This document discusses NoSQL injection and strategies for preventing it. It begins with an introduction comparing NoSQL and SQL databases. Next, it defines NoSQL injection and how it can occur. The document then discusses various techniques for preventing NoSQL injection attacks, including reviewing code for vulnerabilities and using input validation. It also provides an example of how NoSQL injection could happen in a PHP/MongoDB application and how to validate input as a string to prevent it.



![NoSQL Injection
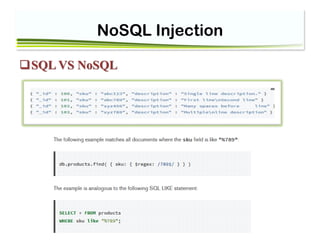
Special case: PHP/MongoDB
find({'username':{’$ne‘ :'Alizadeh‘} })
But PHP will automatically create associative arrays from query string input with square
brackets
page.php? params[foo]= 'Alizadeh’
$params== array(‘foo’ => 'Alizadeh’ )
• MongoDB also use associative arrays for query criteria](https://image.slidesharecdn.com/nosql-classnew-180425094544/85/Session11-NoSQL-InjectionPHP-Injection-11-320.jpg)
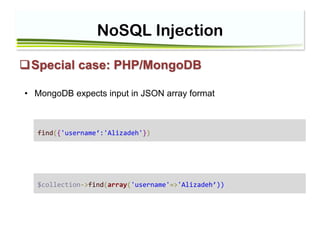
![NoSQL Injection
• if you expect String : just validate “Is it String?”
$db=$dbname;
$m = new MongoClient(); // connect
$db = $m->seminar;
$collection=$db->user;
$username= (string) $_GET['username'];
$query=array('username'=>$username);
$result=$collection->find($query);
foreach ($result as $doc)
{
echo "UserName=".$doc['username'];
}](https://image.slidesharecdn.com/nosql-classnew-180425094544/85/Session11-NoSQL-InjectionPHP-Injection-12-320.jpg)
