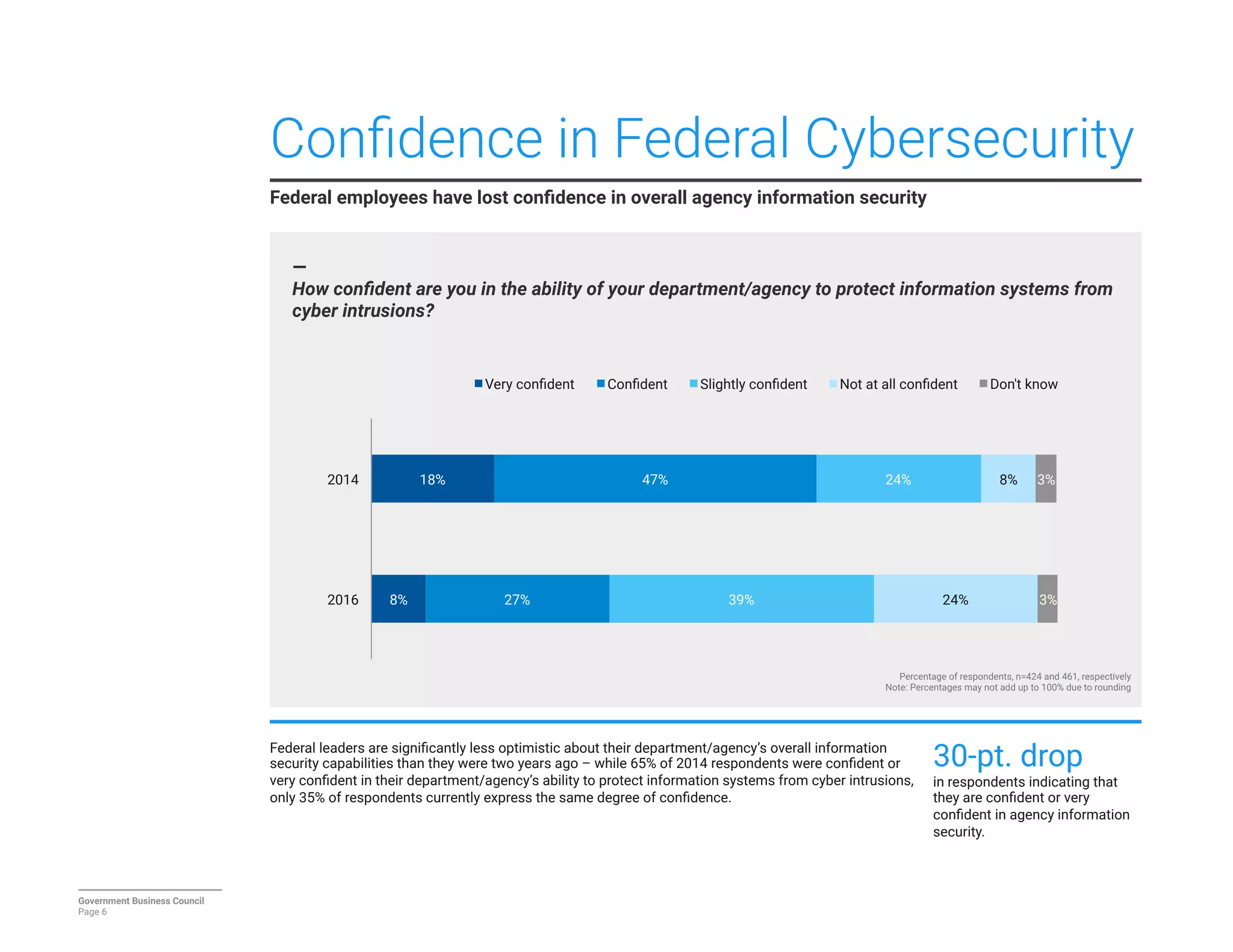
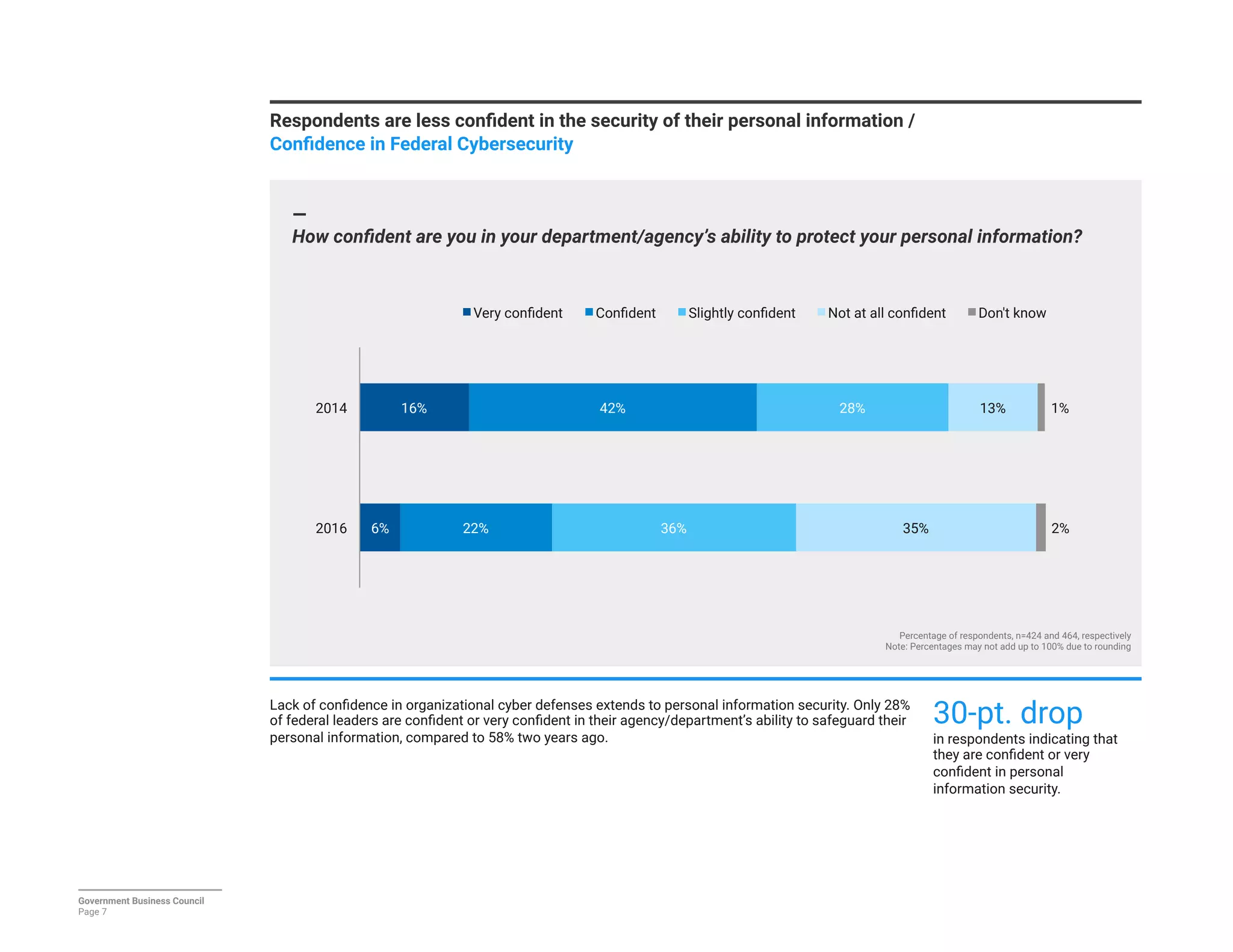
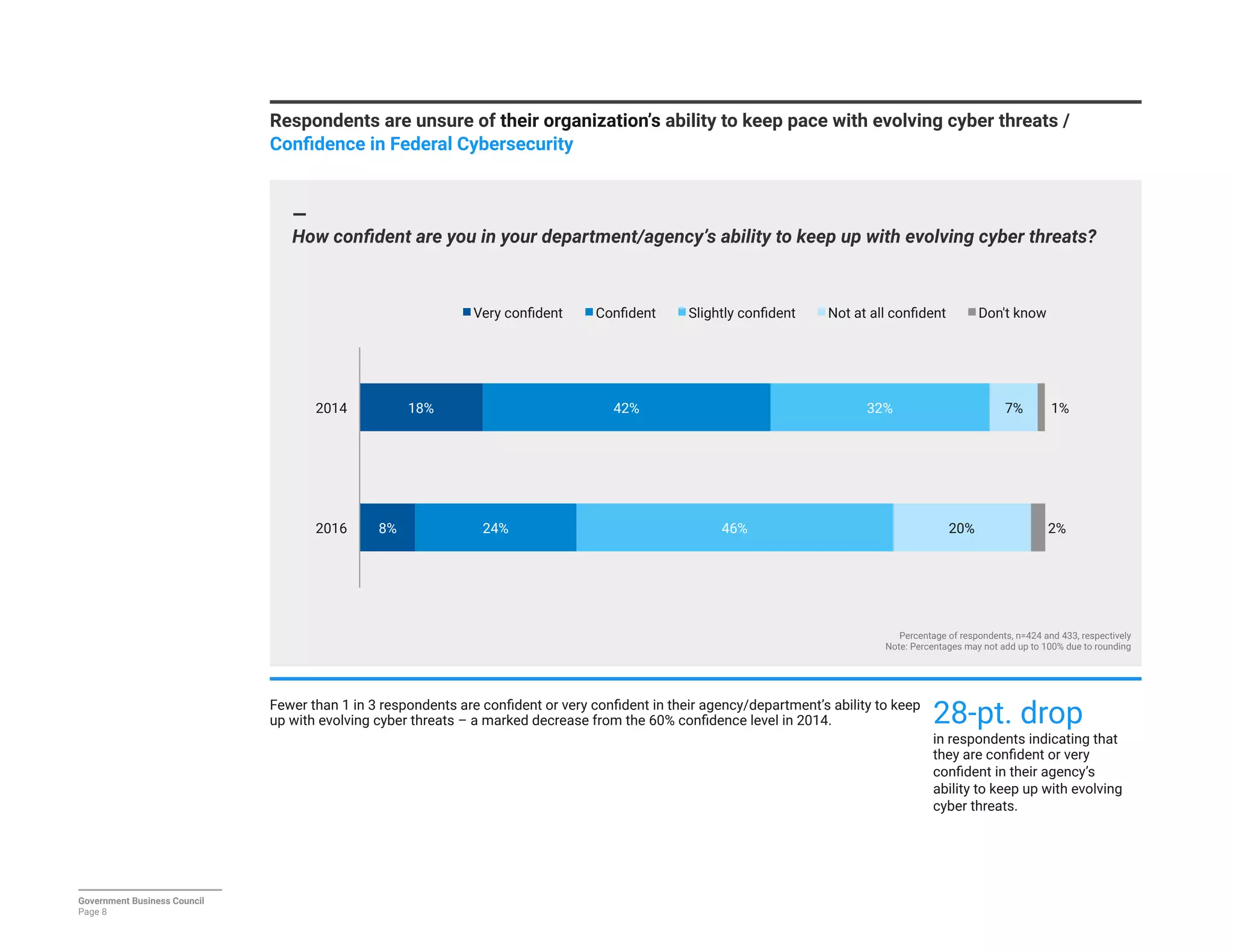
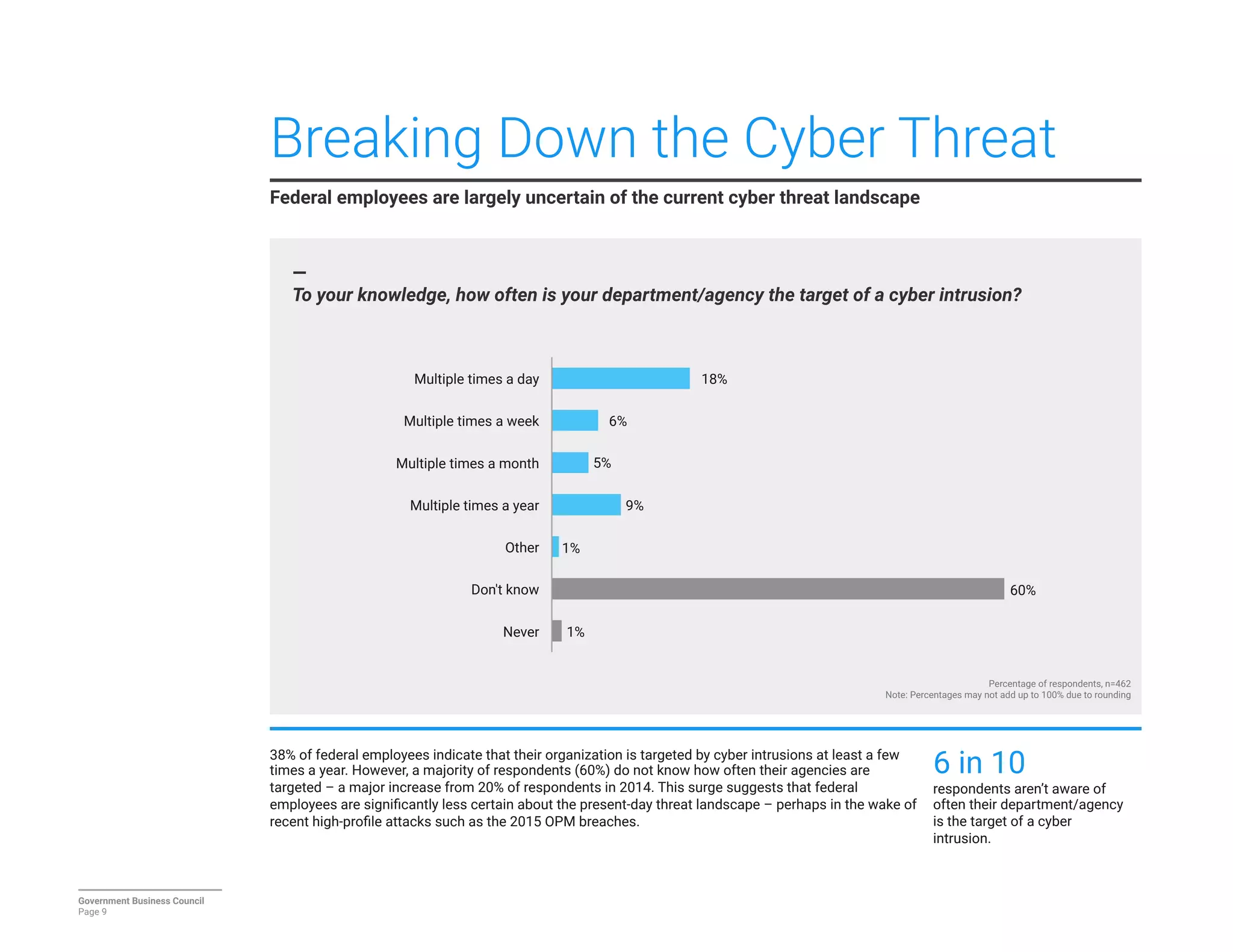
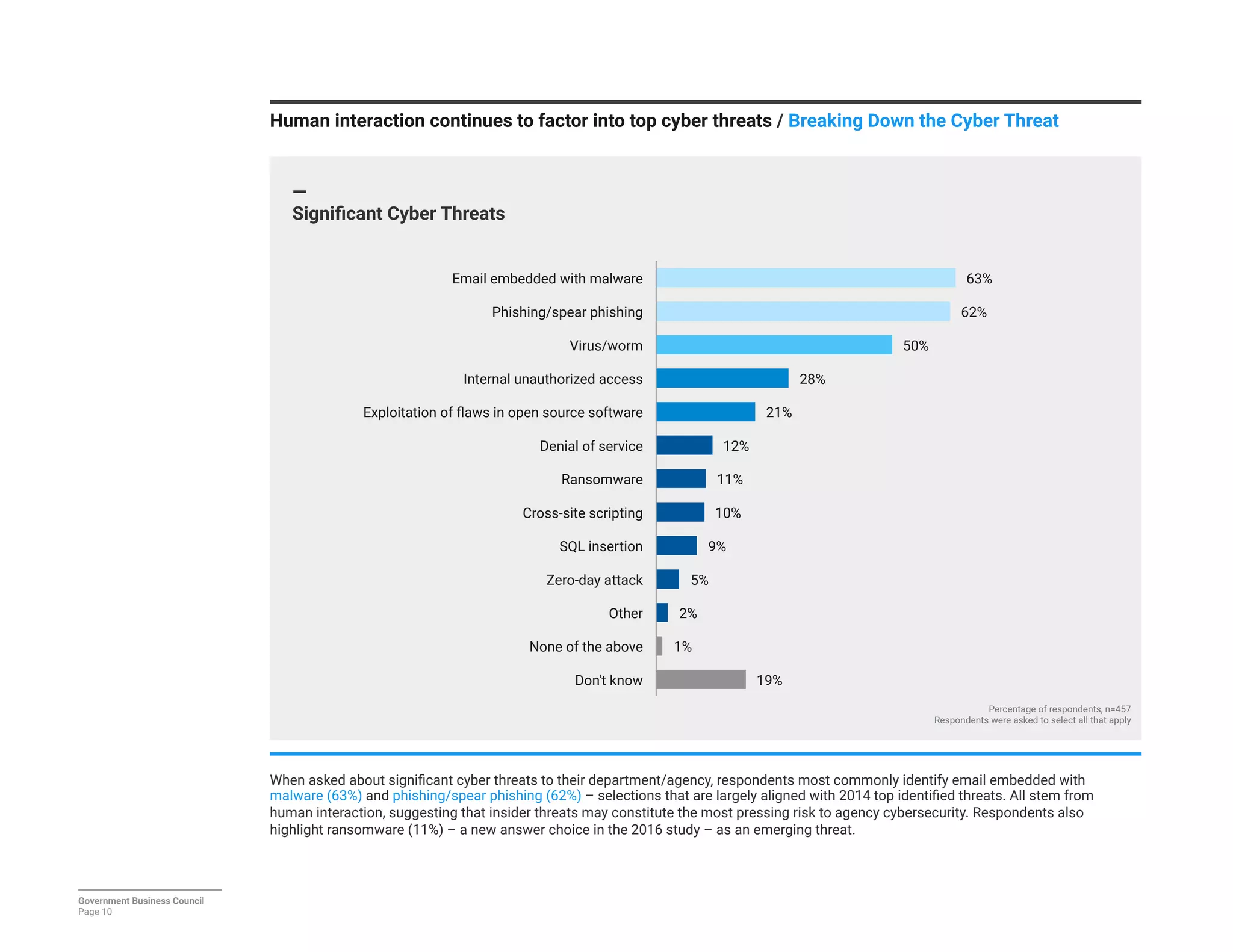
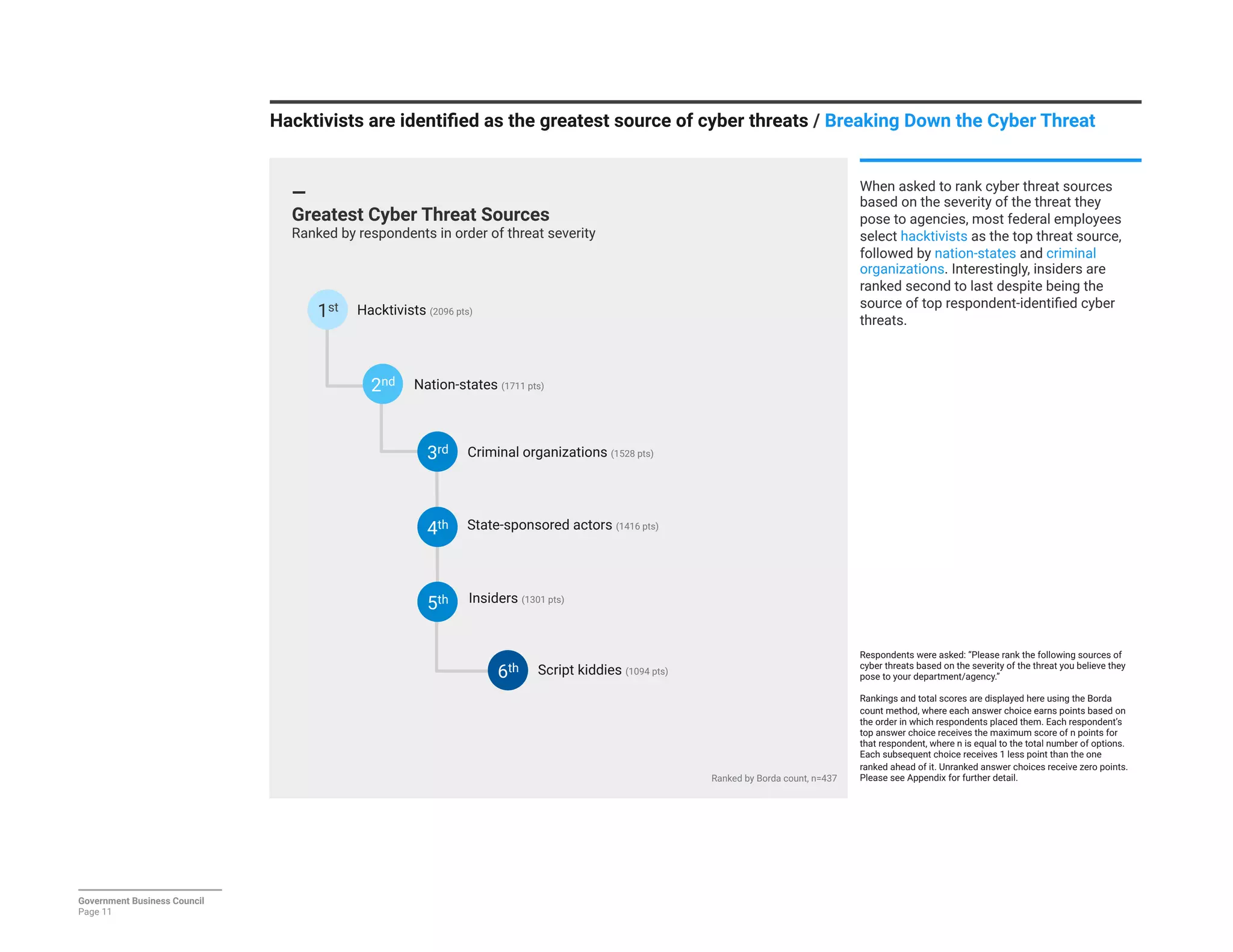
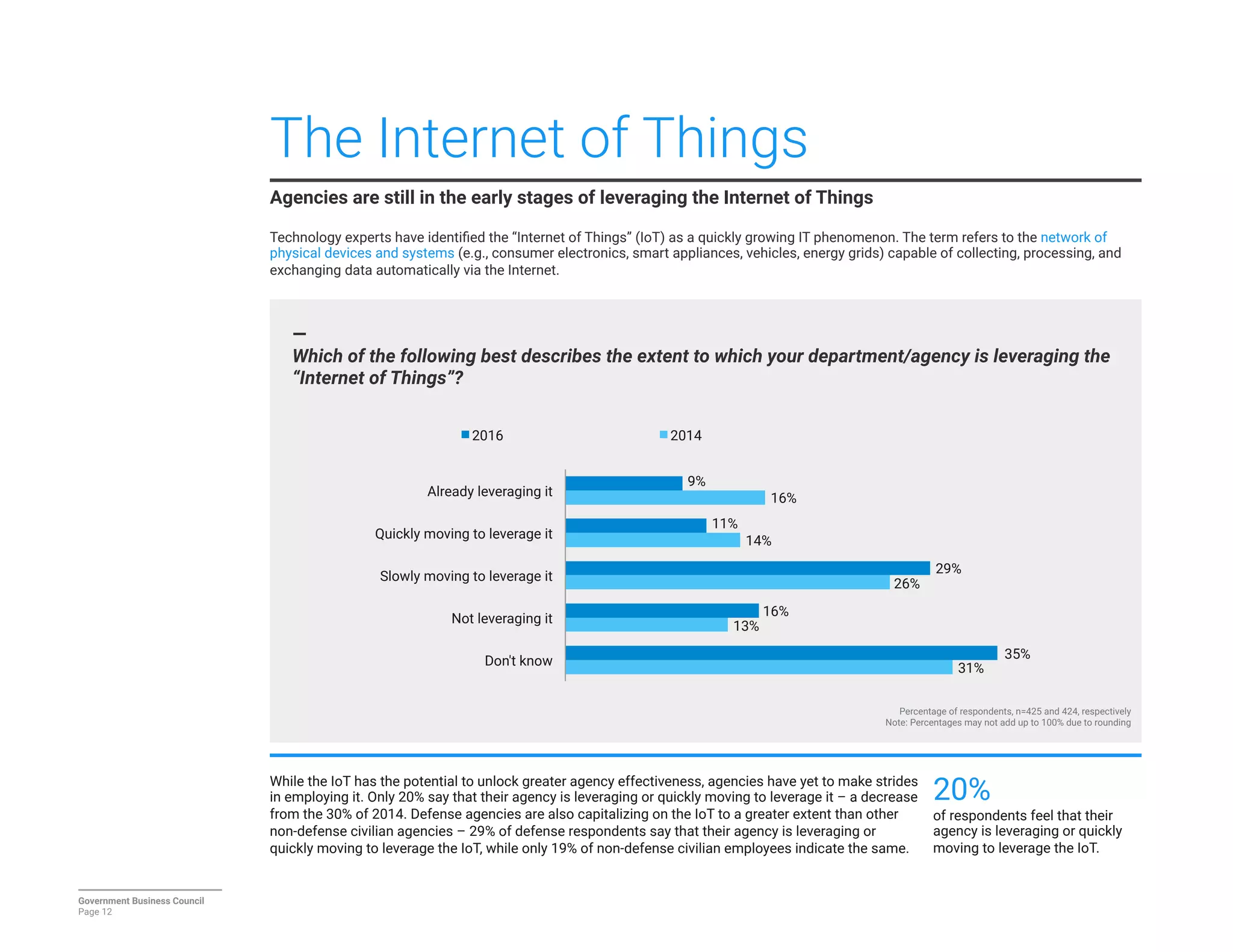
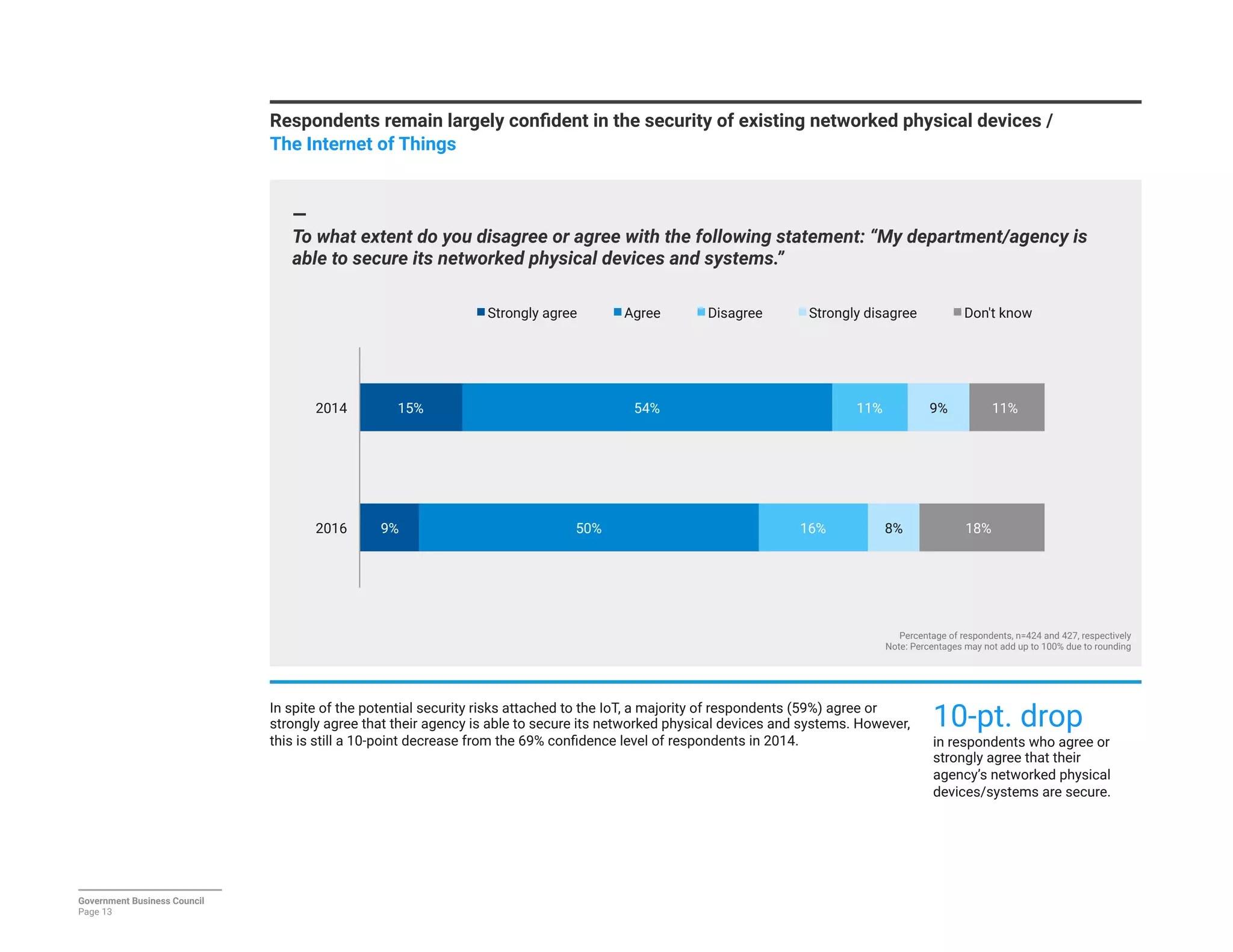
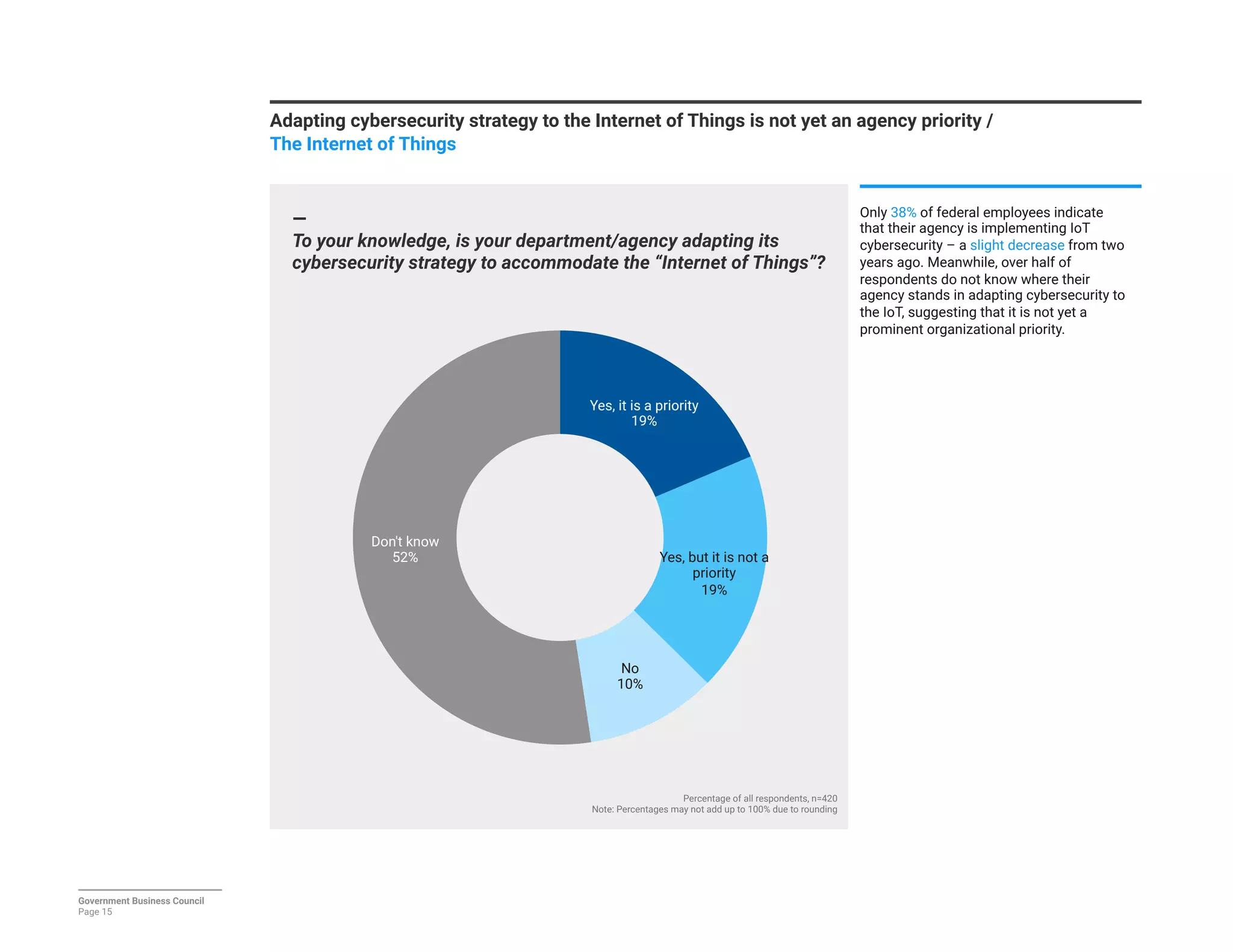
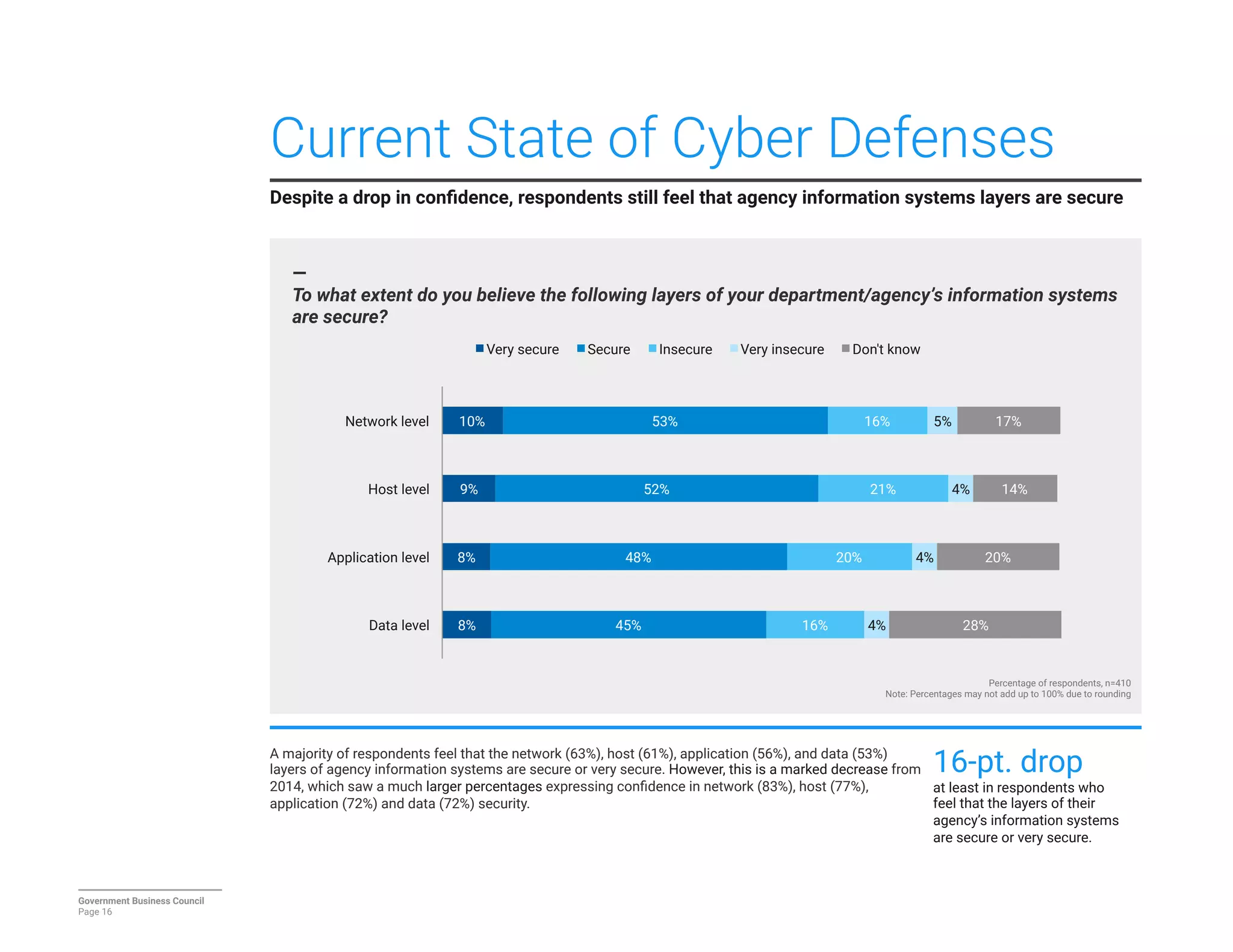
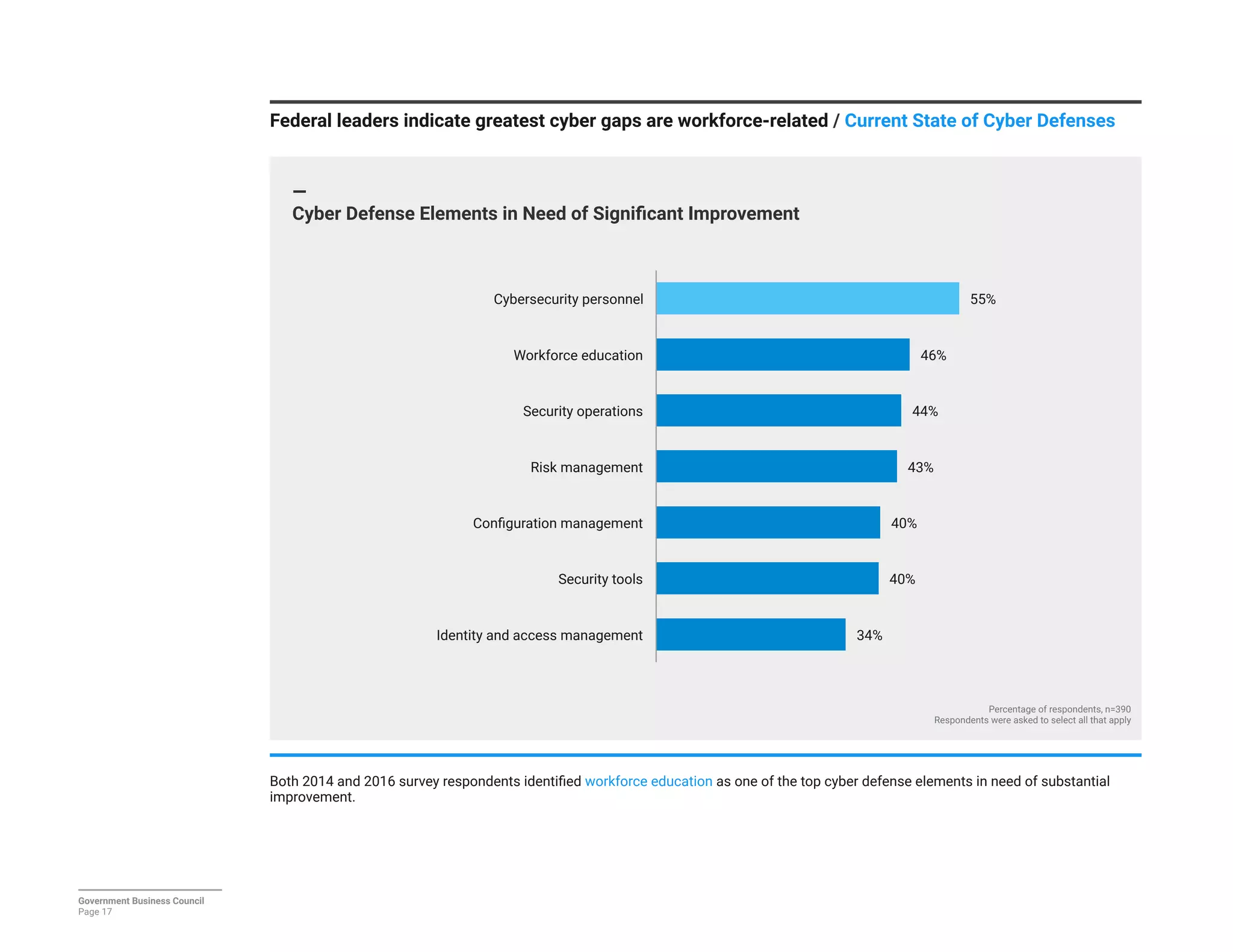
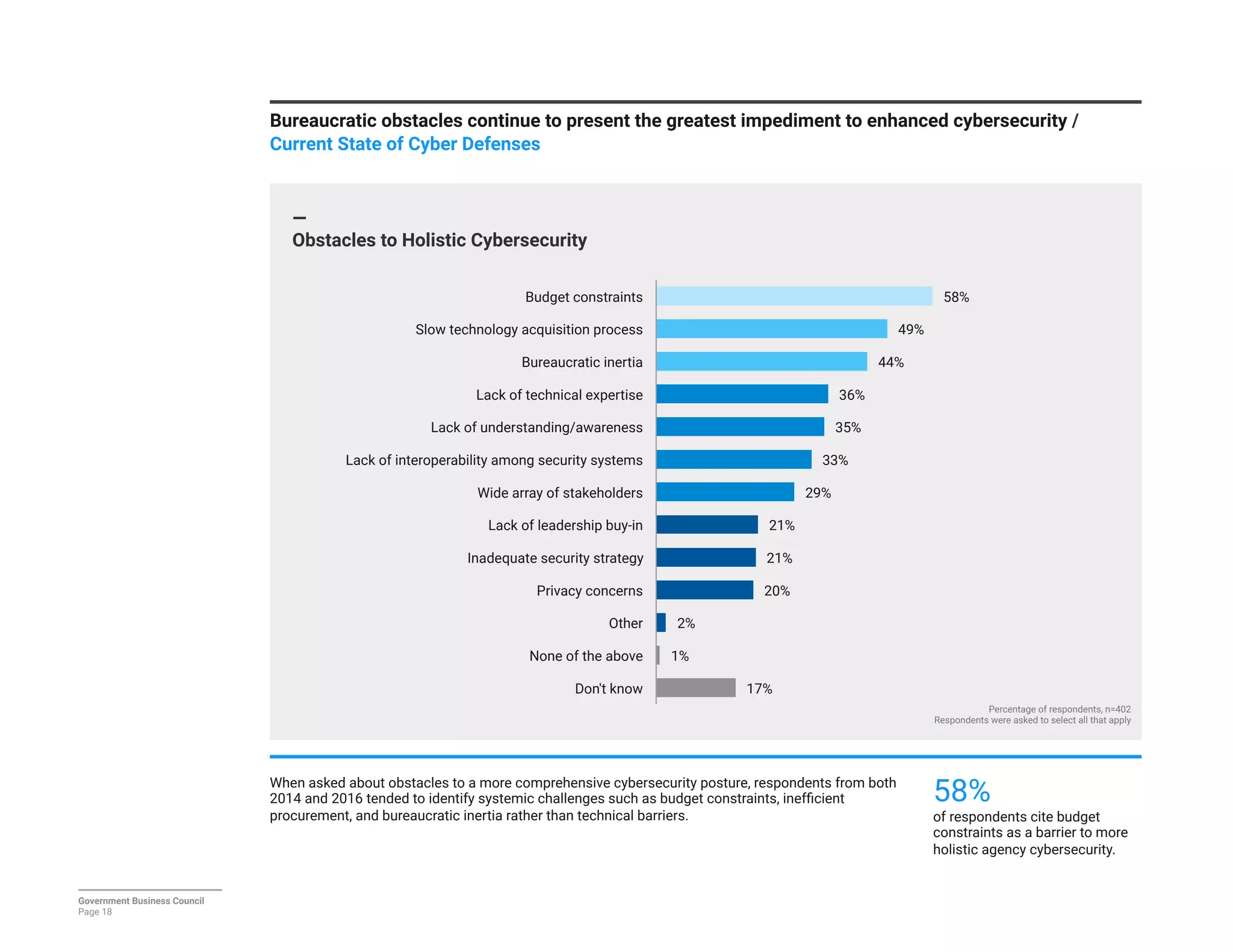
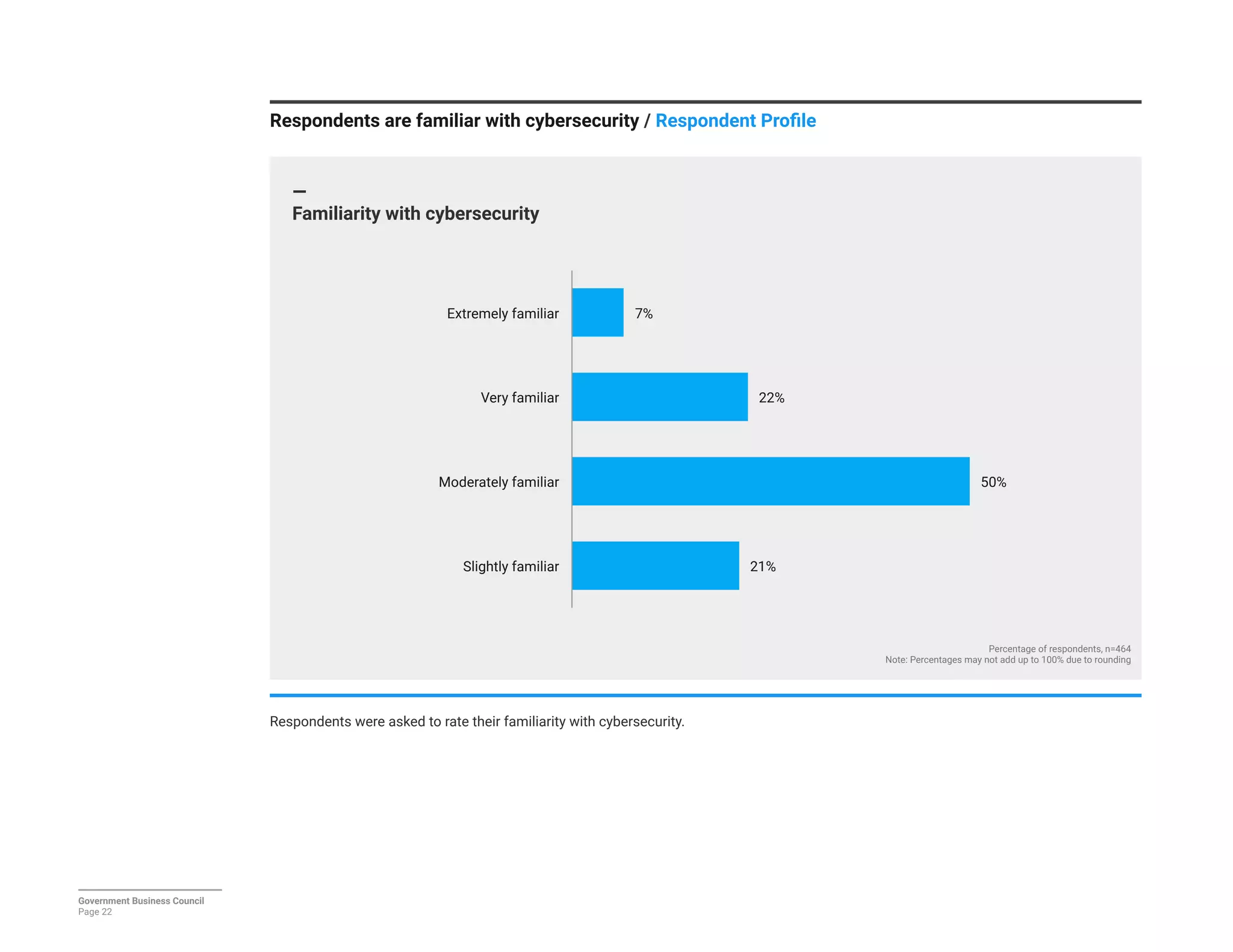
The report details a significant decline in federal leaders' confidence regarding agency cybersecurity from 2014 to 2016, with only 35% expressing confidence in their organization's ability to protect information systems. Major concerns include inadequate workforce education and bureaucratic barriers that impede progress in cybersecurity measures, particularly in adapting to the threats posed by the Internet of Things (IoT). Respondents identified human-related vulnerabilities, such as phishing and malware email attacks, as primary threats, emphasizing the need for improved training and resource allocation.