FOLCA is a fully-online grammar compression method that builds a partial parse tree in an online manner and directly encodes it into a succinct representation using just nlgn+2n+o(n) bits of space. This is asymptotically optimal. It achieves small working space of (1+α)nlgn+n(3+lg(αn)) bits using a compressed hash table. It can extract substrings in O(l+h) time using extra space of nlg(N/n)+3n+o(n) bits. Experiments show it compresses and extracts faster than LZend while using less space.



![Grammar Compression (GC)
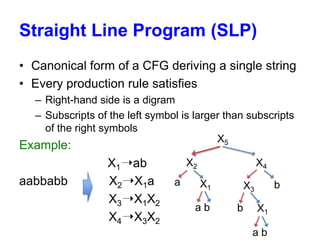
• Build a small CFG from an input string
– Size n = number of production rules
• Two crucial data structures
1. Dictionary : Given Xk, returns XiXj for Xk ➝ XiXj
- Array : 2nlgn bits
2. Reverse dictionary: Given XiXj, return Xk
- Hash table : O(nlgn) bits
X1➝ab
X2➝X1a
X3➝X1X2
X4➝X3X2
Access : Xk ➝ A[2k-1][2k]](https://image.slidesharecdn.com/spire2013tabei-131021203254-phpapp02/85/SPIRE2013-tabei20131009-5-320.jpg)
![Existing grammar compression
• Compression time and working space are
important for scalability
• Online LCA (OLCA) [CCP,2011] = efficient GC
Compression
Method
time
CCP,2011 O(N/α)
SPIRE,2012 O(N/α)
CPM,2013 O(Nlgn)
Working space (bits)
(3+α)nlgn
(11/4+α nlgn
2nlgn(1+o(1))+2nlgp (p << √n)
• Drawbacks : they need a large working space
• Challenge : developing fast GC of smaller
working space](https://image.slidesharecdn.com/spire2013tabei-131021203254-phpapp02/85/SPIRE2013-tabei20131009-6-320.jpg)
![Fully-Online LCA (FOLCA)
Direct encoding of an SLP
SLP (Parse Tree)
Text
abaababa
Partial Parse Tree
Succinct
Representation
12345678910
B:0010101011
L:abaX1X2
P:123469
• Smaller working space : (1+α)nlgn+n(3+lg(αn))
bits
• Optimal encoding: lgn+2n+o(n) bits
– Almost equal to the lower bound [CPM,2013]](https://image.slidesharecdn.com/spire2013tabei-131021203254-phpapp02/85/SPIRE2013-tabei20131009-7-320.jpg)






![Succinct encoding of POPPT
• FOLCA builds POPPT in an online manner, it
encodes the POPPT into dynamic RMM tree
[Sadakane and Navarro,2009]
– ‘0’ for a leaf and ‘1’ for an internal node
– L : a label sequence for leaves
POPPT
Succinct tree
B : 0010101011
L : abaX1X2
nlgn + 2n + o(n) bits
• Simulate tree operations using rank/select
dictionary : random access to Xk ➝ XiXj](https://image.slidesharecdn.com/spire2013tabei-131021203254-phpapp02/85/SPIRE2013-tabei20131009-16-320.jpg)

![Substring extraction
• Keep the starting position of the substring
encoded by each variable Xi in position array P
– Naïve representation : nlgN bits
• Observation : position array is a monotonically
increasing sequence [Grossi et al., 2003]
• nlg(N/n)+3n+o(n) bits
• Extraction time of a substring
of length l is O(l+h)
P
Increasing](https://image.slidesharecdn.com/spire2013tabei-131021203254-phpapp02/85/SPIRE2013-tabei20131009-18-320.jpg)
![Experiments
• Ecoli (108MB) and kernel texts (247MB) from
repetitive collections in pizza & chili corpus
• Evaluate compression time, working space and
substring extraction time
• Compare FOLCA with LZend [Kreft and
Navarro’10]
• Applicability to 100 human genomes (300GB)](https://image.slidesharecdn.com/spire2013tabei-131021203254-phpapp02/85/SPIRE2013-tabei20131009-19-320.jpg)


![Substring extraction time and
working space for the kernel text
Time [sec]
Length
101
102
103
104
105
FOLCA
LZend
0.00007
0.00026
0.00224
0.02176
0.21328
0.00002
0.00011
0.00100
0.00954
0.09215
Working space [MB]
FOLCA
12
LZend
14](https://image.slidesharecdn.com/spire2013tabei-131021203254-phpapp02/85/SPIRE2013-tabei20131009-22-320.jpg)


![Summary of FOLCA
• Directly encode an SLP into a succinct
representation of nlgn+2n+o(o) bits
• Asymptotically equivalent to the information
theoretic lower bound [CPM,2013]
• Compressed hash table for small working space
of (1+α)nlgn+n(3+lg(αn)) bits
• Support substring extraction in O(l+h) time using
additional space of nlg(N/n)+3n+o(n) bits](https://image.slidesharecdn.com/spire2013tabei-131021203254-phpapp02/85/SPIRE2013-tabei20131009-25-320.jpg)