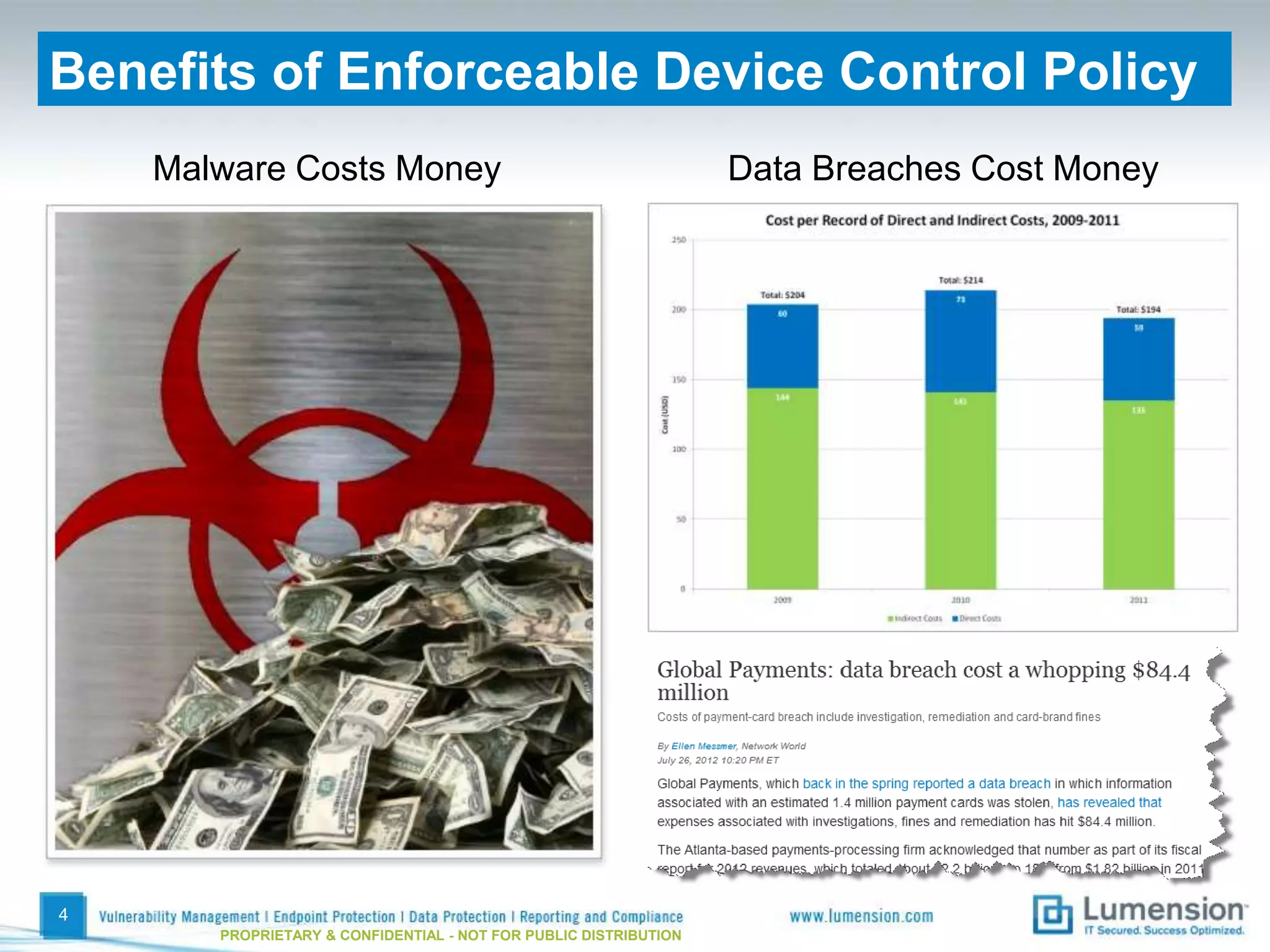
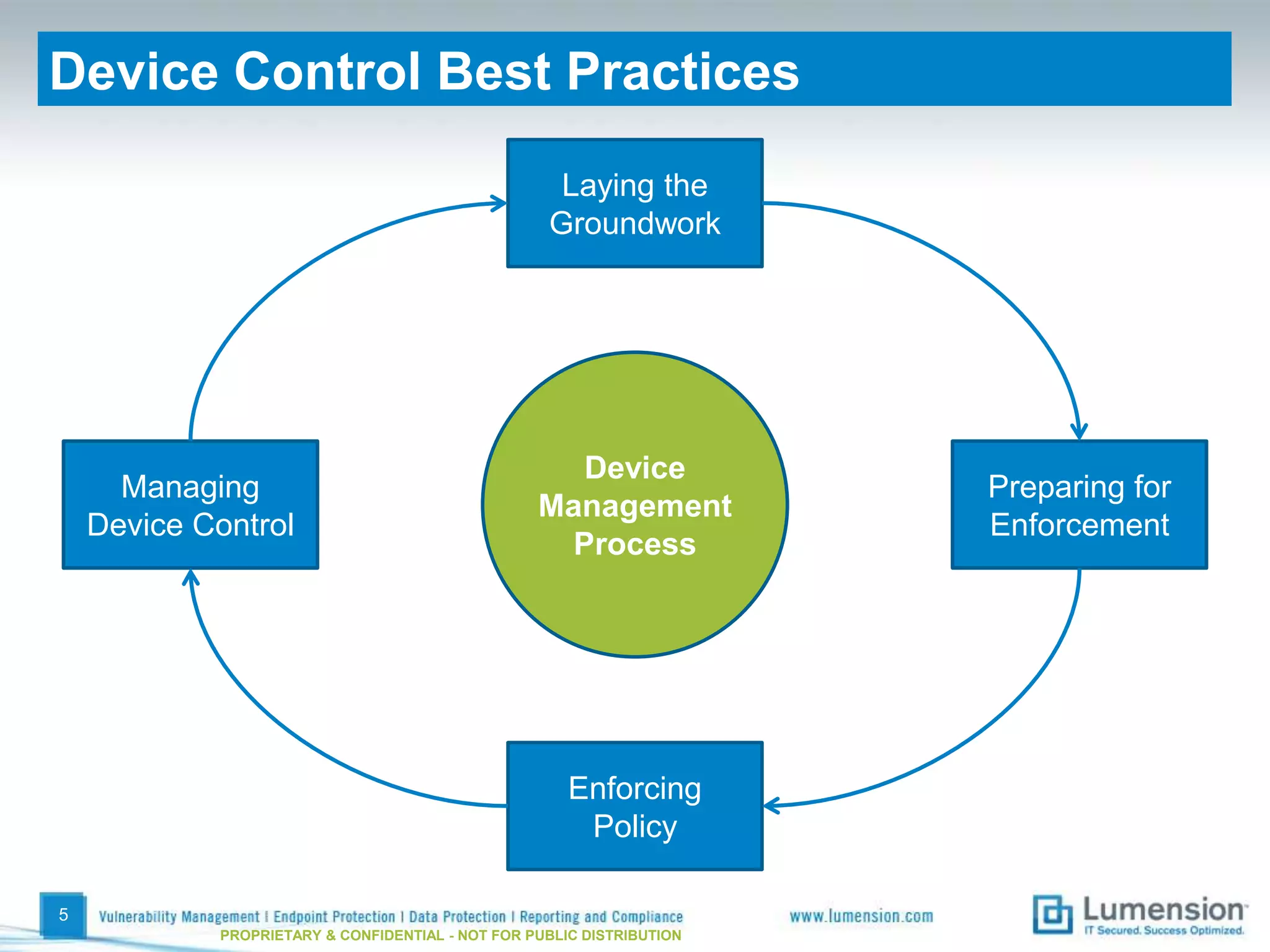
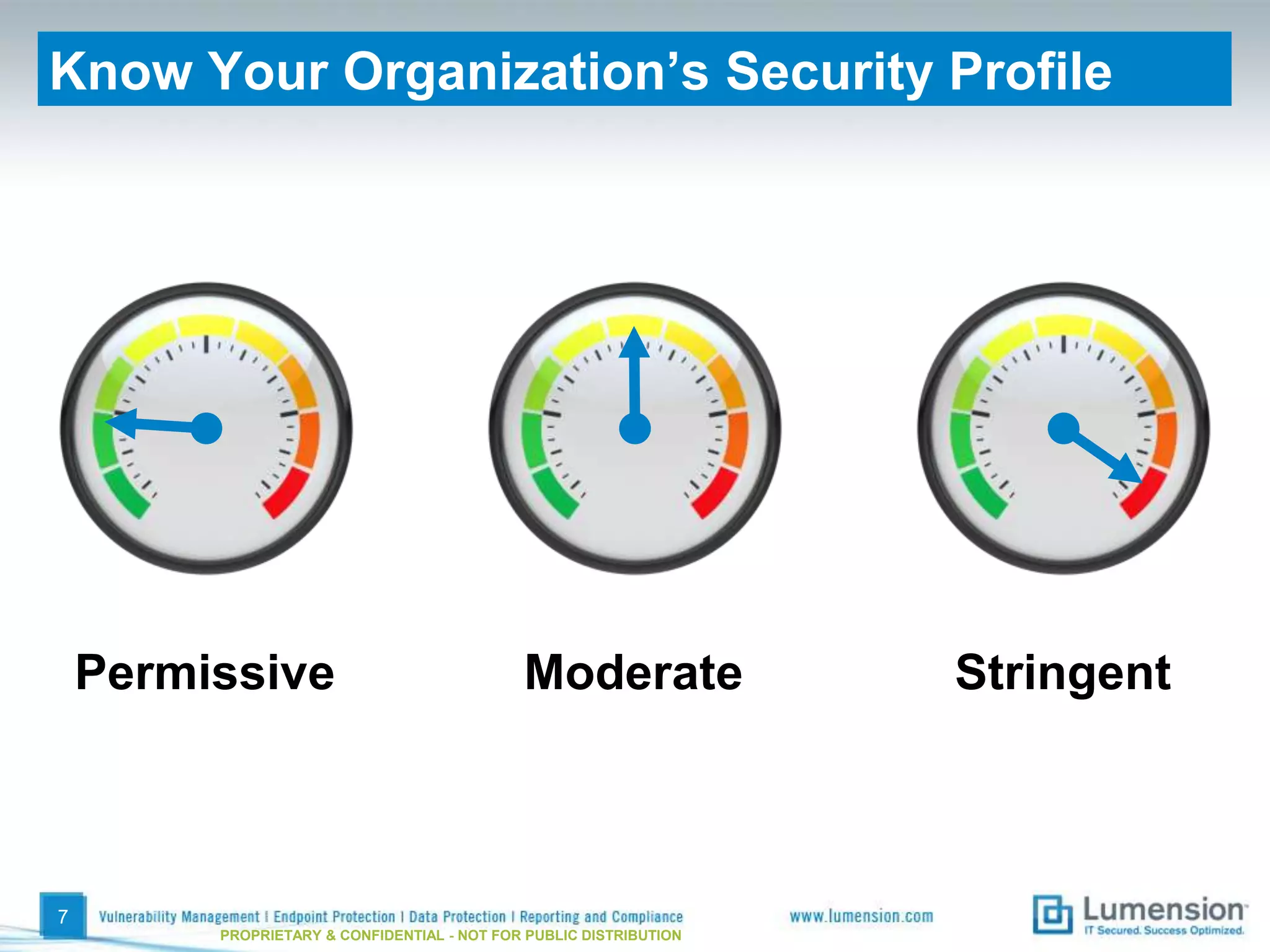
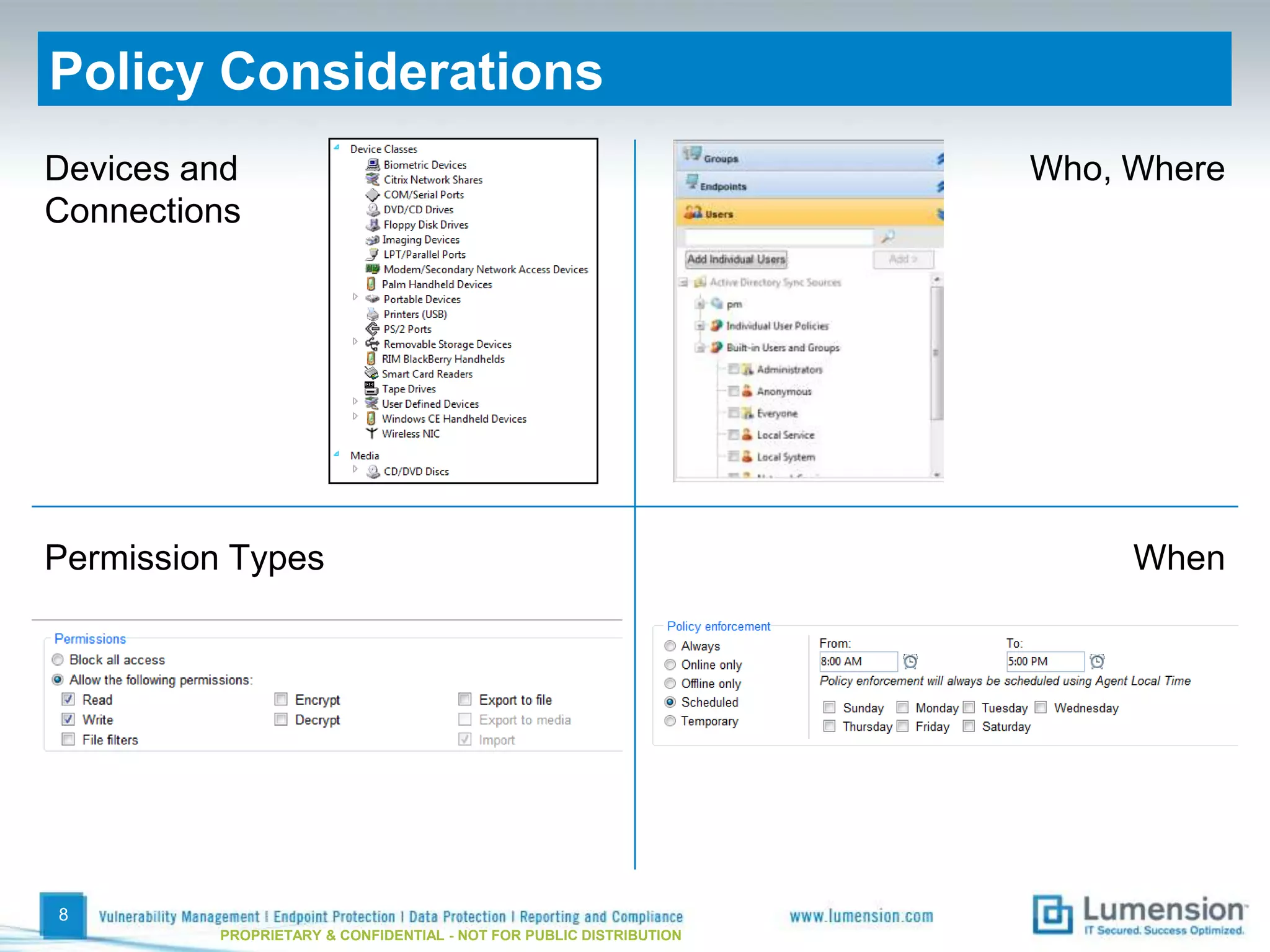
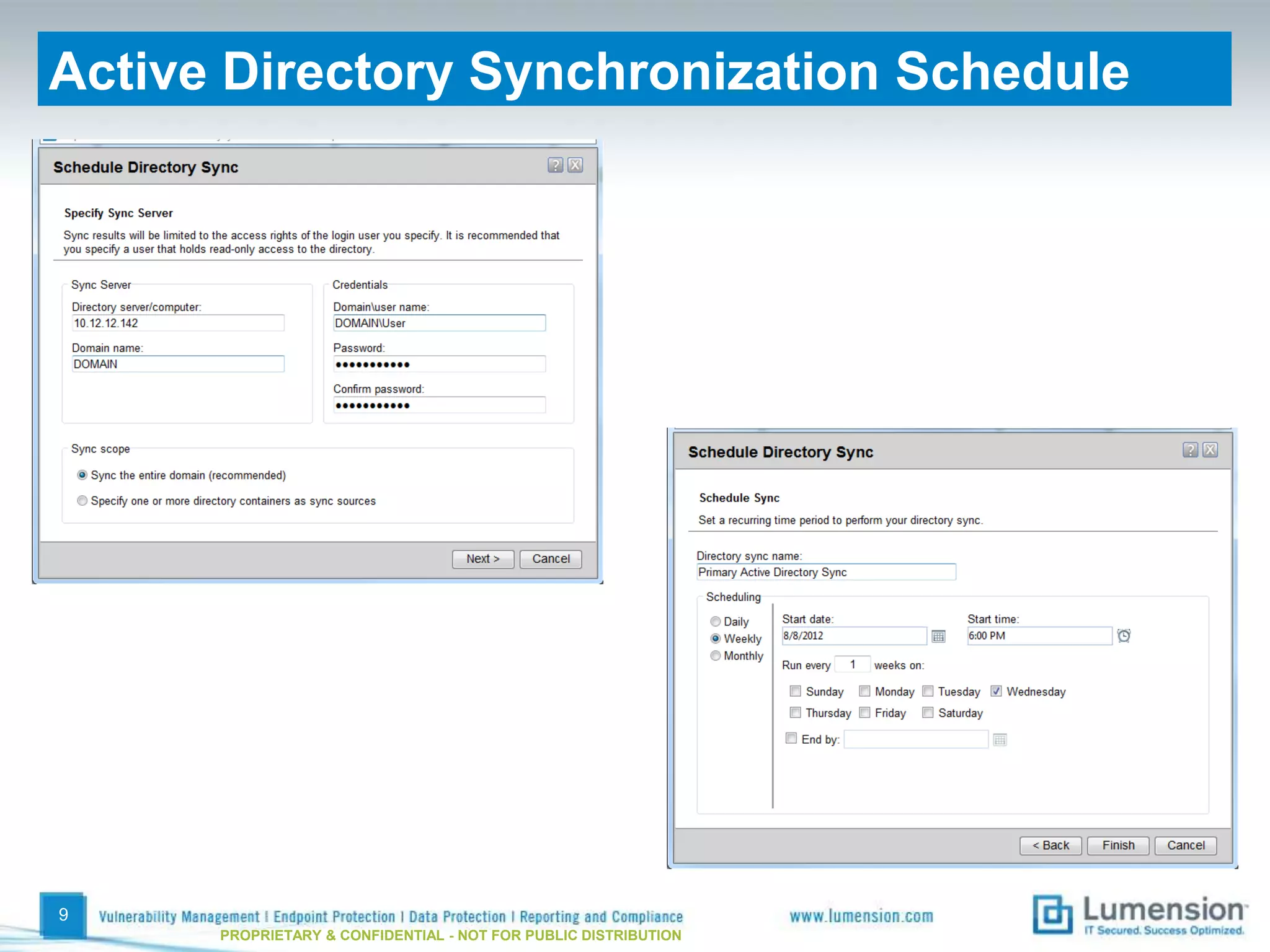
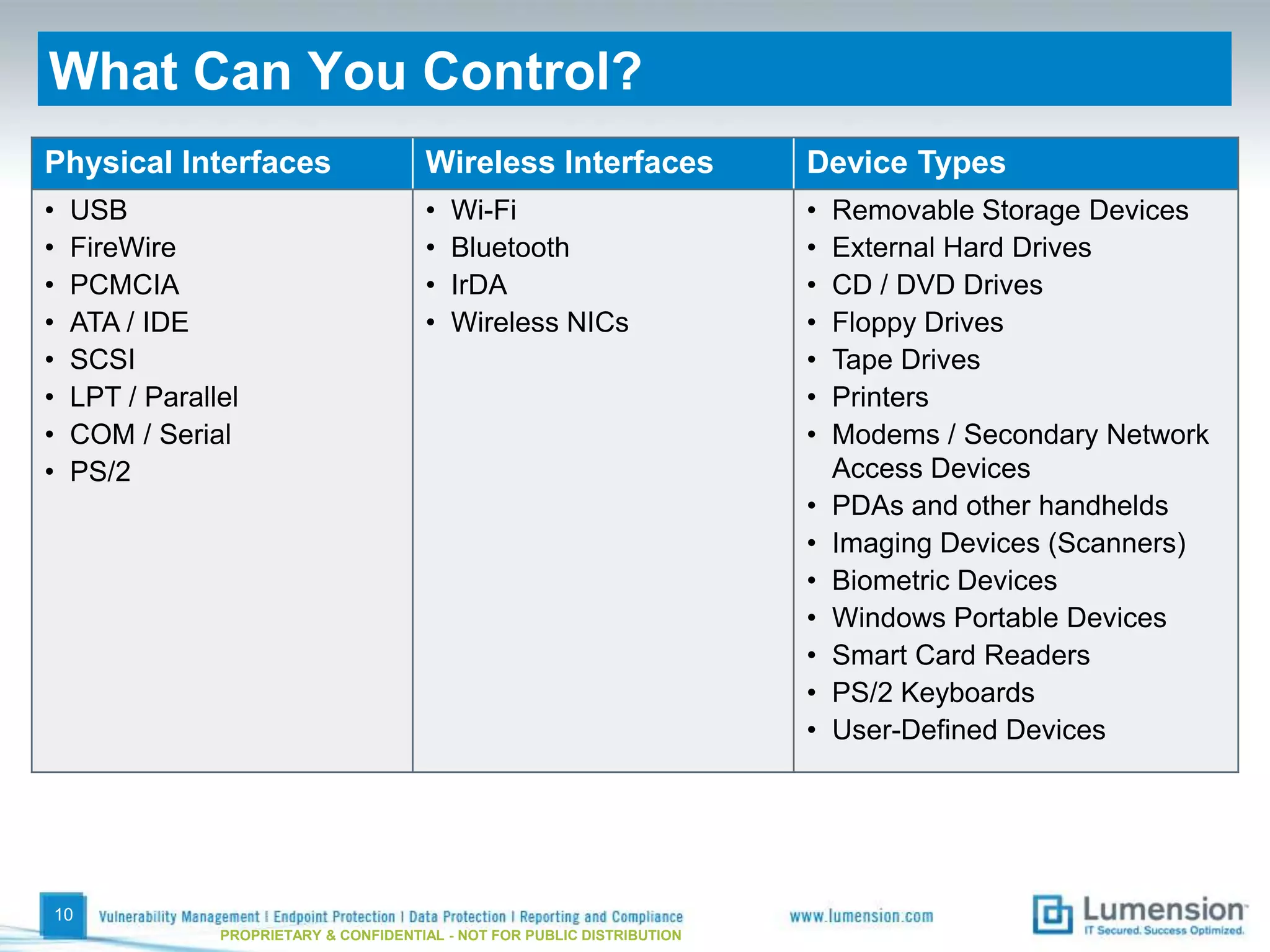
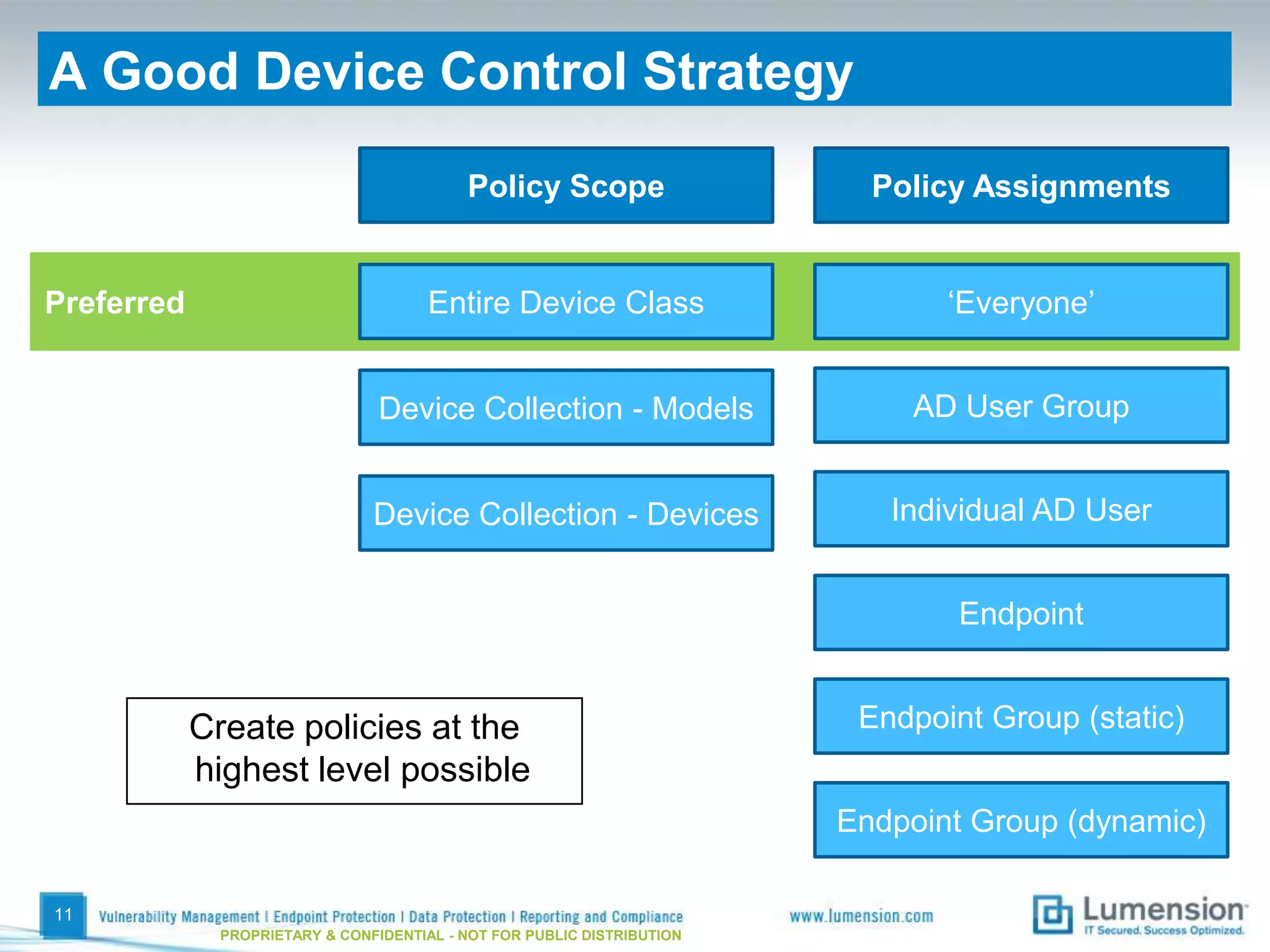
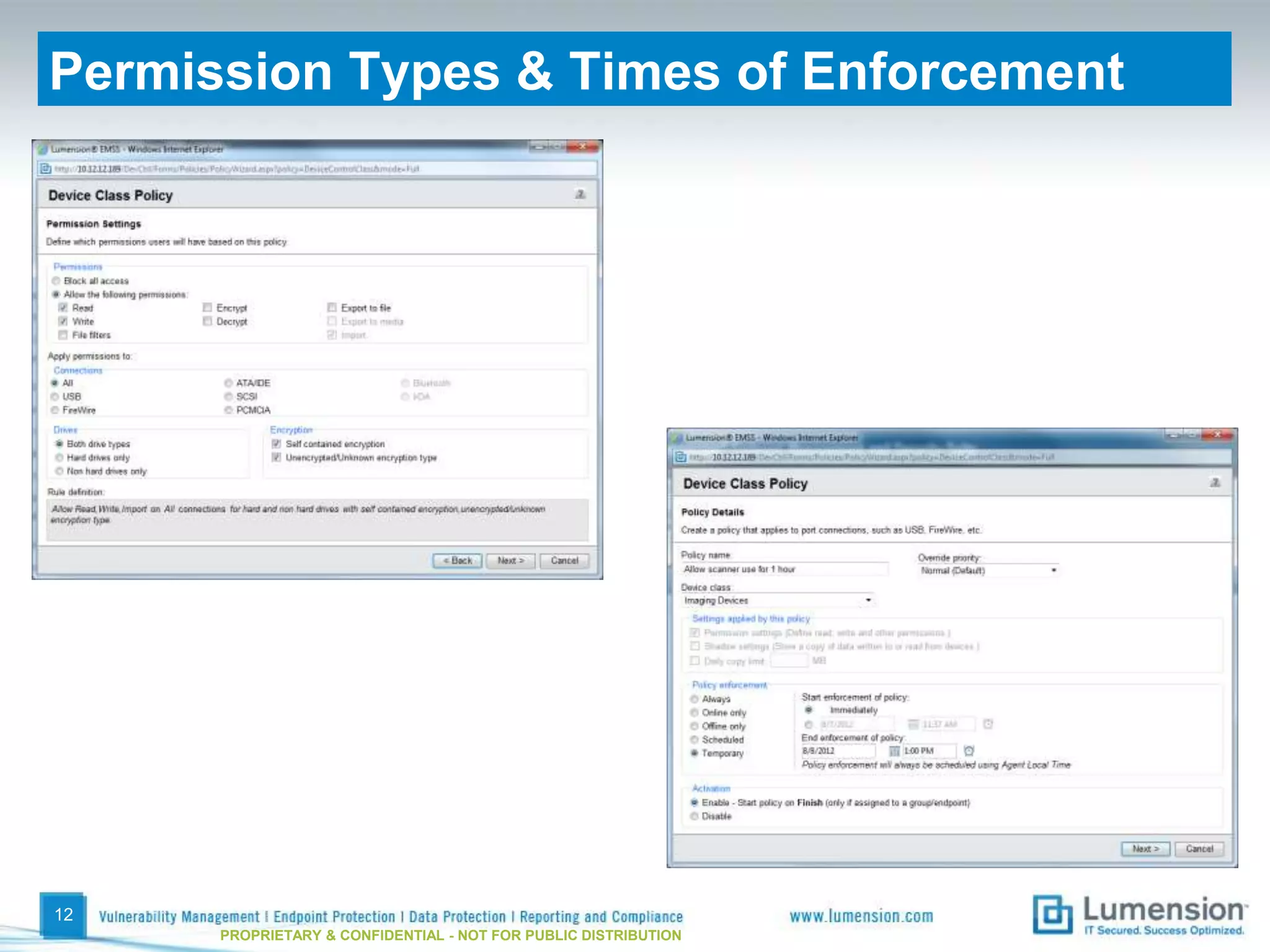
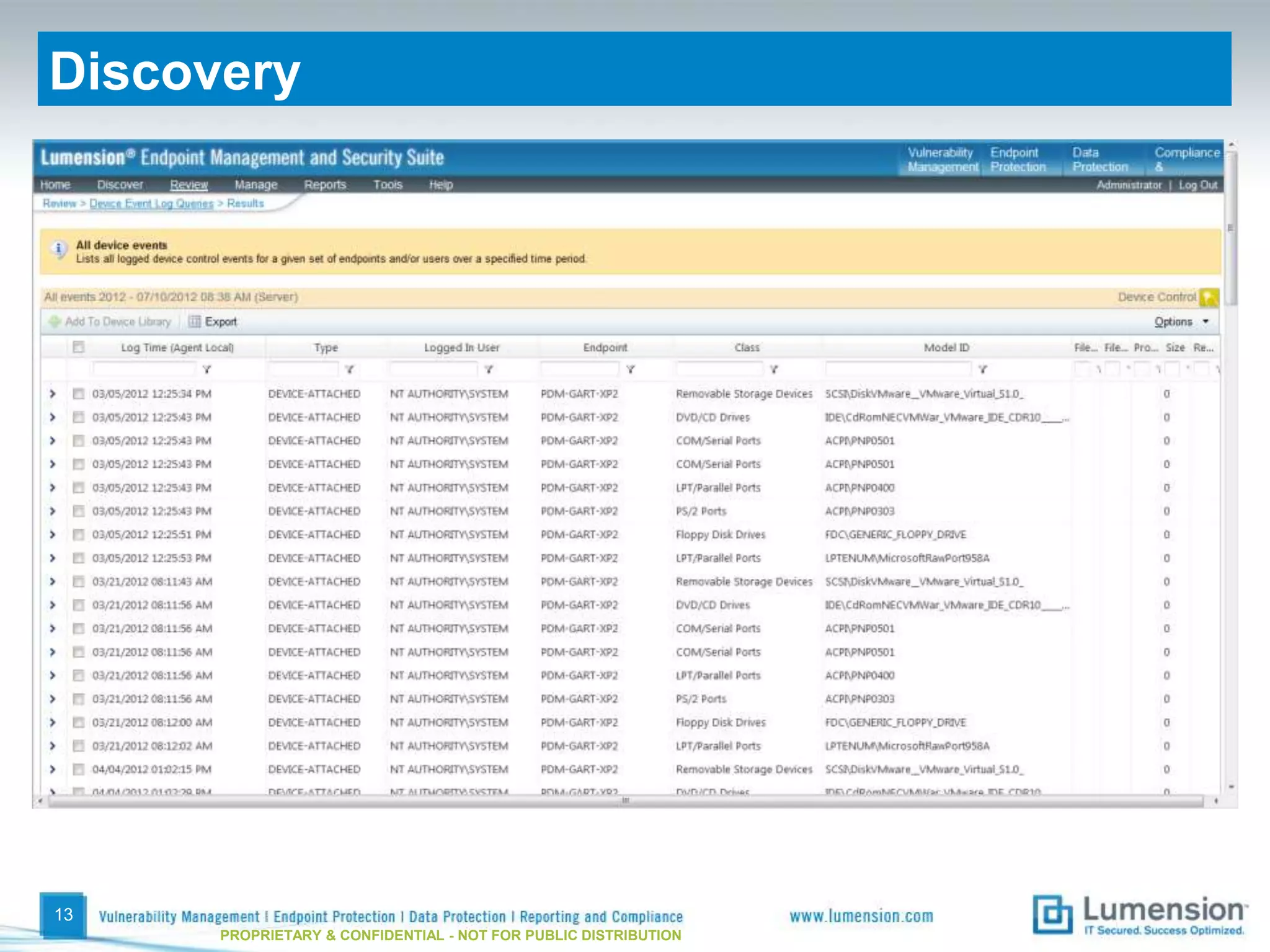
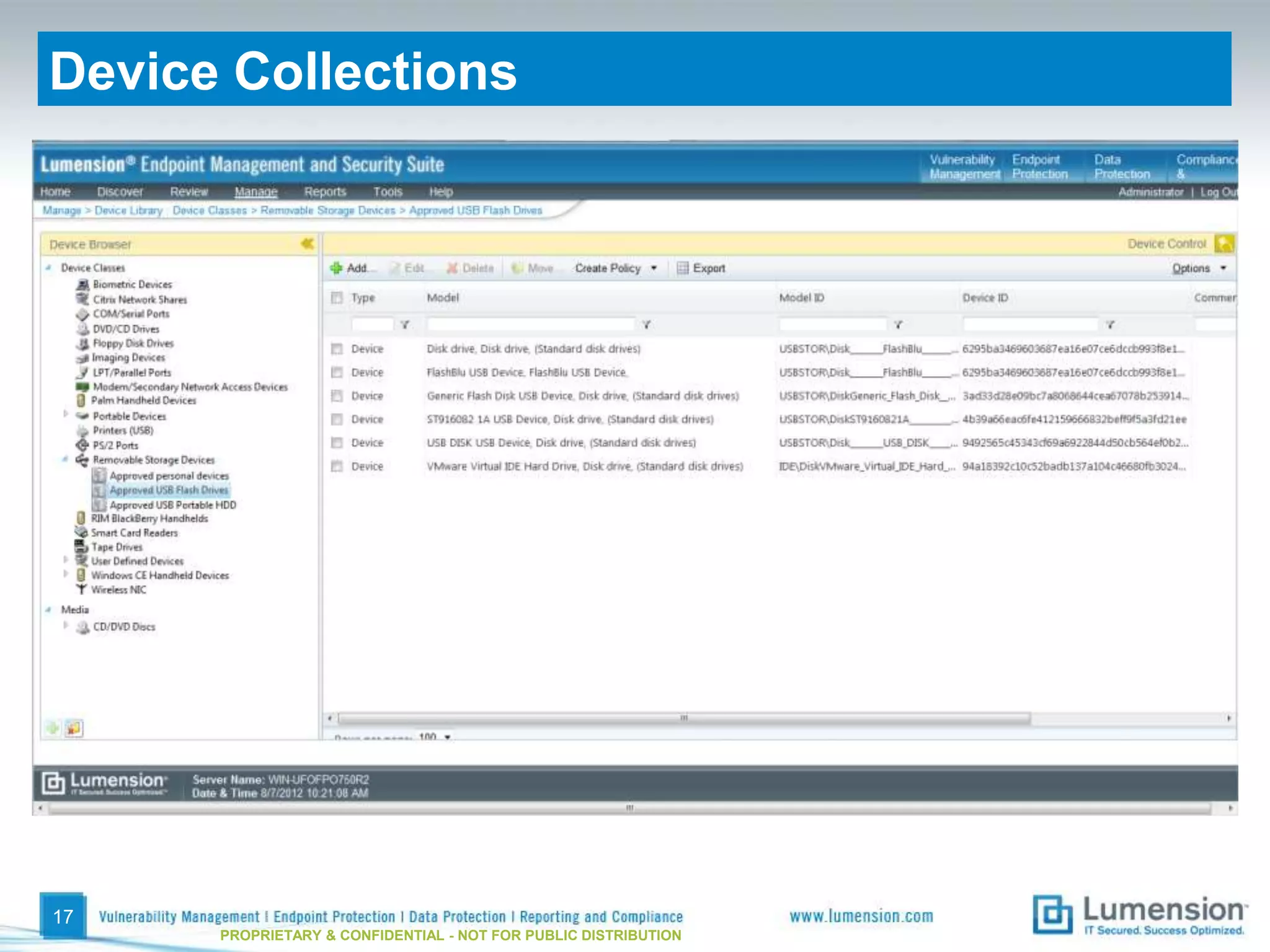
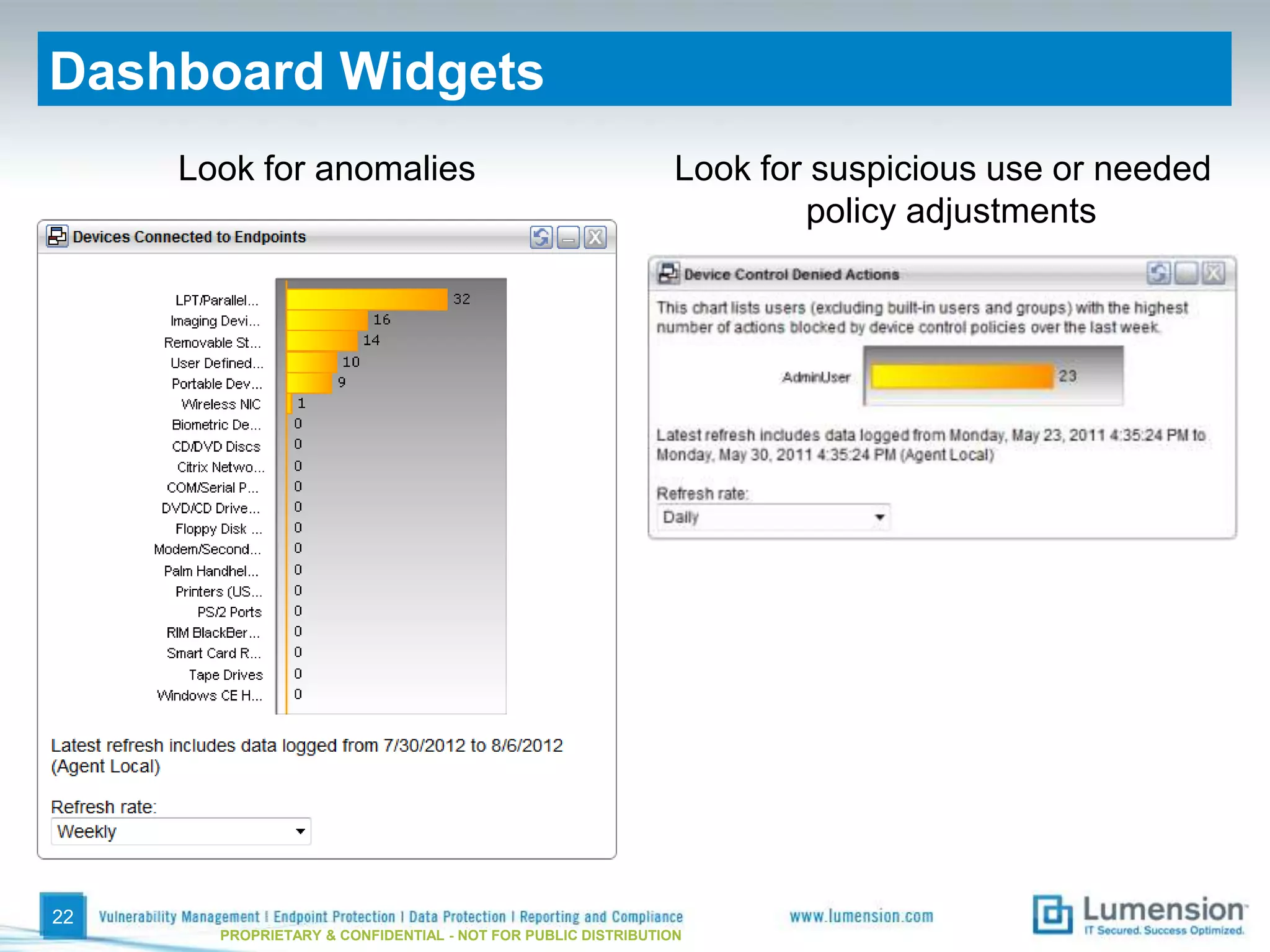
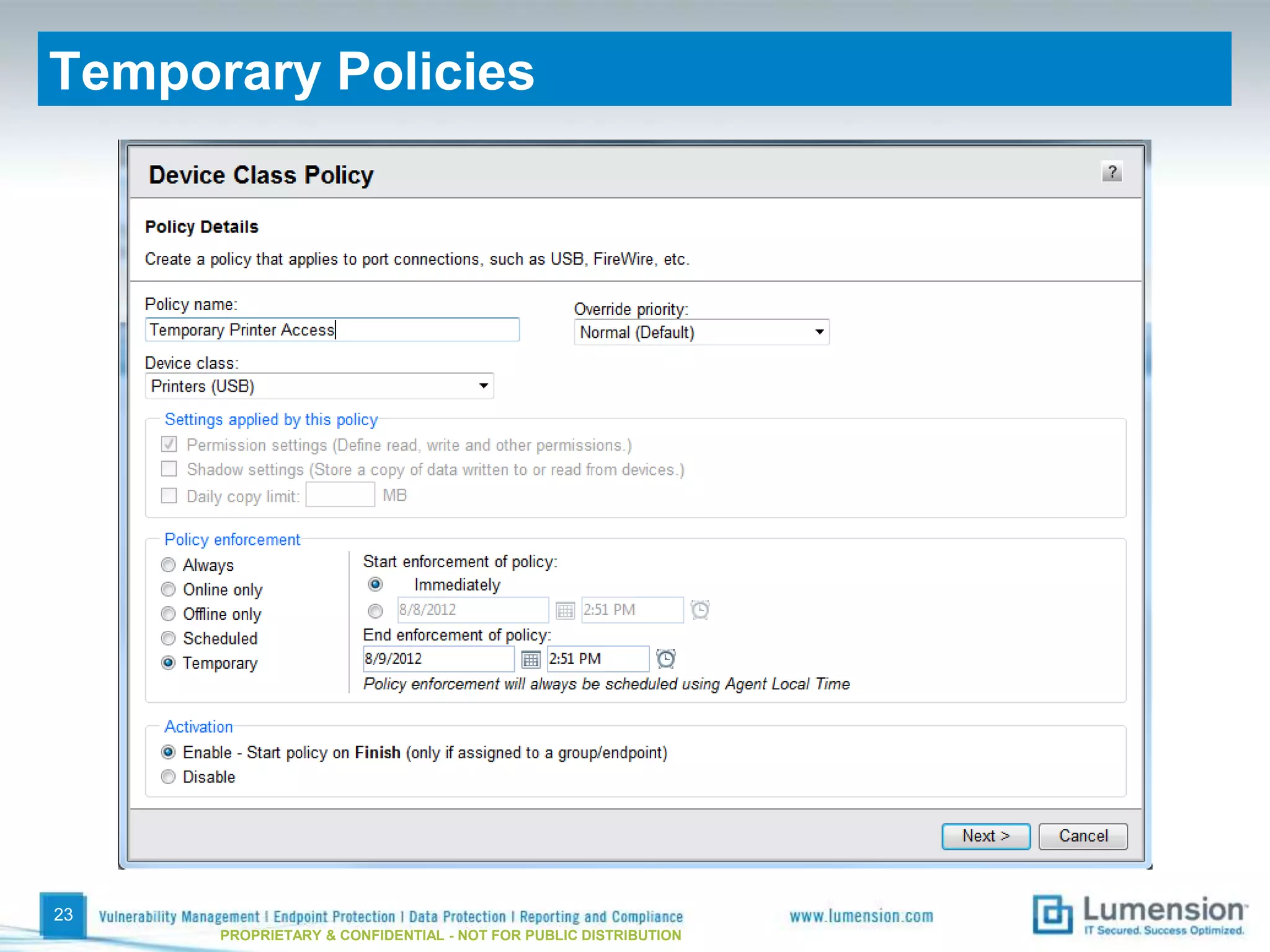
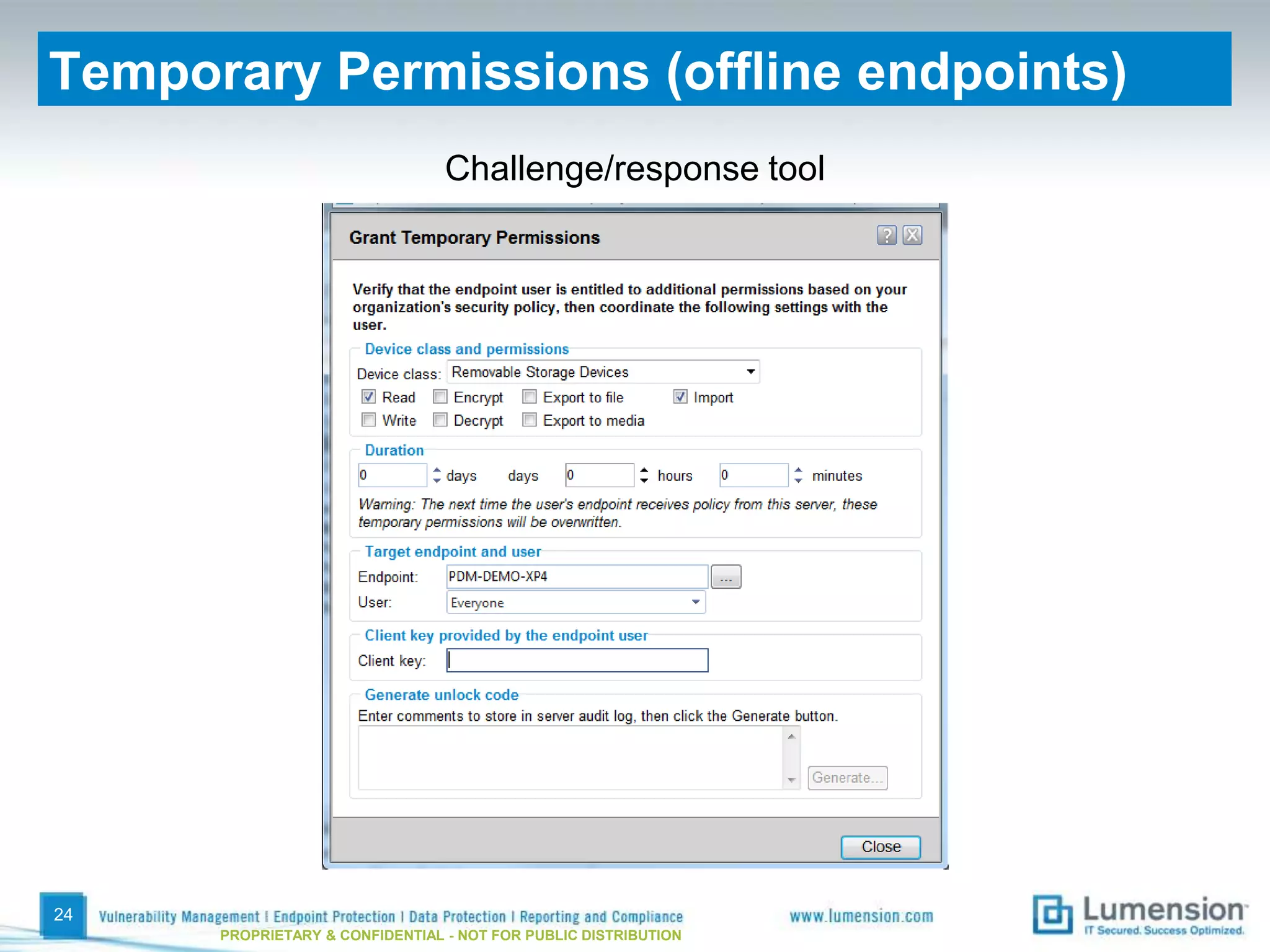
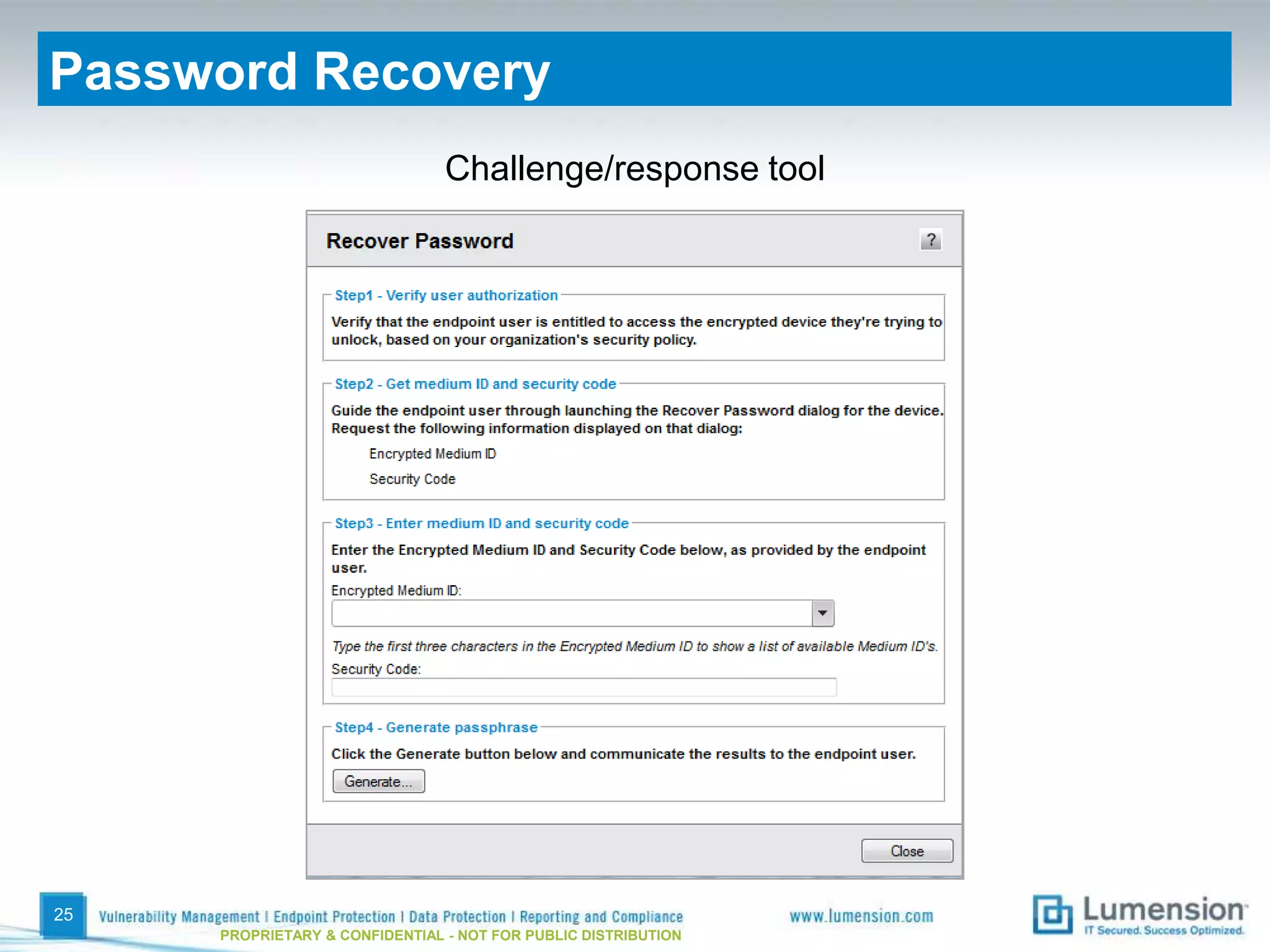
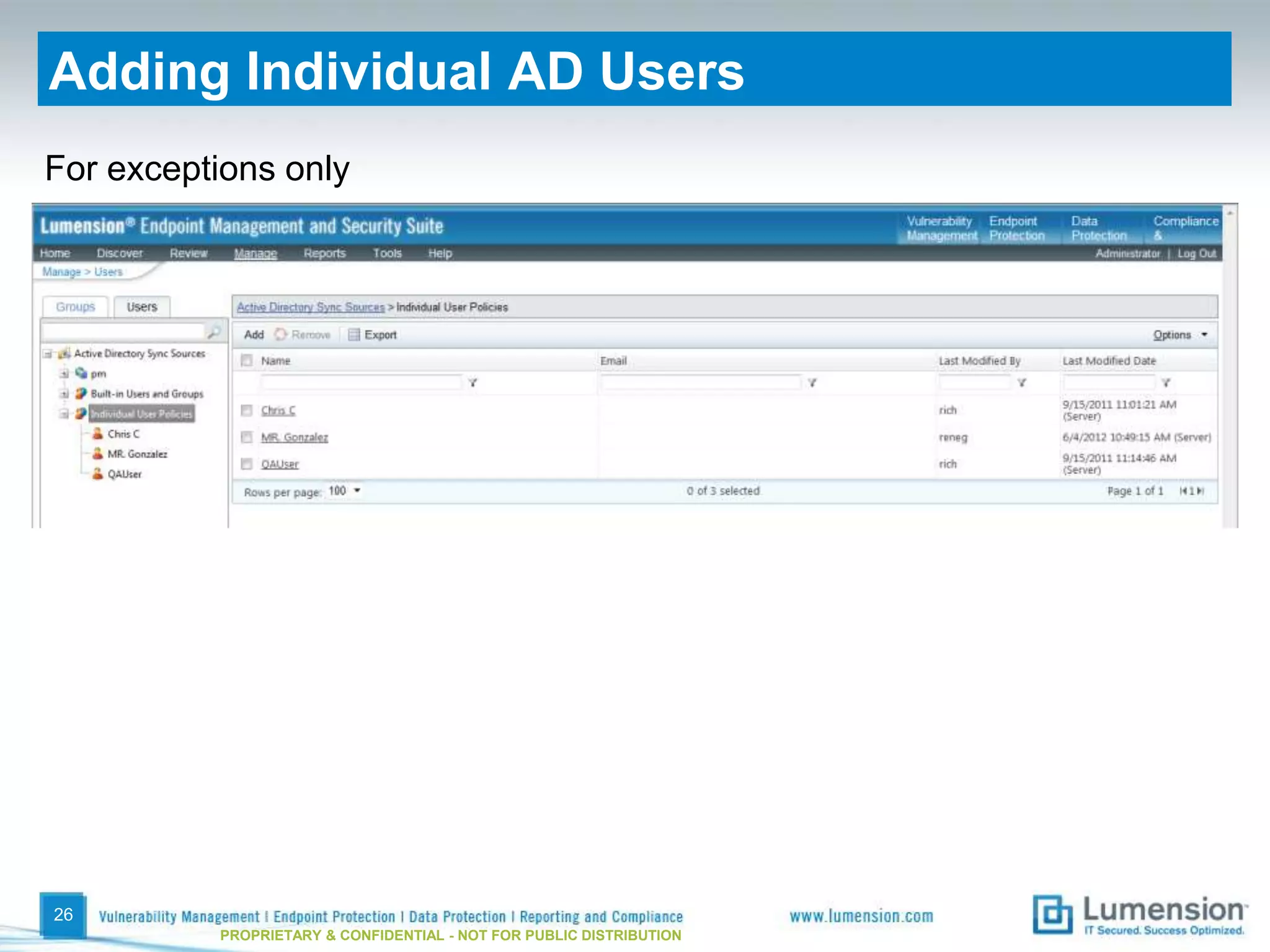
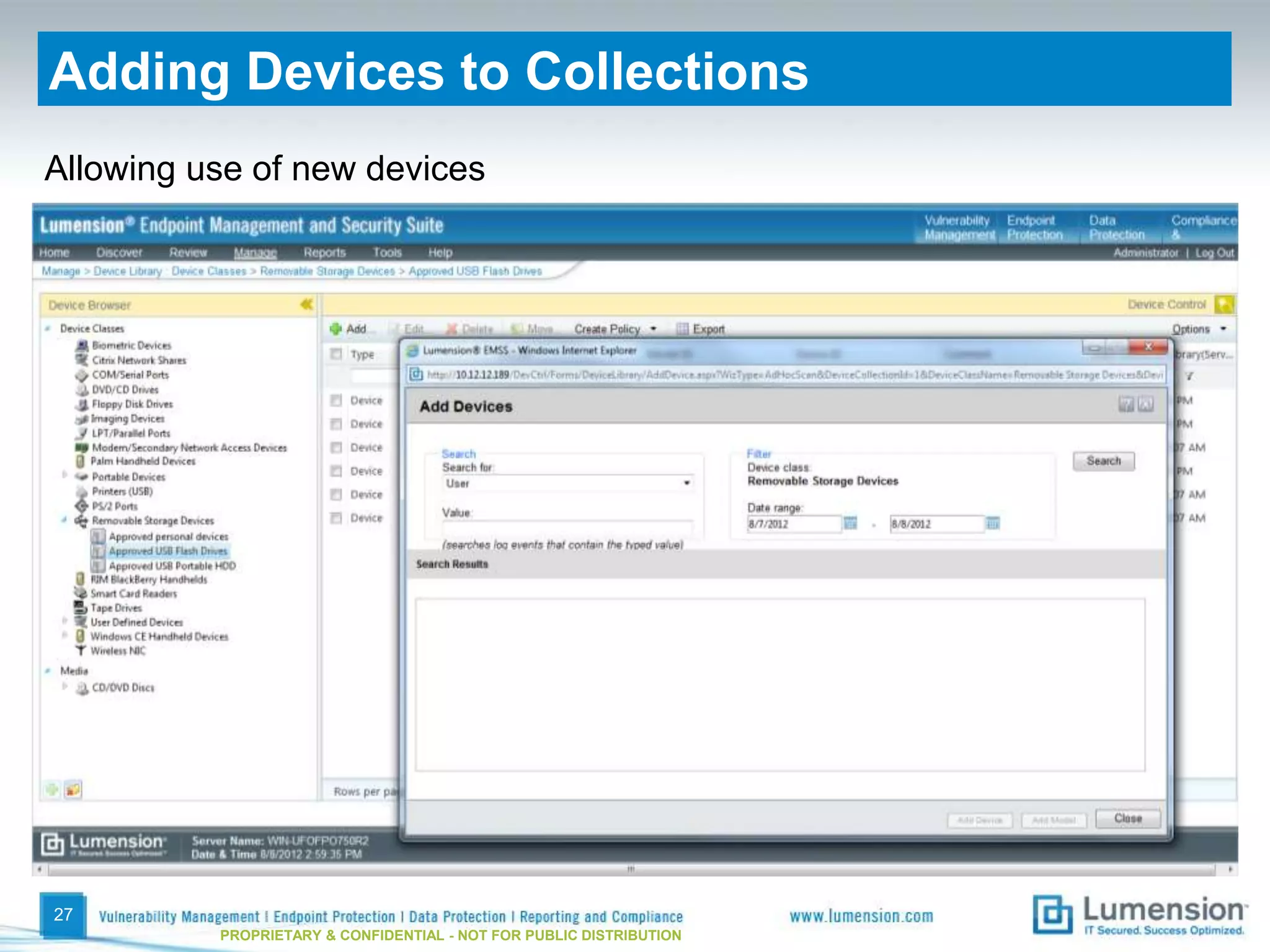
The document discusses best practices for implementing device control policies to protect organizational data. It recommends augmenting endpoint security with device control and lays out steps for preparing and enforcing policies, including laying groundwork by understanding the security profile and policy considerations, preparing by creating policies for device classes and collections, and enforcing policies through a phased rollout while managing device control through monitoring dashboards and handling exceptions. The goal is to control removable storage, external drives, and other devices to prevent data loss and theft.