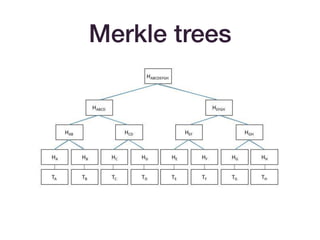
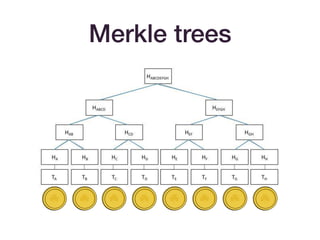
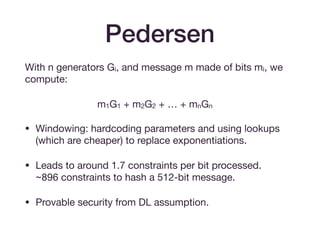
The document discusses advancements in hash functions specifically for SNARKs (Succinct Non-interactive Arguments of Knowledge), highlighting their importance in cryptographic protocols. It covers various hash functions and methods for achieving efficiency and security, including SHA2, Merkle trees, Pedersen hashes, and specific elliptic curve hashing techniques. The document emphasizes the need for low arithmetic complexity while maintaining security properties, providing a roadmap for selecting suitable hash functions in SNARK applications.


![RO hashing to bitstrings
• To replace SHA with its full functionality, various hash
functions (or pairs of hash functions) have been recently
suggested:
• MPC-inspired low-complexity hash functions:
• [AGRRT16] : MIMChash
• [GRRSS16], [AGP+19] : symmetric key
primitives for low arithmetic circuit complexity](https://image.slidesharecdn.com/zksummit-hashfunctions-191108031619/85/snarks-3-hash-functions-11-320.jpg)
![RO hashing to bitstrings
• To replace SHA with its full functionality, various hash
functions (or pairs of hash functions) have been recently
suggested:
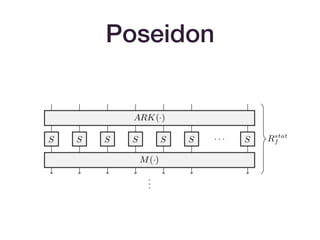
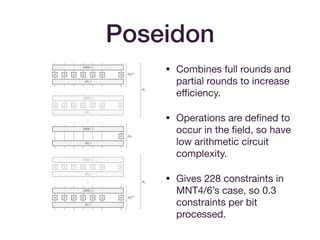
• HADESMIMC-inspired hash functions:
• [AABDS19] : Vision/Rescue
• [GKK+19] : STARKAD/POSEIDON](https://image.slidesharecdn.com/zksummit-hashfunctions-191108031619/85/snarks-3-hash-functions-12-320.jpg)





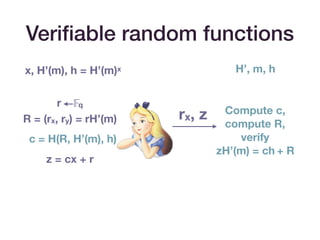
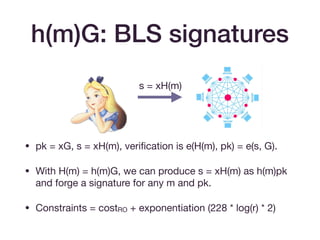
![Snarks with private input
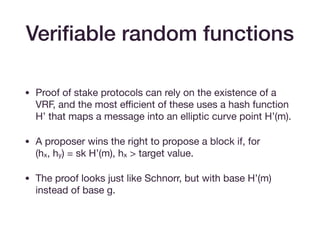
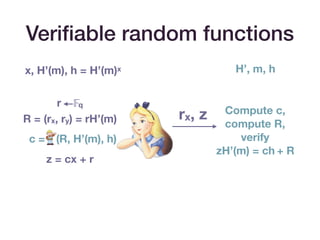
• Simulation extractability
• Ensures that if you can produce a valid transaction, then a
valid witness can be extracted.
• [BG18] transforms Groth16 into a simulation extractable
SNARK.
• It achieves this by including a message hashed to an
elliptic curve point alongside the proof.](https://image.slidesharecdn.com/zksummit-hashfunctions-191108031619/85/snarks-3-hash-functions-23-320.jpg)

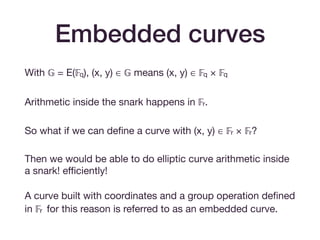
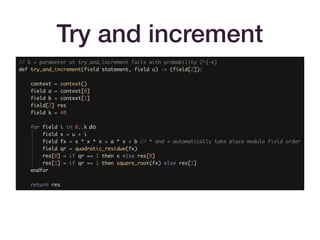
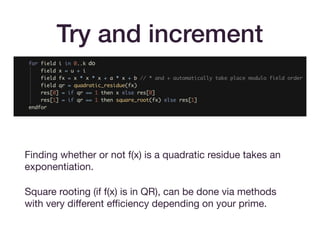
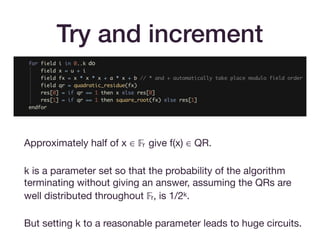
![Icart-style encodings
• These maps look like H = f(h(u)).
• The basic map of [Icart09] achieves one-wayness (if h is
one-way).
• The extension in [BCI+10] to f(h(m)) + gh(m) achieves
indistinguishability from a random oracle, assuming that
h(m) achieves this. (Think of gh(m) as a one-time pad.)](https://image.slidesharecdn.com/zksummit-hashfunctions-191108031619/85/snarks-3-hash-functions-30-320.jpg)
![Icart-style encodings
• These maps look like H = f(h(u)).
• The basic map of [Icart09] achieves one-wayness (if h is
one-way).
• The extension in [BCI+10] to f(h(m)) + gh(m) achieves
indistinguishability from a random oracle, assuming that
h(m) achieves this. (Think of gh(m) as a one-time pad.)](https://image.slidesharecdn.com/zksummit-hashfunctions-191108031619/85/snarks-3-hash-functions-31-320.jpg)
![Icart-style encodings
• The basic function of [Icart09] achieves one-wayness (if h
is one-way).
• The extension in [BCI+10] to f(h0(u)) + f(h1(u)) achieves
indifferentiability from a random oracle, assuming that
h0(u) and h1(u) achieve this. (Think of f(h1(u)) as a one-time
pad.)
• Assumes p = 2 mod 3.](https://image.slidesharecdn.com/zksummit-hashfunctions-191108031619/85/snarks-3-hash-functions-32-320.jpg)
![Icart-style encodings
• The basic function of [Icart09] achieves one-wayness (if h
is one-way).
• The extension in [BCI+10] to f(h0(u)) + f(h1(u)) achieves
indifferentiability from a random oracle, assuming that
h0(u) and h1(u) achieve this. (Think of f(h1(u)) as a one-time
pad.)
• Assumes p = 2 mod 3.](https://image.slidesharecdn.com/zksummit-hashfunctions-191108031619/85/snarks-3-hash-functions-33-320.jpg)
![Icart-style encodings
• The basic function of [Icart09] achieves one-wayness (if h
is one-way).
• The extension in [BCI+10] to f(h0(u)) + f(h1(u)) achieves
indifferentiability from a random oracle, assuming that
h0(u) and h1(u) achieve this. (Think of f(h1(u)) as a one-time
pad.)
• Assumes r = 2 mod 3.](https://image.slidesharecdn.com/zksummit-hashfunctions-191108031619/85/snarks-3-hash-functions-34-320.jpg)

![Skałba/SWU-style encodings
From [BCIMRT10]](https://image.slidesharecdn.com/zksummit-hashfunctions-191108031619/85/snarks-3-hash-functions-36-320.jpg)
![• [BCI+10] extends and simplifies the SWU encoding,
moving it from just achieving one-wayness to also
achieving indifferentiability from a random oracle, but only
with r = 3 mod 4.
• [WB19] then removes this restriction and generalises,
proposing a construction for ab != 0, and one that works
even in this case.
Skałba/SWU-style encodings](https://image.slidesharecdn.com/zksummit-hashfunctions-191108031619/85/snarks-3-hash-functions-37-320.jpg)





![RO hashes
[AGRRT16] : M. Albrecht, L. Grassi, C. Rechberger, A. Roy, and T. Tiessen. MiMC:
Efficient encryption and cryptographic hashing with minimal multiplicative complexity.
https://eprint.iacr.org/2016/492
[GRRSS16] : L. Grassi, C. Rechberger, D. Rotaru, P. Scholl, and N. P. Smart. MPC-
Friendly Symmetric Key Primitives. https://eprint.iacr.org/2016/542
[AGP+19] : M. R. Albrecht, L. Grassi, L. Perrin, S. Ramacher, C. Rechberger, D. Rotaru,
A. Roy, and M. Schofnegger. Feistel Structures for MPC, and More. https://
eprint.iacr.org/2019/397
[AABDS19] : A. Aly, T. Ashur, E. Ben-Sasson, S. Dhooghe, and A. Szepieniec. Design
of Symmetric-Key Primitives for Advanced Cryptographic Protocols. https://
eprint.iacr.org/2019/426
[GKK+19] : L. Grassi, D. Kales, D. Khovratovich, A.Roy, C. Rechberger, and M.
Schofnegger. Starkad and Poseidon: New Hash Functions for Zero Knowledge Proof
Systems. https://eprint.iacr.org/2019/458](https://image.slidesharecdn.com/zksummit-hashfunctions-191108031619/85/snarks-3-hash-functions-43-320.jpg)
![RO hashes to elliptic curves
[SvdW06] A. Shallue and C. van de Woestijne. Construction of rational points on
elliptic curves over finite fields.
[Ulas07] M. Ulas. Rational points on certain hyperelliptic curves over finite fields.
https://arxiv.org/pdf/0706.1448.pdf
[Icart09] T. Icart. How to Hash into Elliptic Curves. https://eprint.iacr.org/2009/226
[BCI+10] E. Brier, J. Coron, T. Icart, D. Madore, H. Randriam, and M. Tibouchi.
Efficient Indifferentiable Hashing into Ordinary Elliptic Curves. https://eprint.iacr.org/
2009/340
[BHKL13] D. J. Bernstein, M. Hamburg, A. Krasnova, and T. Lange. Elligator. https://
elligator.cr.yp.to
[WB19] R. S. Wahby and D. Boneh. Fast and simple constant-time hashing to the
BLS12-381 elliptic curve. https://eprint.iacr.org/2019/403](https://image.slidesharecdn.com/zksummit-hashfunctions-191108031619/85/snarks-3-hash-functions-44-320.jpg)