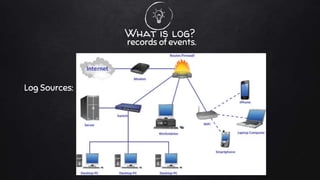
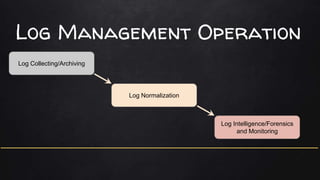
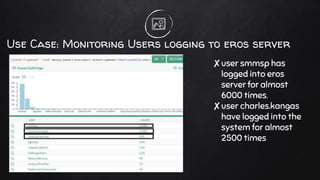
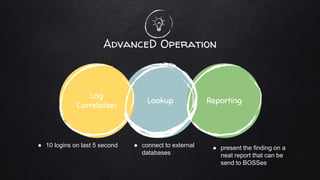
Log management involves collecting logs from various sources, normalizing the data into a readable format, and using log intelligence and monitoring tools to detect threats, enable incident response and forensic investigations, and ensure regulatory compliance. It provides a centralized way to search logs, correlate events, and generate reports which can help security teams more efficiently investigate issues compared to traditional methods of reviewing raw logs. Challenges include a lack of standard log formats and capturing all activity, but the market for log management software is large and growing due to its importance for compliance needs.