SSL/TLS 101 provides an overview of SSL and TLS including:
1) SSL and TLS are cryptographic protocols that provide security for internet communications like HTTPS and HTTP/2. They provide confidentiality, integrity, and authentication.
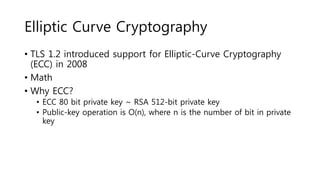
2) Key concepts of SSL/TLS include symmetric encryption for confidentiality, public key cryptography for key exchange, digital signatures for authentication, and X.509 certificates issued by certificate authorities to verify identities.
3) The document reviews the history and versions of SSL/TLS, how the core requirements of confidentiality, integrity and authentication are achieved, and references for further reading on implementing SSL/TLS.



![OSI Model Layer
# OSI Layer Description Example protocols
7 Application Application data HTTP, SMTP, IMAP
6 Presentation Data representation, conversion, encryption SSL/TLS
5 Session Management of multiple connection -
4 Transport Reliable delivery of packets and streams TCP, UDP
3 Network Routing and delivery of datagrams between
network nodes
IP, IPSec
2 Data link Reliable local data connection (LAN) Ethernet
1 Physical Direct physical data connection (cables) CAT5
[BPST] p3](https://image.slidesharecdn.com/ssltls101-151218063117-170929002248/85/SSL-TLS-101-4-320.jpg)














![X.509
• International
Telecommunication Union (ITU)
defines and maintains SSL/TLS
certificate format in a series of
documents
• X.509 : Information technology -
Open Systems Interconnection -
The Directory: Public-key and
attribute certificate frameworks
• RFC2459: Internet X.509 Public
Key Infrastructure Certificate
and CRL Profile
Certificate ::= SEQUENCE {
tbsCertificate TBSCertificate,
signatureAlgorithm AlgorithmIdentifier,
signatureValue BIT STRING }
TBSCertificate ::= SEQUENCE {
version [0] EXPLICIT Version DEFAULT v1,
serialNumber CertificateSerialNumber,
signature AlgorithmIdentifier,
issuer Name,
validity Validity,
subject Name,
subjectPublicKeyInfo SubjectPublicKeyInfo,
issuerUniqueID [1] IMPLICIT UniqueIdentifier OPTIONAL,
-- If present, version shall be v2 or v3
subjectUniqueID [2] IMPLICIT UniqueIdentifier OPTIONAL,
-- If present, version shall be v2 or v3
extensions [3] EXPLICIT Extensions OPTIONAL
-- If present, version shall be v3
}](https://image.slidesharecdn.com/ssltls101-151218063117-170929002248/85/SSL-TLS-101-20-320.jpg)
![Reference
• [BPST] Bulletproof SSL and TLS, Ivan Ristic, Feisty Duck
• [IST] Implementing SSL/TLS, Joshua Davies, Wiley](https://image.slidesharecdn.com/ssltls101-151218063117-170929002248/85/SSL-TLS-101-21-320.jpg)