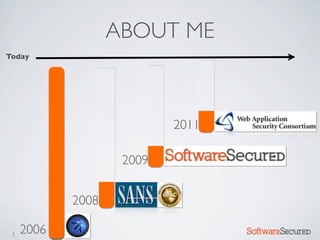
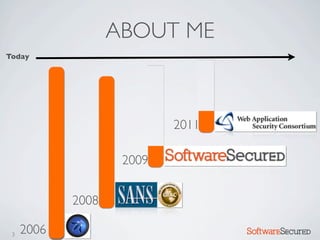
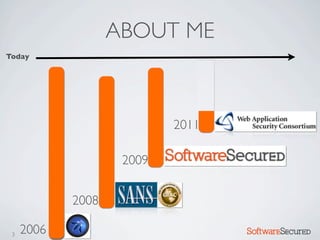
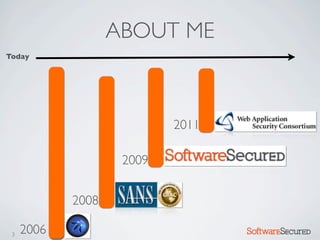
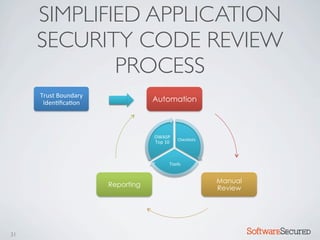
Here are the key things to report:
- Vulnerability type
- Location (file, line number)
- Short description
- Impact
- Recommendation
Provide enough context for developers to understand and fix.
Prioritize vulnerabilities by severity and risk.
29 Softwar S cur
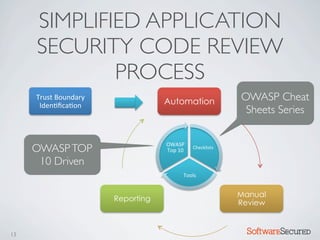
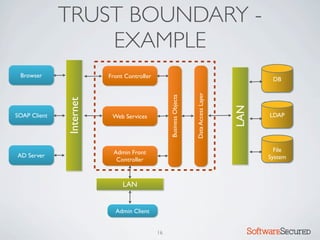
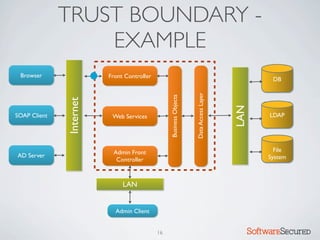
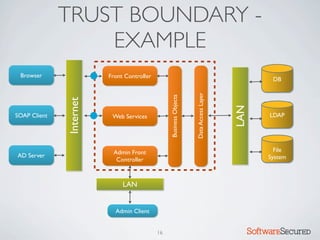
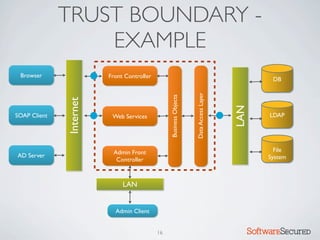
� REPORTING
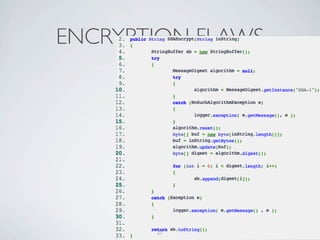
SQL Injection:
Location: \source\ACMEPortal\updateinfo.aspx.cs:
Description: The code below is build dynamic sql statement using
• Weakness Metadata unvalidated data (i.e. name) which can lead to SQL Injection
- High severity
- Data exposure and system access
- Recommend using parameterized