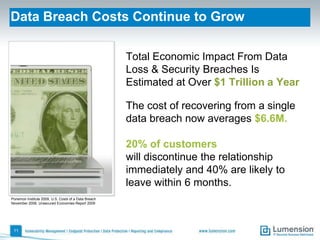
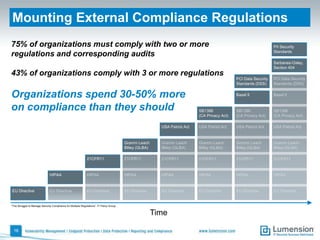
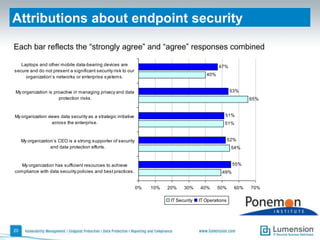
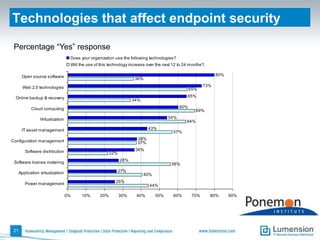
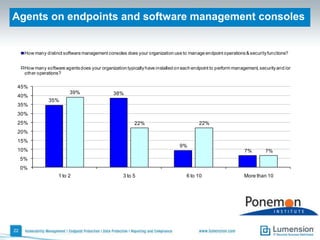
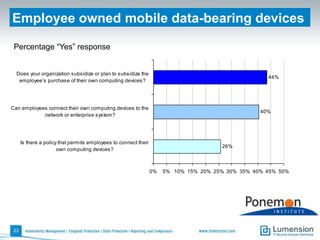
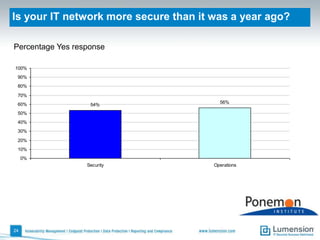
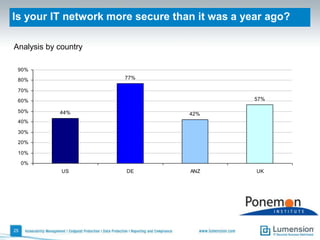
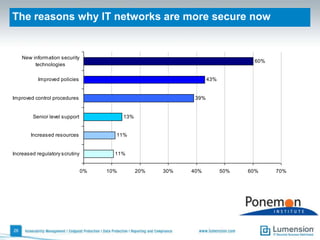
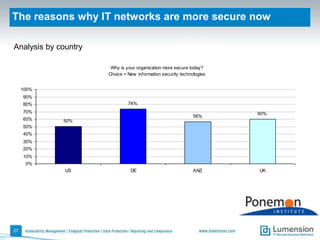
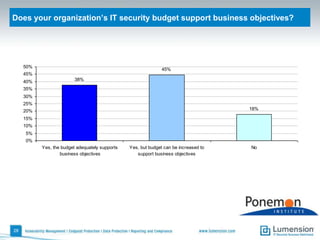
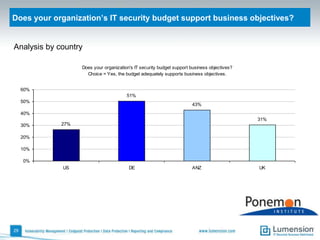
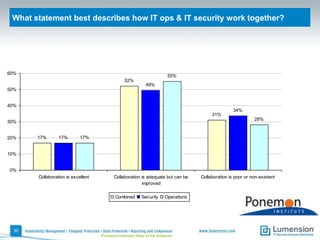
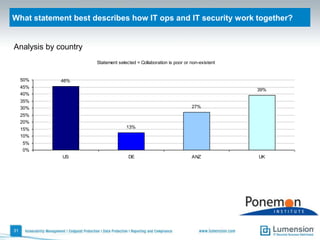
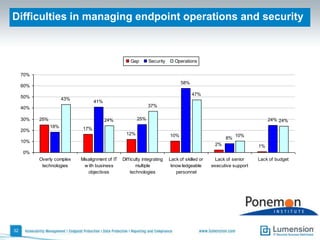
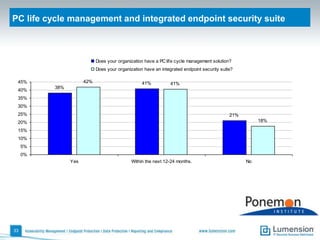
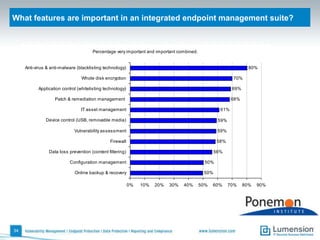
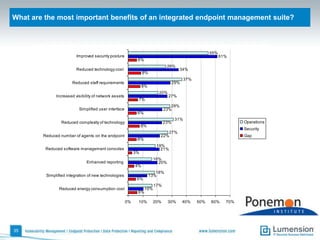
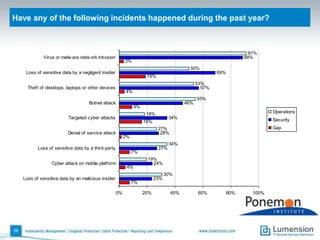
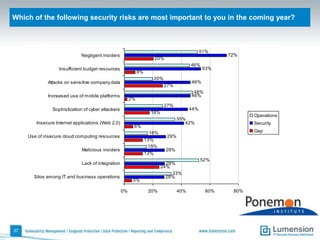
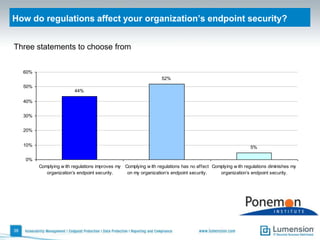
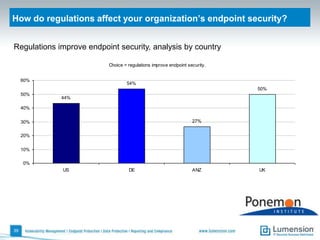
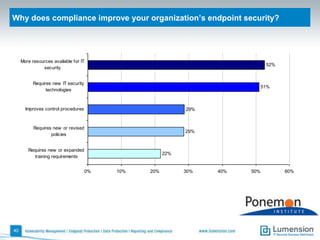
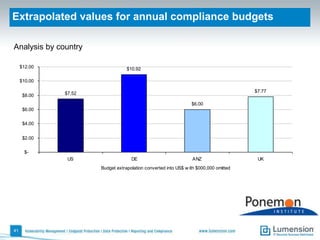
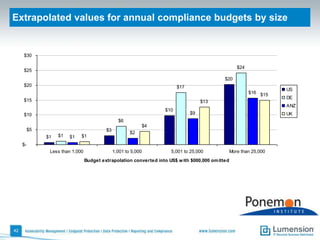
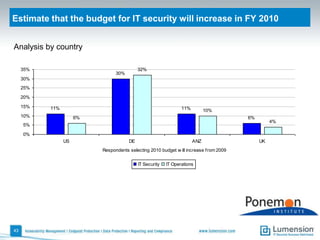
The document discusses the evolving challenges and landscape of endpoint security, highlighting the complexity and disjointed management of endpoint security amidst increasing threats, compliance demands, and the consumerization of IT. It underscores the need for improved collaboration between IT operations and security teams, as well as a shift towards a trust-centric approach to protect information flow rather than merely securing devices. Recommendations are made for organizations to adopt integrated security tools and re-evaluate their strategies in light of the changing technology landscape.