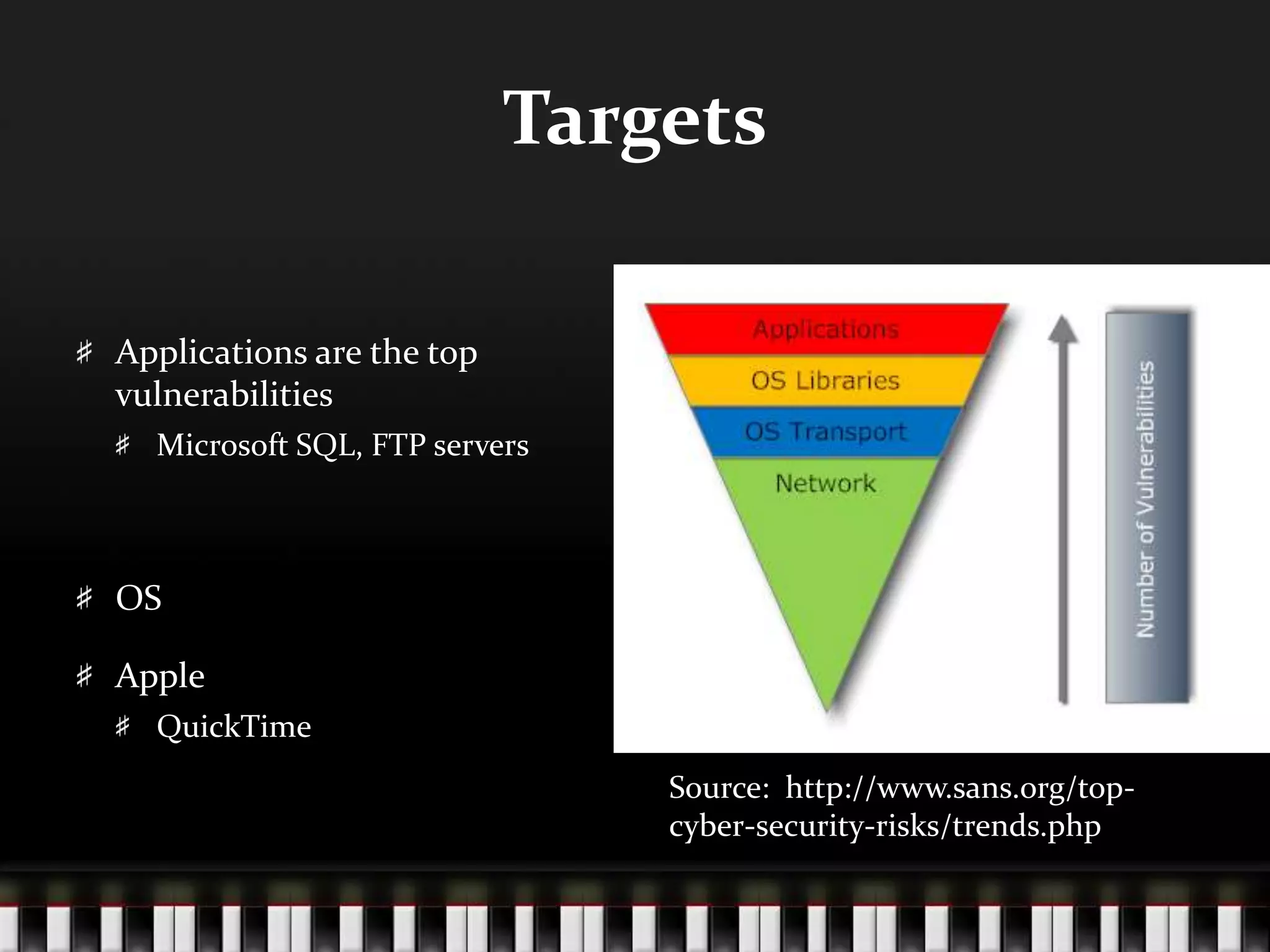
This document discusses how technology can both increase individual capabilities and vulnerabilities. It explores how the internet has evolved from military use in the 1960s to widespread personal use today. It also examines ethics issues around internet content restrictions, censorship, and the responsibilities of different types of internet providers. Solutions to vulnerabilities are suggested, such as software updates and password protection. Overall the document provides a broad overview of social implications, capabilities, vulnerabilities and ethical issues related to increasing technology and internet use.