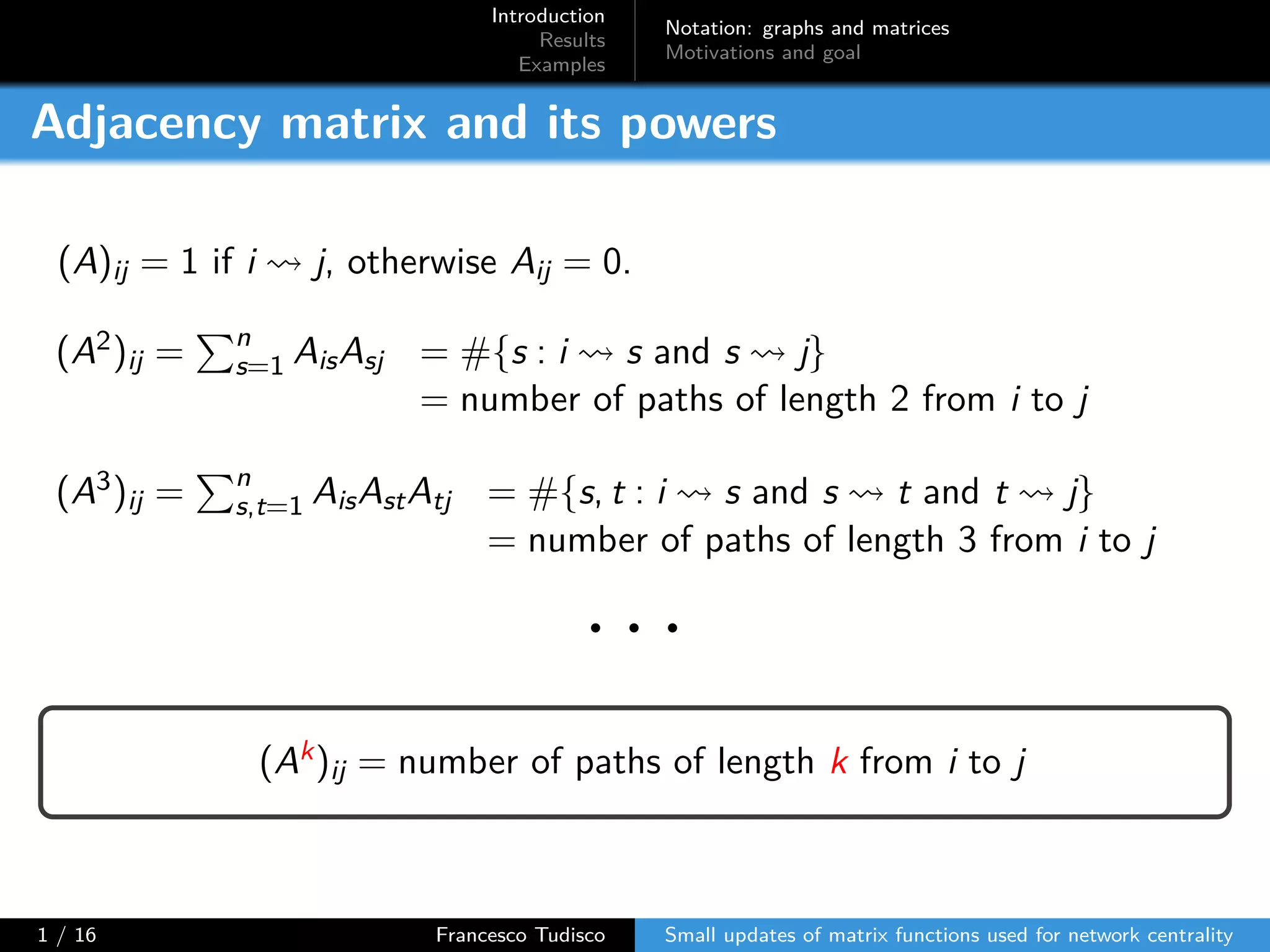
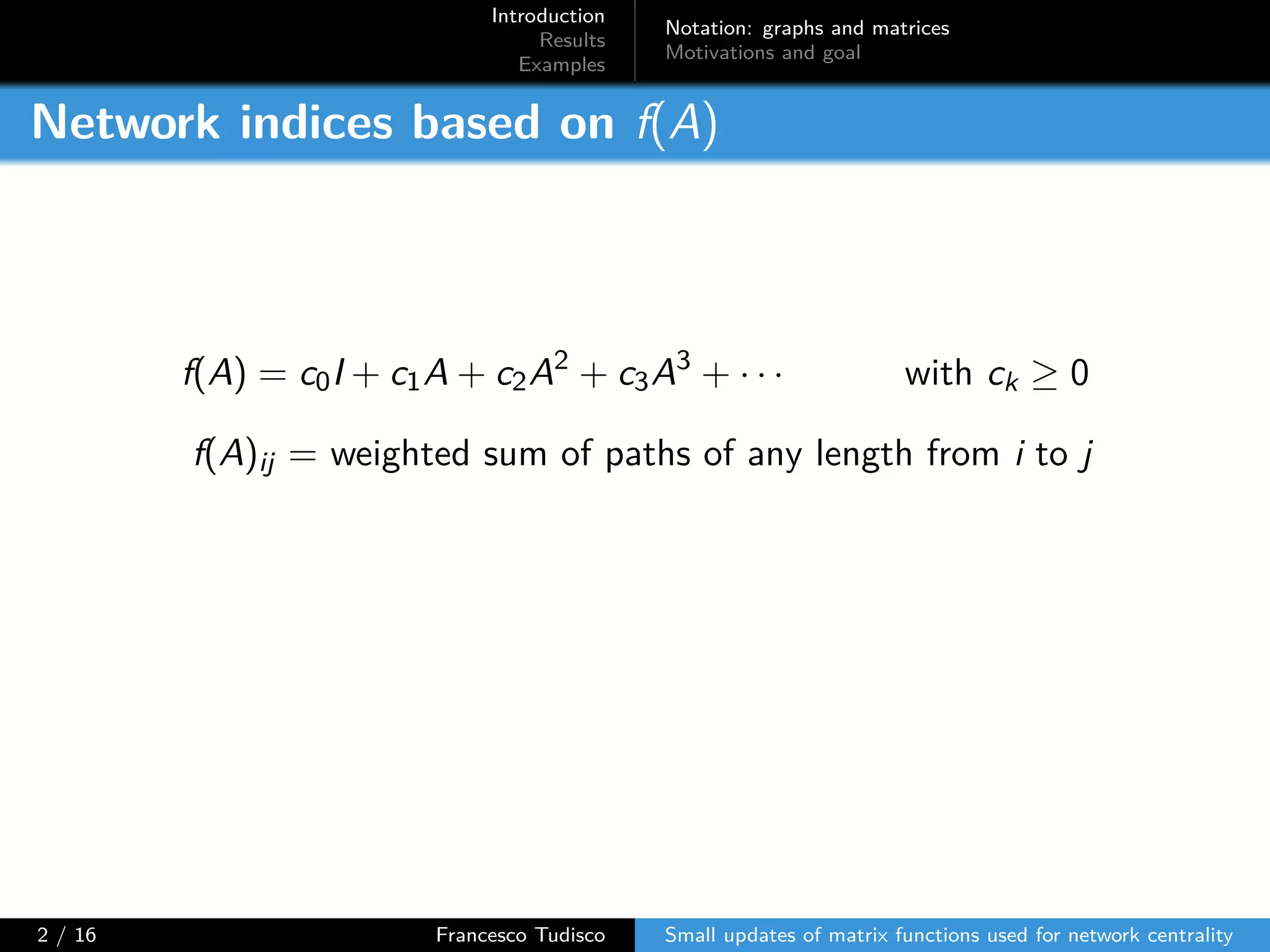
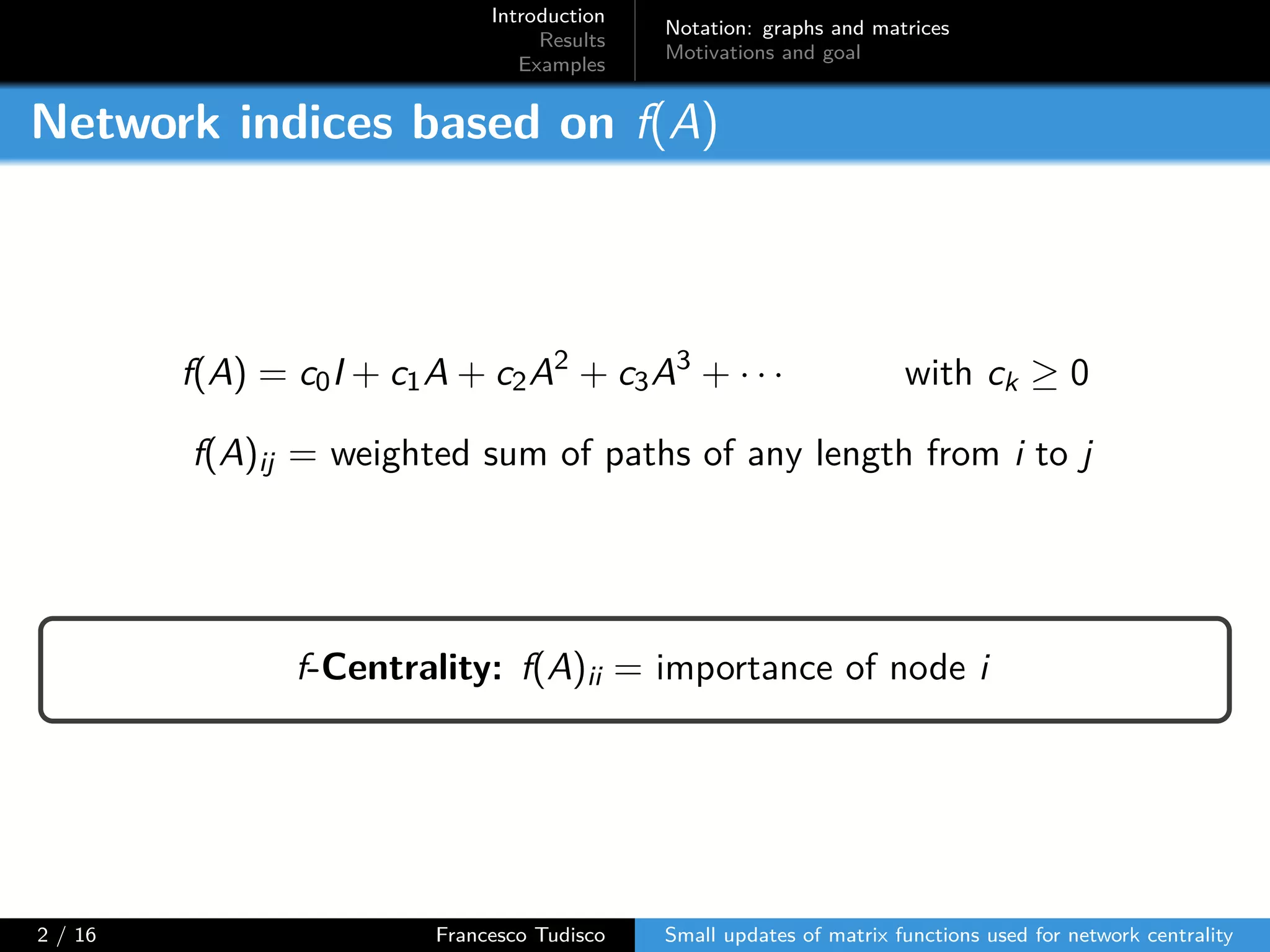
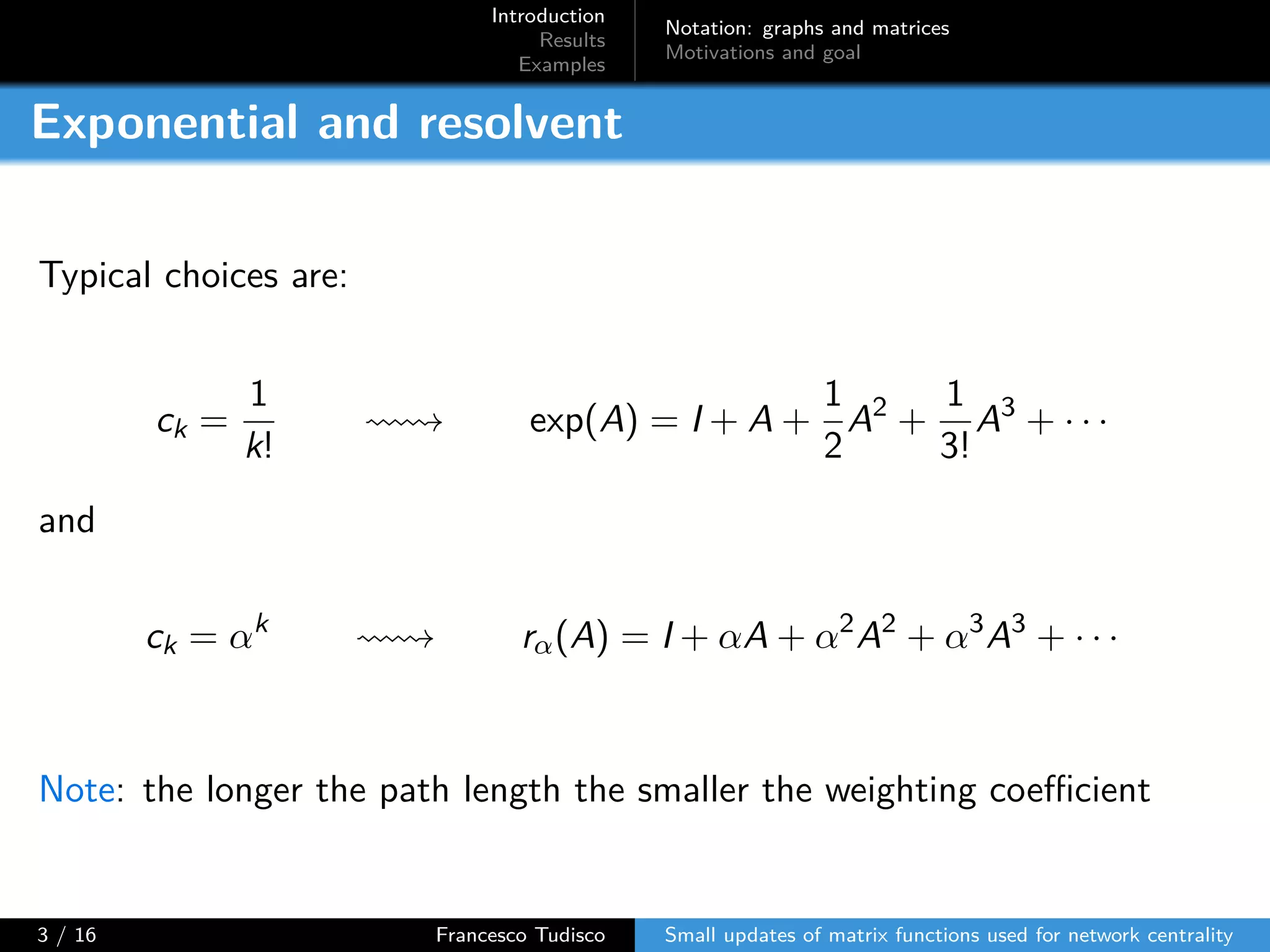
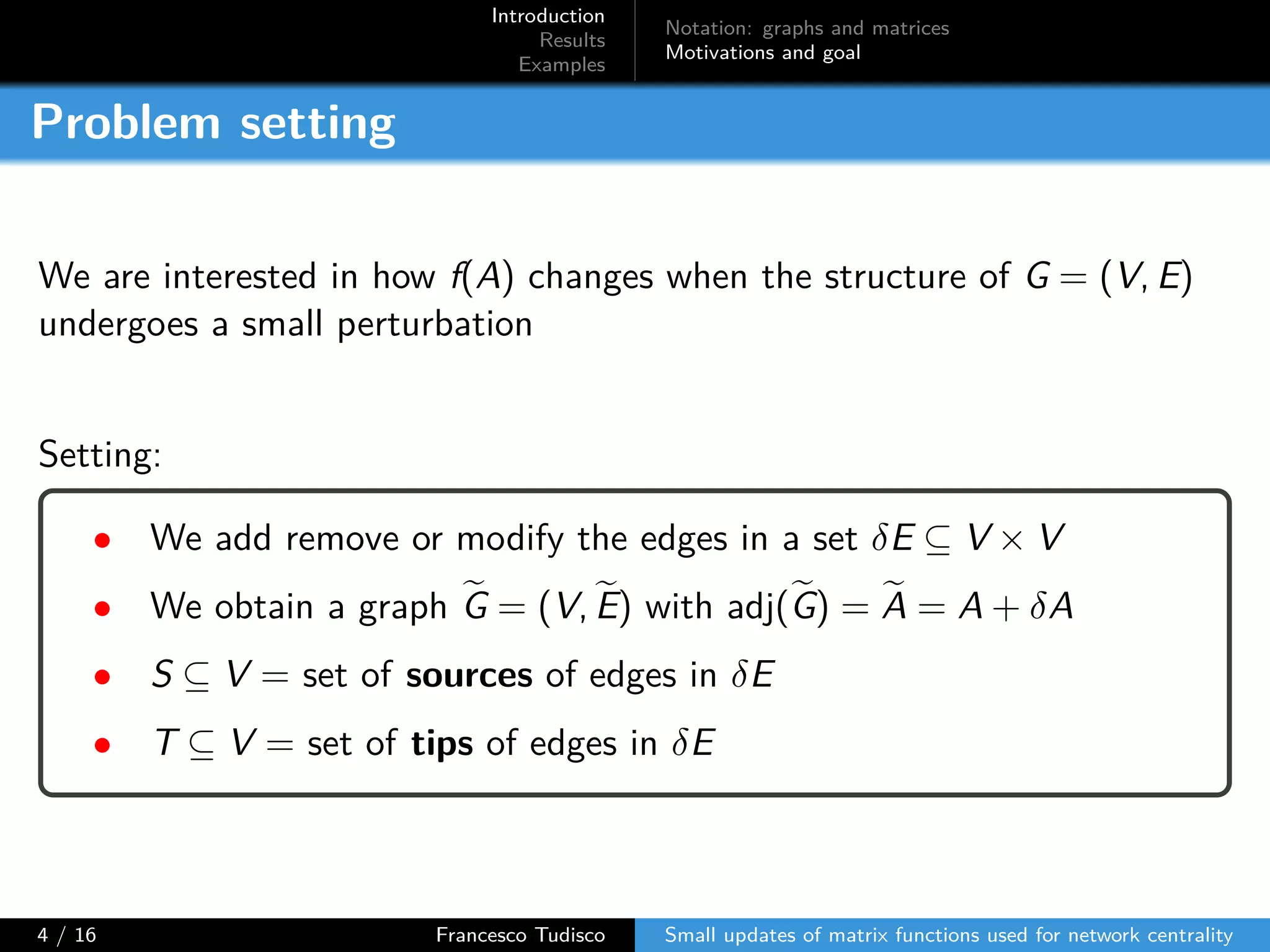
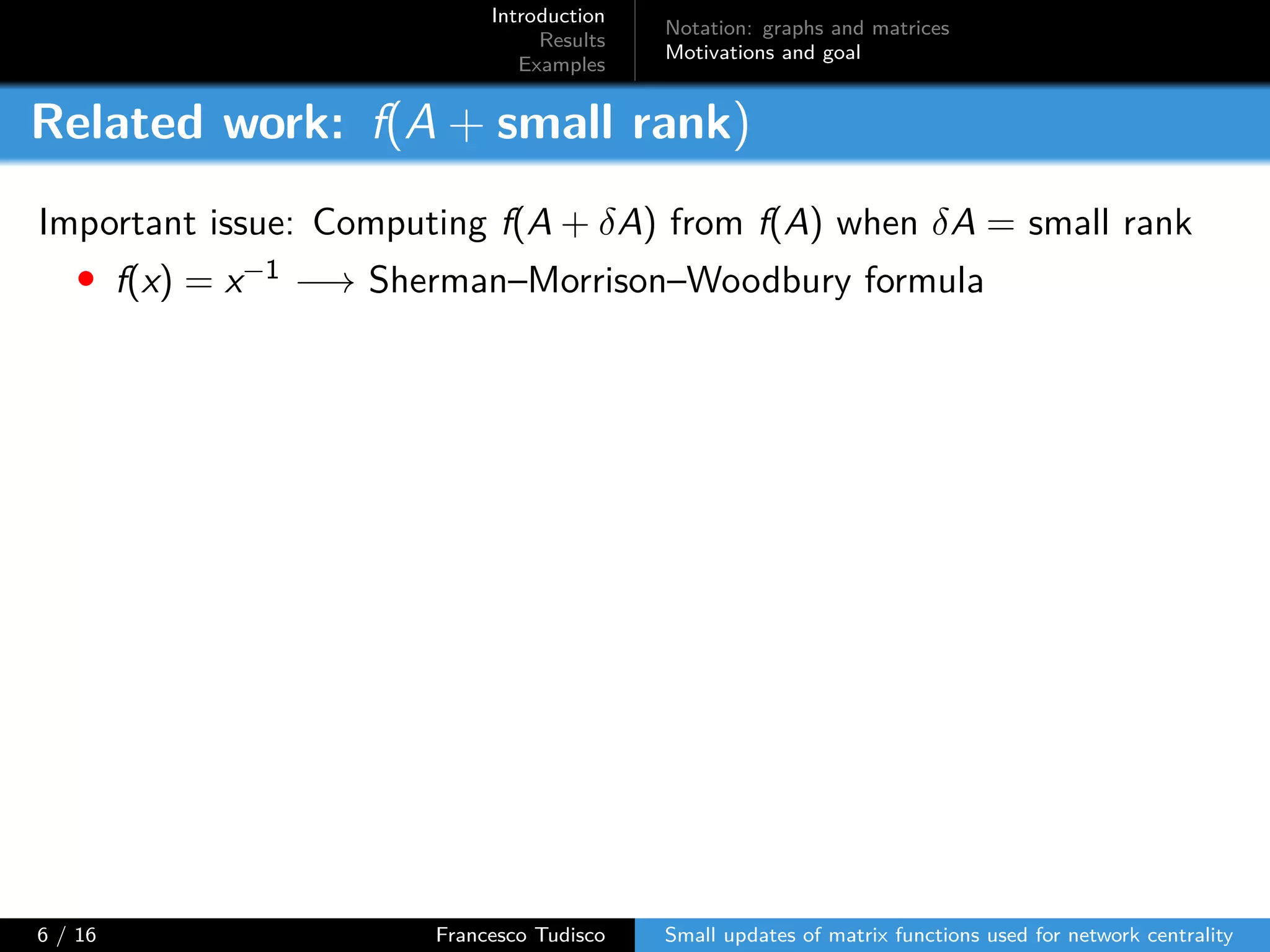
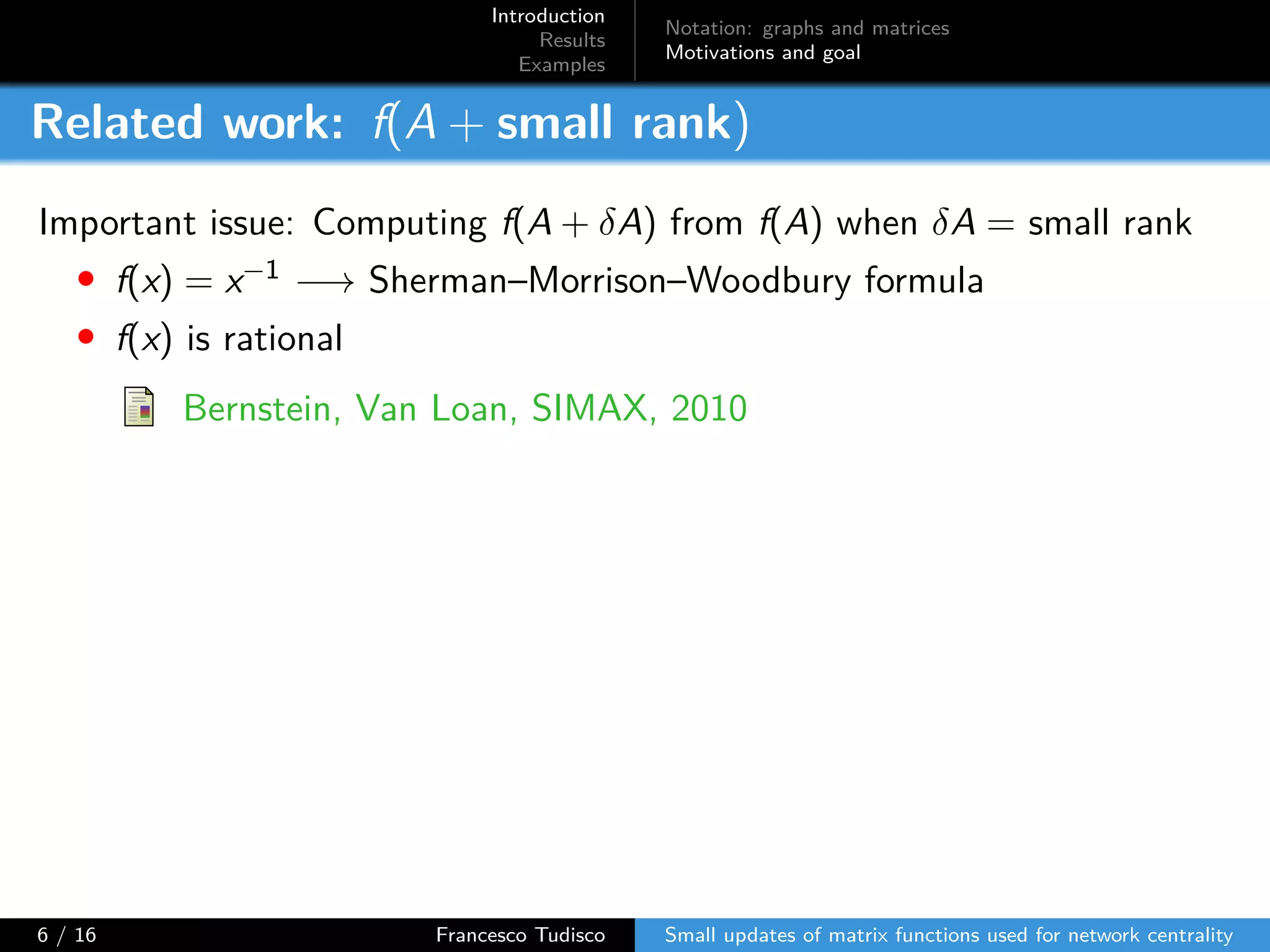
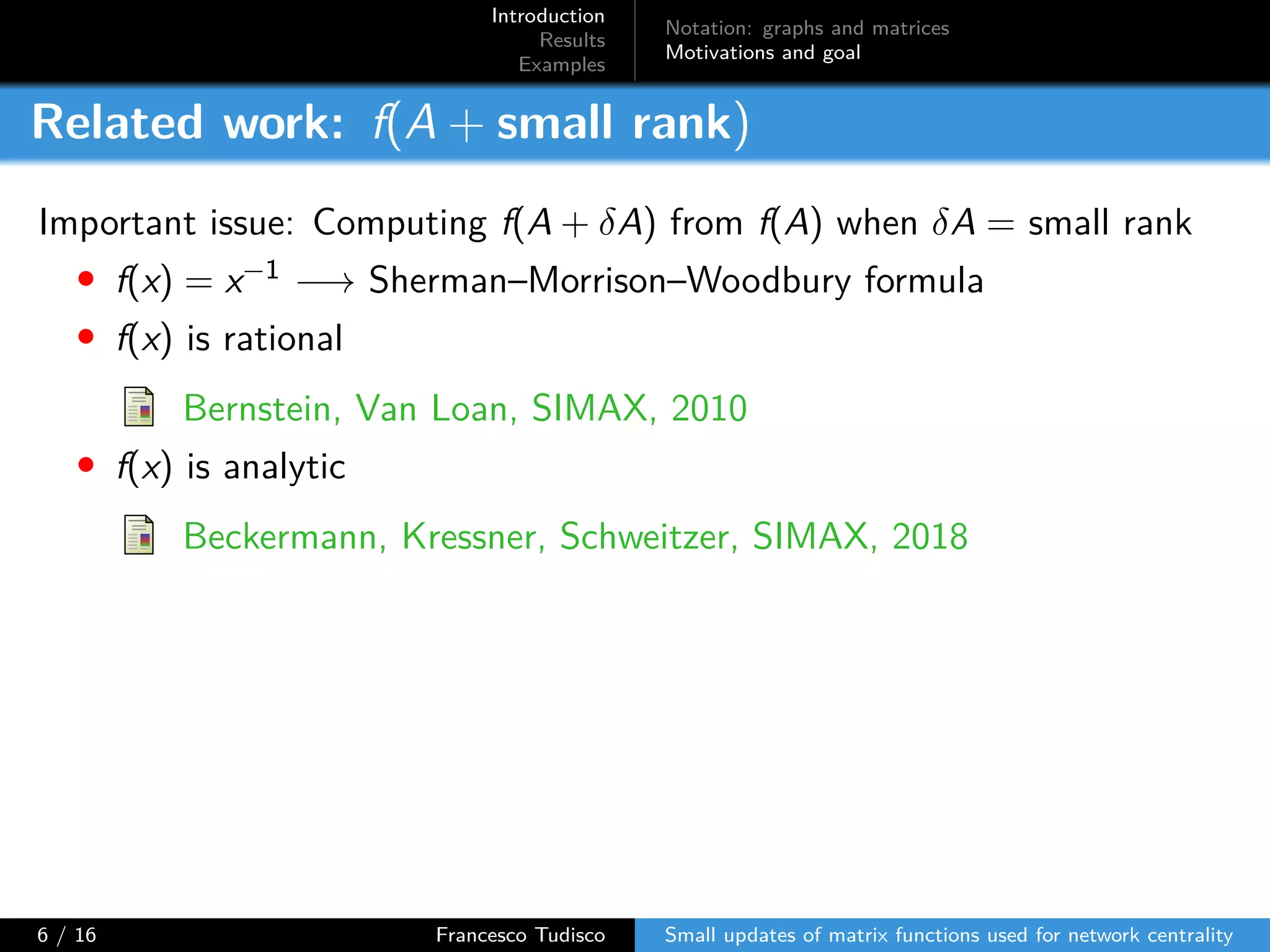
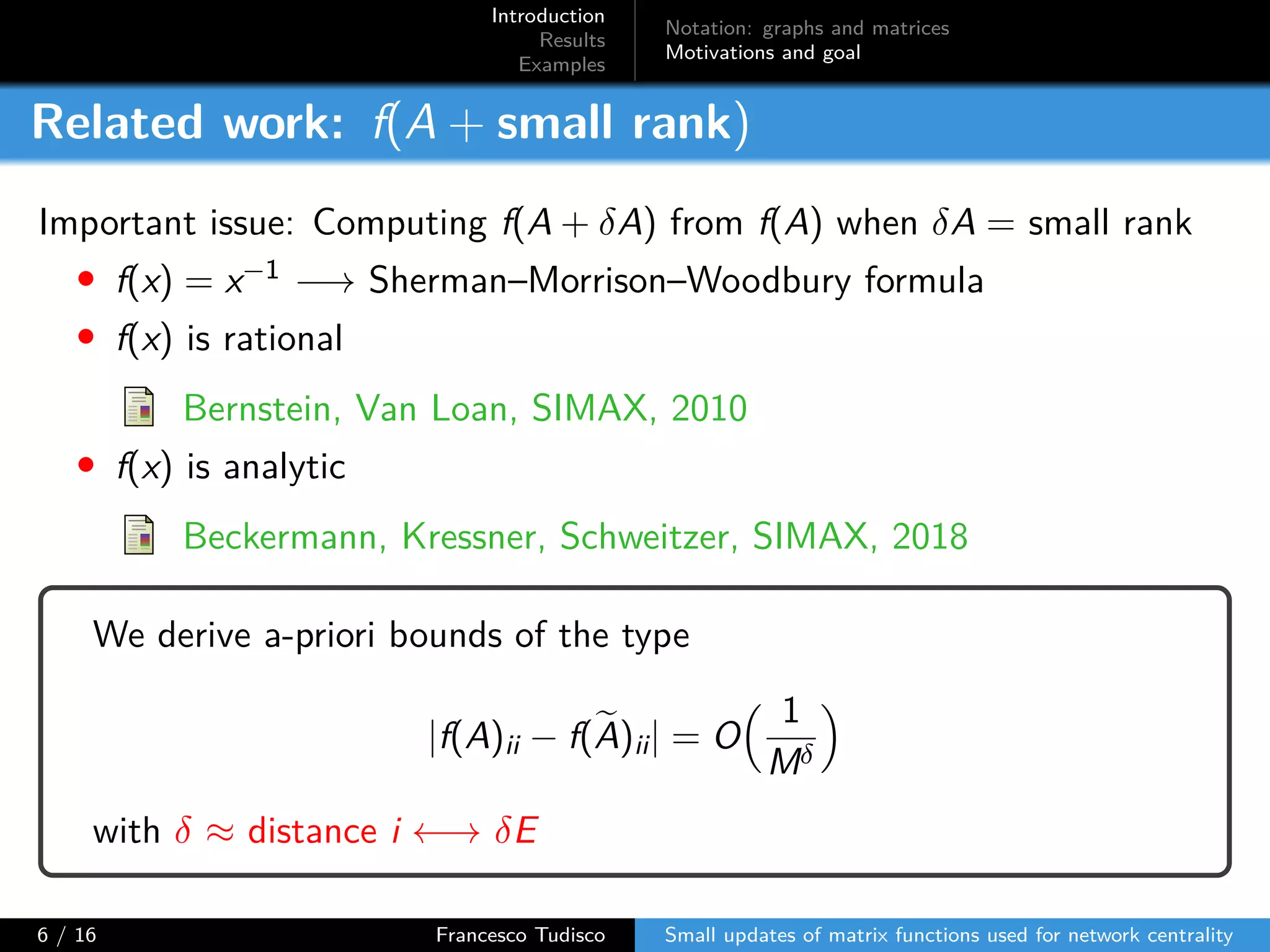
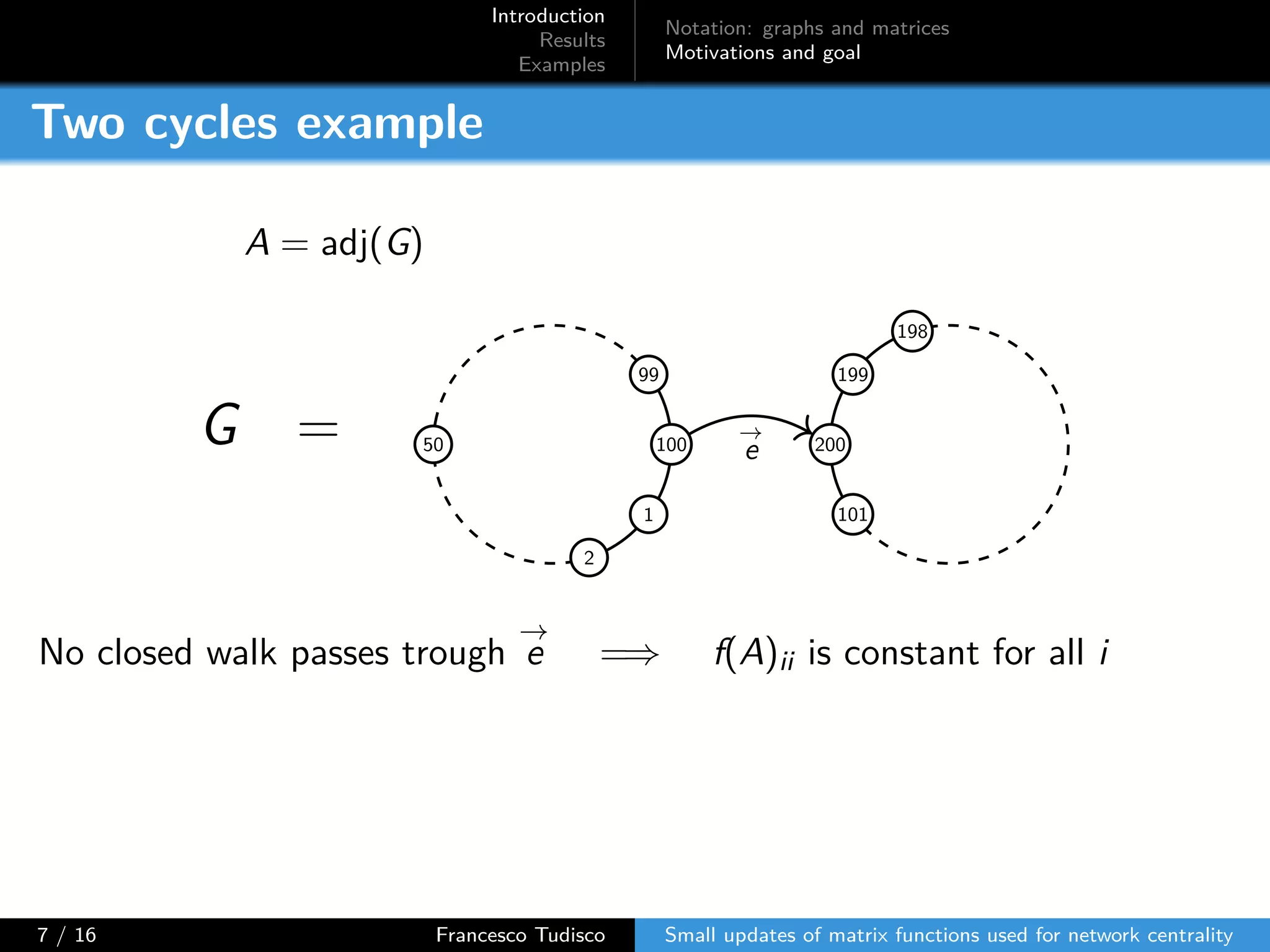
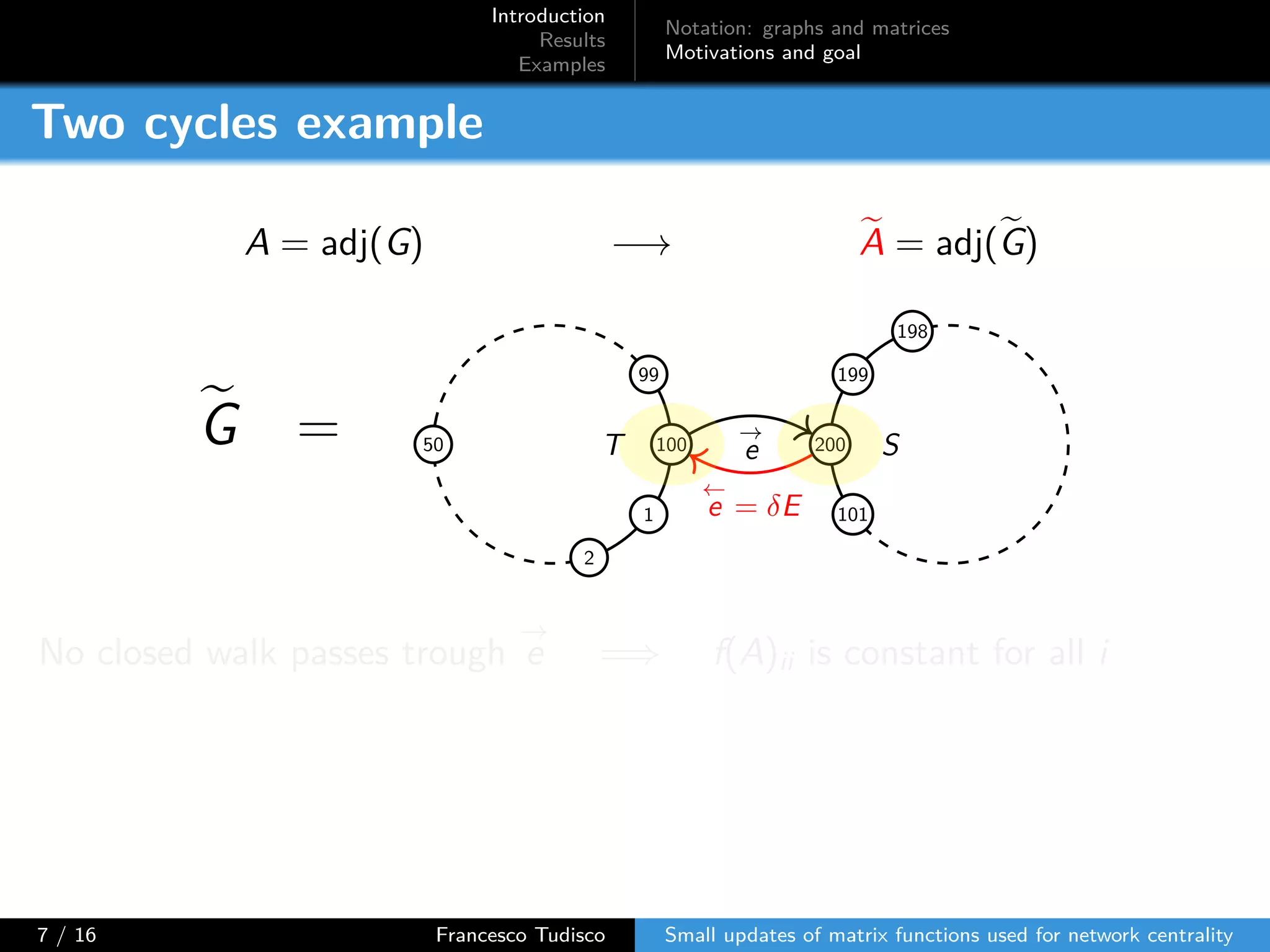
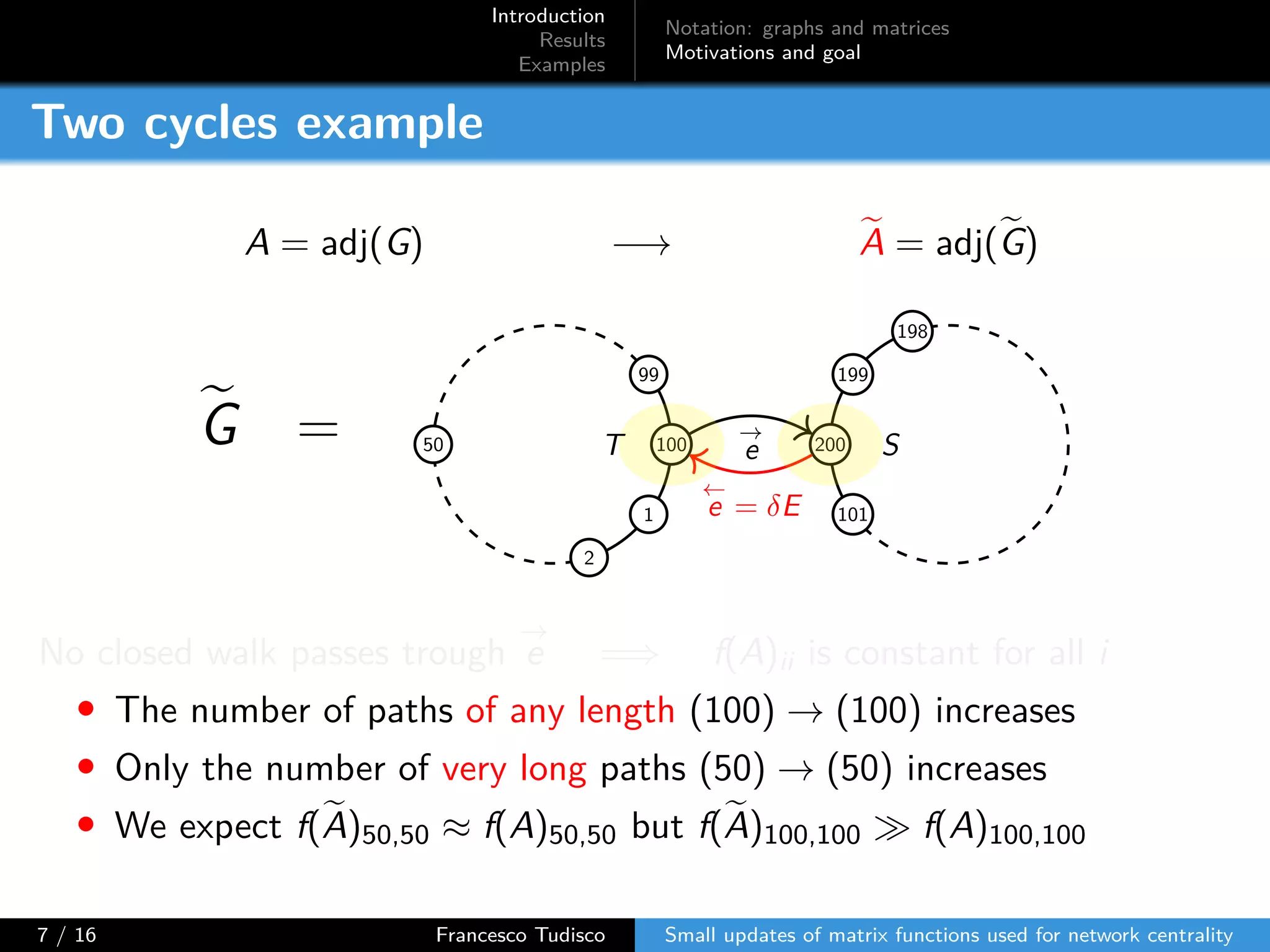
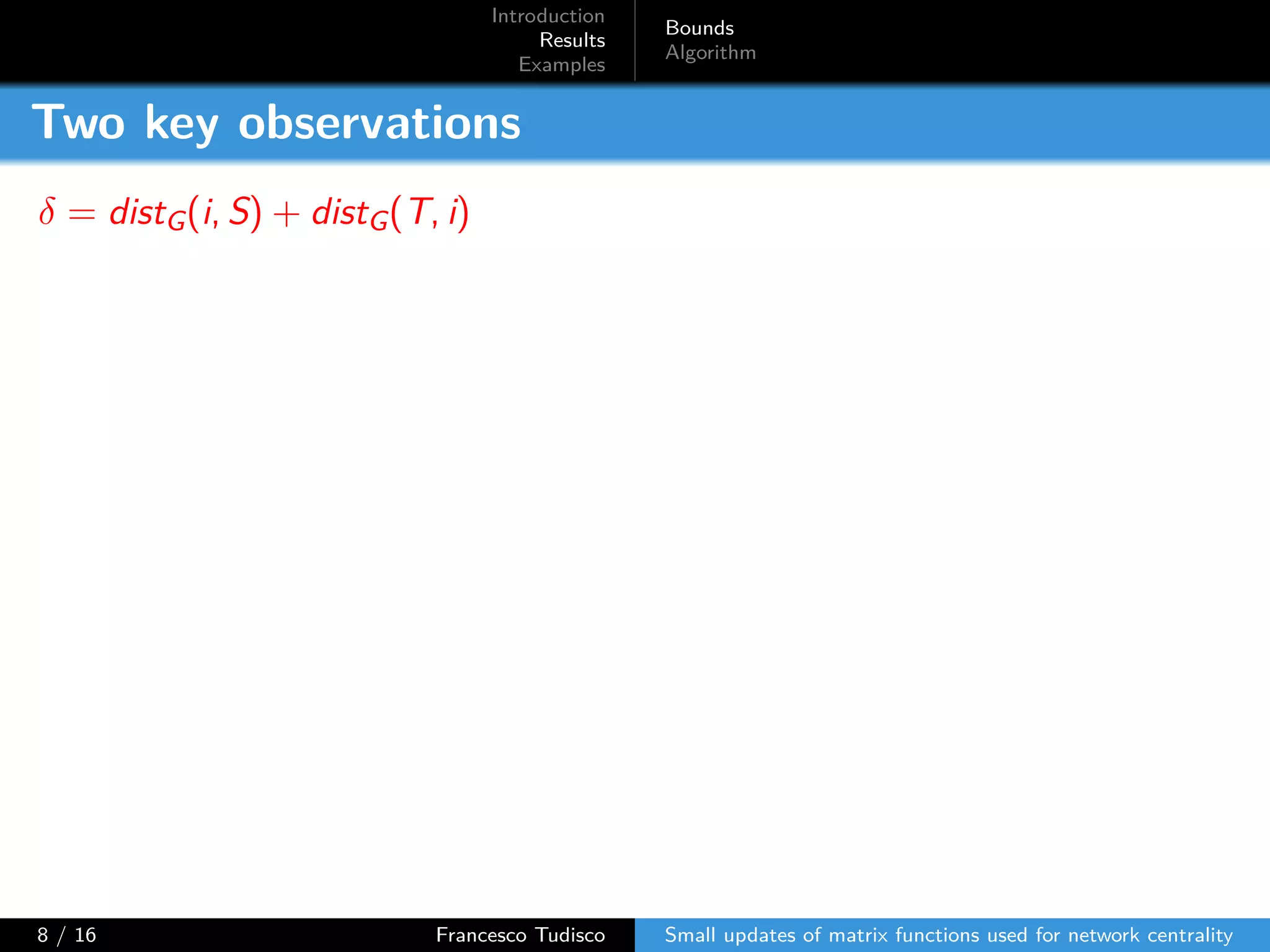
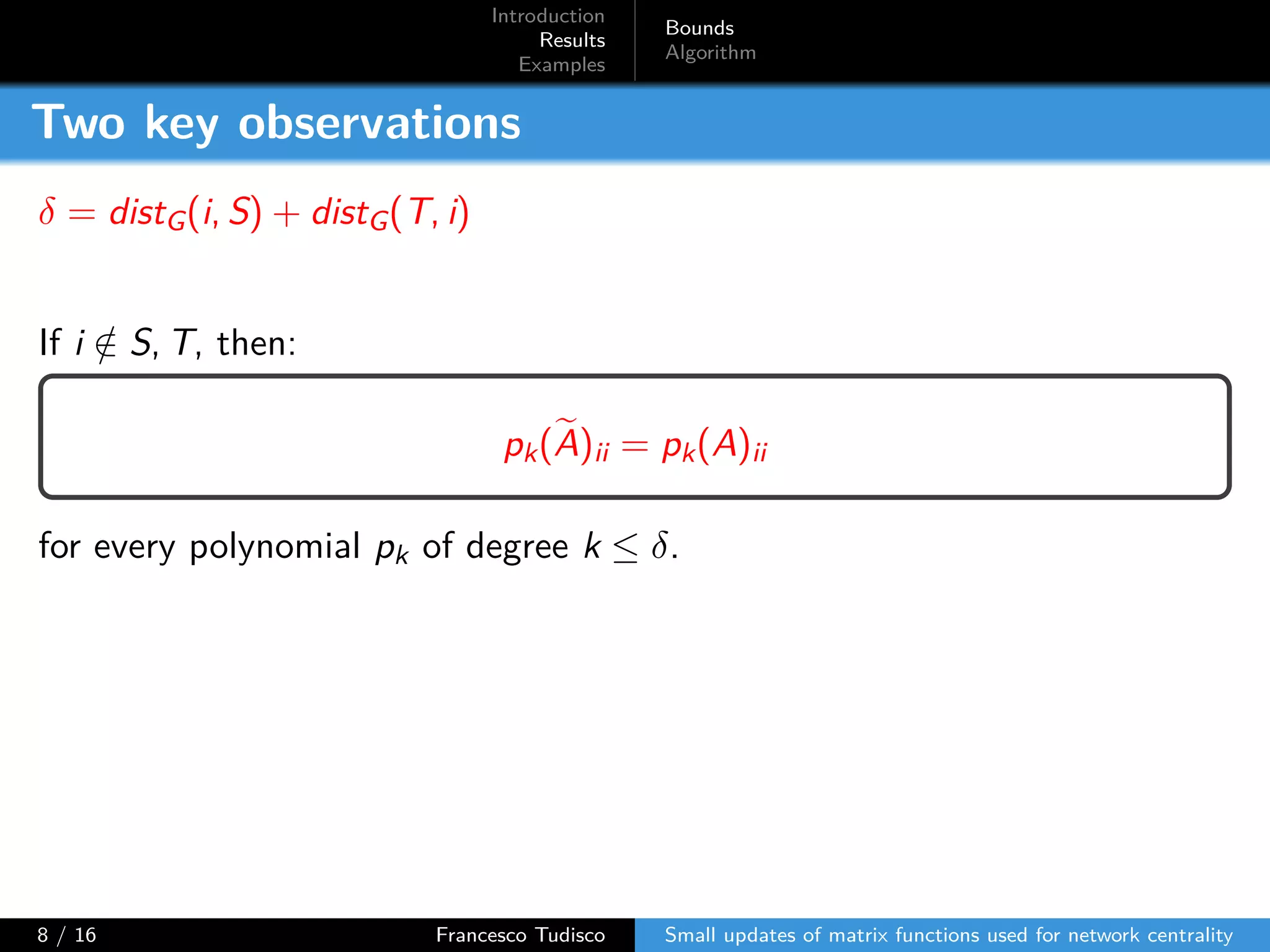
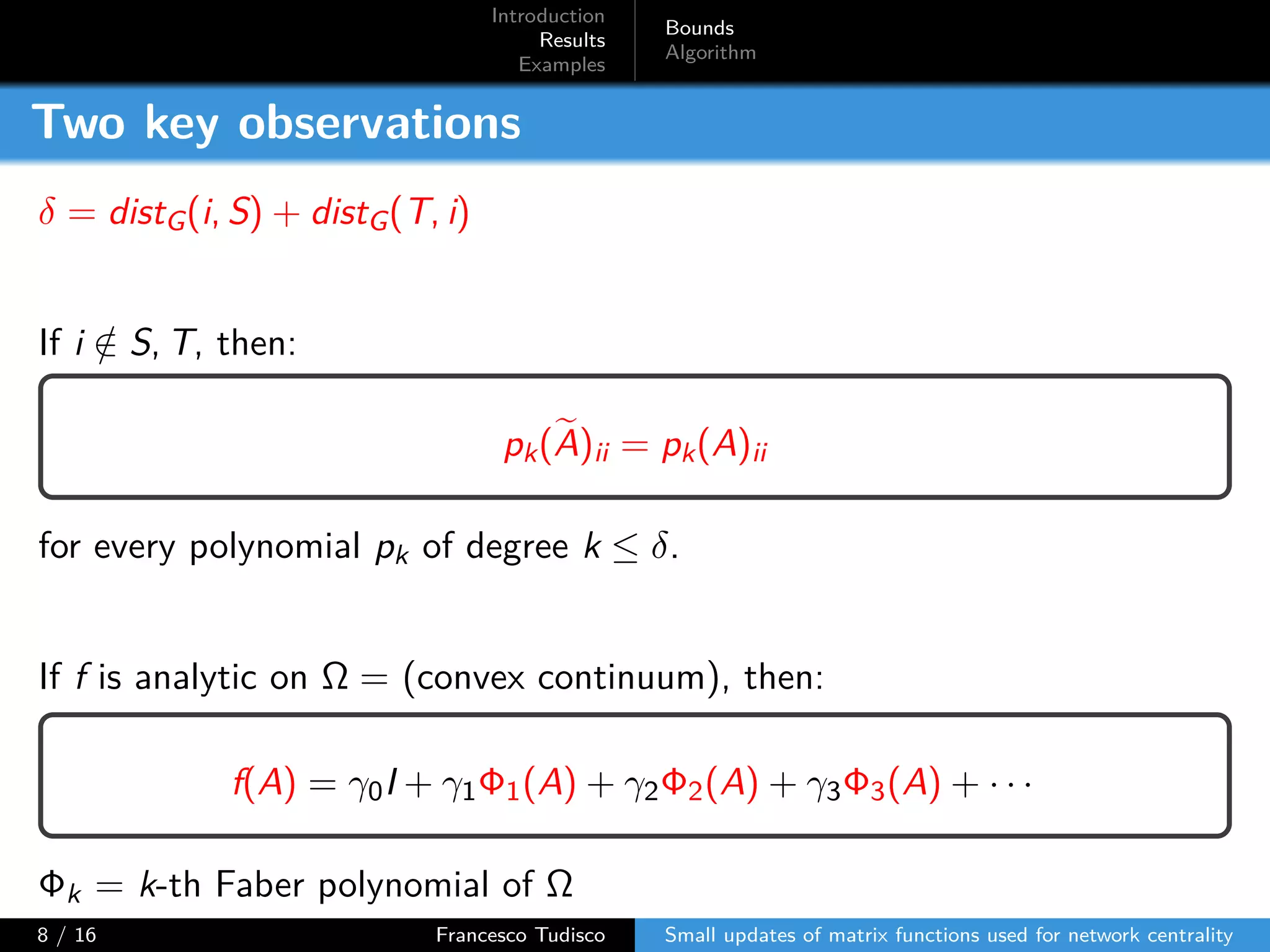
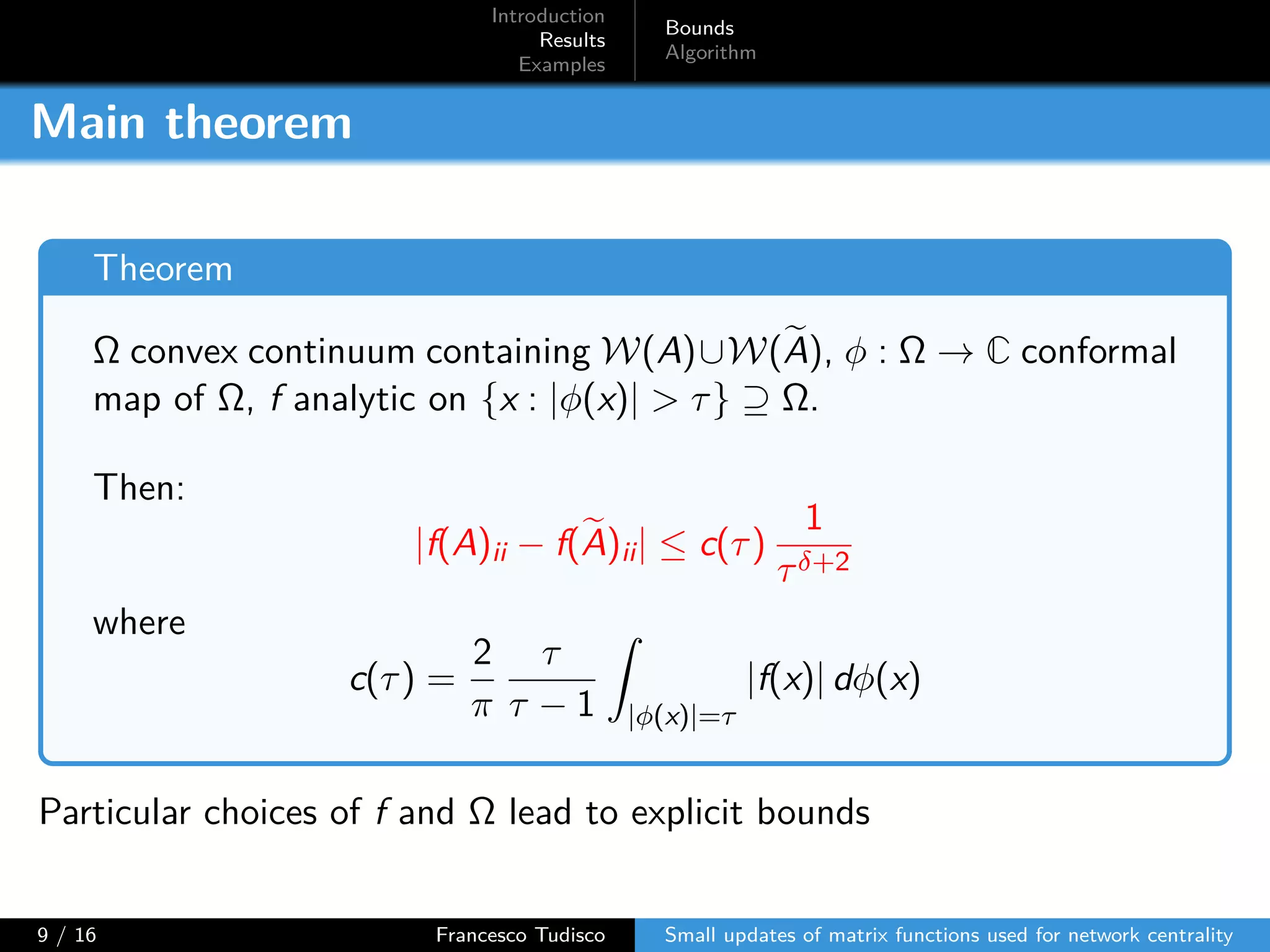
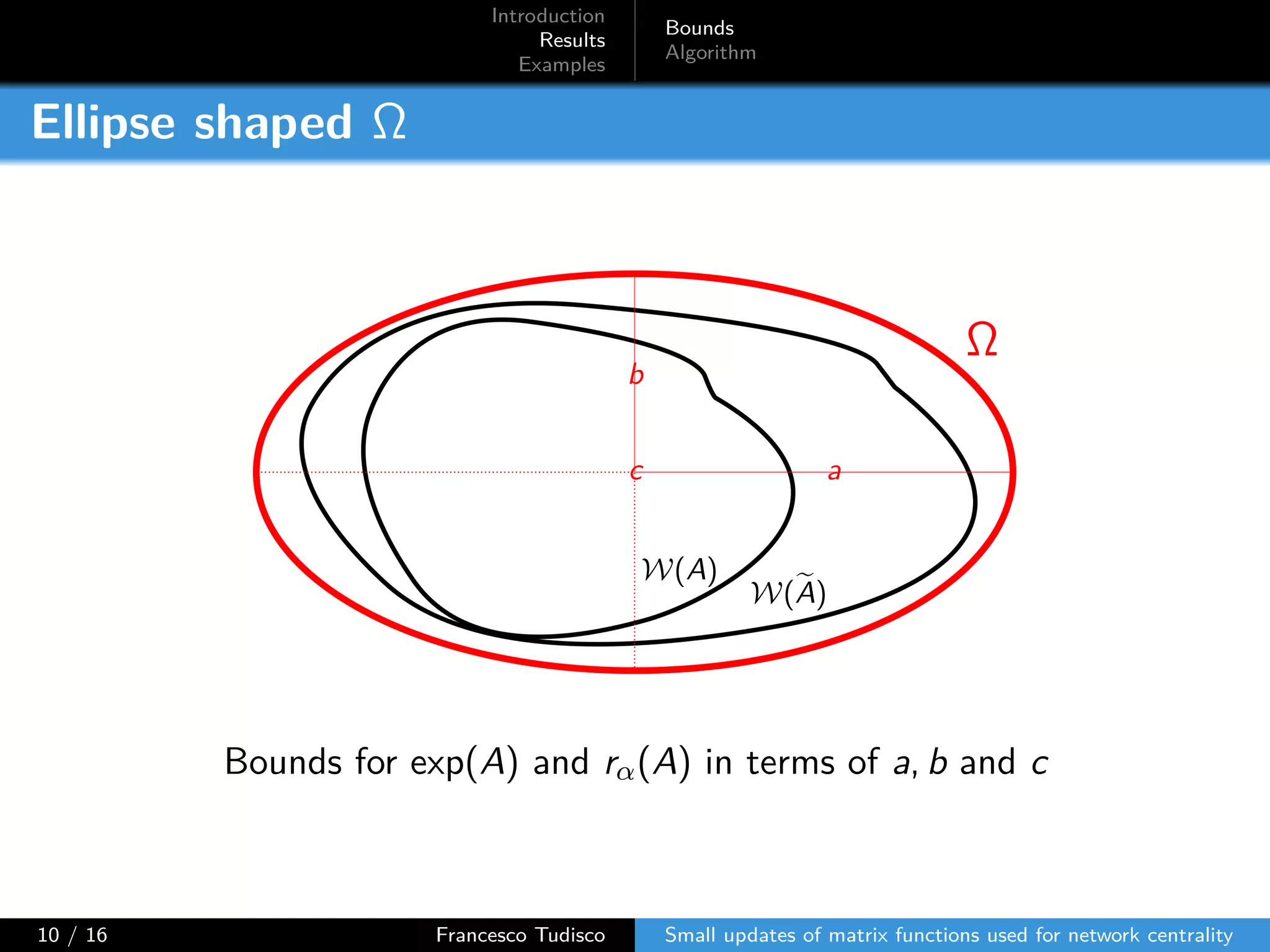
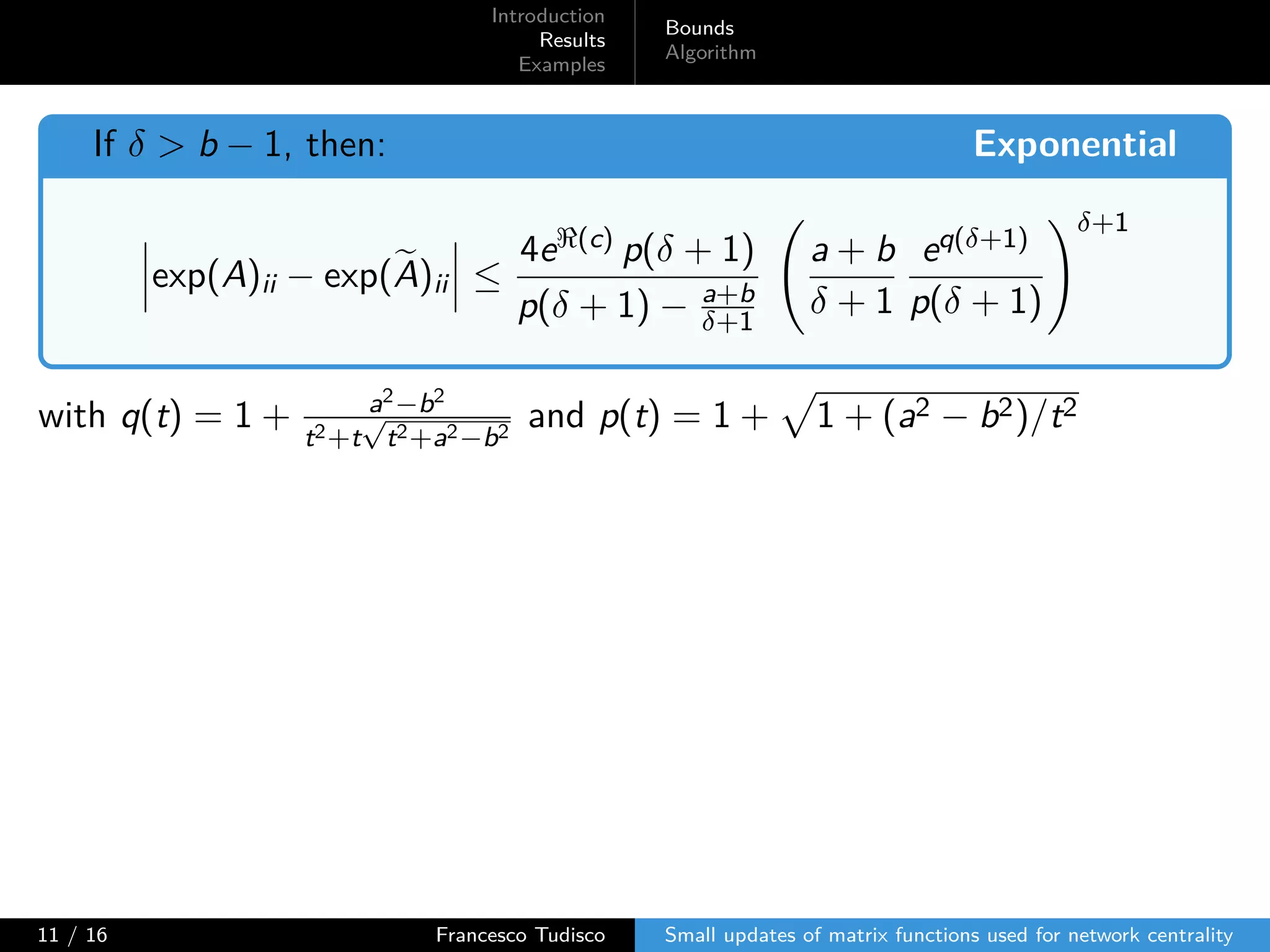
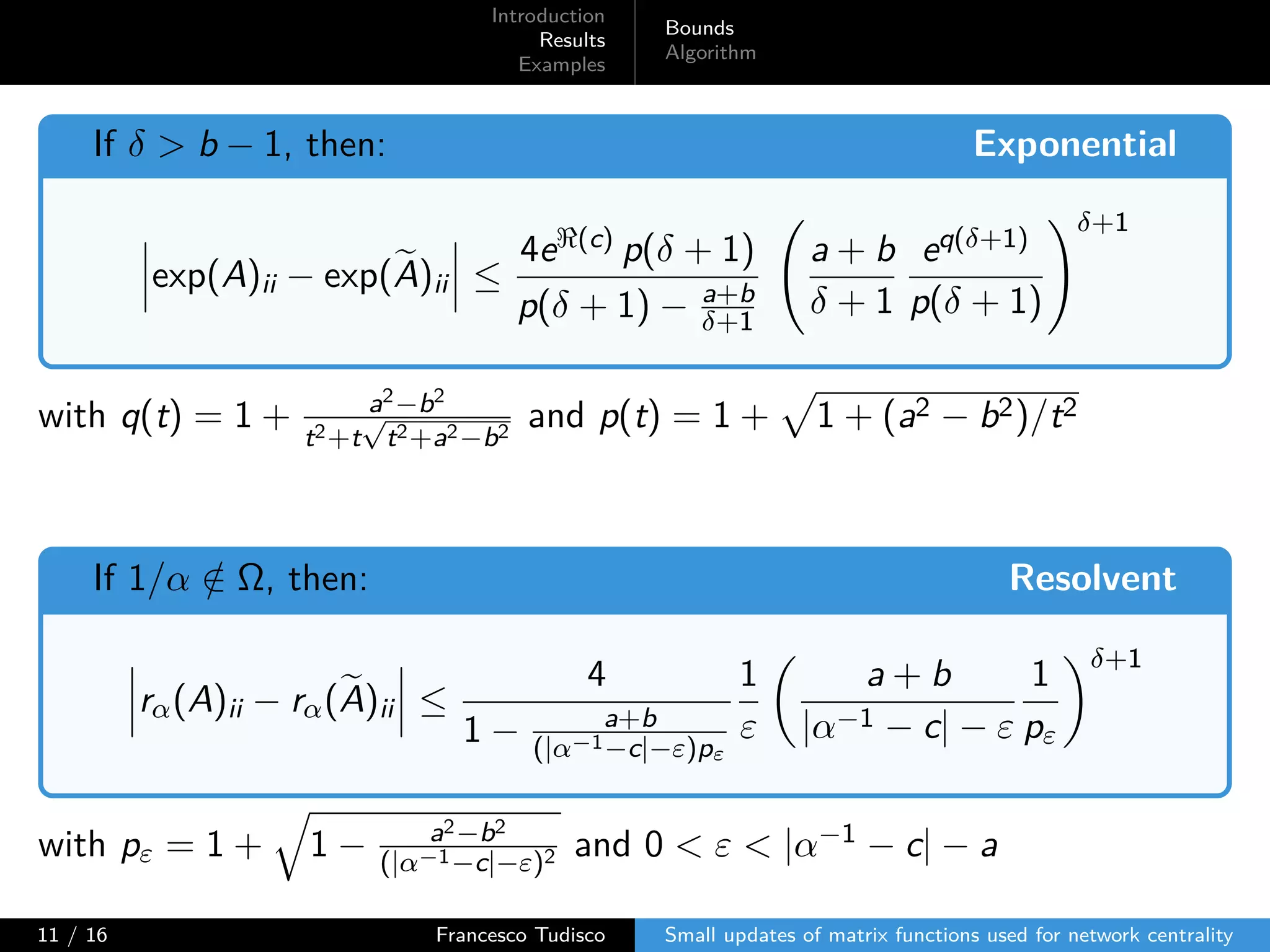
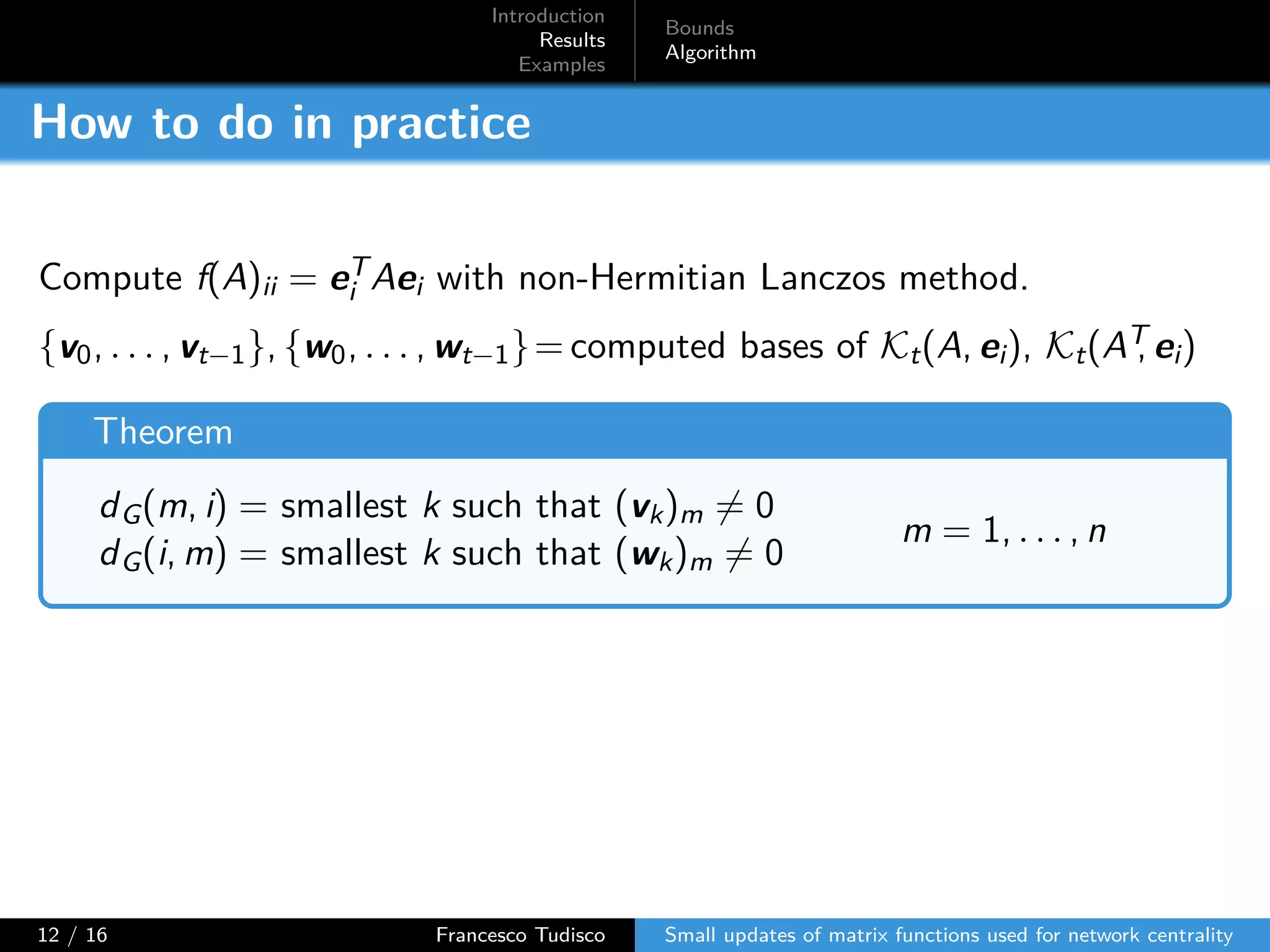
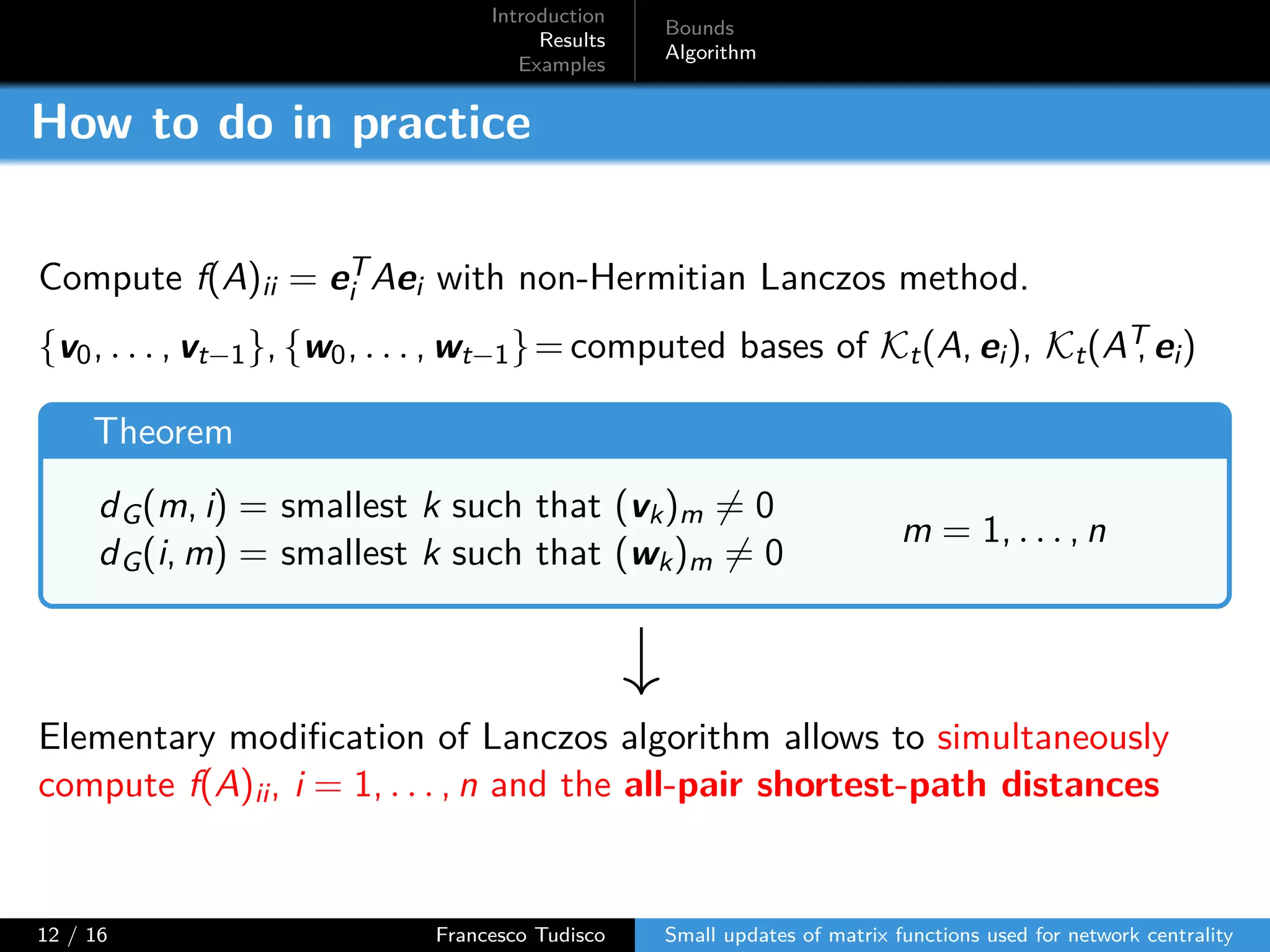
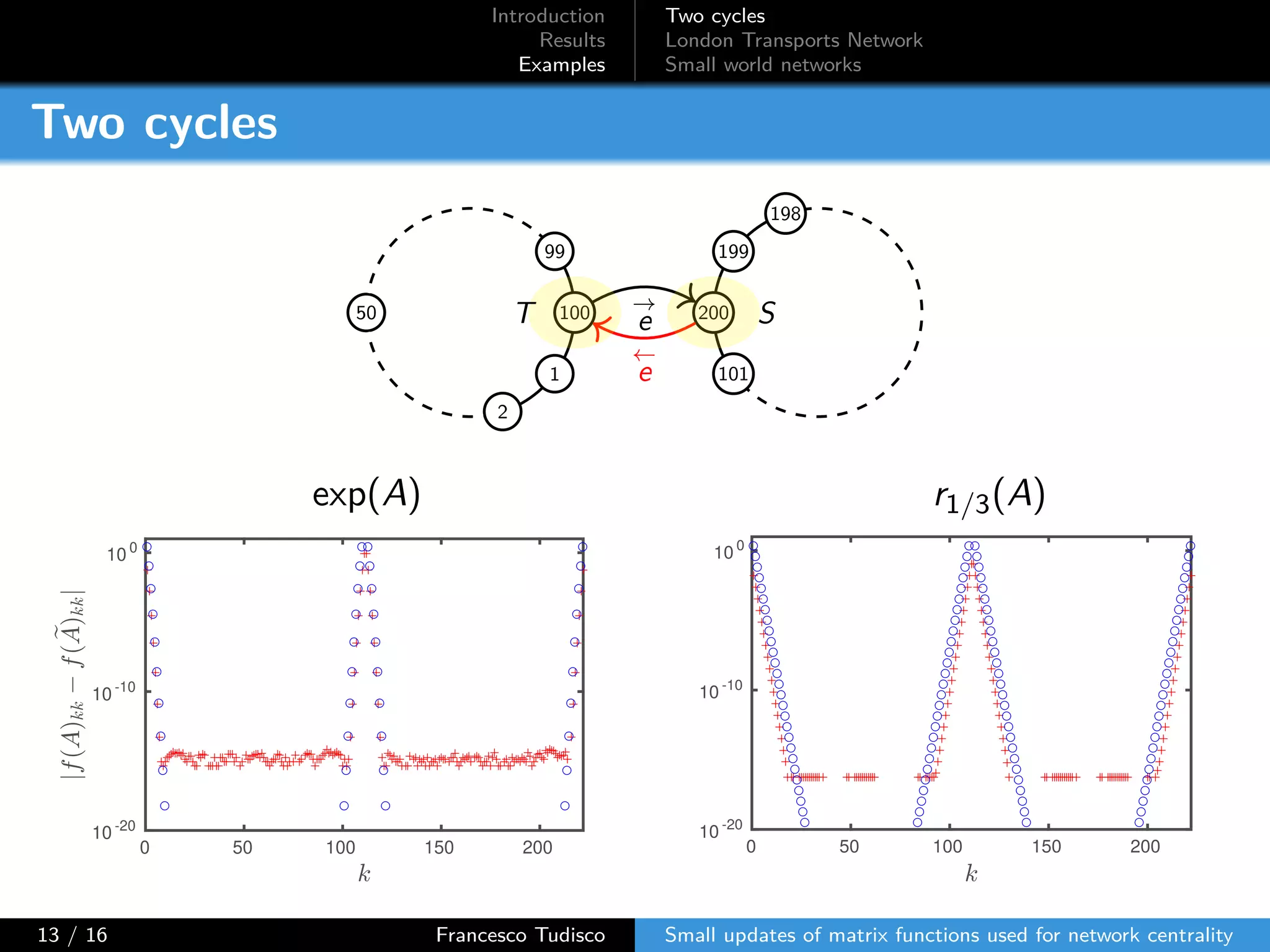
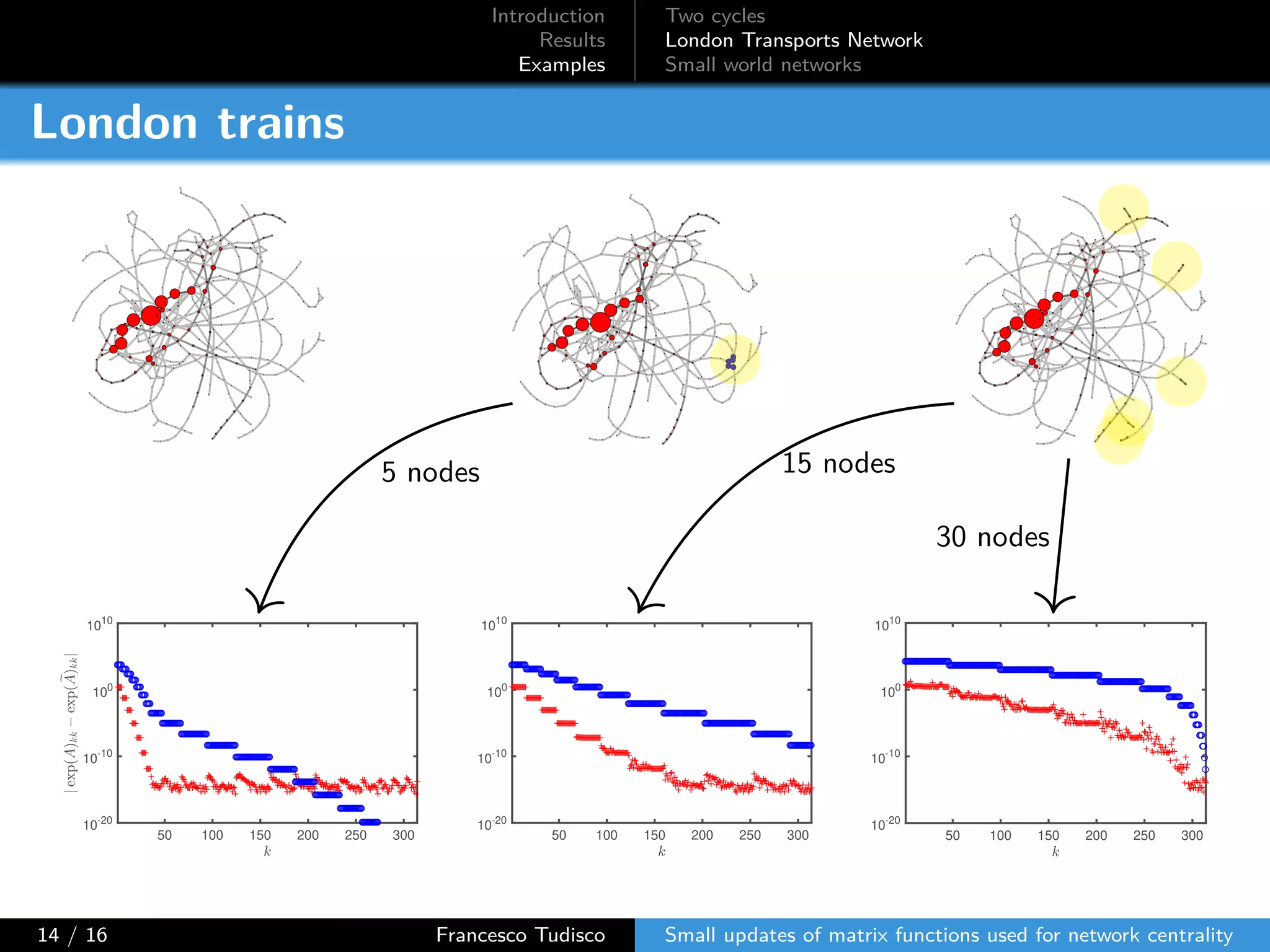
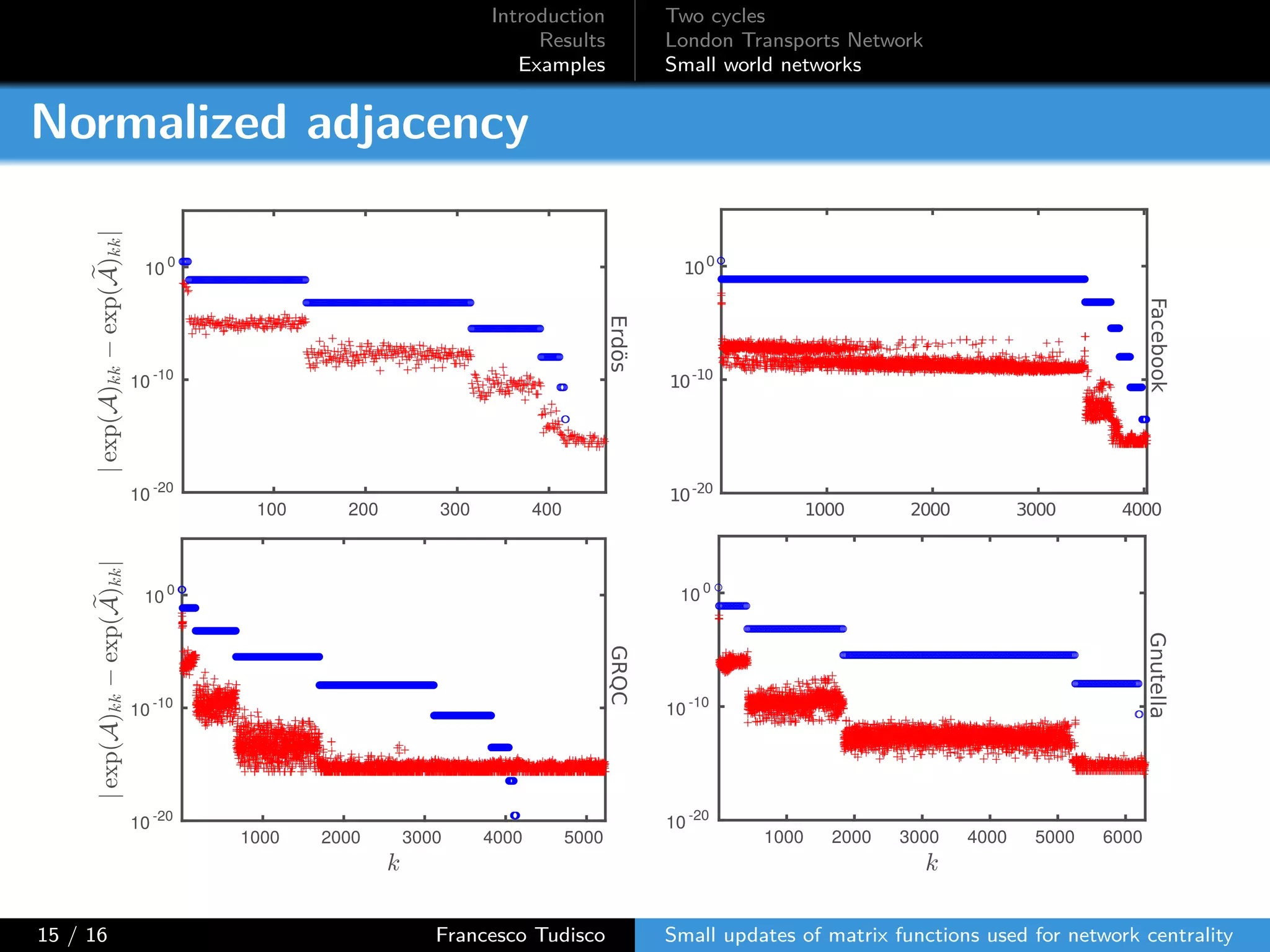
The document discusses updates to matrix functions utilized for evaluating network centrality, focusing on how these functions change with small perturbations in the graph structure. It presents mathematical formulations of network indices based on adjacency matrix properties, addressing computational approaches and related analytical work. The findings highlight bounds on the changes in centrality measures and provide examples from network analysis in various contexts.