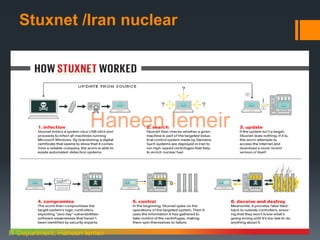
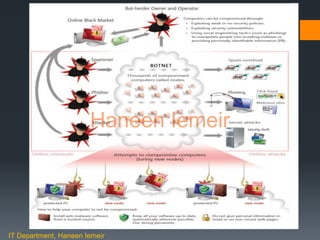
The document discusses information security awareness and cyber attacks. It describes common types of cyber attacks like espionage, phishing, and botnets. Specific examples like Stuxnet, Flame, and the Heartland Payment Systems data breach are examined. The document emphasizes the risks of poor password management, unawareness of data importance, and insider threats. It provides guidance on safeguarding devices and data through measures such as strong passwords, antivirus software, and a business continuity plan.