Embed presentation
Download as PDF, PPTX


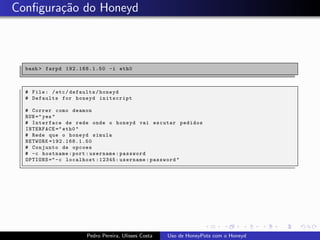
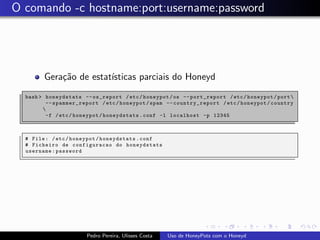
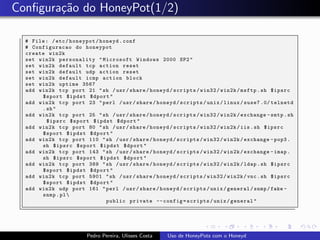
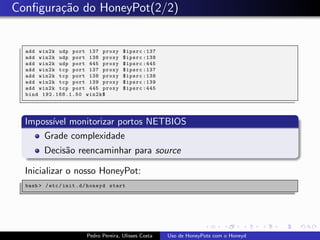
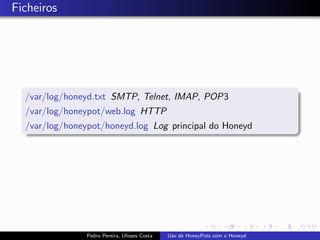
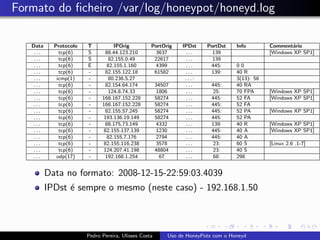

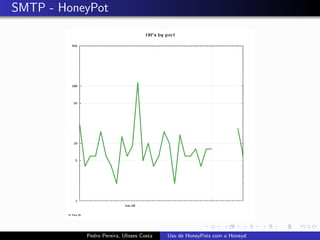

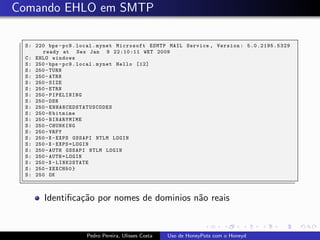
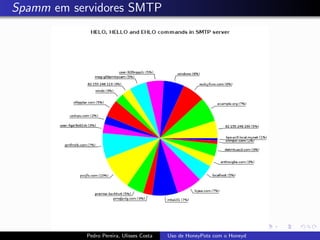

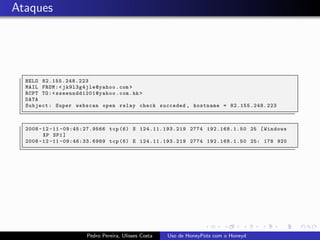
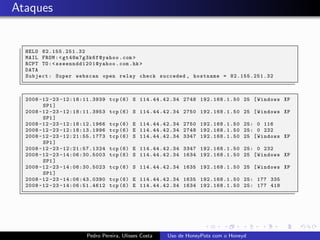
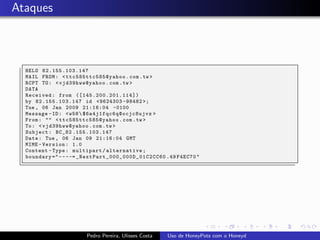

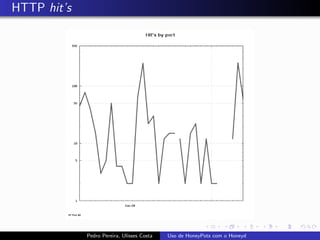

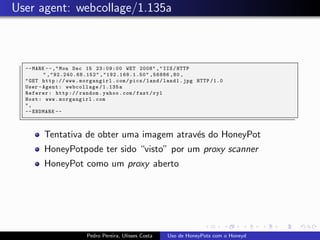
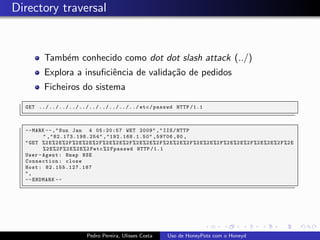
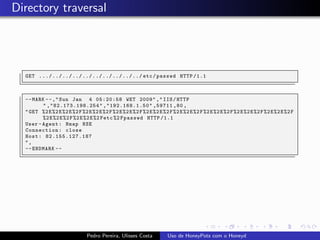
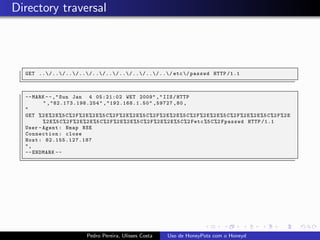
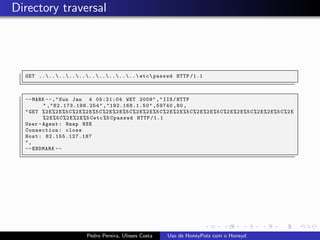
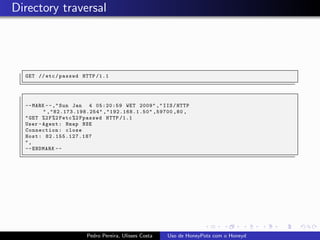

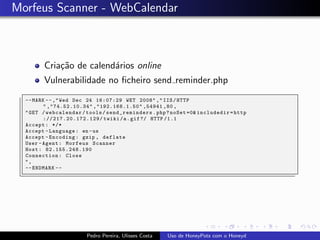
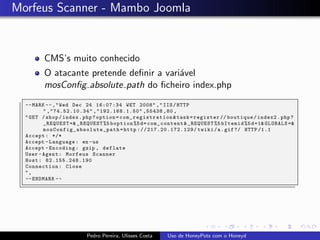
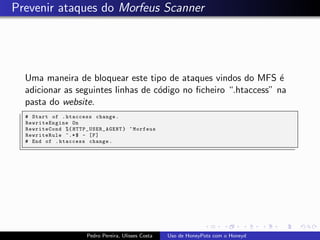
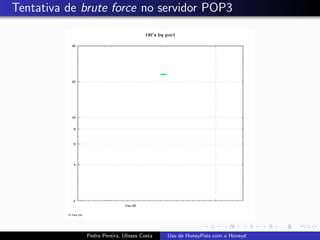
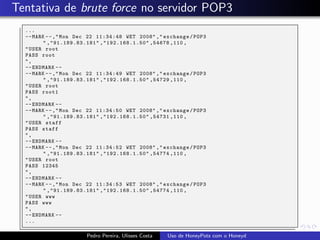

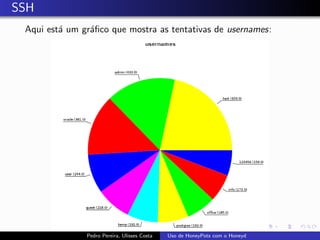
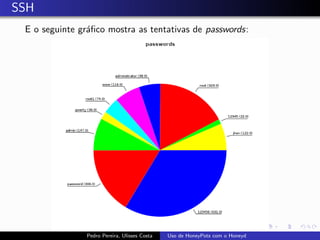

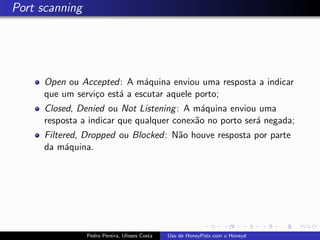
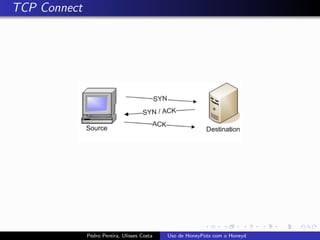


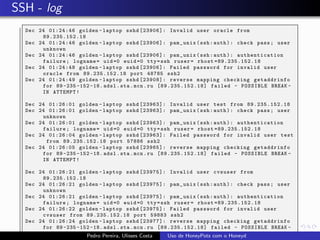



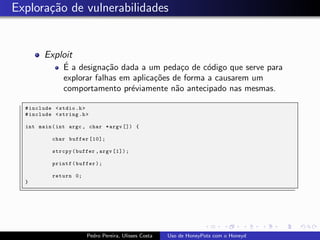
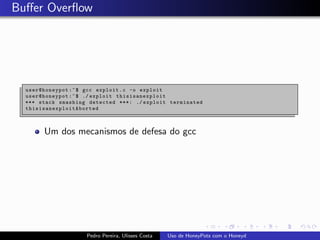


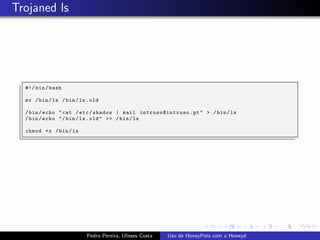

The document discusses using HoneyPots with Honeyd to detect attacks. It describes how Honeyd can create virtual hosts and configure them with various personalities and services. Logs of activity on services like SMTP, HTTP, and SSH can be examined to identify attacks. Configuring a HoneyPot with Honeyd involves creating host profiles, adding services and scripts to emulate operating systems and applications. This allows monitoring of attacks while adding security.





































































