In this presentation, we explore what it truly means to build and operate a detection-first SIEM—beyond log collection and basic alerts.
Drawing from real-world SOC experience, this slide deck covers:
Strategic breakdown of SIEM detection rule types
How to build custom anomaly detection using baseline behavior (not vendor UEBA)
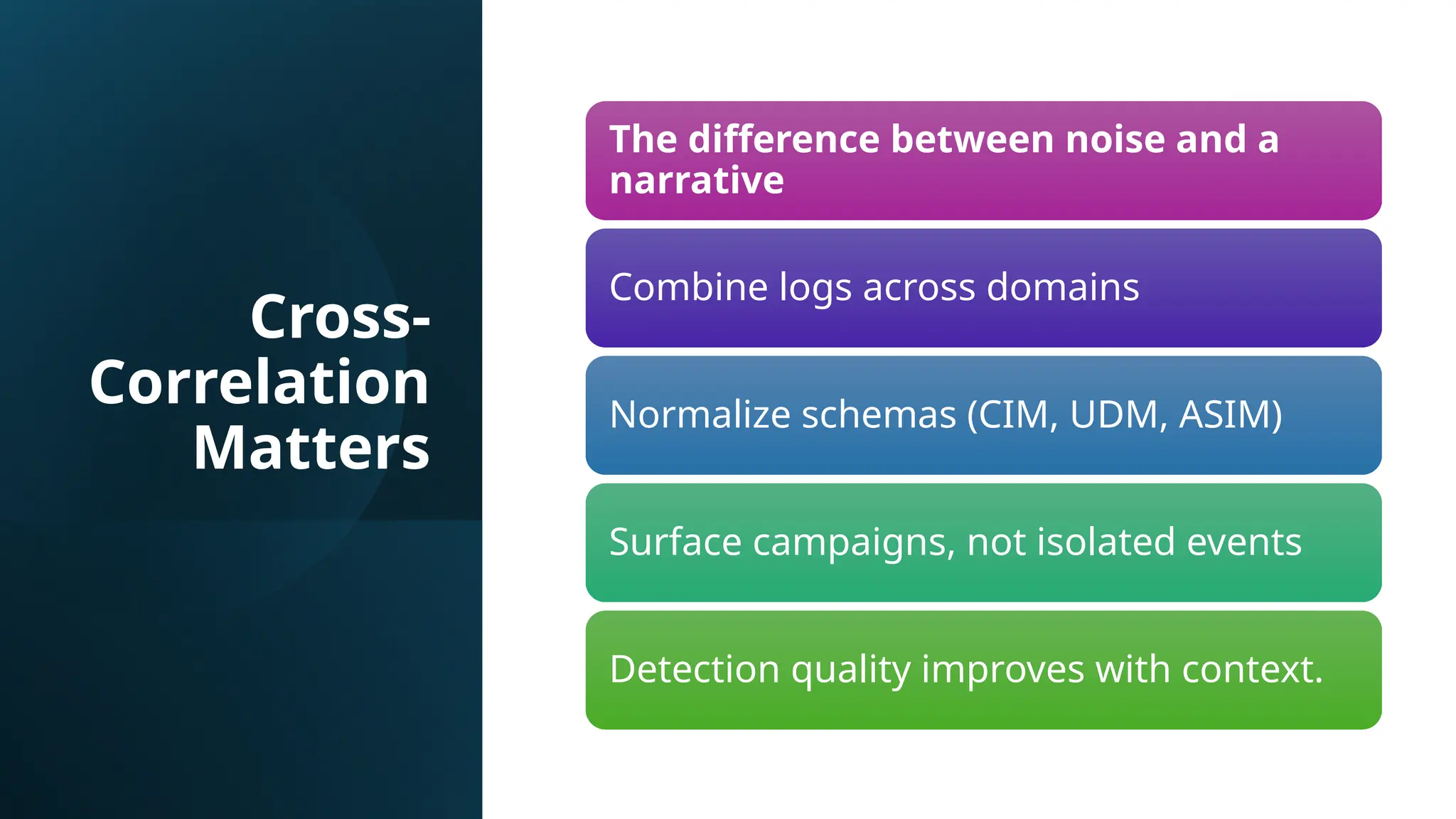
The power of cross-correlation rules to reveal real attack narratives
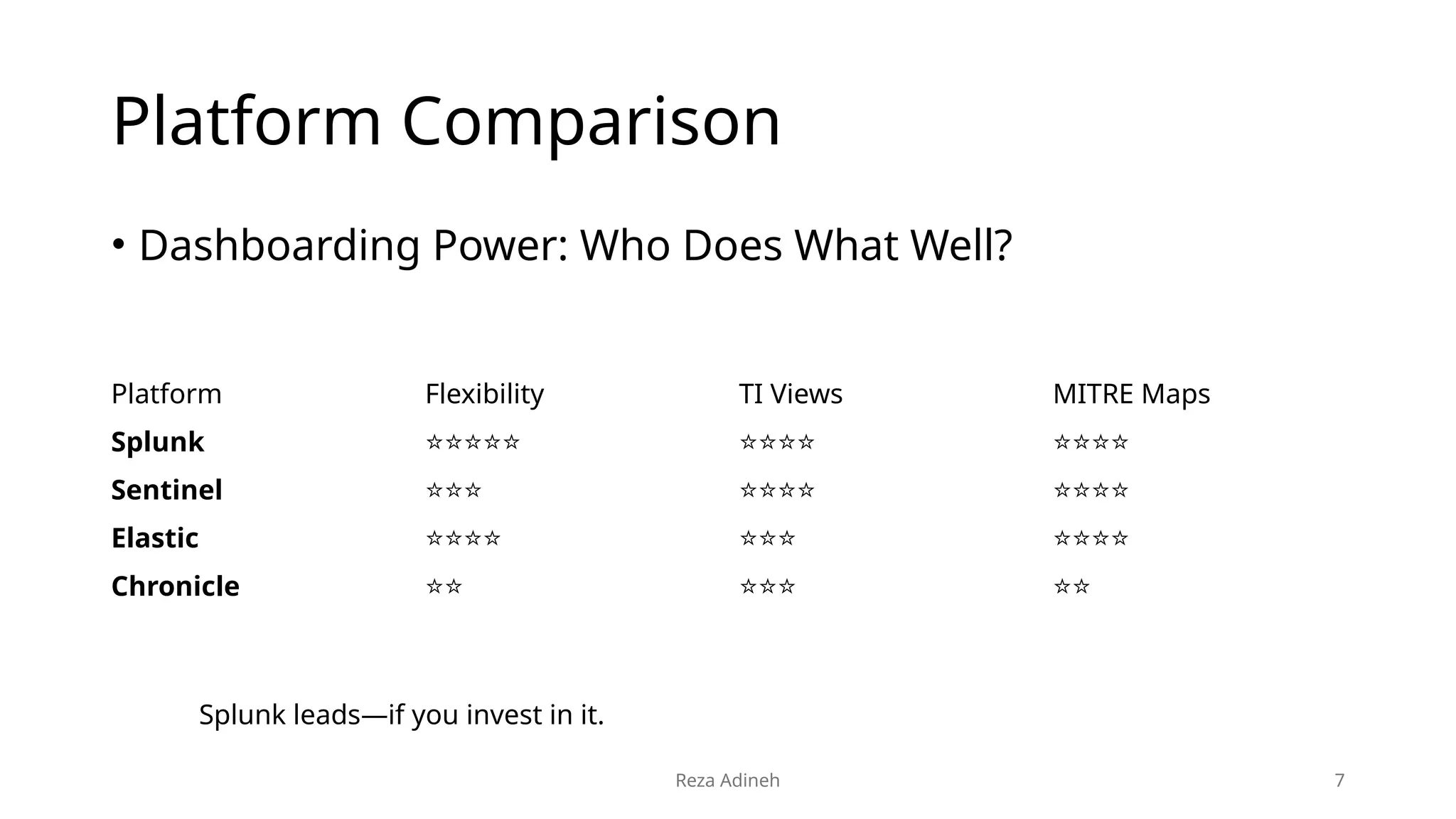
Dashboarding comparison across Splunk, Sentinel, Elastic, and Chronicle
How to design threat-informed use cases mapped to MITRE ATT&CK
Why threat hunting is the R&D wing of any mature SOC
This content is designed for SOC teams, SIEM engineers, threat detection builders, and security leaders who want to shift from reactive operations to intentional, intelligence-driven detection.
Learn how to build detection that sees deeper, responds faster, and evolves smarter.