Embed presentation
Downloaded 166 times

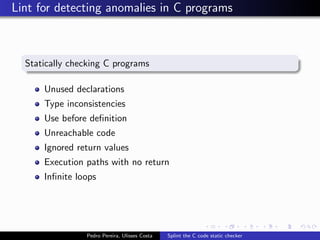


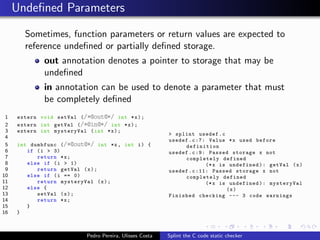
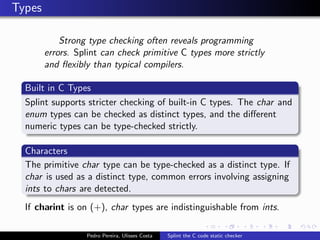

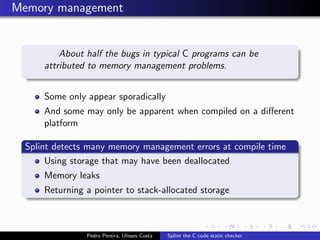

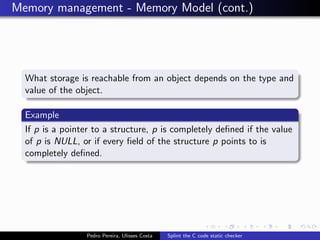
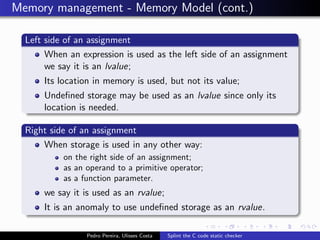

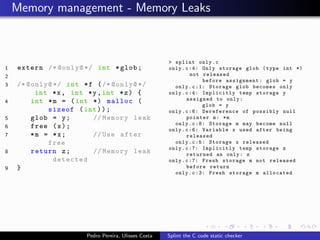
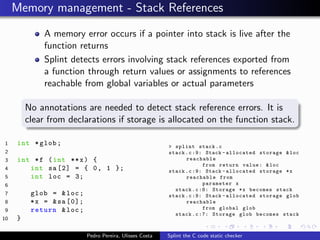

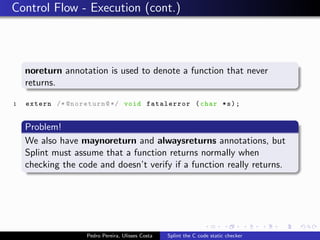
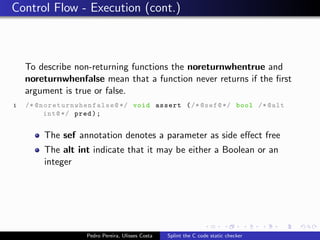
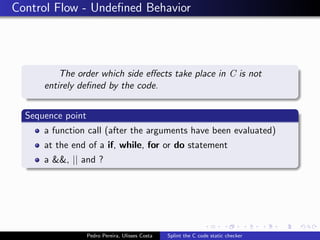
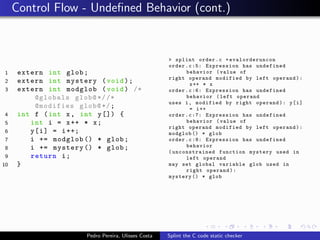
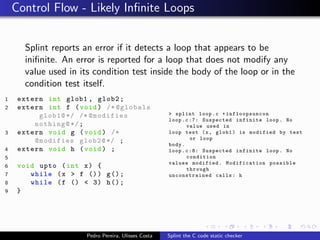
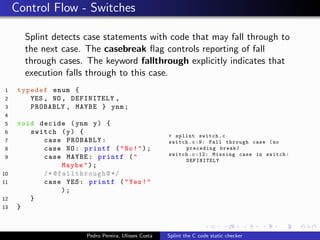



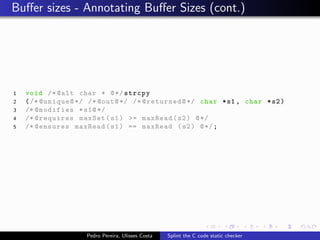
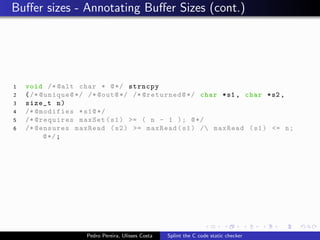
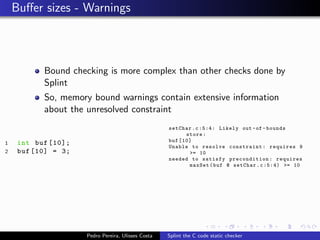
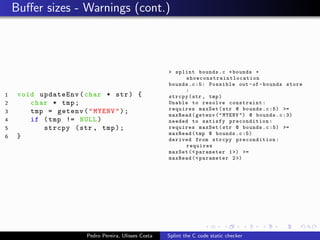




This document summarizes Splint, a static analysis tool for C code. It detects various errors such as unused variables, type inconsistencies, memory management issues, and control flow anomalies. It works by type checking code, tracking variable usage and definitions, and modeling memory allocation. Splint supports custom annotations to specify variable properties. The document describes Splint's checks for unused variables, types, memory management including allocation/deallocation errors and stack references, control flow including execution paths and loops, and switch statements. It also provides examples of errors detected by Splint.










































