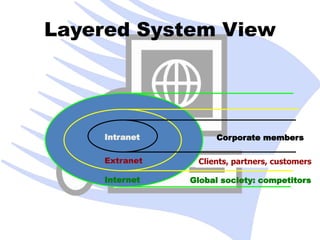
Computer networks allow devices to exchange data by passing packets of information between nodes through connections. The earliest computer networks were developed in the 1960s to allow computers to share resources more efficiently. The best known computer network today is the Internet, which originated from ARPANET and has evolved from connecting universities to becoming a global network relying on TCP/IP protocols.