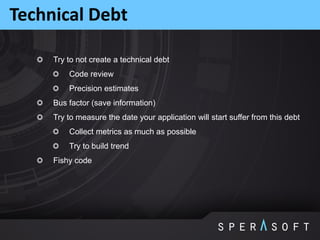
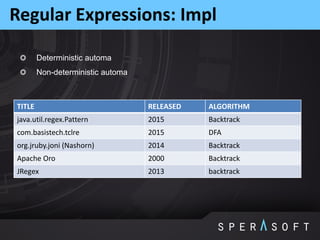
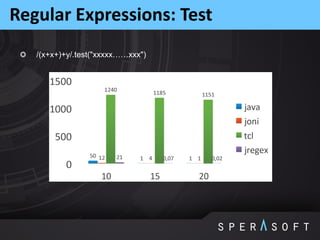
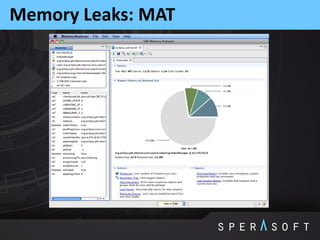
This document provides an overview and agenda for the JPoint 2015 conference. It includes summaries of sessions on memory leaks profiling basics, notes about the Java String class, defining and measuring technical debt, how regular expressions work under the hood, and using memory dumps and analysis tools to find memory leaks. The agenda outlines sessions on memory regions, garbage collection, identifying memory leaks through examples, JVM options for logs and dumps, String class internals, technical debt concepts, and regular expression matching algorithms.










![Immutable
25% of objects are java.lang.String
String concat vs StringBuilder (3250 op/sec vs 125000 op/sec)
-XX:±OptimizeStringConcat
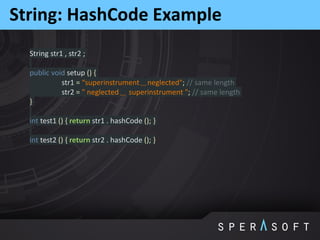
String
OFFSET SIZE TYPE DESCRIPTION
0 12 object header
12 4 char[] value
16 4 int hash
20 4 alligmeent loss](https://image.slidesharecdn.com/sperasofttalksjpoint2015-150904142212-lva1-app6892/85/Sperasoft-talks-j-point-2015-12-320.jpg)

![String: Regexp
String text = “Funny␣girl␣danced␣fell␣hurt␣and␣cried␣aloud.";
String textDup = text.replaceAll ("␣", "␣␣");
Pattern pattern = Pattern.compile ("␣␣");
String [] charSplit () { return text.split ("␣"); } //191.6 ns/op
String [] strSplit () { return textDup.split ("␣␣"); } //527.9 ns/op
String [] strSplit_pattern () { return pattern.split(textDup); } //416.2 ns/op
charSplit: fast path for 1 byte symbols
strSplit: internally creates Pattern
strSplit_pattern: reuse Pattern](https://image.slidesharecdn.com/sperasofttalksjpoint2015-150904142212-lva1-app6892/85/Sperasoft-talks-j-point-2015-16-320.jpg)