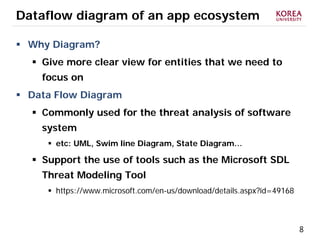
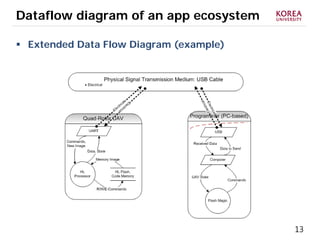
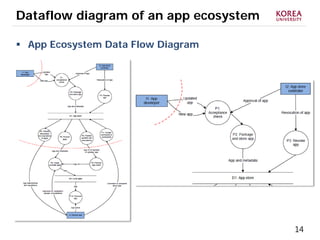
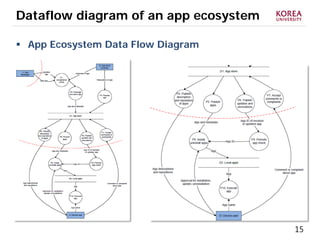
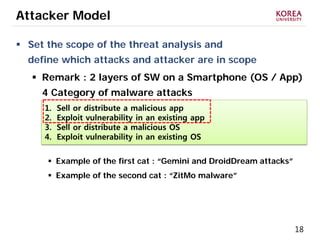
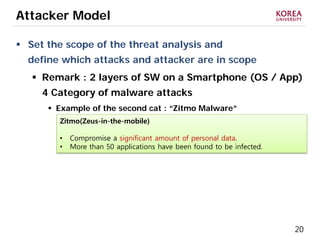
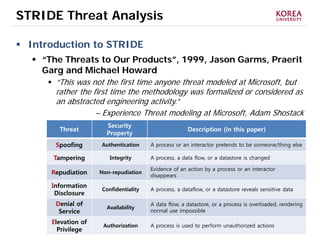
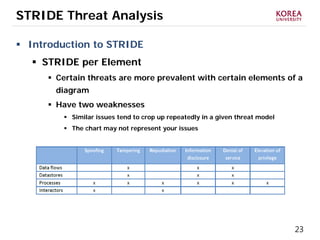
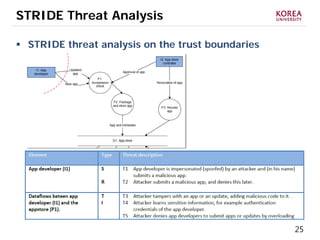
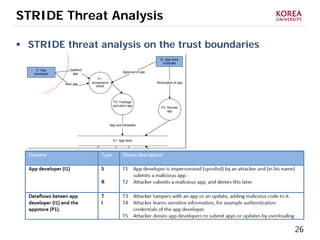
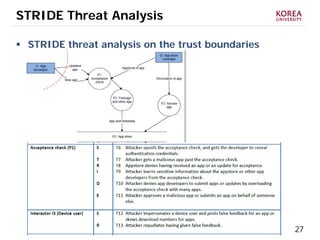
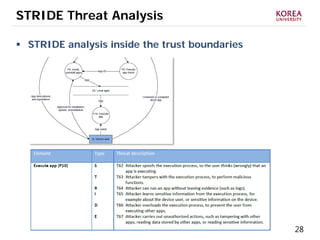
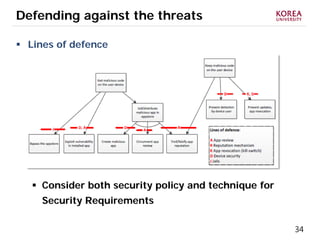
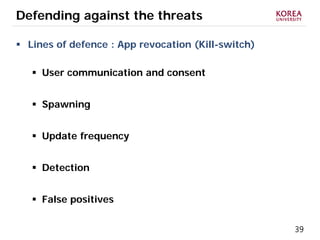
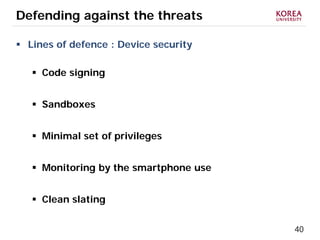
This document provides an overview of strategies to defend against malware threats in mobile app ecosystems. It begins with a data flow diagram that maps the flow of data and processes. It then discusses an attacker model and uses STRIDE threat analysis to evaluate spoofing, tampering, repudiation, information disclosure, denial of service, and elevation of privilege threats. Finally, it proposes five lines of defense: app review using automated and manual analysis, reputation mechanisms based on app history, app revocation, device security features, and walled gardens/jails that restrict apps.














![42
Reference
[1] “Threat modeling using attack trees”, Vineet Saimi
[2] “Threat modeling Smart Home – Technical report”, Kristian Beckers
[3] “Vehicle Control Unit Security using Open source AUTOSAR”,
Anton Bretting & Mei Ha
[4] “Systematic Analysis of Cyber-attacks on CPS-Evaluating applicability of DFD-based
Approach”, Mark Yampolskiy
[5] “Introduction to Microsoft Security Development Lifecycle(SDL) Threat modeling”,
Microsoft
[6] “Google Android security report 2014”, Google
[7] “A threat-driven approach to Cyber security”, Michael Muckin
[8] “How Google Play Security Still Falls Short”, MinPyo Hong
[9] “Online Banking Security Analysis based on STRIDE Threat Model”, Tong Xin
[10] “Threat Modeling as a Basis for Security Requirements”, Suvda Myagmar](https://image.slidesharecdn.com/20160831appstoresecurity-160906081638/85/20160831_app_storesecurity_Seminar-42-320.jpg)
