The document outlines SQL injection and denial-of-service (DoS) attacks, detailing demonstration examples and effective countermeasures. It discusses common vulnerabilities in web applications and emphasizes the importance of validation, preparedness, and various security configurations. Additionally, it presents specific types of DoS attacks, such as Slowloris and LOC, and recommends proactive security measures to mitigate risks.


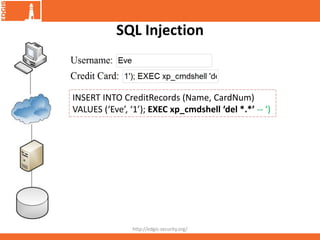
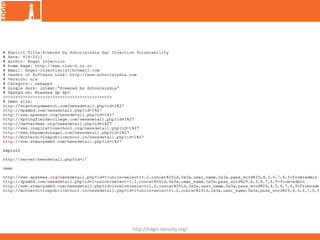
![Information Leakage
http://edgis-security.org/
• Error Type:
Microsoft OLE DB Provider for ODBC Drivers (0x1A2B3C4D)
[Microsoft ][ODBC SQL Server Driver][SQL Server]Unclosed
quotation mark before the character string ‘ and password = “,
/login.asp,line 30
• Error Type:
Microsoft OLE DB Provider for ODBC Drivers (0x1A2B3C4D)
[Microsoft ][ODBC SQL Server Driver][SQL Server]Unclosed
quotation mark before the character string ‘ and password = ‘123“’,
/login.asp,line 30
• User String Validation on Error
Handling](https://image.slidesharecdn.com/sqlinjectiondosslideshare-140608215411-phpapp01/85/SQL-Injection-and-DoS-6-320.jpg)
![Information Leakage (cont’d)
http://edgis-security.org/
• UNION Poisoning
SELECT * FROM records WHERE user=‘[user input]
‘ union all select name, xtype, 0, 0 from sysobjects --
SELECT * FROM records WHERE user=‘[user input]
‘ union all select <column> from <schema.columns>, 0, 0, 0 --](https://image.slidesharecdn.com/sqlinjectiondosslideshare-140608215411-phpapp01/85/SQL-Injection-and-DoS-7-320.jpg)